编译CentOS6.10系统的OpenSSHV9.4rpm安装包
目前OpenSSH版本已至9.4,其作为操作系统底层管理平台软件,需要保持更新以免遭受安全攻击,编译生成rpm包是生产环境中批量升级的最佳途径。编译软件包时与当前的运行环境有较大关系,请注意本安装包系在CentOS6.10原生系统纯净系统下编译完成的。
一、准备编译环境:
1、发布一台虚拟机,最小化安装CentOS6.10,查看系统信息如下:
[root@localhost ~]# cat /etc/redhat-release
CentOS release 6.10 (Final)2、查看系统所带openssl的版本信息:
[root@localhost ~]# rpm -qa|grep openssh
openssh-5.3p1-123.el6_9.x86_64
openssh-server-5.3p1-123.el6_9.x86_64
[root@localhost ~]# rpm -qa|grep openssl
openssl-1.0.1e-57.el6.x86_643、修改系统源为阿里源:
[root@localhost ~]# cd /etc/yum.repos.d/
[root@localhost yum.repos.d]# rm CentOS-* -rf
[root@localhost yum.repos.d]# vi http.repo
[root@localhost yum.repos.d]# cat http.repo
[os]
name=os
baseurl=https://mirrors.aliyun.com/centos-vault/6.10/os/x86_64/
gpgcheck=0
enabled=1
[root@localhost yum.repos.d]# cd ~
[root@localhost ~]# yum repolist
已加载插件:fastestmirror
Determining fastest mirrors
os | 3.7 kB 00:00
os/primary_db | 4.7 MB 00:04
仓库标识 仓库名称 状态
os os 6,713
repolist: 6,713
4、准备相关目录及工具
[root@localhost ~]# cd ~
[root@localhost ~]# mkdir -p rpmbuild/{SOURCES,SPECS}
[root@localhost ~]# yum install wget tree -y
已加载插件:fastestmirror
设置安装进程
Loading mirror speeds from cached hostfile
解决依赖关系
--> 执行事务检查
---> Package tree.x86_64 0:1.5.3-3.el6 will be 安装
---> Package wget.x86_64 0:1.12-10.el6 will be 安装
--> 完成依赖关系计算
依赖关系解决
=========================================================================================================================================================
软件包 架构 版本 仓库 大小
=========================================================================================================================================================
正在安装:
tree x86_64 1.5.3-3.el6 os 36 k
wget x86_64 1.12-10.el6 os 484 k
事务概要
=========================================================================================================================================================
Install 2 Package(s)
总下载量:520 k
Installed size: 1.9 M
下载软件包:
(1/2): tree-1.5.3-3.el6.x86_64.rpm | 36 kB 00:00
(2/2): wget-1.12-10.el6.x86_64.rpm | 484 kB 00:00
---------------------------------------------------------------------------------------------------------------------------------------------------------
总计 799 kB/s | 520 kB 00:00
运行 rpm_check_debug
执行事务测试
事务测试成功
执行事务
正在安装 : tree-1.5.3-3.el6.x86_64 1/2
正在安装 : wget-1.12-10.el6.x86_64 2/2
Verifying : wget-1.12-10.el6.x86_64 1/2
Verifying : tree-1.5.3-3.el6.x86_64 2/2
已安装:
tree.x86_64 0:1.5.3-3.el6 wget.x86_64 0:1.12-10.el6
完毕!5、 准备源文件
[root@localhost ~]# cd rpmbuild/SOURCES/
[root@localhost SOURCES]# wget https://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-9.4p1.tar.gz --no-check-certificate
...
2023-09-05 18:33:37 (69.2 KB/s) - 已保存 “openssh-9.4p1.tar.gz” [1845094/1845094])
[root@localhost SOURCES]# wget https://src.fedoraproject.org/repo/pkgs/openssh/x11-ssh-askpass-1.2.4.1.tar.gz/8f2e41f3f7eaa8543a2440454637f3c3/x11-ssh-askpass-1.2.4.1.tar.gz
...
