组件漏洞_扫描检测工具
文章目录
-
-
- 一 漏洞检测工具NACS
-
- 1 在对应的目录下进行启动
- 2 启动指令返回漏洞扫描结果
- 3 翻译中文:
- 4 分析后,显示版本及对应的漏洞版本号
- 二 漏洞检测工具weblogicSan
-
- 1 在github中下载最新的2022年
- 2 进行下载
- 3 拉取git进行下载
- 4 使用
-
- 4.1 使用说明
- 4.2 使用指令
- 4.3 如下图下面是+号的表示存在漏洞
- 三 漏洞检测工具nuclei
-
一 漏洞检测工具NACS
1 在对应的目录下进行启动
┌──(kalikali)-[~/tools/nacs/0.0.3/nacs_linux_amd64]
└─$ pwd
/home/kali/tools/nacs/0.0.3/nacs_linux_amd64
┌──(kalikali)-[~/tools/nacs/0.0.3/nacs_linux_amd64]
└─$ ls
nacs output.txt pocs
┌──(kalikali)-[~/tools/nacs/0.0.3/nacs_linux_amd64]
└─$ sudo ./nacs -h 192.168.225.166 -pa 7001 # 启动
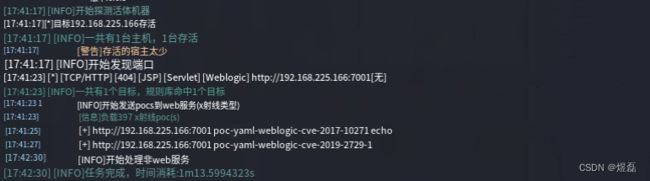
2 启动指令返回漏洞扫描结果
┌──(kalikali)-[~/tools/nacs/0.0.3/nacs_linux_amd64]
└─$ sudo ./nacs -h 192.168.225.166 -pa 7001
_ _ ___ ___ ___
| \| | / \ / __| / __|
| . | | - | | (__ \__ \
|_|\_| |_|_| \___| |___/
Version: 0.0.3
[17:41:17] [INFO] Start to probe alive machines
[17:41:17] [*] Target 192.168.225.166 is alive
[17:41:17] [INFO] There are total of 1 hosts, and 1 are surviving
[17:41:17] [WARNING] Too few surviving hosts
[17:41:17] [INFO] Start to discover the ports
[17:41:23] [*] [TCP/HTTP] [404] [JSP] [Servlet] [Weblogic] http://192.168.225.166:7001 [None]
[17:41:23] [INFO] A total of 1 targets, the rule base hits 1 targets
[17:41:23] [INFO] Start to send pocs to web services (xray type)
[17:41:23] [INFO] Load 397 xray poc(s)
[17:41:25] [+] http://192.168.225.166:7001 poc-yaml-weblogic-cve-2017-10271 echo
[17:41:27] [+] http://192.168.225.166:7001 poc-yaml-weblogic-cve-2019-2729-1
