如何创建一个rootapp
1.先安装iosOpendev,详见(iOS之逆向学习之 iOSOpendev安装)
2.创建一个原生app工程
3.点击+号 Add User-defined settings,添加iOSOpenDev配置项,最主要的是添加CODE_SIGNING_ALLOWED为NO,关闭签名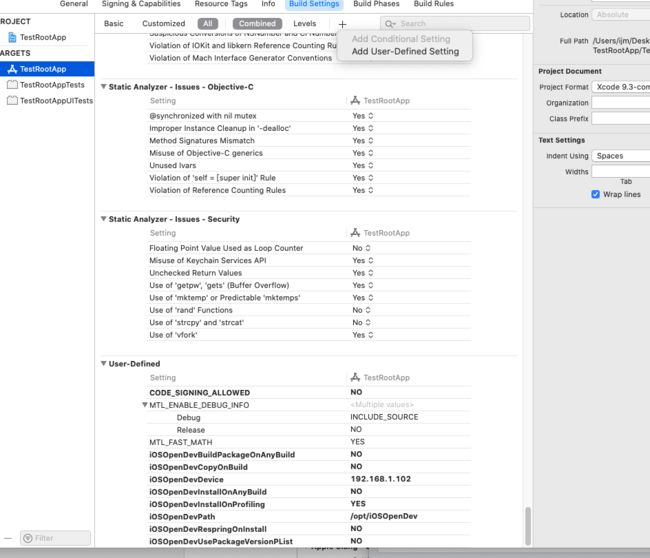
4.还要手动设置证书为空,Targets-->buildSetting里搜索sign,@1 将Code Signing Identity设置为空 @2设置Code Signning Entitlements为本地的entitlements

entitlements内容为:
platform-application
com.apple.private.mobileinstall.allowedSPI
Lookup
Install
Browse
Uninstall
LookupForLaunchServices
InstallForLaunchServices
BrowseForLaunchServices
UninstallForLaunchServices
CopyDiskUsageForLaunchServices
InstallLocalProvisioned
com.apple.private.security.no-container
com.apple.private.skip-library-validation
com.apple.lsapplicationworkspace.rebuildappdatabases
com.apple.private.MobileContainerManager.allowed
com.apple.private.MobileGestalt.AllowedProtectedKeys
com.apple.managedconfiguration.profiled-access
run-unsigned-code
dynamic-codesigning
get-task-allow
iOS15 palera1n越狱的entitlements为:
platform-application
com.apple.private.security.no-container
com.apple.private.security.no-sandbox
com.apple.springboard.launchapplications
com.apple.springboard.debugapplications
get-task-allow
proc_info-allow
task_for_pid-allow
run-unsigned-code
com.apple.QuartzCore.global-capture
com.apple.avfoundation.allow-still-image-capture-shutter-sound-manipulation
com.apple.private.hid.client.event-dispatch
com.apple.private.hid.client.event-filter
com.apple.private.hid.manager.client
com.apple.private.hid.client.service-protected
com.apple.QuartzCore.displayable-context
com.apple.QuartzCore.secure-capture
com.apple.QuartzCore.secure-mode
com.apple.imagent
com.apple.imagent.av
com.apple.CommCenter.fine-grained
spi
com.apple.private.lockdown.finegrained-set
NULL/DeviceName
com.apple.coretelephony.Identity.get
com.apple.lsapplicationworkspace.rebuildappdatabases
com.apple.private.allow-explicit-graphics-priority
com.apple.security.iokit-user-client-class
AGXCommandQueue
AGXDevice
AGXDeviceUserClient
AGXSharedUserClient
AppleCredentialManagerUserClient
AppleJPEGDriverUserClient
ApplePPMUserClient
AppleSPUHIDDeviceUserClient
AppleSPUHIDDriverUserClient
IOAccelContext
IOAccelContext2
IOAccelDevice
IOAccelDevice2
IOAccelSharedUserClient
IOAccelSharedUserClient2
IOAccelSubmitter2
IOHIDEventServiceFastPathUserClient
IOHIDLibUserClient
IOMobileFramebufferUserClient
IOReportUserClient
IOSurfaceAcceleratorClient
IOSurfaceRootUserClient
RootDomainUserClient
com.apple.private.MobileContainerManager.allowed
com.apple.managedconfiguration.profiled-access
com.apple.private.MobileGestalt.AllowedProtectedKeys
com.apple.private.mobileinstall.allowedSPI
Lookup
Install
Browse
Uninstall
LookupForLaunchServices
InstallForLaunchServices
BrowseForLaunchServices
UninstallForLaunchServices
CopyDiskUsageForLaunchServices
InstallLocalProvisioned
PS:iOS15 palera1n越狱的权限有所不同,不然会崩溃,要设置Code Signing Identity、Development Team为有值,而不是None和空,具体如图所示
5.在工程目录下创建一个Package目录,在其下创建Applications和DEBIAN两个文件夹,DEBIAN下创建prerm 、postinst、preinst、postrm、control三个文件
prerm:该脚本负责停止与软件包相关联的daemon服务。它在删除软件包关联文件之前执行。内容为:
#!/bin/bash
killall -9 TestRootApp > /dev/null
postinst
该脚本的主要任务是完成安装包时的配置工作。许多“postinst”脚本负责执行有关命令为新安装或升级的软件重启服务。内容为:
#!/bin/bash
get_ios_ver()
{
OSVERLINE=`grep -n 'ProductVersion' /System/Library/CoreServices/SystemVersion.plist | sed 's/:.*//'`
((OSVERLINE+=1))
OSVER=`cat /System/Library/CoreServices/SystemVersion.plist | sed -n "${OSVERLINE}p" | sed 's/^.*//' | sed 's/<\/string>.*//'`
echo ${OSVER}
}
#cd "/Applications/TestRootApp.app/"
#
## process origin binary
#mv TestRootApp TestRootApp_
#chown root.wheel TestRootApp_
#chmod +s TestRootApp_
#
#cont=`cat <<"EOF"
##!/bin/bash
#dir=$(dirname "$0")
#exec "${dir}"/TestRootApp_ "$@"
#EOF
#`
## create new fake binary
#echo -e "$cont" > TestRootApp
#chown root.wheel TestRootApp
#chmod +x TestRootApp
echo "Set permission..."