2023-09-05 18:41:14 (114 KB/s) - 已保存 “x11-ssh-askpass-1.2.4.1.tar.gz” [29229/29229])
[root@localhost SOURCES]# wget https://www.openssl.org/source/openssl-1.1.1v.tar.gz --no-check-certificate
...
2023-09-06 21:56:18 (901 KB/s) - 已保存 “openssl-1.1.1v.tar.gz” [9893443/9893443])
[root@localhost SOURCES]# vi sshd.pam.el6
#%PAM-1.0
auth required pam_sepermit.so
auth include password-auth
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session optional pam_keyinit.so force revoke
session include password-auth
"sshd.pam.el6" [New] 13L, 575C written
[root@localhost SOURCES]# cat sshd.pam.el6
#%PAM-1.0
auth required pam_sepermit.so
auth include password-auth
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session optional pam_keyinit.so force revoke
session include password-auth
[root@localhost SOURCES]# ll
总用量 11504
-rw-r--r--. 1 root root 1845094 8月 10 11:15 openssh-9.4p1.tar.gz
-rw-r--r--. 1 root root 9893443 8月 1 22:09 openssl-1.1.1v.tar.gz
-rw-r--r--. 1 root root 575 9月 6 19:38 sshd.pam.el6
-rw-r--r--. 1 root root 29229 6月 26 2004 x11-ssh-askpass-1.2.4.1.tar.gz6、 安装编译工具
[root@localhost SOURCES]# cd ../SPECS
[root@localhost SPECS]# yum install rpm-build zlib-devel openssl-devel gcc perl-devel pam-devel -y
...
已安装:
gcc.x86_64 0:4.4.7-23.el6 openssl-devel.x86_64 0:1.0.1e-57.el6 pam-devel.x86_64 0:1.1.1-24.el6 perl-devel.x86_64 4:5.10.1-144.el6
rpm-build.x86_64 0:4.8.0-59.el6 zlib-devel.x86_64 0:1.2.3-29.el6
作为依赖被安装:
cloog-ppl.x86_64 0:0.15.7-1.2.el6 cpp.x86_64 0:4.4.7-23.el6 db4-cxx.x86_64 0:4.7.25-22.el6
db4-devel.x86_64 0:4.7.25-22.el6 elfutils.x86_64 0:0.164-2.el6 gdb.x86_64 0:7.2-92.el6
gdbm-devel.x86_64 0:1.8.0-39.el6 glibc-devel.x86_64 0:2.12-1.212.el6 glibc-headers.x86_64 0:2.12-1.212.el6
kernel-headers.x86_64 0:2.6.32-754.el6 keyutils-libs-devel.x86_64 0:1.4-5.el6 krb5-devel.x86_64 0:1.10.3-65.el6
libcom_err-devel.x86_64 0:1.41.12-24.el6 libgomp.x86_64 0:4.4.7-23.el6 libkadm5.x86_64 0:1.10.3-65.el6
libselinux-devel.x86_64 0:2.0.94-7.el6 libsepol-devel.x86_64 0:2.0.41-4.el6 mpfr.x86_64 0:2.4.1-6.el6
patch.x86_64 0:2.6-8.el6_9 perl.x86_64 4:5.10.1-144.el6 perl-ExtUtils-MakeMaker.x86_64 0:6.55-144.el6
perl-ExtUtils-ParseXS.x86_64 1:2.2003.0-144.el6 perl-Module-Pluggable.x86_64 1:3.90-144.el6 perl-Pod-Escapes.x86_64 1:1.04-144.el6
perl-Pod-Simple.x86_64 1:3.13-144.el6 perl-Test-Harness.x86_64 0:3.17-144.el6 perl-libs.x86_64 4:5.10.1-144.el6
perl-version.x86_64 3:0.77-144.el6 ppl.x86_64 0:0.10.2-11.el6 redhat-rpm-config.noarch 0:9.0.3-51.el6.centos
unzip.x86_64 0:6.0-5.el6 xz.x86_64 0:4.999.9-0.5.beta.20091007git.el6 xz-lzma-compat.x86_64 0:4.999.9-0.5.beta.20091007git.el6
完毕!7、 生成源spec文件
[root@localhost SPECS]# vi openssh.spec
[root@localhost SPECS]# cat openssh.spec
%{?!opensslver: %global opensslver 1.1.1v}
%{?!opensshver: %global opensshver 9.4p1}
%define static_openssl 1
# wheather to build openssl
%global no_build_openssl 0
#if defined openssl_dir, don't build it
%{?openssl_dir:%global no_build_openssl 1}
%global ver %{?opensshver}
%global rel %{?opensshpkgrel}%{?dist}
# OpenSSH privilege separation requires a user & group ID
%global sshd_uid 74
%global sshd_gid 74
# Version of ssh-askpass
%global aversion 1.2.4.1
