Harbor私有仓库搭建
Harbor 是由 VMware 公司中国团队为企业用户设计的 Registry server 开源项目,包括了权限管理(RBAC)、LDAP、审计、管理界面、自我注册、HA 等企业必需的功能,同时针对中国用户的特点,设计镜像复制和中文支持等功能。
![]()
作为一个企业级私有 Registry 服务器,Harbor 提供了更好的性能和安全。提升用户使用 Registry 构建和运行环境传输镜像的效率。Harbor 支持安装在多个 Registry 节点的镜像资源复制,镜像全部保存在私有 Registry 中, 确保数据和知识产权在公司内部网络中管控。另外,Harbor 也提供了高级的安全特性,诸如用户管理,访问控制和活动审计等。
- 基于角色的访问控制 - 用户与 Docker 镜像仓库通过“项目”进行组织管理,一个用户可以对多个镜像仓库在同一命名空间(project)里有不同的权限。
- 镜像复制 - 镜像可以在多个 Registry 实例中复制(同步)。尤其适合于负载均衡,高可用,混合云和多云的场景。
- 图形化用户界面 - 用户可以通过浏览器来浏览,检索当前 Docker 镜像仓库,管理项目和命名空间。
- AD/LDAP 支持 - Harbor 可以集成企业内部已有的 AD/LDAP,用于鉴权认证管理。
- 审计管理 - 所有针对镜像仓库的操作都可以被记录追溯,用于审计管理。
- 国际化 - 已拥有英文、中文、德文、日文和俄文的本地化版本。更多的语言将会添加进来。
- RESTful API - RESTful API 提供给管理员对于 Harbor 更多的操控, 使得与其它管理软件集成变得更容易。
- 部署简单 - 提供在线和离线两种安装工具, 也可以安装到 vSphere 平台(OVA 方式)虚拟设备。
1、下载安装包后解压
tar -xf harbor-offline-installer-v2.6.0.tgz -C /opt
cd /opt
mv harbor harbor-v2.6.0
ln -s harbor-v2.6.0 harbor2、生成证书
mkdir /etc/certs && cd /etc/certs
openssl genrsa -out ca.key 4096
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=BeijingYJHZ/L=BeijingYJHZ/O=example/OU=Personal/CN=192.168.175.111" \
-key ca.key \
-out ca.crt
#生成服务器证书
openssl genrsa -out 192.168.175.111.key 4096
openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=BeijingYJHZ/O=example/OU=Personal/CN=192.168.175.111" \
-key 192.168.175.111.key \
-out 192.168.175.111.csr
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = IP:192.168.175.111
EOF
#使用该v3.ext文件为您的Harbor主机生成证书
openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in 192.168.175.111.csr \
-out 192.168.175.111.crt.转换192.168.175.111.crt为192.168.175.111.cert,供Docker使用 Docker守护程序将.crt文件解释为CA证书,并将.cert文件解释为客户端
openssl x509 -inform PEM -in 192.168.175.111.crt -out 192.168.175.111.cert3.将服务器证书,密钥和CA文件复制到Harbor主机上的Docker certificate文件夹中。您必须首先创建适当的文件夹,客户端都需要这些文件, 有哪些服务器是要通过docker 去访问harbor的都需要创建下面的目录,并且目录的ip名称不变,都是harbor的ip
mkdir -p /etc/docker/certs.d/192.168.175.111/
cp 192.168.175.111.cert /etc/docker/certs.d/192.168.175.111/
cp 192.168.175.111.key /etc/docker/certs.d/192.168.175.111/
cp ca.crt /etc/docker/certs.d/192.168.175.111/3、配置harbor.yml
cd /opt/harbor
cp harbor.yml.tmpl harbor.yml
vim /opt/harbor/harbor.yml
hostname: 192.168.175.111
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 1800
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /etc/certs/192.168.175.111.crt
