fwknop的安装和使用测试
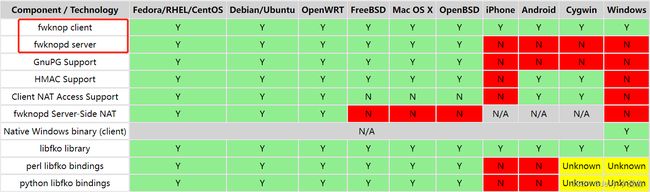
SPA名为单包授权,是一种认证方法,它是一种端口敲门的方法,是之前早起端口敲门的升级版本。目的是为了隐藏服务端口,防止DOS等其他网络攻击,保证服务端的安全。SPA的具体定义这里不细说,网上有太多的资料,此次主要记录SPA的开源软件实现方法fwknop的服务端安装方法和客户端使用方法。我查看了fwknop的服务端支持的os型号有以下几个系统:
其中可以看到,fwknop的server是不支持windows的,所以当你在安装fwknop server的时候,不要去尝试在windows上安装,因为不支持。
1、安装fwknop server
然后就是Linux上安装fwknop server,对于哪个Linux其实方法是一样的,目前基本所有的资料都是源码安装,安装步骤如下所示:
//下载源码
wget http://www.cipherdyne.org/fwknop/download/fwknop-2.6.8.tar.gz
//解压源码
tar -xf fwknop-2.6.8.tar.gz
//编译
cd fwknop-2.6.8/
jelly@DESKTOP-SDB6AM2:~/fwknop/fwknop-2.6.8$ ll
total 1392
-rw-rw-r-- 1 jelly jelly 1787 Dec 24 2015 AUTHORS
-rw-rw-r-- 1 jelly jelly 18002 Dec 24 2015 COPYING
-rw-rw-r-- 1 jelly jelly 11568 Dec 24 2015 CREDITS
-rw-rw-r-- 1 jelly jelly 46595 Dec 24 2015 ChangeLog
-rw-rw-r-- 1 jelly jelly 53256 Dec 24 2015 ChangeLog.git
-rw-rw-r-- 1 jelly jelly 9416 Dec 24 2015 INSTALL
-rw-rw-rw- 1 jelly jelly 48557 Feb 8 15:59 Makefile
-rw-rw-r-- 1 jelly jelly 22349 Dec 24 2015 Makefile.am
-rw-rw-r-- 1 jelly jelly 48199 Dec 24 2015 Makefile.in
-rw-rw-r-- 1 jelly jelly 2409 Dec 24 2015 NEWS
-rw-rw-r-- 1 jelly jelly 15030 Dec 24 2015 README
-rw-rw-r-- 1 jelly jelly 6 Dec 24 2015 VERSION
-rw-rw-r-- 1 jelly jelly 42101 Dec 24 2015 aclocal.m4
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 android
drwxrwxr-x 1 jelly jelly 512 Feb 8 15:59 client
drwxrwxr-x 1 jelly jelly 512 Feb 8 15:59 common
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 config
-rw-rw-rw- 1 jelly jelly 11336 Feb 8 15:59 config.h
-rw-rw-r-- 1 jelly jelly 10684 Dec 24 2015 config.h.in
-rw-rw-rw- 1 jelly jelly 108533 Feb 8 15:59 config.log
-rwxrwxrwx 1 jelly jelly 64403 Feb 8 15:59 config.status
-rwxrwxr-x 1 jelly jelly 551712 Dec 24 2015 configure
-rw-rw-r-- 1 jelly jelly 24240 Dec 24 2015 configure.ac
drwxrwxr-x 1 jelly jelly 512 Feb 8 15:59 doc
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 extras
-rw-rw-r-- 1 jelly jelly 6237 Dec 24 2015 fwknop.spec
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 iphone
drwxrwxr-x 1 jelly jelly 512 Feb 8 15:59 lib
-rwxrwxrwx 1 jelly jelly 293201 Feb 8 15:59 libtool
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 m4
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 perl
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 python
drwxrwxr-x 1 jelly jelly 512 Feb 8 15:59 server
-rw-rw-rw- 1 jelly jelly 23 Feb 8 15:59 stamp-h1
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 test
drwxrwxr-x 1 jelly jelly 512 Dec 24 2015 win32
//安装,如果你的客户端也是Linux,安装的时候去掉--disable-client
./configure --prefix=/usr --sysconfdir=/etc --disable-client
//如果在安装的时候缺少什么包,Ubuntu下直接apt install安装,centos使用yum install安装