# Do we want to disable building of x11-askpass? (1=yes 0=no)
%global no_x11_askpass 1
# Do we want to disable building of gnome-askpass? (1=yes 0=no)
%global no_gnome_askpass 1
# Do we want to link against a static libcrypto? (1=yes 0=no)
%global static_libcrypto 0
# Do we want smartcard support (1=yes 0=no)
%global scard 0
# Use GTK2 instead of GNOME in gnome-ssh-askpass
%global gtk2 1
# Use build6x options for older RHEL builds
# RHEL 7 not yet supported
%if 0%{?rhel} > 6
%global build6x 0
%else
%global build6x 1
%endif
%if 0%{?fedora} >= 26
%global compat_openssl 1
%else
%global compat_openssl 0
%endif
# Do we want kerberos5 support (1=yes 0=no)
%global kerberos5 1
# Reserve options to override askpass settings with:
# rpm -ba|--rebuild --define 'skip_xxx 1'
%{?skip_x11_askpass:%global no_x11_askpass 1}
%{?skip_gnome_askpass:%global no_gnome_askpass 1}
# Add option to build without GTK2 for older platforms with only GTK+.
# RedHat <= 7.2 and Red Hat Advanced Server 2.1 are examples.
# rpm -ba|--rebuild --define 'no_gtk2 1'
%{?no_gtk2:%global gtk2 0}
# Is this a build for RHL 6.x or earlier?
%{?build_6x:%global build6x 1}
# If this is RHL 6.x, the default configuration has sysconfdir in /usr/etc.
%if %{build6x}
%global _sysconfdir /etc
%endif
# Options for static OpenSSL link:
# rpm -ba|--rebuild --define "static_openssl 1"
%{?static_openssl:%global static_libcrypto 1}
# Options for Smartcard support: (needs libsectok and openssl-engine)
# rpm -ba|--rebuild --define "smartcard 1"
%{?smartcard:%global scard 1}
# Is this a build for the rescue CD (without PAM, with MD5)? (1=yes 0=no)
%global rescue 0
%{?build_rescue:%global rescue 1}
# Turn off some stuff for resuce builds
%if %{rescue}
%global kerberos5 0
%endif
Summary: The OpenSSH implementation of SSH protocol version 2.
Name: openssh
Version: %{ver}
%if %{rescue}
Release: %{rel}rescue
%else
Release: %{rel}
%endif
URL: https://www.openssh.com/portable.html
Source0: https://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-%{version}.tar.gz
Source1: http://www.jmknoble.net/software/x11-ssh-askpass/x11-ssh-askpass-%{aversion}.tar.gz
Source2: sshd.pam.el6
%if ! %{no_build_openssl}
Source3: https://www.openssl.org/source/openssl-%{opensslver}.tar.gz
%endif
License: BSD
Group: Applications/Internet
BuildRoot: %{_tmppath}/%{name}-%{version}-buildroot
Obsoletes: ssh
%if %{build6x}
PreReq: initscripts >= 5.00
%else
Requires: initscripts >= 5.20
%endif
BuildRequires: perl
#%if %{compat_openssl}
#BuildRequires: compat-openssl10-devel
#%else
#BuildRequires: openssl-devel >= 1.0.1
#BuildRequires: openssl-devel < 1.1
#%endif
BuildRequires: /bin/login
%if ! %{build6x}
BuildRequires: glibc-devel, pam
%else
BuildRequires: /usr/include/security/pam_appl.h
%endif
%if ! %{no_x11_askpass}
BuildRequires: /usr/include/X11/Xlib.h
# Xt development tools
BuildRequires: libXt-devel
# Provides xmkmf
BuildRequires: imake
# Rely on relatively recent gtk
%if %{gtk2}
BuildRequires: gtk2-devel
%endif
%endif
%if ! %{no_gnome_askpass}
BuildRequires: pkgconfig
%endif
%if %{kerberos5}
BuildRequires: krb5-devel
BuildRequires: krb5-libs
%endif
%package clients
Summary: OpenSSH clients.
