基础入门-算法逆向&散列对称非对称&JS源码逆向&AES&DES&RSA&SHA
文章目录
- 安全测试中:
- 加密解密-识别特征&解密条件
- 其他密文特点见:
- 解密实例-密文存储&数据传输
课件附加资源百度云
安全测试中:
密文-有源码直接看源码分析算法(后端必须要有源码才能彻底知道)
密文-没有源码1、猜识别 2、看前端JS(加密逻辑是不是在前端)
#算法加密-概念&分类&类型
-
单向散列加密 -MD5
单向散列加密算法的优点有(以MD5为例):
方便存储,损耗低:加密/加密对于性能的损耗微乎其微。
单向散列加密的缺点就是存在暴力破解的可能性,最好通过加盐值的方式提高安全性,此外可能存在散列冲突。我们都知道MD5加密也是可以破解的。
常见的单向散列加密算法有:
MD5 SHA MAC CRC -
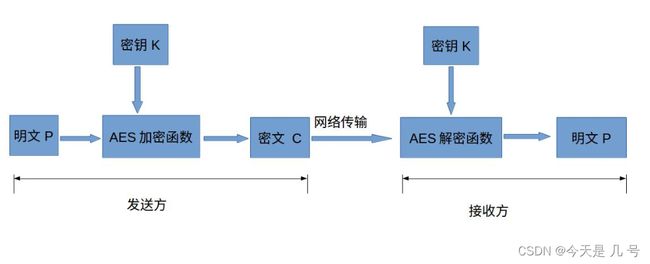
对称加密 -AES
对称加密优点是算法公开、计算量小、加密速度快、加密效率高。
缺点是发送方和接收方必须商定好密钥,然后使双方都能保存好密钥,密钥管理成为双方的负担。
常见的对称加密算法有:
DES AES RC4 -
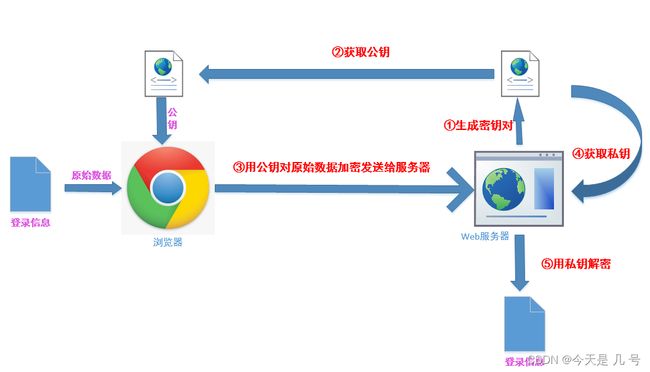
非对称加密 -RSA
非对称加密的优点是与对称加密相比,安全性更好,加解密需要不同的密钥,公钥和私钥都可进行相互的加解密。
缺点是加密和解密花费时间长、速度慢,只适合对少量数据进行加密。
常见的非对称加密算法:
RSA RSA2 PKCS
加密解密-识别特征&解密条件
MD5密文特点:
1、由数字“0-9”和字母“a-f”所组成的字符串
2、固定的位数 16 和 32位
解密需求:密文即可,但复杂明文可能解不出
BASE64编码特点:
0、大小写区分,通过数字和字母的组合
1、一般情况下密文尾部都会有两个等号,明文很少的时候则没有
2、明文越长密文越长,一般不会出现"/“”+"在密文中
AES、DES密文特点:
同BASE64基本类似,但一般会出现"/“和”+"在密文中
解密需求:密文,模式,加密Key,偏移量,条件满足才可解出
RSA密文特点:
特征同AES,DES相似,但是长度较长
解密需求:密文,公钥或私钥即可解出
其他密文特点见:
1.30余种加密编码类型的密文特征分析(建议收藏)
https://mp.weixin.qq.com/s?__biz=MzAwNDcxMjI2MA==&mid=2247484455&idx=1&sn=e1b4324ddcf7d6123be30d9a5613e17b&chksm=9b26f60cac517f1a920cf3b73b3212a645aeef78882c47957b9f3c2135cb7ce051c73fe77bb2&mpshare=1&scene=23&srcid=1111auAYWmr1N0NAs9Wp2hGz&sharer_sharetime=1605145141579&sharer_shareid=5051b3eddbbe2cb698aedf9452370026#rd
2.CTF中常见密码题解密网站总结(建议收藏)
https://blog.csdn.net/qq_41638851/article/details/100526839
3.CTF密码学常见加密解密总结(建议收藏)
https://blog.csdn.net/qq_40837276/article/details/83080460
解密实例-密文存储&数据传输
1、密码存储(后端处理)
X3.2-md5&salt
DZ对应代码段-/uc_server/model/user.php
function add_user() {
p a s s w o r d = m d 5 ( m d 5 ( password = md5(md5( password=md5(md5(password).$salt);
}
$h = 'd7192407bb4bfc83d28f374b6812fbcd';
$hash=md5(md5('123456').'3946d5');
if($h==$hash){
echo 'ok';
}else{
echo 'no';
}
?>
X3.5-hash
