- Java项目设计文档:架构、模块与实现策略详解
体制教科书
本文还有配套的精品资源,点击获取简介:Java项目设计文档是项目规划、实施和维护的重要指导工具,包含系统架构、模块划分、接口定义、类设计、数据库设计、异常处理、测试计划、性能优化以及部署运维等方面。本设计文档集合对于理解Java项目的架构设计和提升项目开发质量具有极高的参考价值。1.项目背景阐述在当今数字化转型的大潮中,企业对于IT系统的依赖日益加重。项目背景阐述这一章,将为您揭示本次项目的发起缘
- JNPF.java前后端分离框架,SpringBoot+SpringCloud开发微服务
「已注销」
JNPF.java版本采用全新的前后端分离架构模式。前后端分离已成为互联网项目开发的业界标准开发方式,通过nginx+tomcat等方式有效的进行解耦合,并且前后端分离会为以后的大型分布式架构、弹性计算架构、微服务架构、多端化服务打下坚实的基础。技术选型:SpringBootSpringCloudMybatis-PlusRedisjqueryvueBootstrapElementUIUniapph
- 一篇文章,彻底理解数据库操作语言:DDL、DML、DCL、TCL
Java布道者
oracle数据库sql
最近与开发和运维讨论数据库账号及赋权问题时,发现大家对DDL和DML两个概念并不了解。于是写一篇文章,系统的整理一下在数据库领域中的DDL、DML、DQL、DCL的使用及区别。通常,数据库SQL语言共分为四大类:数据定义语言DDL,数据操作语言DML,数据查询语言DQL,数据控制语言DCL。再加上事务控制语言TCL,一个共5个。下面,我们就详细了解一下它们。数据定义语言DDLDDL(DataDef
- JVM 类加载 详解
飞滕人生TYF
javajvmjava类加载
JVM类加载详解JVM类加载(JavaClassLoading)是Java虚拟机(JVM)执行Java程序的重要机制之一,用于将.class文件动态加载到内存中并进行验证、解析和初始化,最终生成可以直接使用的类对象。1.类加载的基本概念1.1什么是类加载?类加载是将.class文件加载到JVM并转化为内存中可以运行的类的过程。目标:生成一个内存中的Class对象,供程序使用。触发点:当程序首次访问
- centos下nginx实现按国家/地域封禁、按ip频率限流能力、ngx_http_geoip2_module、ngx_http_geoip_module的区分
zlingh
网络nginxlinux运维服务器
本人亲测,且在docker环境中运行成功一、采用ngx_http_geoip2_module模块nginx版本./configure--with-http_stub_status_module--prefix=/usr/local/nginx--user=nginx--group=nginx--with-http_ssl_module--with-stream--add-module=/usr/l
- 基于Redis geo地理位置的物流路线规划系统实现方案
xiyubaby.17
缓存redis
物流路线规划系统实现方案一、系统架构图数据存储层数据处理层业务服务层客户端RedisGEOPostgreSQL图数据库地理编码服务实时交通处理路线优化引擎距离计算服务路径规划服务订单管理服务物流管理系统司机APP客户门户客户端API网关业务服务层数据处理层数据存储层二、核心模块实现1.地理模型定义publicclassLocation{privateStringid;privateStringad
- Nginx源码剖析--ngx_http_optimize_servers函数分析
gswen
Nginxnginx源码函数
前言本章将继续介绍HTTP模块初始化函数:ngx_http_block中的内容。将会涉及到server块的组织,监听端口的管理,以及ip地址和server块之间的组织关系。下面我们将从listen关键字说起,然后根据listen配置项以及它的解析函数了解nginx组织server块和监听端口的过程。最后在介绍ngx_http_optimize_servers函数。所有这些工作都是为了实现Nginx
- 【前端构建】使用Docker打包多个前端项目到一个Nginx镜像,并给conf文件动态传递参数
Zacks_xdc
前端dockernginx
