eNSP-实验配置总结-适合入门练手(10.9更)
文章目录
- 一、静态路由配置
- 二、缺省路由和回程路由配置
- 三、浮动静态路由
- 四、NAT配置
- 五、防火墙配置
- 六、浮动路由配置
- 七、OSPF配置
- 八、单臂路由配置
- 九、VLAN间通信(同一CORE)
- 十、CORE与边界ROUTER通信
- 十一、ACL(实现端口控制)
- 十二、telnet远程管理
- 十三、EASY-IP配置
- 十四、DHCP配置(interface模式)
- 十五、DNS配置(PC作为DNS SERVER)
- 十六、VRRP配置(master+backup)
- 十七、防火墙(dmz非军事区)
- 十八、ACL访问控制(配合单臂路由)
- 十九、AAA(telnet远程控制)
- 二十、NAT配置(静态+动态+NAPT)
- 二十一、FTP配置(server-router-client)
!!每个部分下的内容比较多,避免浪费时间翻阅,可以根据目录导向查看指定内容!!
一、静态路由配置
实验拓扑及要求:
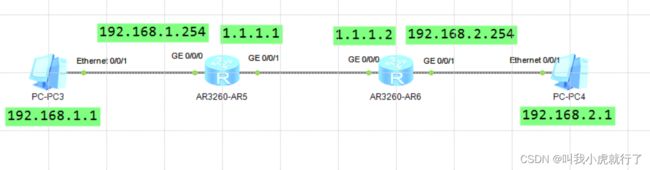
配置过程:
(先按照实验要求把PC的IP和网关给配置完毕,此处PC的设置省略)
(ROUTER的停止信息泛洪和关闭info的设置可以不做)
ROUTER1上:
undo terminal monitor
system-view
[Huawei]sysname ROUTER1
[ROUTER1]undo info-center enable
[ROUTER1]int GigabitEthernet 0/0/0
[ROUTER1-GigabitEthernet0/0/0]ip address 192.168.1.254 24
[ROUTER1-GigabitEthernet0/0/0]q
[ROUTER1]int GigabitEthernet 0/0/1
[ROUTER1-GigabitEthernet0/0/1]ip address 1.1.1.1 24
[ROUTER1-GigabitEthernet0/0/1]q
[ROUTER1]ip route-static 192.168.2.0 24 1.1.1.2
ROUTER2上:
undo terminal monitor
system-view
[Huawei]sysname ROUTER1
[ROUTER1]undo info-center enable
[ROUTER2]int GigabitEthernet 0/0/1
[ROUTER2-GigabitEthernet0/0/1]ip address 192.168.2.254 24
[ROUTER2-GigabitEthernet0/0/1]q
[ROUTER2]int GigabitEthernet 0/0/0
[ROUTER2-GigabitEthernet0/0/0]ip address 1.1.1.2 24
[ROUTER2-GigabitEthernet0/0/0]q
[ROUTER2]ip route-static 192.168.1.0 24 1.1.1.1
(配置完后,可以分别在ROUTER上查看路由信息:ip routing-table)
ps:
以下为比较复杂的静态路由配置(其中包括端口port配置、vlan技术等),调配完基础性配置后才能进行静态路由配置。
实验拓扑及要求:
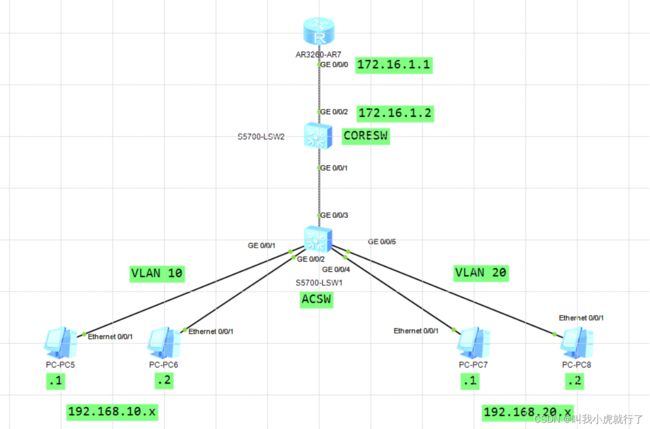 配置过程:
配置过程:
ACSW上:
(此处省略停止泛洪信息和info-ceter信息等配置)
system-view
[Huawei]sysname ACSW
[ACSW]vlan batch 10 20
[ACSW]int GigabitEthernet 0/0/1
[ACSW-GigabitEthernet0/0/1]port link-type access
[ACSW-GigabitEthernet0/0/1]port default vlan 10
[ACSW-GigabitEthernet0/0/1]q
[ACSW]int GigabitEthernet 0/0/2
[ACSW-GigabitEthernet0/0/2]port link-type access
[ACSW-GigabitEthernet0/0/2]port default vlan 10
[ACSW-GigabitEthernet0/0/2]q
[ACSW]int GigabitEthernet 0/0/4
[ACSW-GigabitEthernet0/0/4]port link-type access
[ACSW-GigabitEthernet0/0/4]port default vlan 20
[ACSW-GigabitEthernet0/0/4]q
[ACSW]int GigabitEthernet 0/0/3
[ACSW-GigabitEthernet0/0/3]port link-type trunk
[ACSW-GigabitEthernet0/0/3]port trunk allow-pass vlan all
[ACSW-GigabitEthernet0/0/3]q
CORESW上:
system-view
[Huawei]sysname CORESW
[CORESW]vlan batch 10 20
[CORESW]int GigabitEthernet 0/0/1
[CORESW-GigabitEthernet0/0/1]port link-type trunk