DZ对应代码段-/uc_server/model/user.php
function add_user() {
$salt = ‘’;
$password = t h i s − > g e n e r a t e p a s s w o r d ( this->generate_password( this−>generatepassword(password);
}
function generate_password($password) {
$algo = $this->get_passwordalgo();
$options = $this->get_passwordoptions();
KaTeX parse error: Unexpected character: '' at position 21: …= password_hash̲(password, $algo, $options);
}
$hash = '$2y$10$KA.7VYVheqod8F3X65tWjO3ZXfozNA2fC4oIZoDSu/TbfgKmiw7xO';
if (password_verify('123456', $hash)) {
echo 'ok';
} else {
echo 'error';
}
?>
2、数据通讯
-博客登录-zblog(前端处理)
<script src="script/md5.js" type="text/javascript"></script>
$("#btnPost").click(function(){
var strPassWord=$("#edtPassWord").val();
$("form").attr("action","cmd.php?act=verify");
$("#password").val(MD5(strPassWord));
-墨者靶场-(后端处理)
-1 union select 1,database(),user(),4_mozhe
xgd58ipTrnx8VzSBJicqCibZxIRsZKgXOYUrNQP8fCCtx9JZ+6K1hHt7RKkzV305
eGdkNThpcFRybng4VnpTQkppY3FDaWJaeElSc1pLZ1hPWVVyTlFQOGZDQ3R4OUpaKzZLMWhIdDdSS2t6VjMwNQ==
test.php php加解密 php版本7.3
//aes
namespace vendor;
class EncryptionTool{
public static function enAES($originTxt, $key): string{
return base64_encode(openssl_encrypt($originTxt, 'AES-128-ECB',$key, OPENSSL_RAW_DATA));
}
public static function deAES($originTxt, $key): string{
$data = base64_decode($originTxt);
return openssl_decrypt($data,'AES-128-ECB',$key, OPENSSL_RAW_DATA);
}
}
//des
class DES
{
/**
* @var string $method 加解密方法,可通过 openssl_get_cipher_methods() 获得
*/
protected $method;
/**
* @var string $key 加解密的密钥
*/
protected $key;
/**
* @var string $output 输出格式 无、base64、hex
*/
protected $output;
/**
* @var string $iv 加解密的向量
*/
protected $iv;
/**
* @var string $options
*/
protected $options;
// output 的类型
const OUTPUT_NULL = '';
const OUTPUT_BASE64 = 'base64';
const OUTPUT_HEX = 'hex';
/**
* DES constructor.
