Chapter 6 Fundamental Cloud Security
一.单选题
1
The characteristic of something being made accessible only to authorized parties, it is ______
A
confidentiality
B
integrity
C
authenticity
D
availability
答案:A
保密性(confidentiality) 是指事物只有被授权方才能访问的特性。
Confidentiality is the characteristic of something being made
accessible only to authorized parties.在云环境中,保密性主要是关于对传输和存储的数据进行访问限制的。
完整性(integrity) 是指未被未授权方篡改的特性。Integrity is the characteristic of not having been altered by an
unauthorized party.真实性(authenticity) 是指事物是由经过授权的源提供的这一特性。
Authenticity is the characteristic of something having been provided
by an authorized source.这个概念包括不可否认性,也就是一方不能否认或质疑一次交互的真实性。
可用性(availability) 是指在特定的时间段内可以访问和可以使用的特性。
Availability is the characteristic of being accessible and usable
during a specified time period.
2
_____ and malicious(恶意的) intermediary(中介) attacks are usually carried out by malicious service agents that intercept(拦截) network traffic.
A
Denial of service
B
Traffic eavesdropping
C
Virtualization attack
D
Insufficient authorization
1 Traffic Evaesdropping 交通窃听
当消息传输时可能被人拷贝一份
2 Malicious Intermediary 恶意中介
消息被恶意的中介拦截,并被修改
3 Denial of Servic 拒绝服务
通过大量的攻击让目标IT资源超载,无法提供正常服务
4 Insufficient Authorization /Week Authentication 充足的授权/弱认证
授权给的太广泛导致攻击者可以接触到正常来说是被保护的IT资源 5 Virtualization Attack 虚拟化攻击
虚拟机的使用者滥用了权限,去攻击底层的物理硬件设施
5 Virtualization Attack 虚拟化攻击
利用虚拟化环境中的漏洞来获得对底层硬件的访问权限
6 Overlapping Trust Boundaries 信任边界重叠
是一种潜在的安全微信,攻击者可以利用重叠的信任边界来攻击其他用户的IT资源
答案:B Traffic eavesdropping 也是通过恶意的服务代理来拦截网络信息的
3
The characteristic of not having been altered by an unauthorized party, it is _______
A
confidentiality
B
integrity
C
authenticity
D
availability
答案:B 被未授权的的机构更改,指完整性 integrity
4
_______ are associated with measuring and assessing(评估) insecurity, or the lack of security.
A
Threats
B
Vulnerabilities
C
Risks
D
all
威胁(threat) 是潜在的对安全性破坏,可以试图破坏隐私并/或导致危害,以此挑战防护。
A threat is a potential security violation that can challenge defenses
in an attempt to breach privacy and/or cause harm.漏洞(vulnerability) 是一种可能被利用的弱点,可能是因为安全控制保护不够,也可能是因为攻击击败了现有的安全控制。
A vulnerability is a weakness that can be exploited either because it
is protected by insufficient security controls, or because existing
security controls are overcome by an attack.风险(risk) 是指执行一个行为带来损失或危害的可能性。
Risk is the possibility of loss or harm arising from performing an
activity. Risk is typically measured according to its threat level and
the number of possible or known vulnerabilities.确定IT资源的风险的两个标准:
(1)威胁利用IT资源中漏洞的概率
(2)如果IT资源被损害,预期会造成的损失。
答案:D 以上三种都与衡量与评估不安全和缺少防御有关。
5
_____ is a non-trusted threat agent that usually attempts attacks from outside of a cloud’s boundary.
A
A malicious insider
B
A trusted attacker
C
A malicious service agent
D
An anonymous attacker
**威胁作用者(threat agent)**是引发威胁的实体,因为它能够实施攻击。
1 匿名攻击者(anonymous attacker) 匿名攻击者是云中没有权限、不被信任的云服务用户。通常是一个外部软件程序,通过公网发动网络攻击。
2恶意服务作用者(malicious service agent)
恶意服务作用者能截取并转发云内的网络流量。
3授信的攻击者(trusted attacker)
又称恶意的租户(malicious tenant)。
授权的攻击者与同一云环境中的云用户共享IT资源,试图利用合法的证书来把云提供者以及与他们共享IT资源的云租户作为攻击目标。
4恶意的内部人员(malicious insider)
是人为的威胁作用者,他们的行为代表云提供者或者与之有关。
通常是现任或前任的雇员,或者能够访问云提供者资源范围的第三方。
答案:D 匿名攻击者通常是不被信任,尝试从外界进行攻击的
6
_______ intercepts(拦截) network communication in an attempt to maliciously use or augment(增加) the data.
A
A malicious insider
B
A trusted attacker
C
A malicious service agent
D
An anonymous attacker
答案:C 符合malicious service agent 的定义
7
______ exists as an authorized cloud service consumer with legitimate credentials that it uses to exploit(渗透) access to cloud-based IT resources.