[CORESW-GigabitEthernet0/0/1]port trunk allow-pass vlan all
[CORESW-GigabitEthernet0/0/1]q
[CORESW]int Vlanif 10
[CORESW-Vlanif10]ip address 192.168.1.254 24
[CORESW-Vlanif10]q
[CORESW]int Vlanif 20
[CORESW-Vlanif20]ip address 192.168.2.254 24
[CORESW-Vlanif20]q
[CORESW]int GigabitEthernet 0/0/2
[CORESW-GigabitEthernet0/0/2]port link-type access
[CORESW-GigabitEthernet0/0/2]port default vlan 100
[CORESW-GigabitEthernet0/0/2]q
[CORESW]int Vlanif 100
[CORESW-Vlanif100]ip address 172.16.1.2 24
[CORESW-Vlanif100]q
ROUTER上:
system-view
[Huawei]sysname ROUTER
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]ip address 172.16.1.1 24
[ROUTER-GigabitEthernet0/0/0]q
[ROUTER]ip route-static 192.168.1.0 24 172.16.1.2
[ROUTER]ip route-static 192.168.2.0 24 172.16.1.2
(配置完毕后,可以尝试用PC去ping通ROUTER)
二、缺省路由和回程路由配置
实验拓扑及要求:
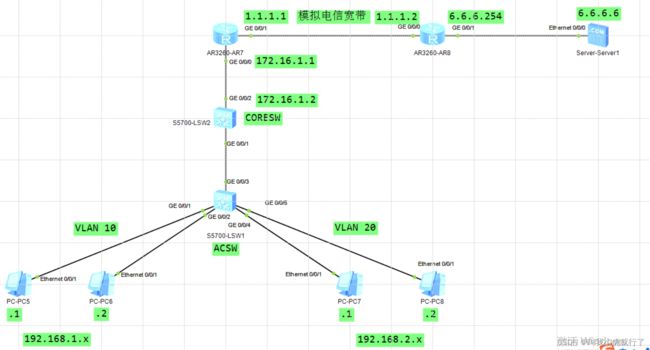
配置过程:
(在上面的配置基础上,添加了“模拟电信宽带”的组网,需要根据需求将ROUTER1和ROUTER2上指定接口的IP预设完毕,且配置SERVER的IP和网关)
(去往互联网的静态路由在CORE上配置,使用0.0.0.0 0.0.0.0)
(此处省略新增组网的基础配置过程,只在原有基础上添加新命令)
CORE上:
[CORESW]ip route-static 0.0.0.0 0.0.0.0 172.16.1.1
ROUTER1上:
[ROUTER]ip route-static 0.0.0.0 0.0.0.0 1.1.1.2
(此阶段配置完毕后,还不能实现内网访问互联网,需要后续做NAT配置)
三、浮动静态路由
实验拓扑及要求:
配置过程:
四、NAT配置
实验拓扑及要求:
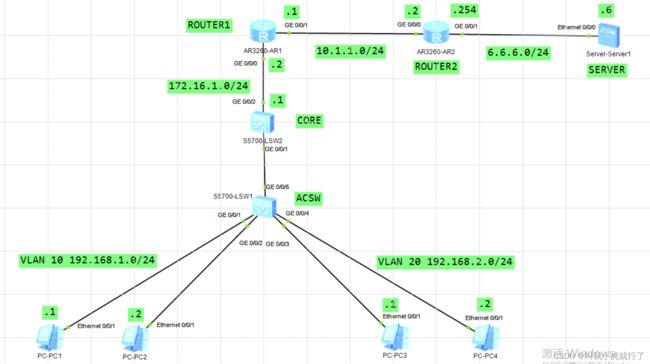
配置过程:
(预设的配置方法与上节一样,以下省略,若IP地址等信息不同,以本节拓扑的地址为主;注意,CORESW和ROUTER的网段中,首先需要给CORE配置VLAN,并在VLAN上配置IP地址;另外,CORESW与ROUTER相连的上行接口必须配置Access-VLAN,否则,即使处于同一个网段,互相也无法ping通)
(在内网可以访问外网SERVER的基础上进行以下配置)
ROUTER1上:
[ROUTER1]acl 2000
[ROUTER1-acl-basic-2000]rule permit source any
[ROUTER1-GigabitEthernet0/0/1]nat outbound 2000
[ROUTER1-GigabitEthernet0/0/1]q
(注意,本节只进行NAT配置、并没有添加其他ACL规则,如想添加deny规则,就需要在进口inb ound进行配置)
五、防火墙配置
实验拓扑及要求:
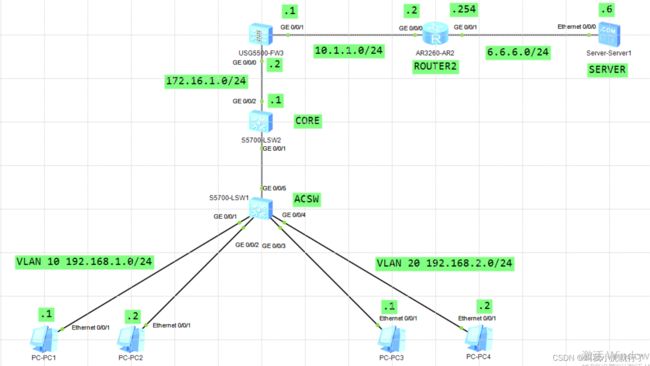 (由于拓扑和之前类似,且配置没有改变,该节不做演示,只做防火墙的简单基本配置,现实情况比这复杂得多)
(由于拓扑和之前类似,且配置没有改变,该节不做演示,只做防火墙的简单基本配置,现实情况比这复杂得多)
(USG6000的安装过程此阶段省略,username:admin,password:Admin@123,输入密码后系统会提示修改新密码)
配置过程:
(···)
[FIREWALL]firewall zone trust
[FIREWALL-zone-trust]add interface GigabitEthernet 0/0/0
[FIREWALL]firewall zone untrust
[FIREWALL-zone-untrust]add interface GigabitEthernet 1/0/0
[FIREWALL-zone-untrust]q
[FIREWALL]security-policy
[FIREWALL-policy-security]rule name shangwang
[FIREWALL-policy-security-rule-shangwang]source-zone trust
[FIREWALL-policy-security-rule-shangwang]destination-zone untrust
[FIREWALL-policy-security-rule-shangwang]action permit
[FIREWALL-policy-security-rule-shangwang]q
[FIREWALL-policy-security]q