Requires: openssh = %{version}-%{release}
Group: Applications/Internet
Obsoletes: ssh-clients
%package server
Summary: The OpenSSH server daemon.
Group: System Environment/Daemons
Obsoletes: ssh-server
Requires: openssh = %{version}-%{release}, chkconfig >= 0.9
%if ! %{build6x}
Requires: /etc/pam.d/system-auth
%endif
%package askpass
Summary: A passphrase dialog for OpenSSH and X.
Group: Applications/Internet
Requires: openssh = %{version}-%{release}
Obsoletes: ssh-extras
%package askpass-gnome
Summary: A passphrase dialog for OpenSSH, X, and GNOME.
Group: Applications/Internet
Requires: openssh = %{version}-%{release}
Obsoletes: ssh-extras
%description
SSH (Secure SHell) is a program for logging into and executing
commands on a remote machine. SSH is intended to replace rlogin and
rsh, and to provide secure encrypted communications between two
untrusted hosts over an insecure network. X11 connections and
arbitrary TCP/IP ports can also be forwarded over the secure channel.
OpenSSH is OpenBSD's version of the last free version of SSH, bringing
it up to date in terms of security and features, as well as removing
all patented algorithms to separate libraries.
This package includes the core files necessary for both the OpenSSH
client and server. To make this package useful, you should also
install openssh-clients, openssh-server, or both.
%description clients
OpenSSH is a free version of SSH (Secure SHell), a program for logging
into and executing commands on a remote machine. This package includes
the clients necessary to make encrypted connections to SSH servers.
You'll also need to install the openssh package on OpenSSH clients.
%description server
OpenSSH is a free version of SSH (Secure SHell), a program for logging
into and executing commands on a remote machine. This package contains
the secure shell daemon (sshd). The sshd daemon allows SSH clients to
securely connect to your SSH server. You also need to have the openssh
package installed.
%description askpass
OpenSSH is a free version of SSH (Secure SHell), a program for logging
into and executing commands on a remote machine. This package contains
an X11 passphrase dialog for OpenSSH.
%description askpass-gnome
OpenSSH is a free version of SSH (Secure SHell), a program for logging
into and executing commands on a remote machine. This package contains
an X11 passphrase dialog for OpenSSH and the GNOME GUI desktop
environment.
%prep
%if ! %{no_x11_askpass}
%setup -q -a 1
%else
%setup -q
%endif
%if ! %{no_build_openssl}
%define openssl_dir %{_builddir}/%{name}-%{version}/openssl
mkdir -p openssl
tar xfz %{SOURCE3} --strip-components=1 -C openssl
pushd openssl
./config shared zlib -fPIC
make %{?_smp_mflags}
popd
%endif
%build
%if %{rescue}
CFLAGS="$RPM_OPT_FLAGS -Os"; export CFLAGS
%endif
export LD_LIBRARY_PATH="%{openssl_dir}"
