nginx ssl加密_如何通过让我们加密SSL证书来保护Nginx
nginx ssl加密
Let’s Encrypt is a free, open source and automated certificate authority (CA) pioneered by Internet Security Research Group (ISRG) and offers SSL/TLS certificates to encrypt communications involving two parties.
Let's Encrypt是由Internet Security Research Group(ISRG)倡导的免费,开源和自动证书颁发机构(CA),并提供SSL / TLS证书来加密涉及两方的通信。
An SSL certificate in your website will not only increase your website’s security through encryption but also improve your site’s SEO ranking since Google has made it mandatory to include an SSL certificate for a better SEO ranking.
您的网站中的SSL证书不仅可以通过加密来提高网站的安全性,而且可以提高您网站的SEO排名,因为Google强制要求包括SSL证书以提高SEO排名。
In this article, we will inquire into how to secure an NGINX server with Let’s Encrypt SSL certificate in Ubuntu 18.04.
在本文中,我们将探讨如何在Ubuntu 18.04中使用Let's Encrypt SSL证书保护NGINX服务器的安全。
先决条件 (Prerequisites)
- You have the privileges to open a SSH session in Ubuntu 18.04 server either by using a root user or by using a sudo enabled user. 您有权使用root用户或使用启用了sudo的用户在Ubuntu 18.04服务器中打开SSH会话。
- You have already installed NGINX by following our tutorial from here. 您已经按照此处的教程安装了NGINX。
- A registered domain name. 注册域名。
- DNS A record that points to your server’s IP address based on the domain name that you want to use. DNS A记录,它根据您要使用的域名指向服务器的IP地址。
安装让我们加密客户端库 (Install Let’s Encrypt Client library)
The very first step that you need to accomplish is to install the Let’s Encrypt client library which in turn will be used to request certificates from LE authority. One way to do this is by cloning the Let’s Encrypt client library from its official repository in your server.
您需要完成的第一步是安装Let's Encrypt客户端库,该库随后将用于向LE授权请求证书。 一种方法是从服务器中的官方存储库中克隆“让我们加密”客户端库。
It is also possible to install the same from the official repository of Ubuntu. In Ubuntu’s repository, the client library is known as certbot provided by Let’s Encrypt developers. But we will choose the former method of installing it i.e. by cloning the Github repository of Let’s Encrypt.
也可以从Ubuntu的官方存储库安装相同的文件。 在Ubuntu的存储库中,客户端库被称为Let's Encrypt开发人员提供的certbot 。 但是我们将选择前一种安装方法,即通过克隆Let's Encrypt的Github存储库。
To do that, navigate to your chosen installation folder and clone the repository. I have chosen the installation folder as /usr/local, you can choose some other folder as per your environment.
为此,请导航到您选择的安装文件夹并克隆存储库。 我已将安装文件夹选择为/usr/local ,您可以根据环境选择其他文件夹。
# apt-get install git
# cd /usr/local
# git clone https://github.com/letsencrypt/letsencryptChange to the letsencrypt folder, you will find all the cloned folders and files including certbot needed by Let’s encrypt to fetch certificates for you.
转到letsencrypt文件夹,您将找到所有克隆的文件夹和文件,包括让我们进行加密以获取证书所需的certbot。
List Lets Encrypt Folder
列表允许加密文件夹
配置“让我们加密”以验证您的域 (Configure Let’s Encrypt to verify your domain)
In the process of fetching a certificate, the Let’s Encrypt client creates a temporary file in .well-known/acme-challenge folder. This file contains a token to validate the fact that you actually own the domain for which you are trying to fetch the certificates. Remember the said folder falls under the web root of the domain.
在获取证书的过程中,Let's Encrypt客户端在.well-known/acme-challenge文件夹中创建一个临时文件。 该文件包含一个令牌,用于验证您实际上拥有要为其获取证书的域的事实。 请记住,上述文件夹位于域的Web根目录下。
Therefore, it is imperative that Let’s Encrypt can access the temporary file to verify the domain. To grant access, you need to configure NGINX since it is the owner of the web root for the domain. Add a location block specifically for the folder /.well-known/acme-challenge that will allow Let’s Encrypt to place a token for domain verification. To do that, Edit the NGINX configuration file for your virtual host. Don’t forget to adjust the root folder as per your environment.