[FIREWALL]int GigabitEthernet 0/0/0
[FIREWALL-GigabitEthernet0/0/0]ip address 172.16.1.2 24
[FIREWALL-GigabitEthernet0/0/0]q
[FIREWALL]int GigabitEthernet 1/0/0
[FIREWALL-GigabitEthernet1/0/0]ip address 10.1.1.1 24
[FIREWALL-GigabitEthernet1/0/0]q
[FIREWALL]nat-policy
[FIREWALL-policy-nat]rule name shangwang
[FIREWALL-policy-nat-rule-shangwang]source-zone trust
[FIREWALL-policy-nat-rule-shangwang]destination-zone untrust
[FIREWALL-policy-nat-rule-shangwang]action source-nat easy-ip
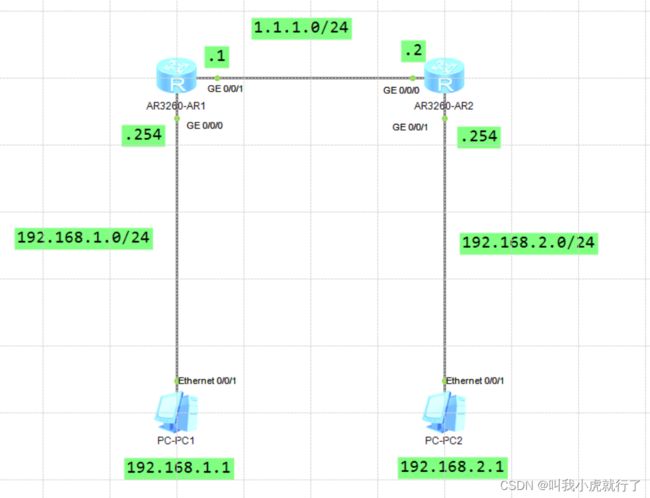
六、浮动路由配置
实验拓扑及要求:

配置过程:
(预设置过程已省略,以下是ROUTER1的浮动路由配置)
[ROUTER1]ip route-static 6.6.6.6 32 2.2.2.2 preference 61
[ROUTER1]ip route-static 6.6.6.6 32 1.1.1.2 preference 60
(实验结果是1.1.1.0网段为主路由、2.2.2.0网段是备路由)
七、OSPF配置
实验拓扑及要求:
配置过程:
(预设置已省略,IP地址按照拓扑演示配置即可,OSPF默认的序号是1,、宣告区域是area 0,ROUTER1的直连网段:192.168.1.0、ROUTER2的直连网段:192.168.2.0)
(···)
ROUTER1上:
[ROUTER1]ospf
[ROUTER1-ospf-1]area 0
[ROUTER1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[ROUTER1-ospf-1-area-0.0.0.0]network 1.1.1.0 0.0.0.255
[ROUTER1-ospf-1-area-0.0.0.0]q
ROUTER2上:
[ROUTER2]ospf
[ROUTER2-ospf-1]area 0
[ROUTER2-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[ROUTER2-ospf-1-area-0.0.0.0]network 1.1.1.0 0.0.0.255
[ROUTER2-ospf-1-area-0.0.0.0]q
(配置结束、PC去ping后,查看路由表,才会显示有OSPF;即,如果不ping,路由表中,不会显示)
ps:
华为官网案例实验:
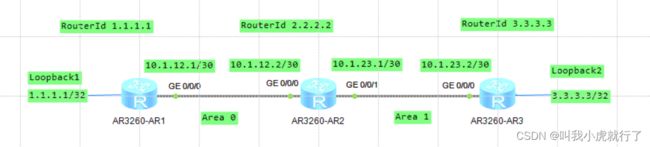
实验拓扑及要求:
(华为官网HCIA课程中的配置案例和上方案例有些许不同,前者案例中,包含了环回口Loopback——代替终端PC、还有RouterId的配置,本次实验中全程按照指定命令进行配置)
配置过程:
ROUTER1上:
[ROUTER1]int LoopBack 0
[ROUTER1-LoopBack0]ip address 1.1.1.1 32
[ROUTER1-LoopBack0]q
[ROUTER1]int GigabitEthernet 0/0/0
[ROUTER1-GigabitEthernet0/0/0]ip address 10.1.12.1 30
[ROUTER1-GigabitEthernet0/0/0]q
[ROUTER1]ospf 1 router-id 1.1.1.1
[ROUTER1-ospf-1]area 0
[ROUTER1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
[ROUTER1-ospf-1-area-0.0.0.0]network 10.1.12.0 0.0.0.3
[ROUTER1-ospf-1-area-0.0.0.0]q
[ROUTER1-ospf-1]q
ROUTER2上:
[ROUTER2]ospf 1 router-id 2.2.2.2
[ROUTER2-ospf-1]area 0
[ROUTER2-ospf-1-area-0.0.0.0]network 10.1.12.0 0.0.0.3
[ROUTER2-ospf-1-area-0.0.0.0]q
[ROUTER2-ospf-1]area 1
[ROUTER2-ospf-1-area-0.0.0.1]network 10.1.23.0 0.0.0.3
[ROUTER2-ospf-1-area-0.0.0.1]q
[ROUTER2-ospf-1]q
ROUTER3上:
[ROUTER3]interface LoopBack 0
[ROUTER3-LoopBack0]ip address 3.3.3.3 32
[ROUTER3-LoopBack0]q
[ROUTER3]int GigabitEthernet 0/0/0
[ROUTER3-GigabitEthernet0/0/0]ip address 10.1.23.2 30
[ROUTER3-GigabitEthernet0/0/0]q
[ROUTER3]ospf 1 router-id 3.3.3.3