%configure \
--sysconfdir=%{_sysconfdir}/ssh \
--libexecdir=%{_libexecdir}/openssh \
--datadir=%{_datadir}/openssh \
--with-default-path=/usr/local/bin:/bin:/usr/bin \
--with-superuser-path=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin \
--with-privsep-path=%{_var}/empty/sshd \
--with-md5-passwords \
--mandir=%{_mandir} \
--with-mantype=man \
--disable-strip \
--with-ssl-dir="%{openssl_dir}" \
%if %{scard}
--with-smartcard \
%endif
%if %{rescue}
--without-pam \
%else
--with-pam \
%endif
%if %{kerberos5}
--with-kerberos5=$K5DIR \
%endif
%if %{static_libcrypto}
#perl -pi -e "s|-lcrypto|%{_libdir}/libcrypto.a|g" Makefile
perl -pi -e "s|-lcrypto|%{openssl_dir}/libcrypto.a -lpthread|g" Makefile
%endif
make %{?_smp_mflags}
%if ! %{no_x11_askpass}
pushd x11-ssh-askpass-%{aversion}
%configure --libexecdir=%{_libexecdir}/openssh
xmkmf -a
make -j
popd
%endif
# Define a variable to toggle gnome1/gtk2 building. This is necessary
# because RPM doesn't handle nested %if statements.
%if %{gtk2}
gtk2=yes
%else
gtk2=no
%endif
%if ! %{no_gnome_askpass}
pushd contrib
if [ $gtk2 = yes ] ; then
make gnome-ssh-askpass2
mv gnome-ssh-askpass2 gnome-ssh-askpass
else
make gnome-ssh-askpass1
mv gnome-ssh-askpass1 gnome-ssh-askpass
fi
popd
%endif
%install
rm -rf $RPM_BUILD_ROOT
mkdir -p -m755 $RPM_BUILD_ROOT%{_sysconfdir}/ssh
mkdir -p -m755 $RPM_BUILD_ROOT%{_libexecdir}/openssh
mkdir -p -m755 $RPM_BUILD_ROOT%{_var}/empty/sshd
make install DESTDIR=$RPM_BUILD_ROOT
echo -e 'PubkeyAcceptedAlgorithms +ssh-rsa\nUsePAM yes\nPermitRootLogin yes\nUseDNS no' >> $RPM_BUILD_ROOT/etc/ssh/sshd_config
install -d $RPM_BUILD_ROOT/etc/pam.d/
install -d $RPM_BUILD_ROOT/etc/rc.d/init.d
install -d $RPM_BUILD_ROOT%{_libexecdir}/openssh
install -m755 contrib/ssh-copy-id $RPM_BUILD_ROOT/usr/bin/ssh-copy-id
install -m644 %{SOURCE2} $RPM_BUILD_ROOT/etc/pam.d/sshd
install -m755 contrib/redhat/sshd.init $RPM_BUILD_ROOT/etc/rc.d/init.d/sshd
%if ! %{no_x11_askpass}
install x11-ssh-askpass-%{aversion}/x11-ssh-askpass $RPM_BUILD_ROOT%{_libexecdir}/openssh/x11-ssh-askpass
ln -s x11-ssh-askpass $RPM_BUILD_ROOT%{_libexecdir}/openssh/ssh-askpass
%endif
%if ! %{no_gnome_askpass}
install contrib/gnome-ssh-askpass $RPM_BUILD_ROOT%{_libexecdir}/openssh/gnome-ssh-askpass
%endif
%if ! %{scard}
rm -f $RPM_BUILD_ROOT/usr/share/openssh/Ssh.bin
%endif
%if ! %{no_gnome_askpass}
install -m 755 -d $RPM_BUILD_ROOT%{_sysconfdir}/profile.d/
install -m 755 contrib/redhat/gnome-ssh-askpass.csh $RPM_BUILD_ROOT%{_sysconfdir}/profile.d/
install -m 755 contrib/redhat/gnome-ssh-askpass.sh $RPM_BUILD_ROOT%{_sysconfdir}/profile.d/