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档文章目录背景正文DockerFileNginx配置模板接收变量并替换Shell脚本将Nginx配置模板替换成配置文件使用构建镜像运行容器总结背景公司给一些客户要部署三个前端项目。最初,每个前端项目都以独立的镜像形式交付并部署。然而,随着客户数量的增加,每个客户都提出了一些自定义需求,后端也进行了对应改造。这导致了部署过程变得复杂且繁琐
- Java Panama 项目:Java 与 AI 的融合
AI天才研究院
计算Java实战DeepSeekR1&大数据AI人工智能大模型人工智能javapython
JavaPanama项目:Java与AI的融合Java在AI领域的优势Java在AI领域的优势主要体现在以下几个方面:强大的生态系统:Java拥有丰富的库和框架,为AI开发提供了坚实的基础。跨平台性:Java的“一次编写,到处运行”特性,降低了AI应用的运维成本。高性能与稳定性:Java虚拟机(JVM)的优化和垃圾回收机制,确保了AI应用的高效运行和内存管理。实时数据处理能力:Java可以高效处理
- Kubernetes Init 容器:实现 Nginx 和 PHP 对 MySQL 的依赖检查
曹天骄
kubernetesnginxphp
在设计KubernetesPod时,如果需要在启动Nginx和PHP之前等待MySQL启动完成,可以通过初始化容器(initC)来实现。初始化容器可以用于检查MySQL是否可用,只有在MySQL可用后,才会继续启动主容器(Nginx和PHP)。设计思路初始化容器(initC):使用一个简单的脚本或工具(如mysql-client)来检查MySQL服务是否可用。如果MySQL可用,初始化容器成功退出
- DunTrust IP SSL证书——支持多端口验证
https
市面上99%的证书品牌的IPSSL证书在签发过程中会涉及默认80或者443端口开放问题,但是也有少数服务商也支持其他端口验证。一、IPSSL证书概述IPSSL证书是一种用于保护IP地址安全的SSL证书,它能够对IP地址进行HTTPS加密,确保传输数据的安全性和完整性。IPSSL证书通常用于没有域名或需要直接使用IP地址进行访问的场景。二、多端口验证的支持情况市面上99%的证书品牌的IPSSL证书在
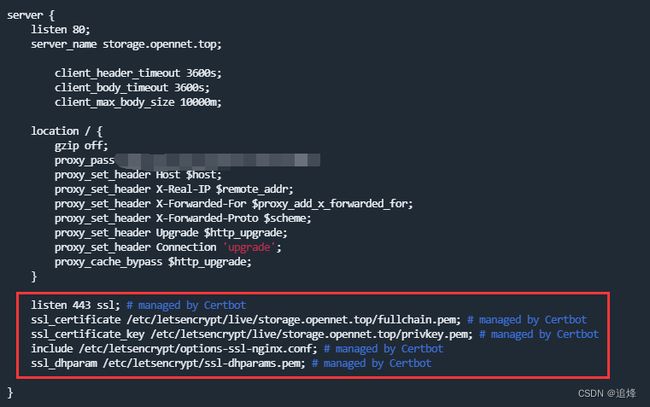
- 内网IP地址SSL证书申请指南
安全
SSL/TLS证书是保障网站和服务安全的重要工具,能够加密数据传输并验证服务器身份。然而,对于局域网/内网IP地址而言,申请SSL证书的过程具有一定的特殊性,以下是一份详细的攻略:一、了解局域网/内网IP地址的特殊性唯一性问题:局域网/内网IP地址在内部网络中可能具有唯一性,但在整个互联网中并不唯一。访问限制:局域网/内网IP地址通常只能在内部网络中访问,无法从外部网络直接访问。二、选择证书颁发机
- 云智慧:拥抱AI算法驱动的智能运维服务创新引擎
随着信息化、数字化、智能化的加码,企业对人工智能、大数据等技术应用呈现出明显兴趣,海笔研究对国内中型规模企业调研表明,在2020年,54.1%的企业选择购买人工智能类应用,41.9%的企业选择购买大数据及BI类应用,各类产品软件的应用大幅提升了企业信息系统复杂度,以及运维管理难度。业务发展催生服务需求从系统管理者角度出发,信息系统从“单机Excel表格”到“集中式单系统”再到“微服务、云架构”等,
- Nginx多台服务器负载均衡
PS测
服务器nginx负载均衡
一操作步骤:1.服务器IP45.114.124.215//主服务器(安装Nginx)45.114.124.99//从服务器(安装Nginx或Apache都可以)2.保证2台服务器网络互通3.在2台服务器上设置不同页面方便验证3.1在主服务器添加一个可以访问的站点3.2在次服务器添加一个站点,端口必须是主服务器在nginx指定给次服务器的端口4.在主服务器45.114.124.215安装Nginx,
- JVM 类加载器之间的层次关系,以及类加载的委托机制
冰糖心书房
JVM2025Java面试系列javajvm
JVM类加载器之间存在一种层次关系,通常被称为双亲委派模型(ParentDelegationModel)。这种层次关系和委托机制是Java类加载机制的核心,对于保证Java程序的安全性和避免类冲突至关重要。1.类加载器的层次关系:JVM中的类加载器(ClassLoader)主要分为以下几种,它们之间存在自顶向下的层次关系(父子关系,但不是继承关系,而是组合关系):启动类加载器(BootstrapC
- 字节跳动离职后,转行学起了AI大模型!该说不说,真的香!!