[ROUTER3-ospf-1]area 1
[ROUTER3-ospf-1-area-0.0.0.1]network 3.3.3.3 0.0.0.0
[ROUTER3-ospf-1-area-0.0.0.1]network 10.1.23.0 0.0.0.3
[ROUTER3-ospf-1-area-0.0.0.1]q
[ROUTER3-ospf-1]q
(配置完成后在任意ROUTER上执行:display ospf peer brief显示ospf邻居信息,本次实操中,未观察到相关效果…)
ps:
补充实验TOPO:
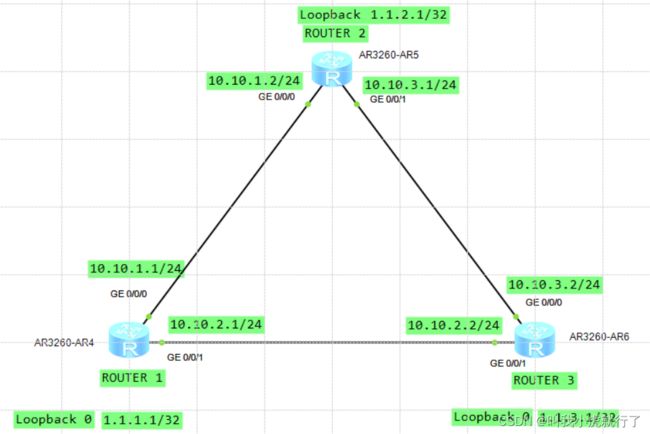
(本TOPO中的配置过程中,以ROUTET1为例,对于loopback 0的ospf配置命令为:network 1.1.1.1 0.0.0.0)
八、单臂路由配置
实验拓扑及要求:
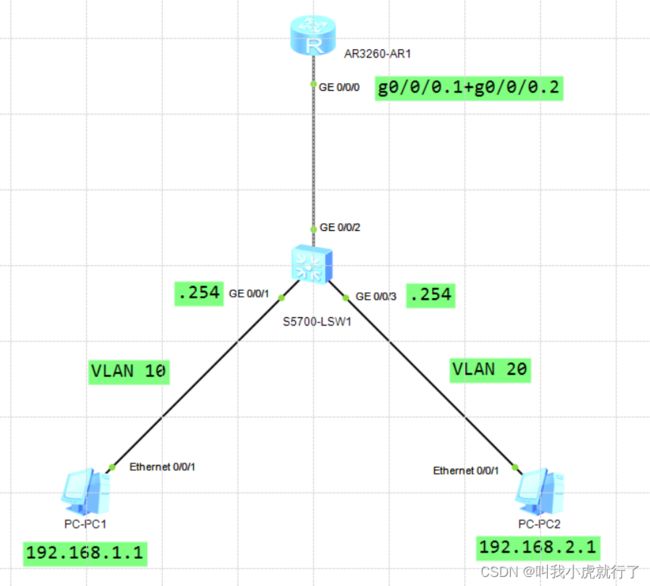
配置过程:
(预设置按照拓扑图的要求进行配置,其中,CORE交换机上接口应配置trunk)
(以下配置内容不包含划分VLAN、配置trunk接口等)
(注意:PC的网关配置在ROUTER上)
ROUTER上:
[ROUTER]int GigabitEthernet 0/0/0.1
[ROUTER-GigabitEthernet0/0/0.1]dot1q termination vid 10
[ROUTER-GigabitEthernet0/0/0.1]ip address 192.168.1.254 24
[ROUTER-GigabitEthernet0/0/0.1]arp broadcast enable
[ROUTER-GigabitEthernet0/0/0.1]q
[ROUTER]int GigabitEthernet 0/0/0.2
[ROUTER-GigabitEthernet0/0/0.2]dot1q termination vid 20
[ROUTER-GigabitEthernet0/0/0.2]ip address 192.168.2.254 24
[ROUTER-GigabitEthernet0/0/0.2]arp broadcast enable
[ROUTER-GigabitEthernet0/0/0.2]q
九、VLAN间通信(同一CORE)
实验拓扑及要求:
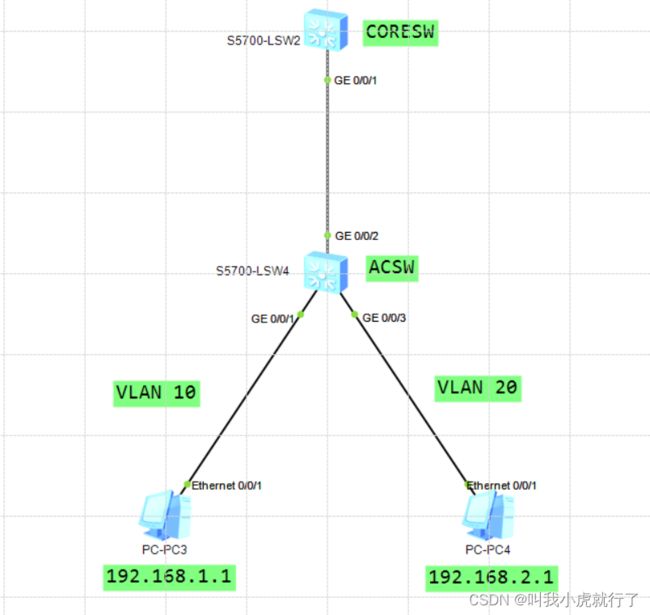
配置过程:
ACSW上:
[ACSW]vlan batch 10 20
[ACSW]int GigabitEthernet 0/0/1
[ACSW-GigabitEthernet0/0/1]port link-type access
[ACSW-GigabitEthernet0/0/1]port default vlan 10
[ACSW-GigabitEthernet0/0/1]q
[ACSW]int GigabitEthernet 0/0/3
[ACSW-GigabitEthernet0/0/3]port link-type access
[ACSW-GigabitEthernet0/0/3]port default vlan 20
[ACSW-GigabitEthernet0/0/3]q
[ACSW]int GigabitEthernet 0/0/2
[ACSW-GigabitEthernet0/0/2]port link-type trunk
[ACSW-GigabitEthernet0/0/2]port trunk allow-pass vlan all
[ACSW-GigabitEthernet0/0/2]q
CORESW:
[CORESW]vlan batch 10 20
[CORESW]int Vlanif 10
[CORESW-Vlanif10]ip address 192.168.1.254 24
[CORESW-Vlanif10]q
[CORESW]int Vlanif 20
[CORESW-Vlanif20]ip address 192.168.2.254 24
[CORESW-Vlanif20]q
[CORESW]int GigabitEthernet 0/0/1
[CORESW-GigabitEthernet0/0/1]port link-type trunk
[CORESW-GigabitEthernet0/0/1]port trunk allow-pass vlan all
[CORESW-GigabitEthernet0/0/1]q
(本节实验的网关配置在VLANIF上,与上节单臂路由不同的是,单臂路由配置网关是在子接口上)
补充:跨交换机的VLAN间访问
实验拓扑及要求:

配置过程:
(该补充内容是:模拟不同区域的PC划分到同一个VLAN,实现不同部门的PC不能互相访问,是一个部门、即同一VLAN的PC可以互相访问;对左侧组网的配置以下省略,只展示trunk配置过程)
(根据测试,如果PC3和PC1处于不同的网段,即使在一个VLAN内,也不能实现通信)
(···)
ACSW1上:
[ACSW1]int GigabitEthernet 0/0/2
[ACSW1-GigabitEthernet0/0/2]port link-type trunk
[ACSW1-GigabitEthernet0/0/2]port trunk allow-pass vlan 10 20
ACSW2上:
[ACSW2]int GigabitEthernet 0/0/3