因此,“加密”功能必须能够访问临时文件以验证域。 要授予访问权限,您需要配置NGINX,因为它是域的Web根目录的所有者。 添加专门用于/.well-known/acme-challenge文件夹的位置块,该位置块将允许我们进行加密以放置域验证令牌。 为此,请为您的虚拟主机编辑NGINX配置文件。 不要忘记根据您的环境调整根文件夹。
server {
listen 80;
server_name SUBDOMAIN.DOMAIN.TLD;
root /var/www/html/wordpress;
...
...
...
location /.well-known/acme-challenge {
allow all;
default_type "text/plain";
}
...
...
}Verify that the configuration file is syntactically correct and restart NGINX:
验证配置文件在语法上是否正确,然后重新启动NGINX:
# nginx -t
# systemctl restart nginx配置UFW防火墙 (Configure UFW Firewall)
Ubuntu 18.04 is shipped with a default firewall manager UFW and if you have already enabled it and is running in your server then no HTTP or HTTPS connections will be allowed to reach the NGINX server.
Ubuntu 18.04附带了默认的防火墙管理器UFW,如果已经启用它并且在服务器中运行,则不允许HTTP或HTTPS连接访问NGINX服务器。
It is also possible that you are trying to install certificates on a previously configured server and the firewall rules are already present. Of course, you can list the firewall rules using ufw status command in your server before proceeding with enabling HTTP and HTTPS connections in your Ubuntu 18.04 server.
您也可能尝试在以前配置的服务器上安装证书,并且防火墙规则已经存在。 当然,您可以在服务器中使用ufw status命令列出防火墙规则,然后再在Ubuntu 18.04服务器中启用HTTP和HTTPS连接。
Run the following set of commands in the terminal to allow HTTP and HTTPS connections in your server.
在终端中运行以下命令集,以允许服务器中的HTTP和HTTPS连接。
# ufw status
# ufw allow http
# ufw allow https
# ufw reload请求让我们加密SSL证书 (Request Let’s Encrypt SSL Certificate)
Let us request an SSL certificate for the chosen domain using the Let’s Encrypt client that we cloned previously. Although there are a lot of configuration options available that one can use with Let’s Encrypt script while requesting a certificate, we will use the following options only.
让我们使用之前克隆的“加密加密”客户端请求所选域的SSL证书。 尽管有许多可用的配置选项,可以在请求证书时与Let's Encrypt脚本一起使用,但我们将仅使用以下选项。
- certonly: This option tells the letsencrypt script to obtain the SSL certificate only. We will do the configuration of NGINX manually later. certonly :此选项告诉letencrypt脚本仅获取SSL证书。 稍后我们将手动进行NGINX的配置。
- webroot: This option specifies webroot plugin to be used in the process of validating the domain name. webroot :此选项指定在验证域名的过程中使用的webroot插件。
- webroot-path: This option sets the root of the domain and must be pointed to website location that you have configured in the NGINX configuration. webroot-path :此选项设置域的根,并且必须指向您在NGINX配置中配置的网站位置。
- agree-tos: Means agree to the Let’s Encrypt’s terms of service. 同意 :表示同意Let's Encrypt的服务条款。
- email: The email is used to receive expiry notice from Let’s Encrypt but can also be used to recover the lost key. email :电子邮件用于从Let's Encrypt接收到期通知,但也可以用于恢复丢失的密钥。
- d: This options specifies the domain name for which certificate will be requested. d :此选项指定要为其请求证书的域名。
Now combining the above options along with letsencrypt client script, request for a certificate using following commands:
现在将上述选项与letencrypt客户端脚本结合在一起,使用以下命令来请求证书:
# cd /usr/local/letsencrypt
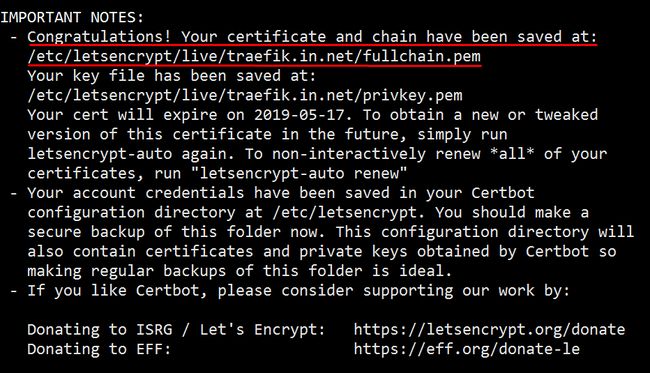
# ./letsencrypt-auto certonly --agree-tos --email [email protected] --webroot --webroot-path /var/www/html/wordpress -d SUBDOMAIN.DOMAIN.TLDThe Let’s Encrypt script will show you a small note once the SSL certificates have been fetched successfully and the certificates will get stored in the /etc/letsencrypt/live folder.