make && make install检测是否安装成功
which fwknopd // 查看fwknop的安装路径
fwknopd -V //查看fwknop安装的版本如果出现如下错误
[jelly@localhost fwknop-2.6.8]$ fwknopd -V
fwknopd: error while loading shared libraries: libfko.so.2: cannot open shared object file: No such file or directory
执行下面命令修复这个错误,建立一个软链接为libfko.so.2在lib目录
[jelly@localhost lib64]$ sudo ln -s /usr/lib/libfko.so libfko.so.2
[jelly@localhost ~]$ fwknopd -V
fwknopd server 2.6.8, compiled for firewall bin: /usr/bin/firewall-cmd如果版本能够显示正常就安装完毕了,这个安装方法几乎适用所有的Linux操作系统。
2、安装fwknop client
接下来是安装客户端,先说Linux系统的客户端安装方法,因为安装客户端的方法和安装服务的是步骤完全一致,只是把上面的
./configure --prefix=/usr --sysconfdir=/etc --disable-client改成
./configure --prefix=/usr --sysconfdir=/etc --disable-server其实也可以不加这个--disable-client或者--disable-server,只是客户端和服务端都安装了,仅此而已。如果是windows作为客户端的话,虽然他官网上写了支持,其实是不支持的,官方说的是windows下面的要用fwknop client的话,去用windows下面的cygwin,这个cygwin我看了下,说是windows上虚拟的Linux环境,最后想了想,我还不如用WSL,毕竟win10开始已经支持WSL,而且也比较轻量级。WSL的话,就是Ubuntu子系统,安装方法就和Linux上的源码安装方法一样了,这里就不重复叙述。
3、配置
1)客户端生成秘钥
$ fwknop -A tcp/22 -a 192.168.163.1 -D 192.168.163.129 -p 62201 -P udp --key-gen --use-hmac --save-rc-stanza-a后为客户端ip,-D后面为服务器ip,-p后为服务器监听SPA包的端口,-P后为发送的SPA包的协议,一般采用UDP包。
执行成功后输出如下信息:[+] Wrote Rijndael and HMAC keys to rc file: /home/jelly/.fwknoprc
查看该文件,内容如下:
[192.168.163.129]
SPA_SERVER_PROTO udp
SPA_SERVER_PORT 62201
ALLOW_IP 192.168.163.1
ACCESS tcp/22
SPA_SERVER 192.168.163.129
KEY_BASE64 gqkSa8ghIDlAfv3FDEAdyyMfC6Q+j9RI+BhodFdifok=
HMAC_KEY_BASE64 IPsM8dg8JLaYvRS3UVEoNiuQ9nBu7FB86tOmQyF7HF0+7cT33pxUHAX5zGcYidP5T03zJLR3ejjrJgR1PezLvA==
USE_HMAC Y2)服务端配置设置
编辑sudo vim /etc/fwknop/access.conf文件,修改里面的内容如下:
OPEN_PORTS tcp/22
FW_ACCESS_TIMEOUT 20
SOURCE ANY
#KEY_BASE64 __CHANGEME__
#HMAC_KEY_BASE64 __CHANGEME__
KEY_BASE64 gqkSa8ghIDlAfv3FDEAdyyMfC6Q+j9RI+BhodFdifok=
HMAC_KEY_BASE64 IPsM8dg8JLaYvRS3UVEoNiuQ9nBu7FB86tOmQyF7HF0+7cT33pxUHAX5zGcYidP5T03zJLR3ejjrJgR1PezLvA==里面的两个KEY必须和客户端的保持一致,否则会验证不过。
FW_ACCESS_TIMEOUT设置20表示敲门,门开会保持20s,20s过了以后,门关闭
编辑文件sudo vim /etc/fwknop/fwknopd.conf
内容改为如下:
PCAP_INTF ens33;ens33是用ifconfig命令查出来的网卡名字:
[jelly@localhost ~]$ ifconfig
ens33: flags=4163 mtu 1500
inet 192.168.163.129 netmask 255.255.255.0 broadcast 192.168.163.255
inet6 fe80::37c8:6a00:e56c:9bf5 prefixlen 64 scopeid 0x20
ether 00:0c:29:66:79:23 txqueuelen 1000 (Ethernet)
RX packets 1336 bytes 112165 (109.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1197 bytes 208285 (203.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 19 base 0x2000 3)在服务端启动停止fwknop
[jelly@localhost ~]$ sudo fwknopd start //启动fwknop
[*] An instance of fwknopd is already running: (PID=4196).
[jelly@localhost ~]$
[jelly@localhost ~]$ sudo fwknopd -S //查看fwknop状态
Detected fwknopd is running (pid=4196).
