企业网络安全架构设计之IPSec VPN应用配置举例
文章目录
- 1. 需求分析
-
- 组网拓扑:
- 组网需求:
- 2. 地址规划
-
- 终端设备地址规划:
- 网络设备地址规划:
- 3. 防火墙接口区域规划
- 4. 分支机构内网配置
-
- LSW4交换机配置
- FW1防火墙配置
- 检查配置情况
- 5. 分支机构外网配置
-
- 防火墙外网地址配置
- 防火墙NAT配置
- 防火墙安全策略配置
- 防火墙路由配置
- 6. 互联网路由器配置【R1】
-
- 接口IP地址配置
- 7. 总部内外网配置
-
- LSW3交换机配置
- FW2防火墙基础配置
- FW3防火墙基础配置
- 防火墙双机热备配置
- 检查双机热备配置情况
- 在FW2主防火墙上配置回程路由
- 在FW2主防火墙上配置安全策略与NAT策略
- 8. 测试总部相关配置情况
-
- 使用Client1访问总部Web服务器
- PC4访问公网DNS服务器
- 9. IPSec VPN配置
-
- 分部配置
- 总部配置
- 10. 测试分部访问总部内网资源情况
-
- 分部访问总部FTP资源
- 分部访问总部PC4
- 11. 公网DNS域名配置
1. 需求分析
组网拓扑:
组网需求:
-
分支机构内部业务Vlan为vlan 10与vlan 20,通过FW1的DHCP服务获取相关网络配置信息。分支机构中Vlan 30为外网Vlan,PC5只可以访问公网,无法通过IPSec访问总部内网资源。
-
分支机构Client1与PC2需要访问总部内部的FTP服务器,为保证数据访问的安全性,采用IPSec VPN的方式通过公网进行资源访问。
-
为保证分支机构访问总部数据的可靠性,总部出口处采用双击热备的方式进行组网。
2. 地址规划
终端设备地址规划:
| 名称 | 所属Vlan | IP地址/掩码 |
|---|---|---|
| Client1 | 10 | 10.1.1.2/24【不支持DHCP,采用手工静态配置】 |
| PC2 | 20 | DHCP获取【网段10.1.1.0/24】 |
| PC5 | 30 | DHCP获取【网段192.168.30.0/24】 |
| 公网DNS | / | 8.8.8.8 |
| Web | 100 | 172.18.17.10/24 |
| FTP | 200 | 192.168.2.2/24 |
| PC4 | 300 | 192.168.3.2/24 |
网络设备地址规划:
| 名称 | 接口 | IP地址/掩码 | 备注 |
|---|---|---|---|
| FW1 | GE1/0/1.10 | 10.1.1.1/24 | Vlan10网关地址 |
| GE1/0/1.20 | 10.1.2.1/24 | Vlan20网关地址 | |
| GE1/0/1.30 | 192.168.30.1/24 | Vlan30网关地址 | |
| GE1/0/0 | 111.160.10.2/30 | 外网出口地址 | |
| R1 | GE0/0/0 | 111.160.10.1/30 | 分支机构互联网网关地址 |
| GE0/0/2 | 8.8.8.1/24 | 公网DNS网关地址 | |
| GE0/0/1 | 111.160.20.1/30 | 总部互联网网关地址 | |
| FW2 | GE1/0/0 | 172.16.1.1/27 | 互联网侧实地址,虚地址为111.160.20.2/30 |
| GE1/0/2 | 1.1.1.1/24 | 心跳地址 | |
| GE1/0/1 | 192.168.100.3/27 | 内网侧实地址,虚地址为192.168.100.1/27 | |
| FW3 | GE1/0/0 | 172.16.1.2/27 | 互联网侧实地址,虚地址为111.160.20.2/30 |
| GE1/0/2 | 1.1.1.2/24 | 心跳地址 | |
| GE1/0/1 | 192.168.100.4/27 | 内网侧实地址,虚地址为192.168.100.1/27 | |
| LSW3 | Vlanif100 | 172.18.17.1/24 | Vlan100网关地址 |
| Vlanif200 | 192.168.2.1/24 | Vlan200网关地址 | |
| Vlanif300 | 192.168.3.1/24 | Vlan300网关地址 | |
| Vlanif1000 | 192.168.100.2/27 | 上联防火墙地址 |
3. 防火墙接口区域规划
| 名称 | 接口 | 所属区域 |
|---|---|---|
| FW1 | GE1/0/1 | Trust |
| GE1/0/1.10 | Trust | |
| GE1/0/1.20 | Trust | |
| GE1/0/1.30 | Trust | |
| GE1/0/0 | Untrust | |
| FW2 | GE1/0/0 | Untrust |
| GE1/0/2 | DMZ | |
| GE1/0/1 | Trust | |
| FW3 | GE1/0/0 | Untrust |
| GE1/0/2 | DMZ | |
| GE1/0/1 | Trust |
4. 分支机构内网配置
LSW4交换机配置
- 创建Vlan
vlan batch 10 20 30
- 配置接口模式,连接终端的接口开启边缘端口加快转发
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
stp edged-port enable
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
stp edged-port enable
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 30
stp edged-port enable
