全手动搭建Kubernetes集群——部署Dashboard仪表盘
在上一篇文章上一篇文章中,我们已经做好了Master管理节点和Node工作节点部署,现在我们将进行Kubernetes Dashboard的部署。
一、Kubernetes Dashboard
Dashboard是Kubernetes集群的通用的、基于Web的用户界面。它使用户可以部署容器化的应用服务、管理集群中运行的应用程序、监控集群应用的状态、以及集群本身并进行故障排除,对集群中所有的资源进行管控。
二、部署Kubernetes Dashboard
1.配置recommended.yaml文件
recommended.yaml文件的下载链接,提取码:oz7z
下载好直接上传到Linux,然后修改recommended.yaml文件:
[root@k8s-master-1 cfg]# vim recommended.yaml
[root@k8s-master-1 cfg]# cat recommended.yaml
省略输出...
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30007
selector:
k8s-app: kubernetes-dashboard
---
#apiVersion: v1
#kind: Secret
#metadata:
# labels:
# k8s-app: kubernetes-dashboard
# name: kubernetes-dashboard-certs
# namespace: kubernetes-dashboard
#type: Opaque
---
省略输出...
两个关键修改部分的截图:
注释掉以下的内容,注释kubernetes-dashboard-certs对象声明,取消自动生成证书。
2.创建证书
创建命名空间:
[root@k8s-master-1 cfg]# kubectl create namespace kubernetes-dashboard
namespace/kubernetes-dashboard created
创建key文件:
[root@k8s-master-1 cfg]# openssl genrsa -out dashboard.key 2048
Generating RSA private key, 2048 bit long modulus
...........................................+++
........................................................................+++
e is 65537 (0x10001)
证书请求:
[root@k8s-master-1 cfg]# openssl req -days 36000 -new -out dashboard.csr -key dashboard.key -subj '/CN=dashboard-cert'
自签证书:
[root@k8s-master-1 cfg]# openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt
Signature ok
subject=/CN=dashboard-cert
Getting Private key
创建kubernetes-dashboard-certs对象:
[root@k8s-master-1 cfg]# kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard
secret/kubernetes-dashboard-certs created
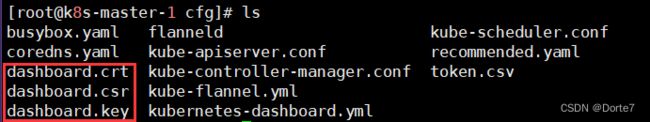
可查看到生成对应的文件:
[root@k8s-master-1 cfg]# ls
busybox.yaml flanneld kube-scheduler.conf
coredns.yaml kube-apiserver.conf recommended.yaml
dashboard.crt kube-controller-manager.conf token.csv
dashboard.csr kube-flannel.yml
dashboard.key kubernetes-dashboard.yml3.安装dashboard
[root@k8s-master-1 cfg]# kubectl create -f recommended.yaml
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
Error from server (AlreadyExists): error when creating "recommended.yaml": namespaces "kubernetes-dashboard" already exists会出现error的报错,可以忽略掉,因为前面的步骤我们已经创建了kubernetes-dashboard的namespace了。
4.查看安装是否成功
[root@k8s-master-1 cfg]# kubectl get pods -A -o wide
NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
default busybox 1/1 Running 12 21d 10.244.0.16 k8s-node-1
default web-5dcb957ccc-t5xpr 1/1 Running 6 21d 10.244.2.25 k8s-node-3
default web2-76fb4f8fd7-lmqvr 0/1 CrashLoopBackOff 17 39h 10.244.1.40 k8s-node-2
kube-system coredns-8686db44f5-67kld 1/1 Running 7 21d 10.244.2.26 k8s-node-3
kube-system kube-flannel-ds-amd64-45z7d 1/1 Running 9 21d 192.168.61.164 k8s-node-3
kube-system kube-flannel-ds-amd64-8xdrs 1/1 Running 11 21d 192.168.61.163 k8s-node-2
kube-system kube-flannel-ds-amd64-9tm4g 1/1 Running 11 21d 192.168.61.162 k8s-node-1