成功获取SSL证书后,Let's Encrypt脚本将为您显示一条小提示,并且证书将存储在/etc/letsencrypt/live文件夹中。
配置NGINX以让我们加密SSL证书 (Configure NGINX for Let’s Encrypt SSL Certificate)
At this stage, the Let’s Encrypt certificate chain has been saved successfully in your server. Now proceed with configuring virtual host file for a secured SSL enabled NGINX web server.
在此阶段,“加密加密”证书链已成功保存在您的服务器中。 现在继续为启用SSL的NGINX Web服务器配置虚拟主机文件。
生成Diffie-Hellman密钥 (Generate Diffie-Hellman Key)
Although using Diffie-Hellman key is optional while configuring Let’s Encrypt certificates with NGINX but it is primarily used as a method of exchanging cryptography keys securely for use in the Let’s encrypt certificate.
尽管在使用NGINX配置Let's Encrypt证书时使用Diffie-Hellman密钥是可选的,但是它主要用作安全地交换加密密钥的方法,以用于Let's加密证书中。
# mkdir -p /etc/nginx/ssl
# cd /etc/nginx/ssl
# openssl dhparam -out /etc/nginx/ssl/dhparam.pem 4096I have placed DH parameter file in the /etc/nginx/ssl directory simply for convenience. You can place the file in some other location.
为了方便起见,我将DH参数文件放在/etc/nginx/ssl目录中。 您可以将文件放置在其他位置。
配置SSL参数 (Configure SSL parameters)
Next, add parameters for SSL connection like protocol versions, cipher suites, session, headers that your server should support in a separate file.
接下来,在单独的文件中添加SSL连接的参数,例如协议版本,密码套件,会话,服务器应支持的标头。
This will set up a strong cipher suite that enables Forward Secrecy whenever possible. Further, we will also enable HSTS and HPKP to harden NGINX server for SSL connections. This will enable a strong and future proof SSL configuration to get an A+ grade on the Qualys Labs SSL Test.
这将建立一个强大的密码套件,该套件在可能的情况下启用前向保密。 此外,我们还将使HSTS和HPKP能够加强NGINX服务器的SSL连接。 这将使一个强大的,可用于未来的SSL配置在Qualys Labs SSL Test上获得A +等级。
# vi /etc/nginx/conf.d/ssl.conf
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:ECDHE-RSA-AES128-GCM-SHA256:AES256+EECDH:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
ssl_dhparam /etc/nginx/ssl/dhparam.pem;
server_tokens off;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
#Online Certificate Status Protocol Stapling
ssl_stapling on;
ssl_stapling_verify on;
ssl_session_tickets off;
#HTTP Strict Transport Security
add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload";
ssl_trusted_certificate /etc/letsencrypt/live/SUBDOMAIN.DOMAIN.TLD/chain.pem;
resolver 8.8.8.8 8.8.4.4 valid=300s;
resolver_timeout 5s;
add_header X-Frame-Options DENY;
add_header X-XSS-Protection "1; mode=block";
add_header X-Content-Type-Options nosniff;
add_header X-Robots-Tag none;编辑NGINX虚拟主机 (Edit NGINX virtual host)
Finally, edit the NGINX server blocks for your chosen domain. Navigate to the default location for NGINX server blocks which is /etc/nginx/sites-available and edit the NGINX virtual host file.
最后,为您选择的域编辑NGINX服务器块。 导航到NGINX服务器块的默认位置/etc/nginx/sites-available然后编辑NGINX虚拟主机文件。
# vi /etc/nginx/sites-available/your_nginx_file.conf
server {
listen 80;
listen [::]:80;
server_name SUBDOMAIN.DOMAIN.TLD;
return 301 https://$host$request_uri;
}
...