* @param string $key
* @param string $method
* ECB DES-ECB、DES-EDE3 (为 ECB 模式时,$iv 为空即可)
* CBC DES-CBC、DES-EDE3-CBC、DESX-CBC
* CFB DES-CFB8、DES-EDE3-CFB8
* CTR
* OFB
*
* @param string $output
* base64、hex
*
* @param string $iv
* @param int $options
*/
public function __construct($key, $method = 'DES-ECB', $output = '', $iv = '', $options = OPENSSL_RAW_DATA | OPENSSL_NO_PADDING)
{
$this->key = $key;
$this->method = $method;
$this->output = $output;
$this->iv = $iv;
$this->options = $options;
}
/**
* 加密
*
* @param $str
* @return string
*/
public function encrypt($str)
{
$str = $this->pkcsPadding($str, 8);
$sign = openssl_encrypt($str, $this->method, $this->key, $this->options, $this->iv);
if ($this->output == self::OUTPUT_BASE64) {
$sign = base64_encode($sign);
} else if ($this->output == self::OUTPUT_HEX) {
$sign = bin2hex($sign);
}
return $sign;
}
/**
* 解密
*
* @param $encrypted
* @return string
*/
public function decrypt($encrypted)
{
if ($this->output == self::OUTPUT_BASE64) {
$encrypted = base64_decode($encrypted);
} else if ($this->output == self::OUTPUT_HEX) {
$encrypted = hex2bin($encrypted);
}
$sign = @openssl_decrypt($encrypted, $this->method, $this->key, $this->options, $this->iv);
$sign = $this->unPkcsPadding($sign);
$sign = rtrim($sign);
return $sign;
}
/**
* 填充
*
* @param $str
* @param $blocksize
* @return string
*/
private function pkcsPadding($str, $blocksize)
{
$pad = $blocksize - (strlen($str) % $blocksize);
return $str . str_repeat(chr($pad), $pad);
}
/**
* 去填充
*
* @param $str
* @return string
*/
private function unPkcsPadding($str)
{
$pad = ord($str{strlen($str) - 1});
if ($pad > strlen($str)) {
return false;
}
return substr($str, 0, -1 * $pad);
}
}
//rsa
define('RSA_PUBLIC', '-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCmkANmC849IOntYQQdSgLvMMGm
8V/u838ATHaoZwvweoYyd+/7Wx+bx5bdktJb46YbqS1vz3VRdXsyJIWhpNcmtKhY
inwcl83aLtzJeKsznppqMyAIseaKIeAm6tT8uttNkr2zOymL/PbMpByTQeEFlyy1
poLBwrol0F4USc+owwIDAQAB
-----END PUBLIC KEY-----');
define('RSA_PRIVATE','-----BEGIN PRIVATE KEY-----
MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAKaQA2YLzj0g6e1h
BB1KAu8wwabxX+7zfwBMdqhnC/B6hjJ37/tbH5vHlt2S0lvjphupLW/PdVF1ezIk
haGk1ya0qFiKfByXzdou3Ml4qzOemmozIAix5ooh4Cbq1Py6202SvbM7KYv89syk
HJNB4QWXLLWmgsHCuiXQXhRJz6jDAgMBAAECgYAIF5cSriAm+CJlVgFNKvtZg5Tk
93UhttLEwPJC3D7IQCuk6A7Qt2yhtOCvgyKVNEotrdp3RCz++CY0GXIkmE2bj7i0
fv5vT3kWvO9nImGhTBH6QlFDxc9+p3ukwsonnCshkSV9gmH5NB/yFoH1m8tck2Gm
BXDj+bBGUoKGWtQ7gQJBANR/jd5ZKf6unLsgpFUS/kNBgUa+EhVg2tfr9OMioWDv