kubernetes-dashboard dashboard-metrics-scraper-6b4884c9d5-rlvcd 1/1 Running 0 2m45s 10.244.0.17 k8s-node-1
kubernetes-dashboard kubernetes-dashboard-7b544877d5-4s67d 1/1 Running 0 2m45s 10.244.1.41 k8s-node-2
[root@k8s-master-1 cfg]# kubectl get service -n kubernetes-dashboard -o wide
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
dashboard-metrics-scraper ClusterIP 10.0.0.44 8000/TCP 4m23s k8s-app=dashboard-metrics-scraper
kubernetes-dashboard NodePort 10.0.0.253 443:30007/TCP 4m24s k8s-app=kubernetes-dashboard
以上查询显示,安装是成功的。
5.配置dashboard-admin.yaml文件,创建dashboard管理员
[root@k8s-master-1 cfg]# vim dashboard-admin.yaml
[root@k8s-master-1 cfg]# cat dashboard-admin.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: dashboard-admin
namespace: kubernetes-dashboard
执行命令:
[root@k8s-master-1 cfg]# kubectl create -f dashboard-admin.yaml
serviceaccount/dashboard-admin created6.给用户分配权限
[root@k8s-master-1 cfg]# vim dashboard-admin-bind-cluster-role.yaml
[root@k8s-master-1 cfg]# cat dashboard-admin-bind-cluster-role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: dashboard-admin-bind-cluster-role
labels:
k8s-app: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kubernetes-dashboard
执行命令:
[root@k8s-master-1 cfg]# kubectl create -f dashboard-admin-bind-cluster-role.yaml
clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin-bind-cluster-role created
7.查看用户token
[root@k8s-master-1 cfg]# kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep dashboard-admin | awk '{print $1}')
Name: dashboard-admin-token-428v8
Namespace: kubernetes-dashboard
Labels:
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: cc7b27ef-5dc2-4b7d-af41-a4424bfad134
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1383 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImkwXzF5UFk4b3JmRDRobmNtMUlST1BPT2JzQ2hwYm9sZXA3UlRSZGQwRTgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tNDI4djgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiY2M3YjI3ZWYtNWRjMi00YjdkLWFmNDEtYTQ0MjRiZmFkMTM0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmRhc2hib2FyZC1hZG1pbiJ9.cFBoGM0dcSxXLfjEY9w0hu4mM0DPQ62wC514bVIilcUNtOlm3Zk3n9H7JDmBc8dPGXZyZJtJkRjQce77ybDBl6b7m5fykFlKYf2gY3LERKzRXMaOlF22ojS6uGLLkXeakOmzJjfZCynA98MtYScEY9D763QxmtD9nL5tjXilWir79MsEkKRyR3Q8mRBG3Oju3GZQcLgBzWpI0aIbyb_5v-F6Yn73JUqLMUOIRrX5PQYGIDeIWm9vUSl10EESYPgx2WT_WOIR_tf-jORoDH-m6PqCzAIFDqUtn1csG_EpQBTVC3GbmAqJiVySTkfWucmDgbyKbDu_hh-G742JoKCDvQ
8.登录Dashboard Web界面
在浏览器输入https://192.168.61.163:3007进行访问,注意用的是https协议。
也可以:https://192.168.61.162:3007和https://192.168.61.164:3007,反正输入node工作节点的IP都行,但是不能用master节点的IP登录。
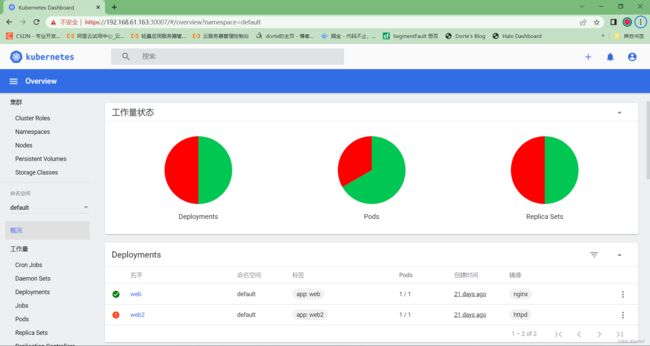
然后输入前面步骤所查询到token密钥,即可登录Dashboard的控制台:
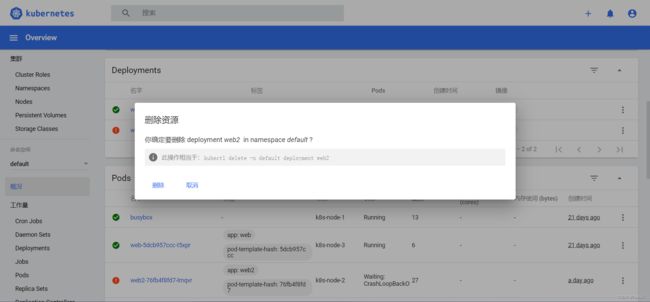
可以简便的进行删除操作:
删除成功:
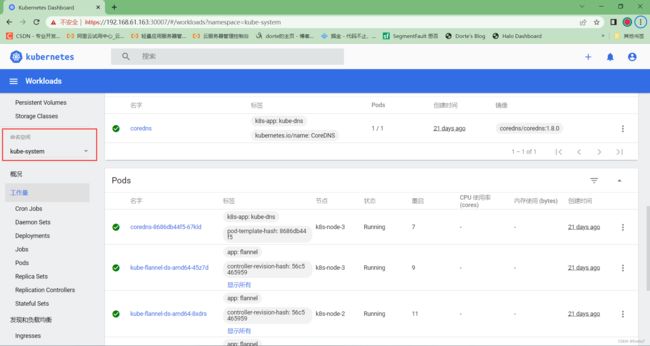
查看Namespaces情况:
以上就是安装Kubernetes Dashboard的内容。