ARP请求拦截及响应
一、前言
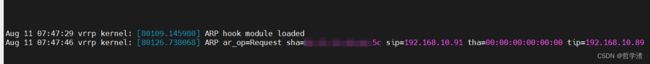
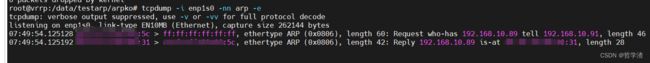
本文主要是介绍如何对arp请求包进行拦截,并代替系统进行响应。对arp请求进行拦截,需要在驱动中进行,具体代码如下文所示。(本文仅供参考)
二、环境
OS Ubuntu 20.04.6 LTS
Linux ubuntu 5.15.0-71-generic
三、源码
驱动代码如下(arp_hook.c):
#include Makefile如下:
# Makefile for driver
KDIR := /lib/modules/$(shell uname -r)/build
PWD := $(shell pwd)
obj-m += arp_hook.o
all: driver
driver:
$(MAKE) -C $(KDIR) M=$(PWD) modules
clean:
$(MAKE) -C $(KDIR) M=$(PWD) clean
运行结果:
其它:
加载驱动命令:insmod arp_hook.ko
卸载驱动命令:remod arp_hook
查看驱动是否已经加载:lsmod | grep arp_hook
linux日志查看:tail -f /var/log/syslog
arp表查看命令:arp -a