%endif
perl -pi -e "s|$RPM_BUILD_ROOT||g" $RPM_BUILD_ROOT%{_mandir}/man*/*
%clean
rm -rf $RPM_BUILD_ROOT
%triggerun server -- ssh-server
if [ "$1" != 0 -a -r /var/run/sshd.pid ] ; then
touch /var/run/sshd.restart
fi
%triggerun server -- openssh-server < 2.5.0p1
# Count the number of HostKey and HostDsaKey statements we have.
gawk 'BEGIN {IGNORECASE=1}
/^hostkey/ || /^hostdsakey/ {sawhostkey = sawhostkey + 1}
END {exit sawhostkey}' /etc/ssh/sshd_config
# And if we only found one, we know the client was relying on the old default
# behavior, which loaded the the SSH2 DSA host key when HostDsaKey wasn't
# specified. Now that HostKey is used for both SSH1 and SSH2 keys, specifying
# one nullifies the default, which would have loaded both.
if [ $? -eq 1 ] ; then
echo HostKey /etc/ssh/ssh_host_rsa_key >> /etc/ssh/sshd_config
echo HostKey /etc/ssh/ssh_host_dsa_key >> /etc/ssh/sshd_config
fi
%triggerpostun server -- ssh-server
if [ "$1" != 0 ] ; then
/sbin/chkconfig --add sshd
if test -f /var/run/sshd.restart ; then
rm -f /var/run/sshd.restart
/sbin/service sshd start > /dev/null 2>&1 || :
fi
fi
%pre server
%{_sbindir}/groupadd -r -g %{sshd_gid} sshd 2>/dev/null || :
%{_sbindir}/useradd -d /var/empty/sshd -s /bin/false -u %{sshd_uid} \
-g sshd -M -r sshd 2>/dev/null || :
%post server
/sbin/chkconfig --add sshd
%postun server
/sbin/service sshd condrestart > /dev/null 2>&1 || :
%preun server
if [ "$1" = 0 ]
then
/sbin/service sshd stop > /dev/null 2>&1 || :
/sbin/chkconfig --del sshd
fi
%files
%defattr(-,root,root)
%doc CREDITS ChangeLog INSTALL LICENCE OVERVIEW README* PROTOCOL* TODO
%attr(0755,root,root) %{_bindir}/scp
%attr(0644,root,root) %{_mandir}/man1/scp.1*
%attr(0755,root,root) %dir %{_sysconfdir}/ssh
%attr(0600,root,root) %config(noreplace) %{_sysconfdir}/ssh/moduli
%if ! %{rescue}
%attr(0755,root,root) %{_bindir}/ssh-keygen
%attr(0755,root,root) %{_bindir}/ssh-copy-id
%attr(0644,root,root) %{_mandir}/man1/ssh-keygen.1*
%attr(0755,root,root) %dir %{_libexecdir}/openssh
%attr(4711,root,root) %{_libexecdir}/openssh/ssh-keysign
%attr(0755,root,root) %{_libexecdir}/openssh/ssh-pkcs11-helper
%attr(0755,root,root) %{_libexecdir}/openssh/ssh-sk-helper
%attr(0644,root,root) %{_mandir}/man8/ssh-keysign.8*
%attr(0644,root,root) %{_mandir}/man8/ssh-pkcs11-helper.8*
%attr(0644,root,root) %{_mandir}/man8/ssh-sk-helper.8*
%endif
%if %{scard}
%attr(0755,root,root) %dir %{_datadir}/openssh
%attr(0644,root,root) %{_datadir}/openssh/Ssh.bin
%endif
%files clients
%defattr(-,root,root)
%attr(0755,root,root) %{_bindir}/ssh
%attr(0644,root,root) %{_mandir}/man1/ssh.1*
%attr(0644,root,root) %{_mandir}/man5/ssh_config.5*
%attr(0644,root,root) %config(noreplace) %{_sysconfdir}/ssh/ssh_config
%if ! %{rescue}
%attr(2755,root,nobody) %{_bindir}/ssh-agent
%attr(0755,root,root) %{_bindir}/ssh-add
%attr(0755,root,root) %{_bindir}/ssh-keyscan
%attr(0755,root,root) %{_bindir}/sftp
%attr(0644,root,root) %{_mandir}/man1/ssh-agent.1*
%attr(0644,root,root) %{_mandir}/man1/ssh-add.1*