[jelly@localhost ~]$
[jelly@localhost ~]$ sudo kill -9 4196 //关闭fwknop,因为我没找到其他关闭命令,衰4)在服务端打开防火墙,屏蔽22端口
[jelly@localhost ~] $ sudo iptables -I INPUT 1 -i ens33 -p tcp --dport 22 -j DROP
[jelly@localhost ~] $ sudo iptables -I INPUT 1 -i ens33 -p tcp --dport 22 -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT5)在客户端使用敲门命令
$ fwknop -n 192.168.163.1296)查看服务端防火墙状态
[jelly@localhost ~]$ sudo iptables -L
Chain FWKNOP_INPUT (1 references)
target prot opt source destination
ACCEPT tcp -- 192.168.163.1 anywhere tcp dpt:ssh /* _exp_1675933589 */
Chain INPUT_ZONES (1 references)
target prot opt source destination
IN_public all -- anywhere anywhere [goto]
IN_public all -- anywhere anywhere [goto]
Chain INPUT_ZONES_SOURCE (1 references)
target prot opt source destination
Chain INPUT_direct (1 references)
target prot opt source destination
Chain IN_public (2 references)
target prot opt source destination
IN_public_log all -- anywhere anywhere
IN_public_deny all -- anywhere anywhere
IN_public_allow all -- anywhere anywhere
ACCEPT icmp -- anywhere anywhere
Chain IN_public_allow (1 references)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW,UNTRACKED
ACCEPT udp -- anywhere anywhere udp dpt:62201 ctstate NEW,UNTRACKED
Chain IN_public_deny (1 references)
target prot opt source destination
Chain IN_public_log (1 references)
target prot opt source destination
Chain OUTPUT_direct (1 references)
target prot opt source destination门敲开了之后,在上面的第四行可以看到192.168.163.1这个地址已经被允许了,那么我就可以使用ssh连接192.168.163.129了,当你过了20s之后再看,这个192.168.163.1地址已经不允许了,ssh也连不上来了,因为我们敲开的门已经关上了,但是之前已经连接成功的ssh不影响使用。
7)使用命令查看日志
我server使用的是centos,查看日志命令如下,查看最新的20条日志,这个日志包括所有的日志,里面可以看到你fwknop的启动关闭和敲门的日志
[jelly@localhost ~]$ sudo journalctl -n 20
-- Logs begin at Thu 2023-02-09 16:40:02 CST, end at Thu 2023-02-09 17:14:31 CST. --
Feb 09 17:13:40 localhost.localdomain systemd-logind[2269]: Removed session 7.
Feb 09 17:13:44 localhost.localdomain fwknopd[4196]: (stanza #1) SPA Packet from IP: 192.168.163.1 received with access source mat
Feb 09 17:13:45 localhost.localdomain fwknopd[4196]: Added access rule to FWKNOP_INPUT for 192.168.163.1 -> 0.0.0.0/0 tcp/22, expi
Feb 09 17:13:47 localhost.localdomain sshd[6157]: Accepted password for jelly from 192.168.163.1 port 12195 ssh2
Feb 09 17:13:47 localhost.localdomain systemd-logind[2269]: New session 9 of user jelly.
Feb 09 17:13:47 localhost.localdomain systemd[1]: Started Session 9 of user jelly.
Feb 09 17:13:47 localhost.localdomain sshd[6157]: pam_unix(sshd:session): session opened for user jelly by (uid=0)
Feb 09 17:13:47 localhost.localdomain dbus[2274]: [system] Activating service name='org.freedesktop.problems' (using servicehelper
Feb 09 17:13:47 localhost.localdomain dbus[2274]: [system] Successfully activated service 'org.freedesktop.problems'
Feb 09 17:13:50 localhost.localdomain dbus[2274]: [system] Activating via systemd: service name='net.reactivated.Fprint' unit='fpr
Feb 09 17:13:50 localhost.localdomain systemd[1]: Starting Fingerprint Authentication Daemon...
Feb 09 17:13:50 localhost.localdomain dbus[2274]: [system] Successfully activated service 'net.reactivated.Fprint'
Feb 09 17:13:50 localhost.localdomain systemd[1]: Started Fingerprint Authentication Daemon.
Feb 09 17:13:51 localhost.localdomain sudo[6208]: jelly : TTY=pts/0 ; PWD=/home/jelly ; USER=root ; COMMAND=/bin/journalctl -n
Feb 09 17:13:51 localhost.localdomain sudo[6208]: pam_unix(sudo:session): session opened for user root by jelly(uid=0)
Feb 09 17:14:00 localhost.localdomain systemd[1]: Time has been changed
Feb 09 17:14:14 localhost.localdomain fwknopd[4196]: Removed rule 1 from FWKNOP_INPUT with expire time of 1675934054
Feb 09 17:14:28 localhost.localdomain sudo[6208]: pam_unix(sudo:session): session closed for user root
Feb 09 17:14:31 localhost.localdomain sudo[6265]: jelly : TTY=pts/0 ; PWD=/home/jelly ; USER=root ; COMMAND=/bin/journalctl -n
Feb 09 17:14:31 localhost.localdomain sudo[6265]: pam_unix(sudo:session): session opened for user root by jelly(uid=0)备注:当开启防火墙屏蔽端口后,使用扫码端口工具就扫不出来端口了,扫码工具是nmap,Linux上直接install就好,windows有UI的客户端版本,地址:windows的nmap界面版本。
如果是Linux,安装好nmap后直接运行如下命令即可以扫码开放的端口
$nmap -T4 -A -v 192.168.163.129等到扫码完成可以看到地址为192.168.163.129服务器开放的所有端口