小城哇哇
人工智能AI大模型语言模型agiaiLLM转行
个人自我介绍鄙人出生于南方小乡镇,为了走出小镇,在当地够拼够努力,不是自夸,确确实实也算得上“别人家的小孩”,至少在学习这件事情少,没有要家里人操过心。高考特别顺利,一个老牌985,具体哪个学校就不说了,不想给母校丢脸。毕业后,也算是“风光”地进入了字节跳动。做的是运维测试。在职期间刚入职的时候真的信心满满⛽️,但才3天就感受到了互联网头部公司的强度不是一般的大。明面上的早十晚八工作制完全不存在,
- Mac安装 brew
潇凝子潇
macosbrew
MacBook-Pro.ssh%/bin/bash-c"$(curl-fsSLhttps://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"==>Checkingfor`sudo`access(whichmayrequestyourpassword)...Password:==>Thisscriptwillinstall:/
- 交换机救命命令手册:华为 & 思科平台最全运维指令速查表
IT程序媛-桃子
数通华为认证服务器运维
引言:这是一份救命的交换机运维秘籍在交换机配置与故障排查过程中,不论你是初入网络世界的小白,还是年资数年的资深工程师,总会遇到那些“关键时刻靠得住的命令”。这篇文章,我将整理一份覆盖华为+思科双平台的实战命令手册,从最基础的设备状态查看,到VLAN、STP、防环、LACP、QOS、抓包、限速、安全加固等操作,通通囊括。关键时刻,拿来即用,就是这篇的全部意义。01️⃣基础生存命令:先活下来再说场景华
- Redis桌面工具:Tiny RDM
微刻时光
微秒速递redis数据库缓存笔记
1.TinyRDM介绍TinyRDM(TinyRedisDesktopManager)是一个现代化、轻量级的Redis桌面客户端,支持Linux、Mac和Windows操作系统。它专为开发和运维人员设计,使得与Redis服务器的交互操作更加便捷愉快。TinyRDM提供了丰富的Redis数据操作功能,具备现代化的界面设计和良好的用户体验,使得Redis的管理和运维变得更加简单高效。2.核心功能极致轻
- SpringCloud框架下的注册中心比较:Eureka与Consul的实战解析
耶耶Norsea
网络杂烩springcloud
摘要在探讨SpringCloud框架中的两种注册中心之前,有必要回顾单体架构与分布式架构的特点。单体架构将所有业务功能集成在一个项目中,优点是架构简单、部署成本低,但耦合度高。分布式架构则根据业务功能对系统进行拆分,每个模块作为独立服务开发,降低了服务间的耦合,便于升级和扩展,然而其复杂性增加,运维、监控和部署难度也随之提高。关键词SpringCloud,注册中心,单体架构,分布式架构,服务拆分一
- 运维面试题(七)
a_j58
运维
1.statefulset用来管理有状态的应用程序,有状态是什么意思?每一个pod都有一个固定的网络标识符,在整个生命周期中不会改变。每个实例都可以拥有自己的持久化存储卷,即使容器被删除并重新创建,存储卷仍然存在。StatefulSet确保了Pod按照顺序启动、更新和终止。2.主键是什么,它与索引有什么关系?主键确保表中每一行数据都可以被唯一标识,避免数据重复。主键通常会自动创建一个唯一索引,加快
- 云原生工程师必修课:如何揪出“假忙真闲”的应用元凶
YAMLMaster
面试题kubernetes运维开发devops
Tagamanent,Spain引言这是一个再经典不过的面试题了,希望大家能学到精髓。开始介绍在分布式系统和高并发场景中,高负载(HighLoad)与低使用率(LowUtilization)的共存矛盾是运维和开发者的常见挑战。这种问题往往隐蔽性强,传统监控指标难以直接定位根因。本文从系统层、应用层、架构层多维度拆解,提供一套完整的排查与优化方法论。核心概念厘清•负载(Load):系统当前待处理任务
- k8s运维 设置Pod实现JVM内存根据容器内存动态调整
风行無痕
K8Skubernetesjvm容器