%attr(0644,root,root) %{_mandir}/man1/ssh-keyscan.1*
%attr(0644,root,root) %{_mandir}/man1/sftp.1*
%endif
%if ! %{rescue}
%files server
%defattr(-,root,root)
%dir %attr(0111,root,root) %{_var}/empty/sshd
%attr(0755,root,root) %{_sbindir}/sshd
%attr(0755,root,root) %{_libexecdir}/openssh/sftp-server
%attr(0644,root,root) %{_mandir}/man8/sshd.8*
%attr(0644,root,root) %{_mandir}/man5/moduli.5*
%attr(0644,root,root) %{_mandir}/man5/sshd_config.5*
%attr(0644,root,root) %{_mandir}/man8/sftp-server.8*
%attr(0755,root,root) %dir %{_sysconfdir}/ssh
%attr(0600,root,root) %config(noreplace) %{_sysconfdir}/ssh/sshd_config
%attr(0600,root,root) %config(noreplace) /etc/pam.d/sshd
%attr(0755,root,root) %config /etc/rc.d/init.d/sshd
%endif
%if ! %{no_x11_askpass}
%files askpass
%defattr(-,root,root)
%doc x11-ssh-askpass-%{aversion}/README
%doc x11-ssh-askpass-%{aversion}/ChangeLog
%doc x11-ssh-askpass-%{aversion}/SshAskpass*.ad
%{_libexecdir}/openssh/ssh-askpass
%attr(0755,root,root) %{_libexecdir}/openssh/x11-ssh-askpass
%endif
%if ! %{no_gnome_askpass}
%files askpass-gnome
%defattr(-,root,root)
%attr(0755,root,root) %config %{_sysconfdir}/profile.d/gnome-ssh-askpass.*
%attr(0755,root,root) %{_libexecdir}/openssh/gnome-ssh-askpass
%endif
[root@localhost SPECS]# 二、编译
1、编译
[root@localhost SPECS]# rpmbuild -bb openssh.spec
warning: line 108: prereq is deprecated: PreReq: initscripts >= 5.00
Executing(%prep): /bin/sh -e /var/tmp/rpm-tmp.zWPwaj
+ umask 022
+ cd /root/rpmbuild/BUILD
+ LANG=C
+ export LANG
+ unset DISPLAY
+ cd /root/rpmbuild/BUILD
+ rm -rf openssh-9.4p1
+ /bin/tar -xf -
+ /usr/bin/gzip -dc /root/rpmbuild/SOURCES/openssh-9.4p1.tar.gz
+ STATUS=0
+ '[' 0 -ne 0 ']'
+ cd openssh-9.4p1
...
Obsoletes: ssh-server
Processing files: openssh-debuginfo-9.4p1-.el6.x86_64
Checking for unpackaged file(s): /usr/lib/rpm/check-files /root/rpmbuild/BUILDROOT/openssh-9.4p1-.el6.x86_64
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-9.4p1-.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-clients-9.4p1-.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-server-9.4p1-.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-debuginfo-9.4p1-.el6.x86_64.rpm
Executing(%clean): /bin/sh -e /var/tmp/rpm-tmp.qcMTW9
+ umask 022
+ cd /root/rpmbuild/BUILD
+ cd openssh-9.4p1
+ rm -rf /root/rpmbuild/BUILDROOT/openssh-9.4p1-.el6.x86_64
+ exit 0
[root@localhost SPECS]#看到“+ exit 0”表示编译成功。
三、测试验证
1、安装新编译的openssh RPM包
[root@localhost SPECS]# cd /root/rpmbuild/RPMS/x86_64/
[root@localhost x86_64]# ll
总用量 15132
-rw-r--r--. 1 root root 4817808 9月 6 19:58 openssh-9.4p1-.el6.x86_64.rpm
-rw-r--r--. 1 root root 4849872 9月 6 19:58 openssh-clients-9.4p1-.el6.x86_64.rpm
-rw-r--r--. 1 root root 4362628 9月 6 19:58 openssh-debuginfo-9.4p1-.el6.x86_64.rpm
-rw-r--r--. 1 root root 1451744 9月 6 19:58 openssh-server-9.4p1-.el6.x86_64.rpm
[root@localhost x86_64]# yum install *
已加载插件:fastestmirror
设置安装进程
诊断 openssh-9.4p1-.el6.x86_64.rpm: openssh-9.4p1-.el6.x86_64
openssh-9.4p1-.el6.x86_64.rpm 将作为 openssh-5.3p1-123.el6_9.x86_64 的更新