MSqzG/sARQ2AbO00ytpkbAKxxKkObPYsn47MWsf5970CQQDIqRiGmCY5QDAaejW4
HbOcsSovoxTqu1scGc3Qd6GYvLHujKDoubZdXCVOYQUMEnCD5j7kdNxPbVzdzXll
9+p/AkEAu/34iXwCbgEWQWp4V5dNAD0kXGxs3SLpmNpztLn/YR1bNvZry5wKew5h
z1zEFX+AGsYgQJu1g/goVJGvwnj/VQJAOe6f9xPsTTEb8jkAU2S323BG1rQFsPNg
jY9hnWM8k2U/FbkiJ66eWPvmhWd7Vo3oUBxkYf7fMEtJuXu+JdNarwJAAwJK0YmO
LxP4U+gTrj7y/j/feArDqBukSngcDFnAKu1hsc68FJ/vT5iOC6S7YpRJkp8egj5o
pCcWaTO3GgC5Kg==
-----END PRIVATE KEY-----');
$password='xiaodisec';
//md5
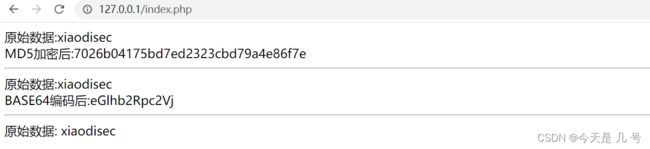
echo "原始数据:$password". "
";
echo "MD5加密后:".md5($password). "
";
//base64
echo "原始数据:$password". "
";
echo "BASE64编码后:".base64_encode($password). "
";
//aes
echo "原始数据: " . $password . "
";
$data = EncryptionTool::enAES($password, "1234567891234567");
echo "AES加密后: " . $data . "
";
//echo "解密后: " . EncryptionTool::deAES($data, "1234567891234567") . "
";
//des
echo "原始数据:$password". "
";
$key = 'key123456';
$iv = 'iv123456';
// DES CBC 加解密
echo 'DES CBC 加解密:';
$des = new DES($key, 'DES-CBC', DES::OUTPUT_BASE64, $iv);
echo $base64Sign = $des->encrypt($password);
echo "
";
//echo $des->decrypt($base64Sign);
echo "
";
// DES ECB 加解密
echo "原始数据:$password". "
";
echo 'DES ECB 加解密:';
$des = new DES($key, 'DES-ECB', DES::OUTPUT_BASE64);
echo $base64Sign = $des->encrypt($password);
echo "
";
//echo $des->decrypt($base64Sign);
//rsa
//公钥加密
$public_key = openssl_pkey_get_public(RSA_PUBLIC);
if(!$public_key){
die('公钥不可用');
}
//第一个参数是待加密的数据只能是string,第二个参数是加密后的数据,第三个参数是openssl_pkey_get_public返回的资源类型,第四个参数是填充方式
$return_en = openssl_public_encrypt($password, $crypted, $public_key);
if(!$return_en){
return('加密失败,请检查RSA秘钥');
}
$eb64_cry = base64_encode($crypted);
echo "RSA公钥加密数据:".$eb64_cry;
echo "
";
//私钥解密
$private_key = openssl_pkey_get_private(RSA_PRIVATE);
if(!$private_key){
die('私钥不可用');
}
$return_de = openssl_private_decrypt(base64_decode($eb64_cry), $decrypted, $private_key);
if(!$return_de){
return('解密失败,请检查RSA秘钥');
}
echo "RSA私钥解密数据:".$decrypted;
echo "
";
//私钥加密
$private_key = openssl_pkey_get_private(RSA_PRIVATE);
if(!$private_key){
die('私钥不可用');
}
$return_en = openssl_private_encrypt($password, $crypted, $private_key);
if(!$return_en){
return('加密失败,请检查RSA秘钥');
}
$eb64_cry = base64_encode($crypted);
echo "RSA私钥加密数据".$eb64_cry;
echo "
";
//公钥解密
$public_key = openssl_pkey_get_public(RSA_PUBLIC);
if(!$public_key){
die('公钥不可用');
}
$return_de = openssl_public_decrypt(base64_decode($eb64_cry), $decrypted, $public_key);
if(!$return_de){
return('解密失败,请检查RSA秘钥');
}
echo "RSA公钥解密数据:".$decrypted;
echo "
";
?>