chown -R root:wheel /Applications/TestRootApp.app
chmod -R u=rwx,go=rx /Applications/TestRootApp.app
chmod ug=rwx,o=rx /Applications/TestRootApp.app
chown root:wheel /Applications/TestRootApp.app/TestRootApp /Applications/TestRootApp.app/libs/* /Applications/TestRootApp.app/*.png /Applications/TestRootApp.app/*.plist
chown -R mobile:mobile /private/var/mobile/Media/TestRootApp
iOSVer=`get_ios_ver`
iOSVerArray=(${iOSVer//./ })
iOSVerCount=${#iOSVerArray[*]}
if [[ ${iOSVerCount} > 1 ]]; then
if [[ ${iOSVerArray[0]} == 11 ]]; then
chmod u+s /Applications/TestRootApp.app/TestRootApp
fi
fi
echo "Clean icon cache..."
su -c /usr/bin/uicache mobile > /dev/null
#The RESPRING script after Install
declare -a cydia
cydia=($CYDIA)
if [[ $1 == install || $1 == upgrade ]]; then
if [[ ${CYDIA+@} ]]; then
eval "echo 'finish:restart' >&${cydia[0]}"
fi
fi
exit 0
preinst,在Deb包文件解包之前,将会运行该脚本。许多“preinst”脚本的任务是停止作用于待升级软件包的服务,直到软件包安装或升级完成.内容为:
#!/bin/bash
#echo "Stop IDBScannerTool services..."
#killall -9 SlionDaemon STask IDBScannerTool > /dev/null
echo "Remove old files..."
rm -rf /Applications/IDBScannerTool.app > /dev/null
postrm.该脚本负责修改软件包链接或文件关联,或删除由它创建的文件。内容为:
#!/bin/bash
echo "Clean icon cache..."
su -c /usr/bin/uicache mobile > /dev/null
#rm -rf /Applications/TouchSprite.app
declare -a cydia
cydia=($CYDIA)
if [[ ${CYDIA+@} ]]; then
eval "echo 'finish:respring' >&${cydia[0]}"
else
echo "Please respring your device after this!"
fi
exit 0
control,主要是设置版本号、包名、依赖系统版本
Package: com.xx.crashDemo.TestRootApp
Name: rootApp
Version: 1.0.0
Description:
Section: System
Depends: firmware (>= 5.0)
Conflicts:
Replaces:
Priority: optional
Architecture: iphoneos-arm
Author: XX
dev:
Homepage:
Depiction:
Maintainer:XX
Icon:
6.在RunScript脚本里加上/opt/iOSOpenDev/bin/iosod --xcbp
7.打包,只能通过Profiling方式打包,xcode-->product-->Build For-->Profiling
8.经历7步骤首次打包还没有问题,多次打包之后会报copy 错误,要解决这个要删除工程里的Package/Applications下的.app,可以写一个脚本专门删除这玩意,在RunScript里运行
work_path=$(dirname $0)
cd ${work_path} # 当前位置跳到脚本位置
rm -rf Package/Applications/*
ps: 我用rootapp里面有个网络请求,我发现用un0cover越狱之后,网络请求死活是 the internet connection appears to be offline,这种情况先的确定是代码问题还是网络权限问题,我们随便写一个百度的get请求发现也是报这个错.顺速是网络权限没开.关键我首次打开app的时候,也没弹提示框啊,这就尴尬了,是不是rootapp都不弹这玩意,那咋能有网呢,我也很懵逼啊,越狱真不是人玩的.我在想各大做越狱root app的厂商也可能有这问题啊,于是玩找到了触动精灵的官网官网一顿找,反正就在常见问题和各种问题里一顿找,终于让我知道这个网站https://www.touchsprite.com/docs/4196
于是发现他们教程里要三个系统联网配置文件
rm -rf /private/var/preferences/com.apple.networkextension.plist
rm -rf /private/var/preferences/com.apple.networkextensioncache.plist
rm -rf /private/var/preferences/com.apple.networkextension.necp.plist
killall -9 SpringBoard真正试验发现只在iOS14上有效果(我只有13、14的机型),在iOS13没效果,我查了半天试了下面方式:
rm -rf /private/var/preferences/com.apple.networkextension.plist
killall -9 CommCenter为了兼容就写成
rm -rf /private/var/preferences/com.apple.networkextension.plist
rm -rf /private/var/preferences/com.apple.networkextensioncache.plist
rm -rf /private/var/preferences/com.apple.networkextension.necp.plist
killall -9 CommCenter
killall -9 SpringBoard本文章引用https://www.touchsprite.com/docs/4196、https://juejin.cn/post/6844904202045489159