一、实现方式推荐方案:利用JVM容器感知特性,按比例动态分配。适用场景:动态根据Pod内存限制自动分配堆内存,无需硬编码参数Java要求:Java8u191+或Java11+Java8u191+或Java11+支持通过-XX:InitialRAMPercentage替代-Xms,根据容器内存限制自动计算堆内存。在容器环境变量中配置-XX:MaxRAMPercentage=75.0,使JVM根据容
- MongoDB慢日志查询及索引创建
laolitou_1024
中间件微服务数据库mongodb
MongoDB的慢日志(SlowQueryLog)对于运维和程序员来说都非常重要,因为它直接关系到数据库的性能和应用程序的稳定性。以下分享介绍下MongoDB慢日志查询及索引创建相关的一些笔记。一,准备1.使用db.currentOp()实时监控db.currentOp()可以查看当前正在执行的操作,适合捕捉瞬时的高CPU操作。db.currentOp()示例:过滤长时间运行的操作db.curre
- CPU占用率飙升至100%:是攻击还是正常现象?
群联云防护小杜
安全问题汇总ddos安全waf服务器cpu占用被攻击
在运维和开发的日常工作中,CPU占用率突然飙升至100%往往是一个令人紧张的信号。这可能意味着服务器正在遭受攻击,但也可能是由于某些正常的、但资源密集型的任务或进程造成的。本文将探讨如何识别和应对服务器的异常CPU占用情况,并通过Python脚本示例,提供一种监控和诊断CPU占用率的方法。一、CPU占用率100%:攻击or正常?1.1攻击迹象持续性高占用:如果CPU占用率长时间保持在100%,且没
- 一文读懂 Linux 下 Docker 搭建及简单应用
Waitccy
linuxdocker运维服务器
一、引言在Linux系统的运维与开发场景中,Docker凭借其高效的容器化技术,极大地简化了应用部署与管理流程。它打破了传统环境配置的复杂性,实现应用及其依赖的封装,确保在不同环境中稳定运行。本文将详细介绍在Linux系统下搭建Docker的步骤,并通过几个简单应用示例,带你快速上手Docker。二、Linux下Docker搭建(一)准备工作系统要求:建议使用主流的Linux发行版,如Ubuntu
- Android安全通信实现
Ya-Jun
android安全
Android安全通信实现前言在移动应用开发中,网络通信安全至关重要。本文将详细介绍Android平台上的安全通信实现方案,包括HTTPS协议、证书验证、双向认证等核心技术,帮助开发者构建安全可靠的网络通信机制。一、HTTPS基础知识1.1HTTPS原理HTTPS(超文本传输安全协议)是HTTP协议的安全版本,通过SSL/TLS协议进行加密通信,确保数据传输的安全性。1.1.1SSL/TLS协议工
- 于STM32F103C8T6的智能灯泡控制系统C++源码实现
程序员Thomas
STM32单片机智能灯泡stm32c++嵌入式硬件
以下是一个基于STM32F103C8T6的智能灯泡控制系统C++源码实现,整合了PWM调光、WiFi控制和环境感知功能。该代码已在STM32CubeIDE中验证,支持直接烧录运行:#include"main.h"#include#include"wifi.h"//LED设备抽象类(3设计)classLEDDevice{protected:TIM_HandleTypeDef*pwmTimer;uin
- 188.HarmonyOS NEXT系列教程之列表切换案例工具类与最佳实践
harmonyos-next
温馨提示:本篇博客的详细代码已发布到git:https://gitcode.com/nutpi/HarmonyosNext可以下载运行哦!HarmonyOSNEXT系列教程之列表切换案例工具类与最佳实践效果演示1.日志工具类1.1Logger类实现classLogger{privatedomain:number;privateprefix:string;privateformat:string='
- 186.HarmonyOS NEXT系列教程之列表切换案例数据管理详解
harmonyos-next
温馨提示:本篇博客的详细代码已发布到git:https://gitcode.com/nutpi/HarmonyosNext可以下载运行哦!HarmonyOSNEXT系列教程之列表切换案例数据管理详解效果演示1.数据模型设计1.1ListInfo类@ObservedexportclassListInfo{//列表项数据结构icon:ResourceStr='';//图标资源name:Resource