#
interface GigabitEthernet0/0/4
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 30
stp edged-port enable
FW1防火墙配置
防火墙初始用户名与密码:admin/Admin@123【初次登陆需要修改密码,修改后的密码为huawei@123】
- 开启DHCP服务
dhcp enable
- 创建业务Vlan
vlan batch 10 20 30
- 创建内网三层子接口,设置封装类型与关联的Vlan id;配置IP地址,并开启DHCP服务,DNS配置公网DNS 8.8.8.8
interface GigabitEthernet1/0/1.10
vlan-type dot1q 10
ip address 10.1.1.1 255.255.255.0
service-manage ping permit
dhcp select interface
dhcp server dns-list 8.8.8.8
#
interface GigabitEthernet1/0/1.20
vlan-type dot1q 20
ip address 10.1.2.1 255.255.255.0
service-manage ping permit
dhcp select interface
dhcp server dns-list 8.8.8.8
#
interface GigabitEthernet1/0/1.30
vlan-type dot1q 30
ip address 192.168.30.1 255.255.255.0
service-manage ping permit
dhcp select interface
dhcp server dns-list 8.8.8.8
- 接口划分至安全区域
firewall zone trust
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/1.10
add interface GigabitEthernet1/0/1.20
add interface GigabitEthernet1/0/1.30#
firewall zone untrust
add interface GigabitEthernet1/0/0
- 配置DHCP安全策略,使终端可以获取IP地址
security-policy
rule name DHCP
source-zone local
source-zone trust
destination-zone local
destination-zone trust
action permit
检查配置情况
5. 分支机构外网配置
防火墙外网地址配置
interface GigabitEthernet1/0/0
ip address 111.160.10.2 30
防火墙NAT配置
nat-policy
rule name to_internet
source-zone trust
destination-zone untrust
action source-nat easy-ip
防火墙安全策略配置
security-policy
rule name to_internet
source-zone trust
destination-zone untrust
action permit
防火墙路由配置
ip route-static 0.0.0.0 0 111.160.10.1
6. 互联网路由器配置【R1】
接口IP地址配置
interface GigabitEthernet0/0/0
ip address 111.160.10.1 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 111.160.20.1 255.255.255.252
#
interface GigabitEthernet0/0/2
ip address 8.8.8.1 255.255.255.0
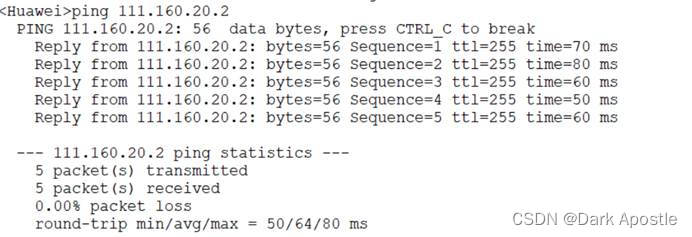
IP地址配置完成后,分支机构的PC可以ping通DNS服务器地址8.8.8.8
7. 总部内外网配置
LSW3交换机配置
- 创建业务Vlan
vlan batch 100 200 300 1000 //vlan 100 200 300为业务Vlan;Vlan1000为交换机与防火墙互联Vlan
- 配置接口所属Vlan,配置边缘端口加快转发
interface GigabitEthernet0/0/1
port link-type access
port default vlan 1000
stp edged-port enable
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 1000
stp edged-port enable
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 100
stp edged-port enable
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 200
stp edged-port enable
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 300
stp edged-port enable
#
- 配置IP地址
interface Vlanif100
ip address 172.18.17.1 255.255.255.0
#
interface Vlanif200
ip address 192.168.2.1 255.255.255.0
#
interface Vlanif300