[ACSW2-GigabitEthernet0/0/3]port link-type trunk
[ACSW2-GigabitEthernet0/0/3]port trunk allow-pass vlan 10 20
十、CORE与边界ROUTER通信
实验拓扑及要求:
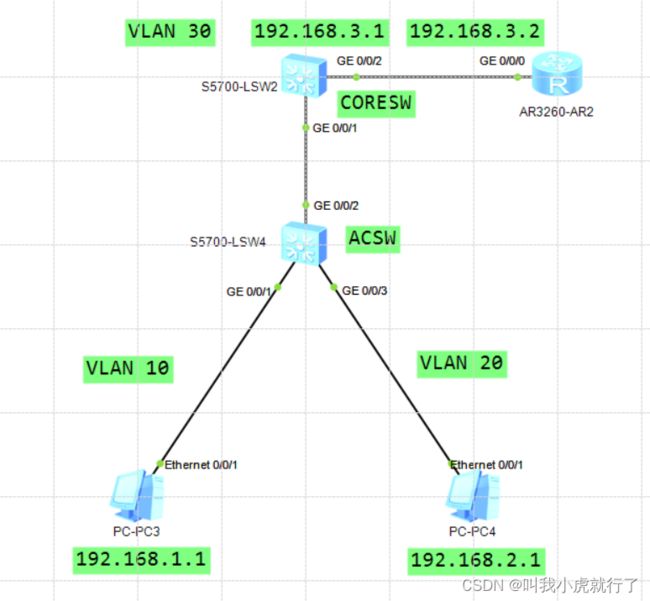 配置过程:
配置过程:
(预设置的内容和上一节相同,该部分本节省略)
(···)
CORESW上:
[CORESW]vlan 30
[CORESW-vlan30]q
[CORESW]int Vlanif 30
[CORESW-Vlanif30]ip address 192.168.3.1 24
[CORESW-Vlanif30]q
[CORESW]int GigabitEthernet 0/0/2
[CORESW-GigabitEthernet0/0/2]port link-type access
[CORESW-GigabitEthernet0/0/2]port default vlan 30
[CORESW-GigabitEthernet0/0/2]q
ROUTER上:
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]ip address 192.168.3.2 24
[ROUTER-GigabitEthernet0/0/0]q
(配置结束后,可以实现边界ROUTER和内网CORESW的通信,尝试ping同即可;由于未做路由配置,所以还不能实现PC与外界通信)
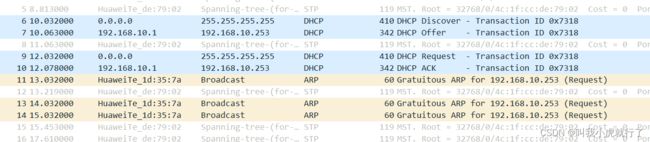
十一、ACL(实现端口控制)
实验拓扑及要求:
(前期,通过DHCP配置后,wireshark抓包得到如下)
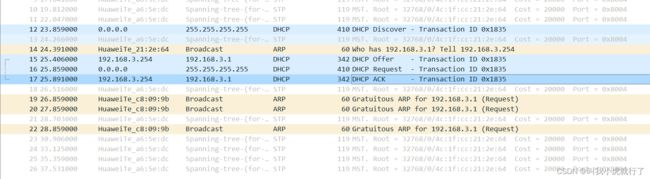 配置过程:
配置过程:
(预设置过程省略,以下是ROUTER上的配置)
[ROUTER]acl 3000
[ROUTER-acl-adv-3000]rule 5 deny udp source any source-port eq 67
[ROUTER-acl-adv-3000]rule 10 permit ip
[ROUTER-acl-adv-3000]q
[ROUTER]q
[ROUTER]port-group group-member GigabitEthernet 0/0/1 to GigabitEthernet 0/0/2
[ROUTER-port-group]traffic-filter inbound acl 3000
十二、telnet远程管理
实验拓扑及要求:
(本TOPO是:真机主机连接路由器)
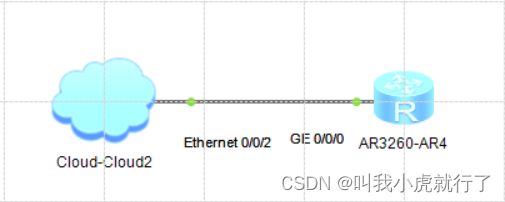
本次实验中,涉及到的非命令配置中有:
1、网卡的IP、网关设置,保证Cloud连接的网卡地址和后续ROUTER
2、Cloud上添加虚拟网卡(本次使用的是已经存在的vm8网卡),使其能够与真机互通(即Cloud就代表真机主机)
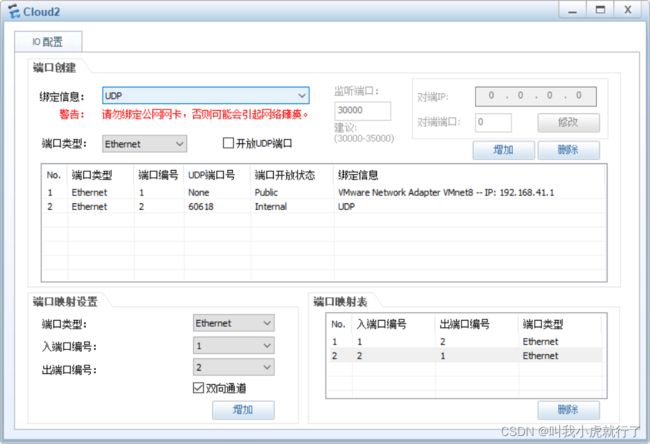
(预设置都结束后,先尝试用真机ping通给ROUTER指定端口配置的IP,由于是直连,所以直接就可以ping通)
配置过程:
[ROUTER]user-interface vty 0 4
[ROUTER-ui-vty0-4]authentication-mode aaa
[ROUTER-ui-vty0-4]q
[ROUTER]aaa
[ROUTER-aaa]local-user xiaohu password cipher 123456
[ROUTER-aaa]local-user xiaohu service-type telnet
[ROUTER-aaa]local-user xiaohu privilege level 15
[ROUTER-aaa]q
[ROUTER]telnet server enable
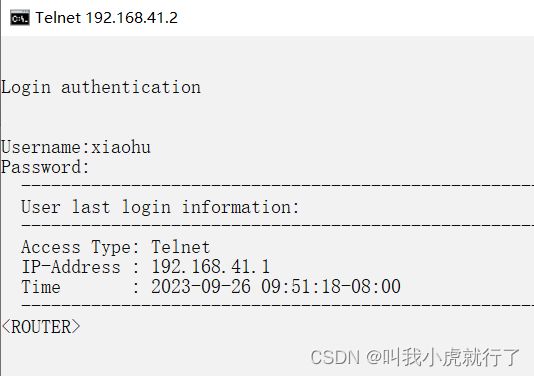
实现结果:
十三、EASY-IP配置
实验拓扑及要求:
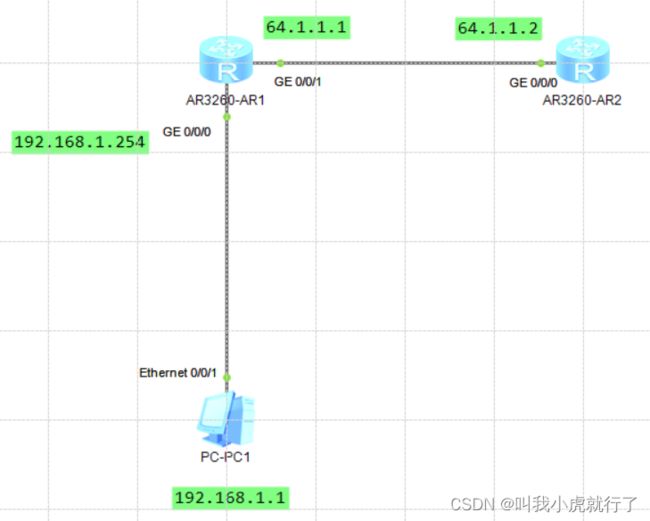
配置过程:
(由于本节实验是采用easyip方式实现NAT,所以只做简化配置,以ROUTER2作为连接外网的ROUTER,配置完easyip后可实现不用配置路由PC就可与外网连通,预设置已做省略)
ROUTER1上:
[ROUTER1]acl 2000
[ROUTER1-acl-basic-2000]rule 5 permit source 192.168.1.0 0.0.0.255
[ROUTER1-acl-basic-2000]q
[ROUTER1]int GigabitEthernet 0/0/1
[ROUTER1-GigabitEthernet0/0/1]nat outbound 2000
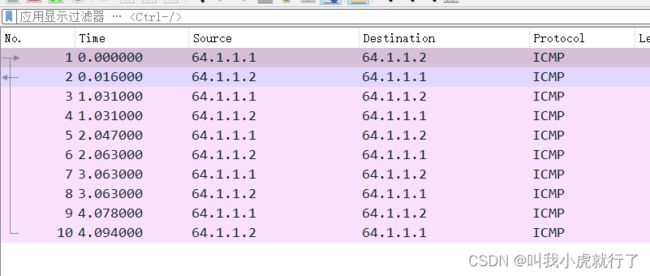
(配置结束后,尝试用PC去ping通ROUTER2的接口IP,通过wireshark抓包,可以显示出数据包的源IP地址是ROUTER1的0/0/1接口地址)
十四、DHCP配置(interface模式)
实验拓扑及要求:
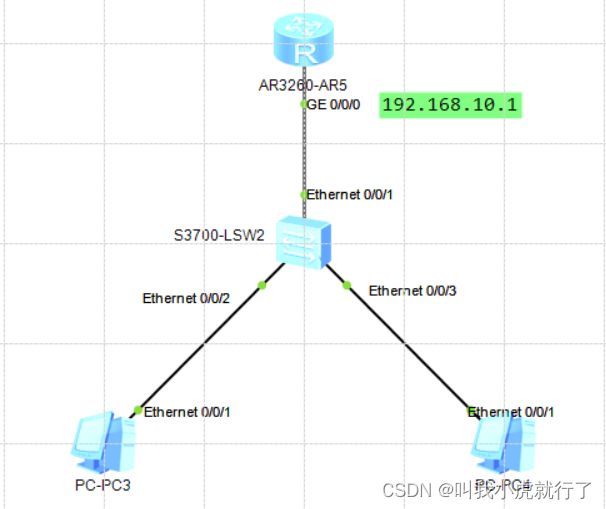
配置过程:
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]ip address 192.168.10.1 24