- java线程的无限循环和退出
3213213333332132
java
最近想写一个游戏,然后碰到有关线程的问题,网上查了好多资料都没满足。
突然想起了前段时间看的有关线程的视频,于是信手拈来写了一个线程的代码片段。
希望帮助刚学java线程的童鞋
package thread;
import java.text.SimpleDateFormat;
import java.util.Calendar;
import java.util.Date
- tomcat 容器
BlueSkator
tomcatWebservlet
Tomcat的组成部分 1、server
A Server element represents the entire Catalina servlet container. (Singleton) 2、service
service包括多个connector以及一个engine,其职责为处理由connector获得的客户请求。
3、connector
一个connector
- php递归,静态变量,匿名函数使用
dcj3sjt126com
PHP递归函数匿名函数静态变量引用传参
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Current To-Do List</title>
</head>
<body>
- 属性颜色字体变化
周华华
JavaScript
function changSize(className){
var diva=byId("fot")
diva.className=className;
}
</script>
<style type="text/css">
.max{
background: #900;
color:#039;
- 将properties内容放置到map中
g21121
properties
代码比较简单:
private static Map<Object, Object> map;
private static Properties p;
static {
//读取properties文件
InputStream is = XXX.class.getClassLoader().getResourceAsStream("xxx.properti
- [简单]拼接字符串
53873039oycg
字符串
工作中遇到需要从Map里面取值拼接字符串的情况,自己写了个,不是很好,欢迎提出更优雅的写法,代码如下:
import java.util.HashMap;
import java.uti
- Struts2学习
云端月影
最近开始关注struts2的新特性,从这个版本开始,Struts开始使用convention-plugin代替codebehind-plugin来实现struts的零配置。
配置文件精简了,的确是简便了开发过程,但是,我们熟悉的配置突然disappear了,真是一下很不适应。跟着潮流走吧,看看该怎样来搞定convention-plugin。
使用Convention插件,你需要将其JAR文件放
- Java新手入门的30个基本概念二
aijuans
java新手java 入门
基本概念: 1.OOP中唯一关系的是对象的接口是什么,就像计算机的销售商她不管电源内部结构是怎样的,他只关系能否给你提供电就行了,也就是只要知道can or not而不是how and why.所有的程序是由一定的属性和行为对象组成的,不同的对象的访问通过函数调用来完成,对象间所有的交流都是通过方法调用,通过对封装对象数据,很大限度上提高复用率。 2.OOP中最重要的思想是类,类是模板是蓝图,
- jedis 简单使用
antlove
javarediscachecommandjedis
jedis.RedisOperationCollection.java
package jedis;
import org.apache.log4j.Logger;
import redis.clients.jedis.Jedis;
import java.util.List;