...The above server block instructs NGINX to listen for any incoming request in the port 80 for the domain SUBDOMAIN.DOMAIN.TLD and redirect the same to the https section, the configuration for which is given below.
上面的服务器块指示NGINX侦听端口80中域SUBDOMAIN.DOMAIN.TLD任何传入请求,并将其重定向到https部分,其配置如下。
...
...
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
root /var/www/html/wordpress;
index index.html index.php index.htm;
server_name SUBDOMAIN.DOMAIN.TLD;
error_log /var/log/nginx/SUBDOMAIN.DOMAIN.TLD-error.log debug;
access_log /var/log/nginx/SUBDOMAIN.DOMAIN.TLD-access.log;
ssl_certificate /etc/letsencrypt/live/SUBDOMAIN.DOMAIN.TLD/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/SUBDOMAIN.DOMAIN.TLD/privkey.pem;
include /etc/nginx/conf.d/ssl.conf;
location /.well-known/acme-challenge {
allow all;
default_type "text/plain";
}
location / {
try_files $uri $uri/ =404;
}
location = /favicon.ico {
log_not_found off;
access_log off;
}
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
location ~* \.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}Check the configuration file for any syntactical error:
检查配置文件中是否存在语法错误:
# nginx -tTo activate the server block create a symbolic link of the above virtual host configuration file inside /etc/nginx/sites-enabled folder.
要激活服务器块,请在/etc/nginx/sites-enabled文件夹中创建上述虚拟主机配置文件的符号链接。
# cd /etc/nginx/sites-enabled
# ln -s ../sites-available/your_nginx_file.conf .Reload NGINX to apply new settings:
重新加载NGINX以应用新设置:
# systemctl reload nginxTo analyze the configuration of above SSL settings, point your browser to SSL Labs Test and type in your domain name and click ‘Submit’. Wait for a minute to view the summary of the test. An A+ rating means, we have included most of the SSL options in the process of securing the NGINX server.
要分析上述SSL设置的配置,请将浏览器指向SSL Labs Test,然后输入域名,然后单击“提交”。 等待一分钟以查看测试摘要。 A +评级意味着,在保护NGINX服务器安全的过程中,我们已包括了大多数SSL选项。
自动更新Let's Encrypt证书 (Auto renewal of Let’s Encrypt certificate)
The Let’s Encrypt certificates are valid for 90 days. The rationale for this is to limit the damage from key compromise and encourage automation.
Let's Encrypt证书的有效期为90天。 这样做的理由是为了限制关键妥协所造成的损害并鼓励自动化。
To automate the certificate renewal process, create a cronjob using crontab and add a line of script that will execute once every week to renew the certificates when they are about to expire.
要自动执行证书更新过程,请使用crontab创建一个cronjob并添加一行脚本,该脚本每周执行一次,以在证书即将到期时进行更新。
# crontab -e
45 4 * * 6 cd /usr/local/letsencrypt/ && ./certbot-auto renew && systemctl restart nginxThe above single line script will run in every Saturday to check if certificates are up for renewal and if it so, it will renew the certificates followed by restarting of NGINX server.
上面的单行脚本将在每个星期六运行,以检查是否可以更新证书,如果可以,它将更新证书,然后重新启动NGINX服务器。
Note that it’s not fully optimized because the NGINX server will get restarted even if the certificate is not renewed. The best option would be to write a custom script to renew the SSL certificate and restart NGINX server if the certificates are actually renewed.
请注意,它还没有完全优化,因为即使不更新证书,NGINX服务器也会重新启动。 最好的选择是编写一个自定义脚本来续订SSL证书,如果实际已续订证书,则重新启动NGINX服务器。
结论 (Conclusion)
In this article, we learned how to install Let’s Encrypt client library, request a certificate for your domain and how to configure Let’s Encrypt SSL certificates with NGINX. Further, An example cronjob also shows you how to take care of the certificate renewal process regularly.
在本文中,我们学习了如何安装Let's Encrypt客户端库,为您的域请求证书以及如何使用NGINX配置Let's Encrypt SSL证书。 此外,示例cronjob还向您显示了如何定期维护证书更新过程。
翻译自: https://www.journaldev.com/25906/nginx-lets-encrypt-ssl-certificate
nginx ssl加密