[ROUTER-GigabitEthernet0/0/0]q
[ROUTER]dhcp enable
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]dhcp select interface
配置过程:
(使用wireshark抓包后,显示实验结果)
十五、DNS配置(PC作为DNS SERVER)
实验拓扑及要求:

配置过程:
(预配置为TOPO所示:注意SERVER1的网关需要配置成ROUTER的接口地址,就是说ROUTER0/0/0接口IP地址既作为PC2的网关、也是SERVER网关;网关配置完毕后,可以尝试使用PC2pingROUTER的网关地址;设置SERVER上的服务器配置,填入域名,并对应PC2的IP、并启动;PC1上打开DHCP功能)
ROUTER上:
[ROUTER]dhcp enable
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]dhcp select interface
[ROUTER-GigabitEthernet0/0/0]dhcp server dns-list 192.168.2.10
[ROUTER-GigabitEthernet0/0/0]q
(配置完毕后,查看PC1分配的IP地址和DNS SERVER地址,查看是否是SERVER的IP,并直接ping域名)
十六、VRRP配置(master+backup)
实验拓扑及要求:
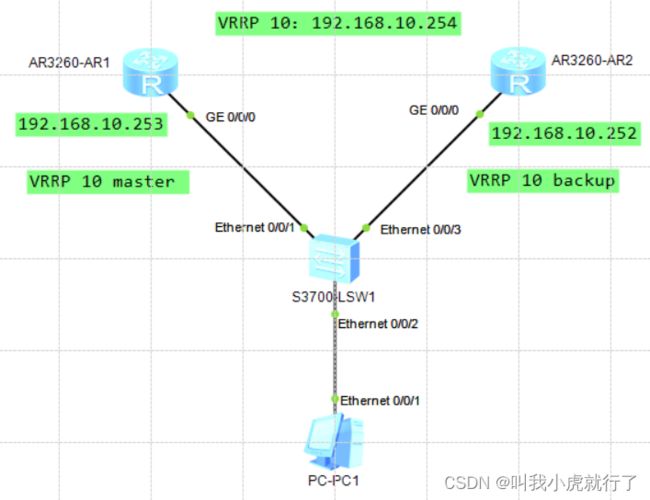
(根据如图所示TOPO,实现左侧ROUTER1为VRRP MASTER、右侧ROUTER2为VRRP BACKUP,且设置的VRRPID都为10,地址都是192.168.10.254;注意,实验前需要将ROUTER1和ROUTER2的接口都配置好IP)
配置过程:
ROUTER1上:
[ROUTER1]int GigabitEthernet 0/0/0
[ROUTER1-GigabitEthernet0/0/0]ip address 192.168.10.253 24
[ROUTER1-GigabitEthernet0/0/0]vrrp vrid 10 virtual-ip 192.168.10.254
[ROUTER1-GigabitEthernet0/0/0]vrrp vrid 10 priority 105
[ROUTER1-GigabitEthernet0/0/0]q
ROUTER2上:
[ROUTER2]int GigabitEthernet 0/0/0
[ROUTER2-GigabitEthernet0/0/0]ip address 192.168.10.252 24
[ROUTER2-GigabitEthernet0/0/0]vrrp vrid 10 virtual-ip 192.168.10.254
(由于ROUTER2的VRRP没有priority没有进行配置,即默认为100、小于ROUTER1的priority,所以默认ROUTER1是MASTER,ROUTER2是BACKUP;且使用PC去ping三个地址:252、253、254都可以ping通)
十七、防火墙(dmz非军事区)
实验拓扑及要求:
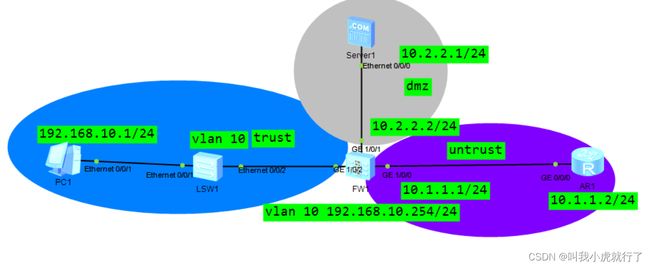 配置过程:
配置过程:
(防火墙默认阻挡所有流量通过)
配置IP地址:
LSW1上:
vlan 10
int vlan 10
undo shutdown
port-group group-member eth0/0/1 eth0/0/2
port link-type access
port default vlan 10
AR1上:
int gi0/0/0
ip add 10.1.1.2 24
undo shutdown
int loopback 0
ip add 1.1.1.1 32
FW1上:
vlan 10
int vlan 10
ip add 192.168.10.254 24
undo shutdown
int gi1/0/2
portswitch #转换成二层接口
port link-type access
port default vlan 10
undo shutdown
int gi1/0/1
ip add 10.2.2.2 24
undo shutdown
int gi1/0/0
ip add 10.1.1.1 24
undo shutdown
firewall zone trust #进入安全区域
add int vlan 10 #把安全区域的接口或者vlan划分进去
quit
firewall zone untrust #进入外网区域,这个区域是不能访问内网的
add int gi1/0/0 #添加这个区域的接口
quit
firewall zone dmz #进入dmz区域,这个区域是非军事区域,也就是相当于防火墙里面的第二道防火墙
add int gi1/0/1 #添加这个区域的接口
quit
(默认防火墙所有接口都是在local区域的,所以我们要放行local区域)
security-policy #建立安全策略
rule name local #起个名字为local
source-zone local #默认所有接口的区域在local
action permit #放行流量通过
这样还不算完,这些都做了之后,其它设备还是ping不通防火墙,需要开启连接防火墙的三个接口
int gi1/0/2 #进入gi1/0/2接口