import java.util.Map;
import java.util.Set;
pub
- PL/SQL的函数和包体的基础
百合不是茶
PL/SQL编程函数包体显示包的具体数据包
由于明天举要上课,所以刚刚将代码敲了一遍PL/SQL的函数和包体的实现(单例模式过几天好好的总结下再发出来);以便明天能更好的学习PL/SQL的循环,今天太累了,所以早点睡觉,明天继续PL/SQL总有一天我会将你永远的记载在心里,,,
函数;
函数:PL/SQL中的函数相当于java中的方法;函数有返回值
定义函数的
--输入姓名找到该姓名的年薪
create or re
- Mockito(二)--实例篇
bijian1013
持续集成mockito单元测试
学习了基本知识后,就可以实战了,Mockito的实际使用还是比较麻烦的。因为在实际使用中,最常遇到的就是需要模拟第三方类库的行为。
比如现在有一个类FTPFileTransfer,实现了向FTP传输文件的功能。这个类中使用了a
- 精通Oracle10编程SQL(7)编写控制结构
bijian1013
oracle数据库plsql
/*
*编写控制结构
*/
--条件分支语句
--简单条件判断
DECLARE
v_sal NUMBER(6,2);
BEGIN
select sal into v_sal from emp
where lower(ename)=lower('&name');
if v_sal<2000 then
update emp set
- 【Log4j二】Log4j属性文件配置详解
bit1129
log4j
如下是一个log4j.properties的配置
log4j.rootCategory=INFO, stdout , R
log4j.appender.stdout=org.apache.log4j.ConsoleAppender
log4j.appender.stdout.layout=org.apache.log4j.PatternLayout
log4j.appe
- java集合排序笔记
白糖_
java
public class CollectionDemo implements Serializable,Comparable<CollectionDemo>{
private static final long serialVersionUID = -2958090810811192128L;
private int id;
private String nam
- java导致linux负载过高的定位方法
ronin47
定位java进程ID
可以使用top或ps -ef |grep java
![图片描述][1]
根据进程ID找到最消耗资源的java pid
比如第一步找到的进程ID为5431
执行
top -p 5431 -H
![图片描述][2]
打印java栈信息
$ jstack -l 5431 > 5431.log
在栈信息中定位具体问题
将消耗资源的Java PID转
- 给定能随机生成整数1到5的函数,写出能随机生成整数1到7的函数
bylijinnan
函数
import java.util.ArrayList;
import java.util.List;
import java.util.Random;
public class RandNFromRand5 {
/**
题目:给定能随机生成整数1到5的函数,写出能随机生成整数1到7的函数。
解法1:
f(k) = (x0-1)*5^0+(x1-
- PL/SQL Developer保存布局
Kai_Ge
近日由于项目需要,数据库从DB2迁移到ORCAL,因此数据库连接客户端选择了PL/SQL Developer。由于软件运用不熟悉,造成了很多麻烦,最主要的就是进入后,左边列表有很多选项,自己删除了一些选项卡,布局很满意了,下次进入后又恢复了以前的布局,很是苦恼。在众多PL/SQL Developer使用技巧中找到如下这段:
&n
- [未来战士计划]超能查派[剧透,慎入]
comsci
计划
非常好看,超能查派,这部电影......为我们这些热爱人工智能的工程技术人员提供一些参考意见和思想........
虽然电影里面的人物形象不是非常的可爱....但是非常的贴近现实生活....