Loading mirror speeds from cached hostfile
诊断 openssh-clients-9.4p1-.el6.x86_64.rpm: openssh-clients-9.4p1-.el6.x86_64
openssh-clients-9.4p1-.el6.x86_64.rpm 将被安装
诊断 openssh-debuginfo-9.4p1-.el6.x86_64.rpm: openssh-debuginfo-9.4p1-.el6.x86_64
openssh-debuginfo-9.4p1-.el6.x86_64.rpm 将被安装
诊断 openssh-server-9.4p1-.el6.x86_64.rpm: openssh-server-9.4p1-.el6.x86_64
openssh-server-9.4p1-.el6.x86_64.rpm 将作为 openssh-server-5.3p1-123.el6_9.x86_64 的更新
解决依赖关系
--> 执行事务检查
---> Package openssh.x86_64 0:5.3p1-123.el6_9 will be 升级
---> Package openssh.x86_64 0:9.4p1-.el6 will be an update
---> Package openssh-clients.x86_64 0:9.4p1-.el6 will be 安装
---> Package openssh-debuginfo.x86_64 0:9.4p1-.el6 will be 安装
---> Package openssh-server.x86_64 0:5.3p1-123.el6_9 will be 升级
---> Package openssh-server.x86_64 0:9.4p1-.el6 will be an update
--> 完成依赖关系计算
依赖关系解决
=========================================================================================================================================================
软件包 架构 版本 仓库 大小
=========================================================================================================================================================
正在安装:
openssh-clients x86_64 9.4p1-.el6 /openssh-clients-9.4p1-.el6.x86_64 12 M
openssh-debuginfo x86_64 9.4p1-.el6 /openssh-debuginfo-9.4p1-.el6.x86_64 17 M
正在升级:
openssh x86_64 9.4p1-.el6 /openssh-9.4p1-.el6.x86_64 12 M
openssh-server x86_64 9.4p1-.el6 /openssh-server-9.4p1-.el6.x86_64 3.5 M
事务概要
=========================================================================================================================================================
Install 2 Package(s)
Upgrade 2 Package(s)
总文件大小:44 M
确定吗?[y/N]:y
下载软件包:
运行 rpm_check_debug
执行事务测试
事务测试成功
执行事务
正在升级 : openssh-9.4p1-.el6.x86_64 1/6
正在升级 : openssh-server-9.4p1-.el6.x86_64 2/6
正在安装 : openssh-clients-9.4p1-.el6.x86_64 3/6
正在安装 : openssh-debuginfo-9.4p1-.el6.x86_64 4/6
清理 : openssh-server-5.3p1-123.el6_9.x86_64 5/6
清理 : openssh-5.3p1-123.el6_9.x86_64 6/6
Verifying : openssh-debuginfo-9.4p1-.el6.x86_64 1/6
Verifying : openssh-server-9.4p1-.el6.x86_64 2/6
Verifying : openssh-9.4p1-.el6.x86_64 3/6
Verifying : openssh-clients-9.4p1-.el6.x86_64 4/6
Verifying : openssh-5.3p1-123.el6_9.x86_64 5/6
Verifying : openssh-server-5.3p1-123.el6_9.x86_64 6/6
已安装:
openssh-clients.x86_64 0:9.4p1-.el6 openssh-debuginfo.x86_64 0:9.4p1-.el6
更新完毕:
openssh.x86_64 0:9.4p1-.el6 openssh-server.x86_64 0:9.4p1-.el6
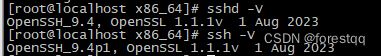
完毕!2、版本验证:
可以将/root/rpmbuild/RPMS/x86_64下的软件包进行拷贝分发或放到http服务器共享。至此,rpm包制作完成。
3、注意事项
openssh升级后加密算法最低要求256位,因此升级openssh后低版本的客户端和CRT都将无法连接,报以下错误:
Key exchange failed.
No compatible key-exchange method. The server supports these methods: [email protected],curve25519-sha256,[email protected],ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256
此时其它未升级openssh的centos6服务器都连不上更新服务器的,不要以为升级失败了,只需将需要连接本服务器的主机的openssh-client也升级了即可。
Windows连接请升级SecureCRT到8.*.*版本,同时会话属性中仅启用256或512位算法,即可正常连接。
可以看到连接是没有任何问题的。