ip address 192.168.3.1 255.255.255.0
#
interface Vlanif1000
ip address 192.168.100.2 255.255.255.224
#
- 配置默认路由
ip route-static 0.0.0.0 0 192.168.100.1 //下一跳地址为防火墙的虚地址
- 配置安全防护策略
由于Web服务器提供对外访问,属于DMZ区域,需要在核心交换机上配置策略使其不能访问内网资源。
#
acl number 3000
rule 5 deny ip source 172.18.17.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 10 deny ip source 172.18.17.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 15 permit ip
#
traffic classifier geli operator and
if-match acl 3000
#
traffic behavior geli
permit
#
traffic policy geli
classifier geli behavior geli
#
vlan 100
traffic-policy geli inbound
FW2防火墙基础配置
防火墙初始用户名与密码:admin/Admin@123【初次登陆需要修改密码,修改后的密码为huawei@123】
- 接口IP地址配置
interface GigabitEthernet1/0/0
undo shutdown
ip address 172.16.1.1 255.255.255.224
service-manage ping permit //外网接口一般不允许ping,不建议打开ping功能,此为实验环境仅做测试使用
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.100.3 255.255.255.224
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.1 255.255.255.0
#
- 安全区域配置
firewall zone trust
add interface GigabitEthernet1/0/1
#
firewall zone untrust
add interface GigabitEthernet1/0/0
#
firewall zone dmz
add interface GigabitEthernet1/0/2
#
FW3防火墙基础配置
防火墙初始用户名与密码:admin/Admin@123【初次登陆需要修改密码,修改后的密码为huawei@123】
- 接口IP地址配置
interface GigabitEthernet1/0/0
undo shutdown
ip address 172.16.1.2 255.255.255.224
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.100.4 255.255.255.224
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.2 255.255.255.0
#
- 安全区域配置
firewall zone trust
add interface GigabitEthernet1/0/1
#
firewall zone untrust
add interface GigabitEthernet1/0/0
#
firewall zone dmz
add interface GigabitEthernet1/0/2
#
防火墙双机热备配置
FW2为双机热备的主防火墙,FW3作为备防火墙,当FW2故障后FW3切换为主防火墙进行数据转发工作
- FW2的VGMP配置
interface GigabitEthernet1/0/0
vrrp vrid 1 virtual-ip 111.160.20.2 255.255.255.252 active
vrrp vrid 1 timer advertise 30
#
interface GigabitEthernet1/0/1
vrrp vrid 2 virtual-ip 192.168.100.1 active
vrrp vrid 2 timer advertise 30
#
- FW3的VGMP配置
interface GigabitEthernet1/0/0
vrrp vrid 1 virtual-ip 111.160.20.2 255.255.255.252 standby
vrrp vrid 1 timer advertise 30
#
interface GigabitEthernet1/0/1
vrrp vrid 2 virtual-ip 192.168.100.1 standby
vrrp vrid 2 timer advertise 30
#
- 配置心跳接口,开启双机热备
FW2:
hrp interface GigabitEthernet1/0/2 remote 1.1.1.2
hrp enable
FW3:
hrp interface GigabitEthernet1/0/2 remote 1.1.1.1
hrp enable
检查双机热备配置情况
- FW2与FW3查看hrp状态、VGMP状态
在FW2主防火墙上配置回程路由
由于静态路由默认不会同步至备墙,需要配置命令用来开启静态路由同步,然后同步配置备份。
FW2:
ip route-static 172.18.17.0 255.255.255.0 192.168.100.2
ip route-static 192.168.2.0 255.255.255.0 192.168.100.2