&nbs
- Google Map API V2
dai_lm
google map
以后如果要开发包含google map的程序就更麻烦咯
http://www.cnblogs.com/mengdd/archive/2013/01/01/2841390.html
找到篇不错的文章,大家可以参考一下
http://blog.sina.com.cn/s/blog_c2839d410101jahv.html
1. 创建Android工程
由于v2的key需要G
- java数据计算层的几种解决方法2
datamachine
javasql集算器
2、SQL
SQL/SP/JDBC在这里属于一类,这是老牌的数据计算层,性能和灵活性是它的优势。但随着新情况的不断出现,单纯用SQL已经难以满足需求,比如: JAVA开发规模的扩大,数据量的剧增,复杂计算问题的涌现。虽然SQL得高分的指标不多,但都是权重最高的。
成熟度:5星。最成熟的。
- Linux下Telnet的安装与运行
dcj3sjt126com
linuxtelnet
Linux下Telnet的安装与运行 linux默认是使用SSH服务的 而不安装telnet服务 如果要使用telnet 就必须先安装相应的软件包 即使安装了软件包 默认的设置telnet 服务也是不运行的 需要手工进行设置 如果是redhat9,则在第三张光盘中找到 telnet-server-0.17-25.i386.rpm
- PHP中钩子函数的实现与认识
dcj3sjt126com
PHP
假如有这么一段程序:
function fun(){
fun1();
fun2();
}
首先程序执行完fun1()之后执行fun2()然后fun()结束。
但是,假如我们想对函数做一些变化。比如说,fun是一个解析函数,我们希望后期可以提供丰富的解析函数,而究竟用哪个函数解析,我们希望在配置文件中配置。这个时候就可以发挥钩子的力量了。
我们可以在fu
- EOS中的WorkSpace密码修改
蕃薯耀
修改WorkSpace密码
EOS中BPS的WorkSpace密码修改
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
蕃薯耀 201
- SpringMVC4零配置--SpringSecurity相关配置【SpringSecurityConfig】
hanqunfeng
SpringSecurity
SpringSecurity的配置相对来说有些复杂,如果是完整的bean配置,则需要配置大量的bean,所以xml配置时使用了命名空间来简化配置,同样,spring为我们提供了一个抽象类WebSecurityConfigurerAdapter和一个注解@EnableWebMvcSecurity,达到同样减少bean配置的目的,如下:
applicationContex
- ie 9 kendo ui中ajax跨域的问题
jackyrong
AJAX跨域
这两天遇到个问题,kendo ui的datagrid,根据json去读取数据,然后前端通过kendo ui的datagrid去渲染,但很奇怪的是,在ie 10,ie 11,chrome,firefox等浏览器中,同样的程序,
浏览起来是没问题的,但把应用放到公网上的一台服务器,
却发现如下情况:
1) ie 9下,不能出现任何数据,但用IE 9浏览器浏览本机的应用,却没任何问题
- 不要让别人笑你不能成为程序员
lampcy
编程程序员
在经历六个月的编程集训之后,我刚刚完成了我的第一次一对一的编码评估。但是事情并没有如我所想的那般顺利。
说实话,我感觉我的脑细胞像被轰炸过一样。
手慢慢地离开键盘,心里很压抑。不禁默默祈祷:一切都会进展顺利的,对吧?至少有些地方我的回答应该是没有遗漏的,是不是?
难道我选择编程真的是一个巨大的错误吗——我真的永远也成不了程序员吗?
我需要一点点安慰。在自我怀疑,不安全感和脆弱等等像龙卷风一
- 马皇后的贤德
nannan408
马皇后不怕朱元璋的坏脾气,并敢理直气壮地吹耳边风。众所周知,朱元璋不喜欢女人干政,他认为“后妃虽母仪天下,然不可使干政事”,因为“宠之太过,则骄恣犯分,上下失序”,因此还特地命人纂述《女诫》,以示警诫。但马皇后是个例外。
有一次,马皇后问朱元璋道:“如今天下老百姓安居乐业了吗?”朱元璋不高兴地回答:“这不是你应该问的。”马皇后振振有词地回敬道:“陛下是天下之父,
- 选择某个属性值最大的那条记录(不仅仅包含指定属性,而是想要什么属性都可以)
Rainbow702
sqlgroup by最大值max最大的那条记录
好久好久不写SQL了,技能退化严重啊!!!
直入主题:
比如我有一张表,file_info,
它有两个属性(但实际不只,我这里只是作说明用):
file_code, file_version
同一个code可能对应多个version
现在,我想针对每一个code,取得它相关的记录中,version 值 最大的那条记录,
SQL如下:
select
*
- VBScript脚本语言
tntxia
VBScript
VBScript 是基于VB的脚本语言。主要用于Asp和Excel的编程。
VB家族语言简介
Visual Basic 6.0
源于BASIC语言。
由微软公司开发的包含协助开发环境的事
- java中枚举类型的使用
xiao1zhao2
javaenum枚举1.5新特性
枚举类型是j2se在1.5引入的新的类型,通过关键字enum来定义,常用来存储一些常量.
1.定义一个简单的枚举类型
public enum Sex {
MAN,
WOMAN
}
枚举类型本质是类,编译此段代码会生成.class文件.通过Sex.MAN来访问Sex中的成员,其返回值是Sex类型.
2.常用方法
静态的values()方