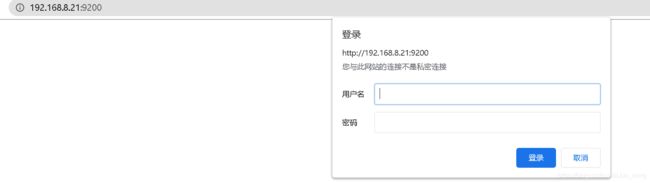
elasticsearch集群未授权访问漏洞,设置用户登录认证
elasticsearch集群未授权访问漏洞,设置用户登录认证
ES安装步骤省略
1.节点上生成认证文件 ca证书
[elasticsearch@pgdb-es1 bin]$
[elasticsearch@pgdb-es1 bin]$ ./elasticsearch-certutil ca
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by org.bouncycastle.jcajce.provider.drbg.DRBG (file:/opt/elasticsearch-7.2.0/lib/tools/security-cli/bcprov-jdk15on-1.61.jar) to constructor sun.security.provider.Sun()
WARNING: Please consider reporting this to the maintainers of org.bouncycastle.jcajce.provider.drbg.DRBG
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'ca' mode generates a new 'certificate authority'
This will create a new X.509 certificate and private key that can be used
to sign certificate when running in 'cert' mode.
Use the 'ca-dn' option if you wish to configure the 'distinguished name'
of the certificate authority
By default the 'ca' mode produces a single PKCS#12 output file which holds:
* The CA certificate
* The CA's private key
If you elect to generate PEM format certificates (the -pem option), then the output will
be a zip file containing individual files for the CA certificate and private key
Please enter the desired output file [elastic-stack-ca.p12]: ---直接回车
Enter password for elastic-stack-ca.p12 : ---直接回车
[elasticsearch@pgdb-es1 bin]$
2.生产新文件elastic-stack-ca.p12
[elasticsearch@pgdb-es1 bin]$ cd ..
[elasticsearch@pgdb-es1 elasticsearch-7.2.0]$ ll -lrt
total 552
-rw-r--r--. 1 elasticsearch elasticsearch 8478 Jun 20 2019 README.textile
-rw-r--r--. 1 elasticsearch elasticsearch 13675 Jun 20 2019 LICENSE.txt
drwxr-xr-x. 2 elasticsearch elasticsearch 4096 Jun 20 2019 plugins
-rw-r--r--. 1 elasticsearch elasticsearch 502598 Jun 20 2019 NOTICE.txt
drwxr-xr-x. 3 elasticsearch elasticsearch 4096 Jun 20 2019 lib
drwxr-xr-x. 8 elasticsearch elasticsearch 4096 Jun 20 2019 jdk
drwxr-xr-x. 2 elasticsearch elasticsearch 4096 Jun 20 2019 bin
drwxr-xr-x. 30 elasticsearch elasticsearch 4096 Jun 20 2019 modules
drwxr-xr-x. 2 elasticsearch elasticsearch 4096 Aug 27 2020 config
drwxr-xr-x. 2 elasticsearch elasticsearch 4096 Apr 26 13:37 logs
-rw------- 1 elasticsearch elasticsearch 2527 Apr 26 13:47 elastic-stack-ca.p12
[elasticsearch@pgdb-es1 elasticsearch-7.2.0]$
3. 使用第一步生成的证书,生成p12秘钥 (三步回车)
[elasticsearch@pgdb-es1 bin]$
[elasticsearch@pgdb-es1 bin]$ ./elasticsearch-certutil cert --ca elastic-stack-ca.p12
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by org.bouncycastle.jcajce.provider.drbg.DRBG (file:/opt/elasticsearch-7.2.0/lib/tools/security-cli/bcprov-jdk15on-1.61.jar) to constructor sun.security.provider.Sun()
WARNING: Please consider reporting this to the maintainers of org.bouncycastle.jcajce.provider.drbg.DRBG
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
The 'cert' mode generates X.509 certificate and private keys.
* By default, this generates a single certificate and key for use
on a single instance.
* The '-multiple' option will prompt you to enter details for multiple
instances and will generate a certificate and key for each one
* The '-in' option allows for the certificate generation to be automated by describing
the details of each instance in a YAML file
* An instance is any piece of the Elastic Stack that requires a SSL certificate.
Depending on your configuration, Elasticsearch, Logstash, Kibana, and Beats
may all require a certificate and private key.