service-manager ping permit #在接口上允许ping,如果不开这个ping,就算策略做了也不能与防火墙通信
quit
int gi1/0/1
service-manager ping permit
quit
int gi1/0/0
service-manager ping permit
(本实验在FW上的配置出现了一些问题,配置TOPO和命令是借鉴的其他博主的,由结果看方法可行)
十八、ACL访问控制(配合单臂路由)
实验拓扑及要求: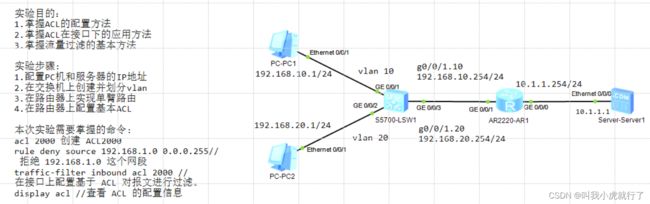
配置过程:
CORE上:
[CORE]vlan batch 10 20
[CORE]int GigabitEthernet 0/0/1
[CORE-GigabitEthernet0/0/1]port link-type access
[CORE-GigabitEthernet0/0/1]port default vlan 10
[CORE-GigabitEthernet0/0/1]q
[CORE]int GigabitEthernet 0/0/2
[CORE-GigabitEthernet0/0/2]port link-type access
[CORE-GigabitEthernet0/0/2]port default vlan 20
[CORE-GigabitEthernet0/0/2]q
[CORE]int GigabitEthernet 0/0/3
[CORE-GigabitEthernet0/0/3]port link-type trunk
[CORE-GigabitEthernet0/0/3]port trunk allow-pass vlan all
[CORE-GigabitEthernet0/0/3]q
ROUTER上:
[ROUTER]int GigabitEthernet 0/0/1.10
[ROUTER-GigabitEthernet0/0/1.10]ip address 192.168.10.254 24
[ROUTER-GigabitEthernet0/0/1.10]dot1q termination vid 10
[ROUTER-GigabitEthernet0/0/1.10]arp broadcast enable
[ROUTER-GigabitEthernet0/0/1.10]q
[ROUTER]int GigabitEthernet 0/0/1.20
[ROUTER-GigabitEthernet0/0/1.20]ip address 192.168.20.254 24
[ROUTER-GigabitEthernet0/0/1.20]dot1q termination vid 20
[ROUTER-GigabitEthernet0/0/1.20]arp broadcast enable
[ROUTER-GigabitEthernet0/0/1.20]q
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]ip address 10.1.1.254 24
[ROUTER-GigabitEthernet0/0/0]q
[ROUTER]acl 2000
[ROUTER-acl-basic-2000]rule 5 permit source 192.168.10.0 0.0.0.255
[ROUTER-acl-basic-2000]rule 10 deny source 192.168.20.0 0.0.0.255
[ROUTER-acl-basic-2000]q
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]traffic-filter outbound acl 2000
[ROUTER-GigabitEthernet0/0/0]display acl 2000
Basic ACL 2000, 2 rules
Acl’s step is 5
rule 5 permit source 192.168.10.0 0.0.0.255
rule 10 deny source 192.168.20.0 0.0.0.255
[ROUTER-GigabitEthernet0/0/0]q
十九、AAA(telnet远程控制)
实验拓扑及要求:

配置过程:
ROUTER1上:
[ROUTER1]int GigabitEthernet 0/0/0
[ROUTER1-GigabitEthernet0/0/0]ip address 192.168.1.1 24
[ROUTER1-GigabitEthernet0/0/0]q
[ROUTER1]user-interface vty 0 4
[ROUTER1-ui-vty0-4]authentication-mode aaa
[ROUTER1-ui-vty0-4]q
[ROUTER1]aaa
[ROUTER1-aaa]local-user xiaohu password cipher 123456
[ROUTER1-aaa]local-user xiaohu privilege level 15
[ROUTER1-aaa]local-user xiaohu service-type telnet
[ROUTER1-aaa]q
ROUTER2上:
[ROUTER2]int GigabitEthernet 0/0/1
[ROUTER2-GigabitEthernet0/0/1]ip address 192.168.1.2 24