A
A malicious insider
B
A trusted attacker
C
A malicious service agent
D
An anonymous attacker
答案:B 符合 trusted attacker的定义
8
______ is a human that attempts to abuse(滥用) access privileges to cloud premises.
A
A malicious insider
B
A trusted attacker
C
A malicious service agent
D
An anonymous attacker
答案: A 符合 malicious insider的定义,滥用了高优先级的访问权限
9
Traffic eavesdropping and malicious intermediary attacks are usually carried out by _____ that intercept network traffic.
A
malicious insiders
B
trusted attackers
C
malicious service agents
D
anonymous attackers
答案: C 符合 malicious service agents的定义,拦截了网络上的信息
10
A ______ attack occurs when a targeted IT resource is overloaded with requests in an attempt to cripple or render it unavailable.
A
denial of service
B
traffic eavesdropping
C
malicious intermediary
D
insufficient authorization
答案: A 通过大量的访问时目标IT资源变得不可用
11
The _____ attack occurs when access is granted(授权)to an attacker erroneously or too broadly, or when weak passwords are used.
A
denial of service
B
traffic eavesdropping
C
malicious intermediary
D
insufficient authorization
答案:D 充足的授权 insufficient是不充足的,怎么带上authorizaiton就变成了充足的授权了?
二.判断题
1
Authenticity is the characteristic of something being made accessible only to authorized parties.
答案:错误 confidentiality才是
2
Integrity is the characteristic of not having been altered by an unauthorized party.
答案:正确
3
Confidentiality is the characteristic of something having been provided by an authorized source.
答案:错误 authenticity才是
4
Availability is the characteristic of being accessible and usable during all time period.
答案:错误 是在specified time period
5
Traffic eavesdropping is to compromise the confidentiality and integrity.
答案: 错误 交通窃听破坏了保密性但并未破坏真实性
6
A virtualization attack exploits vulnerabilities within physical environments to gain
unauthorized access to underlying physical hardware.
答案:错误
虚拟化攻击利用的是虚拟化环境中的漏洞,获得了对底层物理硬件未被授权的访问。
A virtualization attack exploits vulnerabilities within virtualized
environments to gain unauthorized access to underlying physical
hardware.
7
Overlapping trust boundaries represent a threat whereby attackers can exploit cloud-based
IT resources shared by multiple cloud consumers.
答案:正确
重叠的信任边界潜藏了一种威胁,攻击者可以利用多个云用户共享的、基于云的IT资源。
Overlapping trust boundaries represent a threat whereby attackers can
exploit cloud-based IT resources shared by multiple cloud consumers.
三.简答题
1
(1)What are characteristics that can be associated with measuring security?
答案:
1 threat
A threat is a potential security violation that can challenge defenses
in an attempt to breach privacy and/or cause harm.
2 vulnerability
A vulnerability is a weakness that can be exploited either because it
is protected by insufficient security controls, or because existing
security controls are overcome by an attack.
3 risk
Risk is the possibility of loss or harm arising from performing an
activity. Risk is typically measured according to its threat level and
the number of possible or known vulnerabilities.
(2)Which characteristic is destroyed by denial of service attack?
答案:
IT resource is overloaded with requests in an attempt to cripple or render it unavailable.
2
How many cloud security threats in the book? which is cloud security threat in the figure?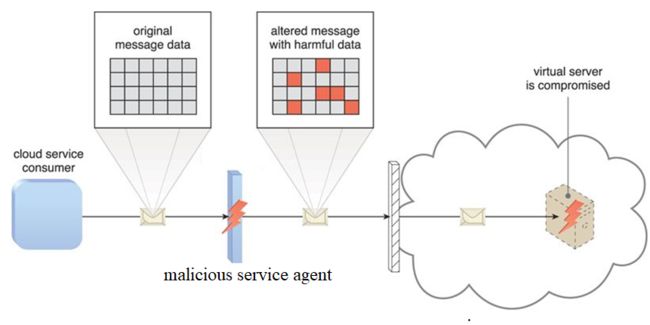
答案:
six
1 Traffic Evaesdropping
2 Malicious Intermediary
3 Denial of Servic
4 Insufficient Authorization /Week Authentication
5 virtualization attack
6 Overlapping trust boundaries
Malicious Intermediary