ip route-static 192.168.3.0 255.255.255.0 192.168.100.2
hrp auto-sync config static-route //开启静态路由配置同步
hrp sync config //退回至用户视图,使用该命令将主墙配置同步至备墙
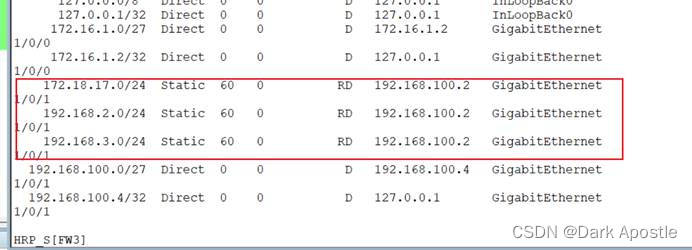
- 在备墙上查看路由表
在FW2主防火墙上配置安全策略与NAT策略
安全策略与NAT策略配置完成后会直接同步至备墙
目的:使办公终端可以上网,同时将Web网站映射至公网上,供互联网用户访问该资源。
- 配置安全策略
【Web服务器与PC终端上网策略】
#
security-policy
rule name to_internet
source-zone trust
destination-zone untrust
source-address 172.18.17.0 mask 255.255.255.0
source-address 192.168.3.0 mask 255.255.255.0
action permit
#
【公网用户访问Web服务器策略】
#
rule name web
source-zone untrust
destination-zone trust
destination-address 172.18.17.10 mask 255.255.255.255
action permit
#
- 配置NAT地址池
#
nat address-group addr 1
mode no-pat global
route enable
section 1 111.160.20.2 111.160.20.2
#
- 配置NAT策略
nat-policy
rule name to_internet
source-zone trust
destination-zone untrust
source-address 172.18.17.0 mask 255.255.255.0
source-address 192.168.3.0 mask 255.255.255.0
action source-nat address-group addr
- 配置默认路由
ip route-static 0.0.0.0 0 111.160.20.1
HRP_Mhrp sync config //同步配置
- 配置Web服务器对外映射
nat server protocol tcp global 111.160.20.2 www inside 172.18.17.10 www
8. 测试总部相关配置情况
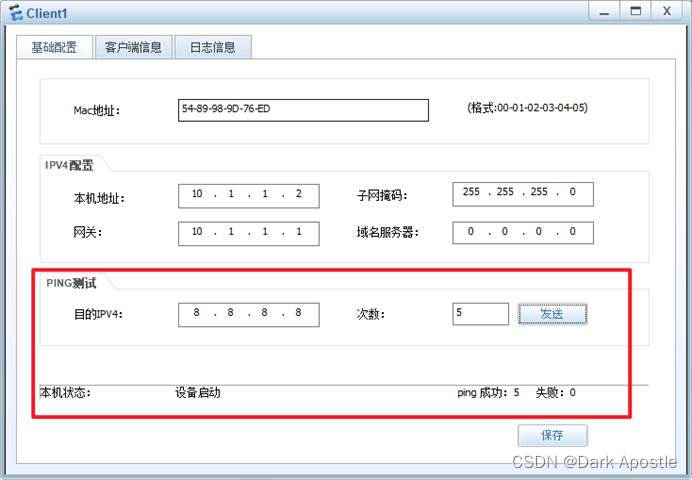
使用Client1访问总部Web服务器
PC4访问公网DNS服务器
9. IPSec VPN配置
分部配置
- 配置IKE提议
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
- 配置IKE对等体
ike peer zongbu
pre-shared-key huawei@123
ike-proposal 1
remote-address 111.160.120.2
- 配置感兴趣流
acl number 3001
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 15 permit ip source 10.1.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 20 permit ip source 10.1.2.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
- 配置IPSec提议
ipsec proposal 1
transform ah-esp
ah authentication-algorithm sha2-256
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
- 配置IPSec策略
ipsec policy to-zongbu 1 isakmp
security acl 3001
ike-peer zongbu
proposal 1
- 应用至接口
interface GigabitEthernet1/0/0
ipsec policy to-zongbu
- 配置NAT策略,针对感兴趣流不做NAT转换,将该策略放置NAT策略最前端
nat-policy
rule name ipsec-data
source-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 192.168.2.0 mask 255.255.255.0
destination-address 192.168.3.0 mask 255.255.255.0
action no-nat
quit
rule move ipsec-data up
- 配置安全策略用于IPSec连接建立
【通常情况放通ESP服务与UDP 500端口即可,实验环境服务全部放通】
security-policy
rule name ipsec-connect1
source-zone local
destination-zone untrust
source-address 111.160.10.2 mask 255.255.255.255
destination-address 111.160.20.2 mask 255.255.255.255
action permit
rule name ipsec-connect2
source-zone untrust
destination-zone local
source-address 111.160.20.2 mask 255.255.255.255