[ROUTER2-GigabitEthernet0/0/1]q
[ROUTER2]q
telnet 192.168.1.1
Press CTRL_] to quit telnet mode
Trying 192.168.1.1 …
Connected to 192.168.1.1 …
Login authentication
Username:xiaohu
Password:
(配置完成后输入预设好的账号还有密码进行验证结果)
二十、NAT配置(静态+动态+NAPT)
实验拓扑及要求(该TOPO应用三种NAT配置): (静态NAT)
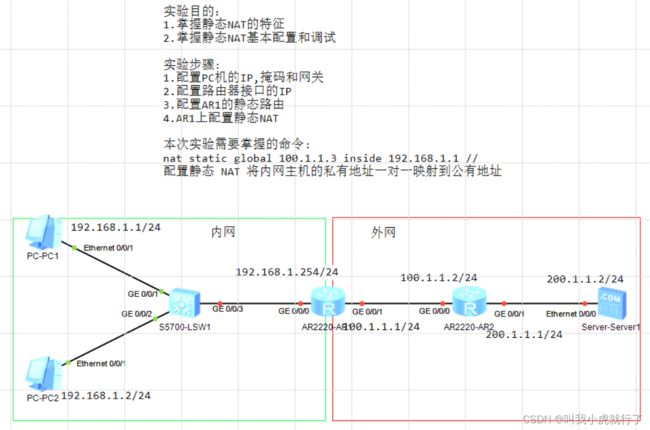
配置过程:
ROUTER1上:
[ROUTER1]int GigabitEthernet 0/0/0
[ROUTER1-GigabitEthernet0/0/0]ip address 192.168.1.254 24
[ROUTER1-GigabitEthernet0/0/0]q
[ROUTER1]int GigabitEthernet 0/0/1
[ROUTER1-GigabitEthernet0/0/1]ip address 100.1.1.1 24
[ROUTER1-GigabitEthernet0/0/1]q
[ROUTER1]ip route-static 0.0.0.0 100.1.1.2
[ROUTER1]int GigabitEthernet 0/0/1
[ROUTER1-GigabitEthernet0/0/1]nat static global 12.1.1.1 inside 192.168.1.1
[ROUTER1-GigabitEthernet0/0/1]nat static global 12.1.1.2 inside 192.168.1.2
[ROUTER1-GigabitEthernet0/0/1]q
ROUTER2上:
[ROUTER2]int GigabitEthernet 0/0/0
[ROUTER2-GigabitEthernet0/0/0]ip address 100.1.1.2 24
[ROUTER2-GigabitEthernet0/0/0]q
[ROUTER2]int GigabitEthernet 0/0/1
[ROUTER2-GigabitEthernet0/0/1]ip address 200.1.1.1 24
[ROUTER2-GigabitEthernet0/0/1]q
[ROUTER2]ip route-static 192.168.1.0 24 100.1.1.1
(配置完成后使用wireshark进行抓包,结果显示静态nat可一对一进行地址转换)
(动态NAT)
配置过程:
(先前配置过程相同,故省略,直接从动态NAT配置开始)
[ROUTER1]nat address-group 1 1.1.1.1 1.1.1.3
[ROUTER1]acl 2000
[ROUTER1-acl-basic-2000]rule 5 permit source 192.168.1.0 0.0.0.255
[ROUTER1-acl-basic-2000]q
[ROUTER1]int GigabitEthernet 0/0/1
[ROUTER1-GigabitEthernet0/0/1]nat outbound 2000 address-group 1 no-pat
[ROUTER1-GigabitEthernet0/0/1]q
(NAPT)
(和动态NAT配置不同的是,NAPT后不加no-pat)
二十一、FTP配置(server-router-client)
实验拓扑及要求:
 配置过程:
配置过程:
(本次实验是以其他TOPO为例进行整体配置的,其SERVER和CLIENT的IP地址和网关按照上图所示进行配置;使FTP SERVER根目录中的文件已经创建好,方便后续调用。本次创建了test.txt,选择后启动FTP SERVER)
ROUTER上:
[ROUTER]int GigabitEthernet 0/0/0
[ROUTER-GigabitEthernet0/0/0]ip address 10.0.1.254 24
[ROUTER-GigabitEthernet0/0/0]q
[ROUTER]int GigabitEthernet 0/0/1
[ROUTER-GigabitEthernet0/0/1]ip address 10.0.2.254 24
[ROUTER-GigabitEthernet0/0/1]q
(CLIENT、SERVER、ROUTER相通后,再进行以下操作)
[ROUTER]user-interface vty 0 4
[ROUTER-ui-vty0-4]authentication-mode aaa
[ROUTER-ui-vty0-4]q
[ROUTER]aaa
[ROUTER-aaa]local-user FTP password cipher 123456
[ROUTER-aaa]local-user FTP privilege level 15
[ROUTER-aaa]local-user FTP ftp-directory flash:
[ROUTER-aaa]local-user FTP service-type ftp
[ROUTER-aaa]q
[ROUTER]ftp server enable
(完成该步配置后,在FTP CLIENT上进行登录,账号密码和ROUTER上配置的相同,IP地址填写ROUTER上接口的地址,登录后,选择本地的文件上传至FTP服务器上,结果显示文件上传成功)