* The minimum required value for each instance is a name. This can simply be the
hostname, which will be used as the Common Name of the certificate. A full
distinguished name may also be used.
* A filename value may be required for each instance. This is necessary when the
name would result in an invalid file or directory name. The name provided here
is used as the directory name (within the zip) and the prefix for the key and
certificate files. The filename is required if you are prompted and the name
is not displayed in the prompt.
* IP addresses and DNS names are optional. Multiple values can be specified as a
comma separated string. If no IP addresses or DNS names are provided, you may
disable hostname verification in your SSL configuration.
* All certificates generated by this tool will be signed by a certificate authority (CA).
* The tool can automatically generate a new CA for you, or you can provide your own with the
-ca or -ca-cert command line options.
By default the 'cert' mode produces a single PKCS#12 output file which holds:
* The instance certificate
* The private key for the instance certificate
* The CA certificate
If you specify any of the following options:
* -pem (PEM formatted output)
* -keep-ca-key (retain generated CA key)
* -multiple (generate multiple certificates)
* -in (generate certificates from an input file)
then the output will be be a zip file containing individual certificate/key files
Enter password for CA (elastic-stack-ca.p12) :
Please enter the desired output file [elastic-certificates.p12]:
Enter password for elastic-certificates.p12 :
Certificates written to /opt/elasticsearch-7.2.0/elastic-certificates.p12
This file should be properly secured as it contains the private key for
your instance.
This file is a self contained file and can be copied and used 'as is'
For each Elastic product that you wish to configure, you should copy
this '.p12' file to the relevant configuration directory
and then follow the SSL configuration instructions in the product guide.
For client applications, you may only need to copy the CA certificate and
configure the client to trust this certificate.
[elasticsearch@pgdb-es1 bin]$
拷贝p12秘钥文件
[elasticsearch@pgdb-es1 config]$
[elasticsearch@pgdb-es1 config]$ mkdir certs
[elasticsearch@pgdb-es1 config]$
[elasticsearch@pgdb-es1 config]$ cp ../elastic-certificates.p12 ./certs/
[elasticsearch@pgdb-es1 config]$
4.将p12秘钥文件拷贝到节点
节点上conf下创建mkdir certs目录
scp [email protected]:/opt/elasticsearch-7.2.0/config/certs/* ./certs/
5.修改es配置文件添加如下参数配置
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: certs/elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: certs/elastic-certificates.p12
6.重启ES
./bin/elasticsearch -d
7.设置密码:
想要成功设置密码的话,必须确保集群状态正常才行,否则密码设置会失败。在其中一个节点就可以。
[elasticsearch@pgdb-es1 bin]$ ./elasticsearch-setup-passwords interactive
Initiating the setup of passwords for reserved users elastic,apm_system,kibana,logstash_system,beats_system,remote_monitoring_user.
You will be prompted to enter passwords as the process progresses.
Please confirm that you would like to continue [y/N]y
Enter password for [elastic]:
passwords must be at least [6] characters long
Try again.
Enter password for [elastic]:
passwords must be at least [6] characters long
Try again.
Enter password for [elastic]:
Reenter password for [elastic]:
Enter password for [apm_system]:
Reenter password for [apm_system]:
Enter password for [kibana]:
Reenter password for [kibana]:
Enter password for [logstash_system]:
Reenter password for [logstash_system]:
Enter password for [beats_system]:
Reenter password for [beats_system]:
Enter password for [remote_monitoring_user]:
Reenter password for [remote_monitoring_user]:
Changed password for user [apm_system]
Changed password for user [kibana]
Changed password for user [logstash_system]
Changed password for user [beats_system]
Changed password for user [remote_monitoring_user]
Changed password for user [elastic]
[elasticsearch@pgdb-es1 bin]$
8.设置kibana用户密码
修改kiban配置文件添加
elasticsearch.username: "kibana"
elasticsearch.password: "123456"
注意:使用kibana用户登录后报错: {"statusCode":403,"error":"Forbidden","message":"Forbidden"}
可用超级用户elastic登录进行创建用户或修改权限
9.验证
分别访问ES和kibana需要输入用户密码访问
9.设置密码head访问异常无法连接集群:
解决方式在访问地址加上用户密码:
http://192.168.8.20:9100/?auth_user=elastic&auth_password=123456