private_key: /etc/certs/192.168.175.111.key
harbor_admin_password: harboradmin
data_volume: /data/harbor/data
log:
local:
location: /data/harbor/log4、创建目录
mkdir -p /data/harbor/data
mkdir -p /data/harbor/log5、安装 docker-compose依赖包
yum install docker-compose -y
或者已经下载了docker-compose-linux-x86_64安装文件的
cp docker-compose-linux-x86_64 /usr/local/bin/docker-compose
chmod +x /usr/local/bin/docker-compose
docker-compose version6、安装harbor
cd /opt/harbor
./install.sh#安装后如果有修改配置,就用下面命令重新加载配置
./prepare
7、查看运行状态
[root@localhost harbor]# docker-compose ps
NAME COMMAND SERVICE STATUS PORTS
harbor-core "/harbor/entrypoint.…" core running (healthy)
harbor-db "/docker-entrypoint.…" postgresql running (healthy)
harbor-jobservice "/harbor/entrypoint.…" jobservice running (healthy)
harbor-log "/bin/sh -c /usr/loc…" log running (healthy) 127.0.0.1:1514->10514/tcp
harbor-portal "nginx -g 'daemon of…" portal running (healthy)
nginx "nginx -g 'daemon of…" proxy running (healthy) 0.0.0.0:1800->8080/tcp, :::1800->8080/tcp, 0.0.0.0:443->8443/tcp, :::443->8443/tcp
redis "redis-server /etc/r…" redis running (healthy)
registry "/home/harbor/entryp…" registry running (healthy)
registryctl "/home/harbor/start.…" registryctl running (healthy)
[root@localhost harbor]#2.docker 添加仓库地址
在两台文件服务器的docker中添添加harbor地址
vim /etc/docker/daemon.json
{
"graph": "/data/docker",
"storage-driver": "overlay2",
"insecure-registries": ["http://192.168.175.111:1800"],
"registry-mirrors": [
"https://q2gr04k2.mirror.aliyuncs.com"],
"exec-opts": ["native.cgroupdriver=systemd"],
"bip": "172.7.21.1/24",
"live-restore": true
}
systemctl daemon-reload
systemctl restart docker验证是否能登录harbor,如果最后打印Login Succeeded 表示登录成功
root@localhost harbor]# docker login 192.168.175.111:1800
Username: admin
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded其他访问网站:https://192.168.175.111:1800 看是否能正常登录(浏览器用谷歌,ie可能打不开)
常用命令
docker-compose down ----停止并卸载harbor服务
docker-compose up -d ----启动harbor服务
3.4验证推送镜像
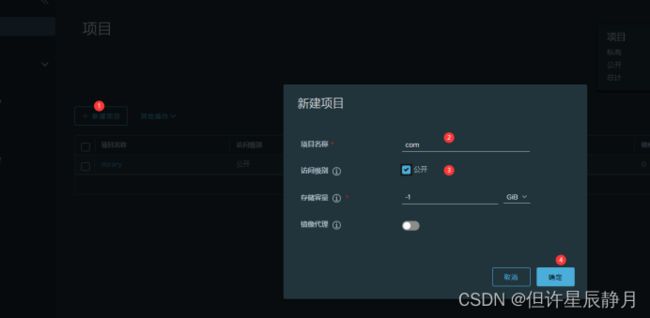
创建一个com 的项目。
#下载一个镜像,如
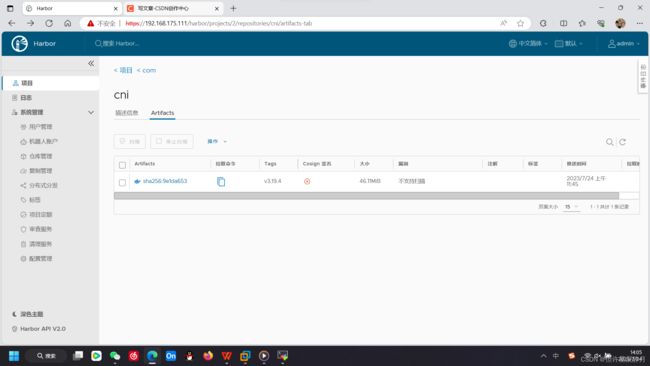
docker pull docker.io/calico/cni:v3.19.4
docker tag docker.io/calico/cni:v3.19.4 192.168.175.111:1800/com/cni:v3.19.4
docker push 192.168.175.111:1800/com/cni:v3.19.4如果能推送成功,在harbor网站中能看到,表示harbor的安装配置都正常。