destination-address 111.160.10.2 mask 255.255.255.255
action permit
- 配置安全策略用于分部与总部之前内网流量互访
security-policy
rule name ipsec-data-out
source-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 192.168.2.0 mask 255.255.255.0
destination-address 192.168.3.0 mask 255.255.255.0
action permit
rule name ipsec-data-in
source-zone untrust
destination-zone trust
source-address 192.168.2.0 mask 255.255.255.0
source-address 192.168.3.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action permit
总部配置
- 配置IKE提议
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
- 配置IKE对等体
ike peer fenbu
pre-shared-key huawei@123
ike-proposal 1
remote-address 111.160.10.2
- 配置感兴趣流
acl number 3001
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 15 permit ip source 192.168.3.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
rule 20 permit ip source 192.168.3.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
- 配置IPSec提议
ipsec proposal 1
transform ah-esp
ah authentication-algorithm sha2-256
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
- 配置IPSec策略
ipsec policy to-fenbu 1 isakmp
security acl 3001
ike-peer fenbu
proposal 1
- 应用至接口
interface GigabitEthernet1/0/0
ipsec policy to-fenbu
- 配置NAT策略,针对感兴趣流不做NAT转换,将该策略放置NAT策略最前端
nat-policy
rule name ipsec-data
source-zone trust
destination-zone untrust
source-address 192.168.2.0 mask 255.255.255.0
source-address 192.168.3.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action no-nat
quit
rule move ipsec-data up
- 配置安全策略用于IPSec连接建立
【通常情况放通ESP服务与UDP 500端口即可,实验环境服务全部放通】
security-policy
rule name ipsec-connect1
source-zone local
destination-zone untrust
source-address 111.160.20.2 mask 255.255.255.255
destination-address 111.160.10.2 mask 255.255.255.255
action permit
rule name ipsec-connect2
source-zone untrust
destination-zone local
source-address 111.160.10.2 mask 255.255.255.255
destination-address 111.160.20.2 mask 255.255.255.255
action permit
- 配置安全策略用于分部与总部之前内网流量互访
security-policy
rule name ipsec-data-in
source-zone untrust
destination-zone trust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 192.168.2.0 mask 255.255.255.0
destination-address 192.168.3.0 mask 255.255.255.0
action permit
rule name ipsec-data-out
source-zone trust
destination-zone untrust
source-address 192.168.2.0 mask 255.255.255.0
source-address 192.168.3.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action permit
10. 测试分部访问总部内网资源情况
分部访问总部FTP资源
分部Clinet1终端可以访问总部FTP服务器资源,可正常下载。
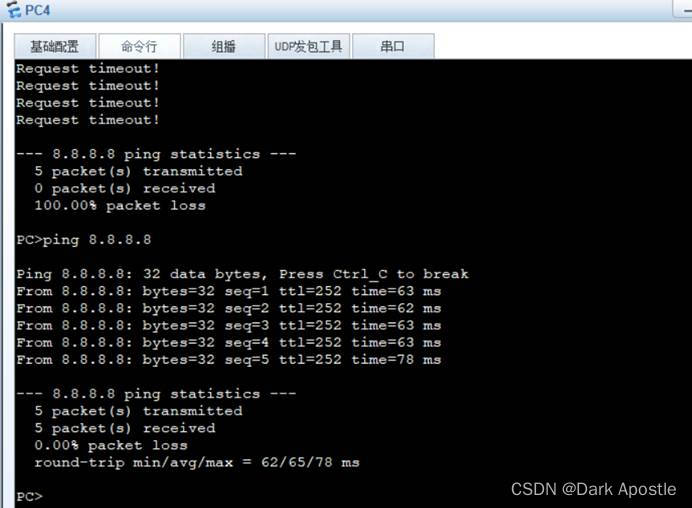
分部访问总部PC4
分部Client1终端访问总部PC4正常
11. 公网DNS域名配置
配置DNS域名映射,分部外网主机可以通过域名访问总部Web服务器