[17:42:30] [INFO] Start to process nonweb services
[17:42:30] [INFO] Task finish, consumption of time: 1m13.5994323s
3 翻译中文:
4 分析后,显示版本及对应的漏洞版本号
二 漏洞检测工具weblogicSan
1 在github中下载最新的2022年
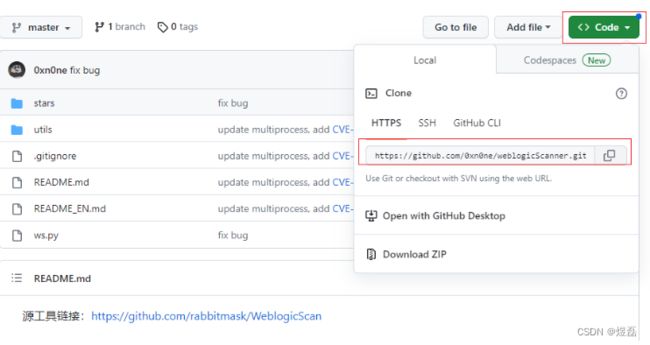
2 进行下载
源工具链接:https://github.com/rabbitmask/WeblogicScan
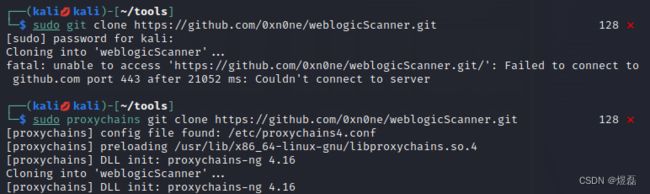
3 拉取git进行下载
┌──(kalikali)-[~/tools]
└─$ sudo git clone https://github.com/0xn0ne/weblogicScanner.git
如下载连接超时使用如下
┌──(kalikali)-[~/tools]
└─$ sudo proxychains git clone https://github.com/0xn0ne/weblogicScanner.git
4 使用
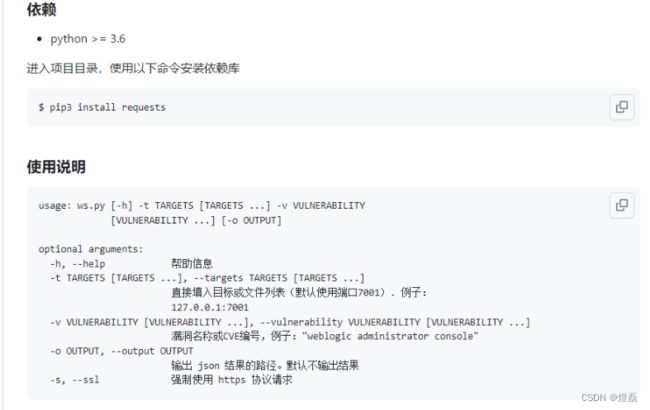
4.1 使用说明
usage: ws.py [-h] -t TARGETS [TARGETS ...] -v VULNERABILITY
[VULNERABILITY ...] [-o OUTPUT]
optional arguments:
-h, --help 帮助信息
-t TARGETS [TARGETS ...], --targets TARGETS [TARGETS ...]
直接填入目标或文件列表(默认使用端口7001). 例子:
127.0.0.1:7001
-v VULNERABILITY [VULNERABILITY ...], --vulnerability VULNERABILITY [VULNERABILITY ...]
漏洞名称或CVE编号,例子:"weblogic administrator console"
-o OUTPUT, --output OUTPUT
输出 json 结果的路径。默认不输出结果
-s, --ssl 强制使用 https 协议请求
4.2 使用指令
┌──(kalikali)-[~/tools/weblogicScanner]
└─$ pwd
/home/kali/tools/weblogicScanner
┌──(kalikali)-[~/tools/weblogicScanner]
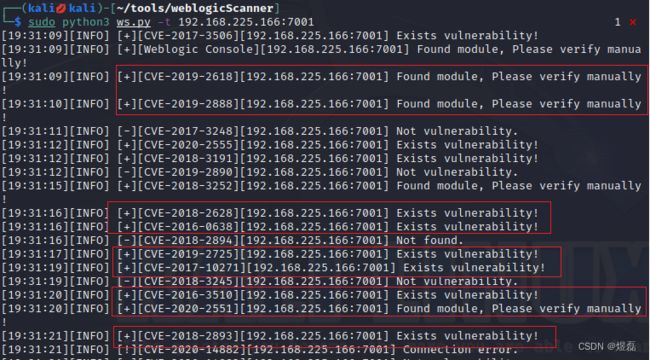
└─$ sudo python3 ws.py -t 192.168.225.166:7001
4.3 如下图下面是+号的表示存在漏洞
三 漏洞检测工具nuclei
cd /home/kali/tools/nuclei/2.9.10
./nuclei # 启动检测
./nuclei --help #帮助文档
./nuclei -up #更新
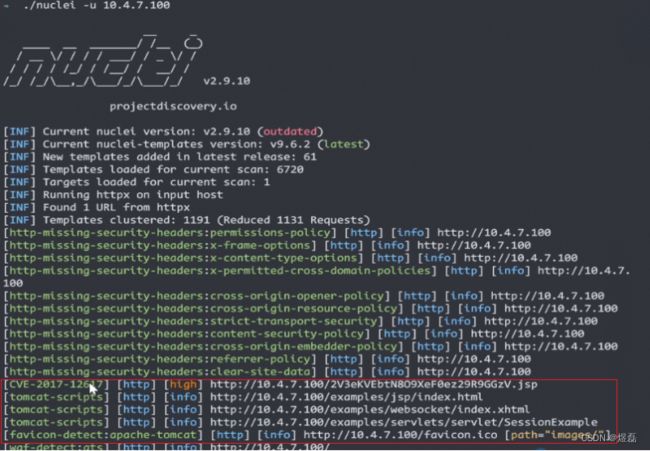
./nuclei -u 192.168.225.166
下图是扫描到的结果