Kubernetes-11 K8s的Ingress
Kubernetes的Ingress
- 前言
- Ingress和Pod的关系
- Ingress工作流程
- 部署使用Ingress
-
- 首先创建一个Nginx的Deployment和SVC和Tomcat的Deployent和SVC
- 部署Ingress-Nginx
- 在hosts文件加入解析的域名
- Ingress HTTPS代理访问
-
- 创建证书,以及cert存储方式
- Nginx进行BasicAuth认证
-
- 配置yaml文件
- Nginx重写
前言
如果我们想让外部可以访问Pod,需要通过SVC的NodePort模式暴露IP+端口号来实现。
- 在每个节点上都会启动端口
- 在访问的时候通过任何节点,通过IP+端口号就能实现
但NodePort还存在这一些缺陷
- 端口不能重复,所以每个端口只能用一次,一个端口对应一个应用
- 实际访问都是通过域名,根据不同域名跳转到不同端口服务中
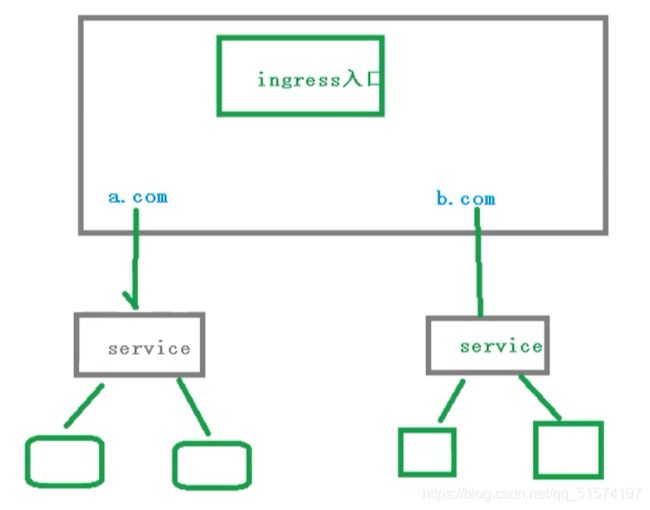
Ingress和Pod的关系
Pod和Ingress是通过Service进行关联的,而Ingress作为统一入口,由Service管理一组Pod。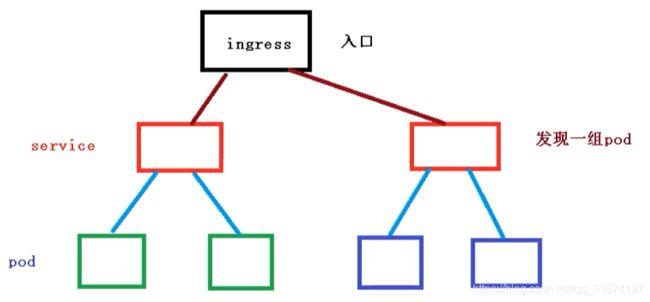
- 首先SVC通过label标签关联一组Pod
- 然后Ingress作为入口,首先需要关联到SVC,然后发现一组Pod
- 发现Pod以后,就可以做负载均衡
Ingress工作流程
在实际访问中,我们需要维护很多域名,a.com,b.com。然后不同的域名对应不同的SVC,然后SVC管理不同的Pod
注意:
Ingress不是内置组件,需要我们单独安装Ingress插件
部署使用Ingress
这里我们使用Ingress-Nignx
- 安装Ingress Controller
- 创建Ingress规则(通过标签发现)
首先创建一个Nginx的Deployment和SVC和Tomcat的Deployent和SVC
## nginx-deployment的yaml
cat dep-nginx.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
spec:
selector:
matchLabels:
run: nginx
replicas: 2
template:
metadata:
labels:
run: nginx
spec:
containers:
- name: my-nginx
image: nginx
ports:
- containerPort: 80
## tomcat的deployment的yaml
cat dep-tomcat.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: tomcat
spec:
selector:
matchLabels:
run: tomcat
replicas: 2
template:
metadata:
labels:
run: tomcat
spec:
containers:
- name: tomcat
image: tomcat
ports:
- containerPort: 8080
## nginx的svc
cat svc-nginx.yaml
apiVersion: v1
kind: Service
metadata:
labels:
app: web
name: nginx
spec:
ports:
- port: 80
name: web-nginx
type: NodePort
selector:
run: nginx
## tomcat的svc
apiVersion: v1
kind: Service
metadata:
labels:
app: web
name: tomcat
spec:
ports:
- port: 80
name: web-tomcat
targetPort: 8080
type: NodePort
selector:
run: tomcat
引用yaml文件
kubectl apply -f dep-nginx.yaml dep-tomcat.yaml nginx-svc.yaml tomcat-svc.yaml
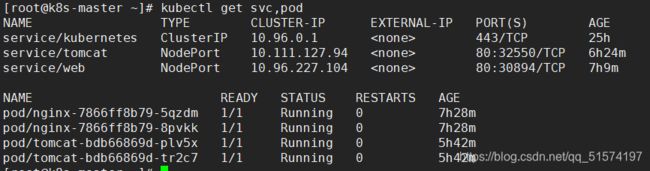
kubectl get svc,pod
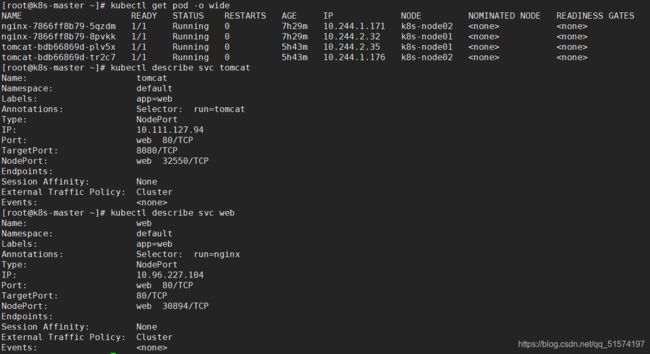
kubectl get pod -o wide
kubectl describe svc nginx
kubectl describe svc tomcat
部署Ingress-Nginx
##插件yaml
cat mandatory.yaml
apiVersion: v1
kind: Namespace
metadata:
name: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: nginx-configuration
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: tcp-services
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: udp-services
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole
metadata:
name: nginx-ingress-clusterrole
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- "extensions"
- "networking.k8s.io"
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- "extensions"
- "networking.k8s.io"
resources:
- ingresses/status
verbs:
- update
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: Role
metadata:
name: nginx-ingress-role
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
resourceNames:
# Defaults to "-"
# Here: "-"
# This has to be adapted if you change either parameter
# when launching the nginx-ingress-controller.
- "ingress-controller-leader-nginx"
verbs:
- get
- update
- apiGroups:
- ""
resources:
- configmaps
verbs:
- create
- apiGroups:
- ""
resources:
- endpoints
verbs:
- get
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: RoleBinding
metadata:
name: nginx-ingress-role-nisa-binding
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: nginx-ingress-role
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: nginx-ingress-clusterrole-nisa-binding
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: nginx-ingress-clusterrole
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-ingress-controller
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
prometheus.io/port: "10254"
prometheus.io/scrape: "true"
spec:
serviceAccountName: nginx-ingress-serviceaccount
containers:
- name: nginx-ingress-controller
image: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.25.0
args:
- /nginx-ingress-controller
- --configmap=$(POD_NAMESPACE)/nginx-configuration
- --tcp-services-configmap=$(POD_NAMESPACE)/tcp-services
- --udp-services-configmap=$(POD_NAMESPACE)/udp-services
- --publish-service=$(POD_NAMESPACE)/ingress-nginx
- --annotations-prefix=nginx.ingress.kubernetes.io
securityContext:
allowPrivilegeEscalation: true
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
# www-data -> 33
runAsUser: 33
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
ports:
- name: http
containerPort: 80
- name: https
containerPort: 443
livenessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
##SVC的yaml
cat service-nodeport.yaml
apiVersion: v1
kind: Service
metadata:
name: ingress-nginx
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
type: NodePort
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
- name: https
port: 443
targetPort: 443
protocol: TCP
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
部署Ingress,通过SVC名字关联
cat nginx-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-test
spec:
rules:
- host: www.a.com
http:
paths:
- path: /
backend:
serviceName: nginx
servicePort: 80
- host: www.b.com
http:
paths:
- path: /
backend:
serviceName: tomcat
servicePort: 80
应用yaml文件,确认
kubectl apply -f mandatory.yaml service-nodeport.yaml nginx-ingress.yaml
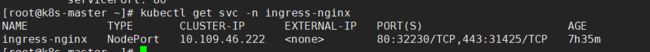
kubectl get svc,deployment -n ingress-nginx
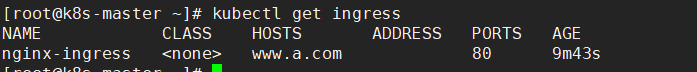
kubectl get ingress
在hosts文件加入解析的域名
www.a.com 192.168.2.73
www.b.com 192.168.2.73
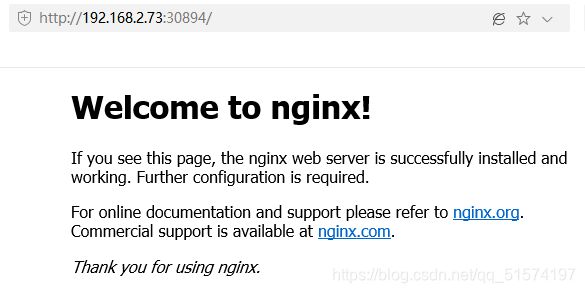
在浏览器中访问
www.a.com:30891

到这里就完成了Ingress-Nginx的作用,通过域名+端口访问的方式。
Ingress HTTPS代理访问
创建证书,以及cert存储方式
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginxsvc/O=nginxsvc"
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
##配置Deployment、Service、Ingress
vim ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-ingress
spec:
tls:
- hosts:
- www.a.com
secretName: tls-secret
- hosts:
- www.b.com
secretName: tls-secret
rules:
- host: www.a.com
http:
paths:
- path: /
backend:
serviceName: web
servicePort: 80
- host: www.b.com
http:
paths:
- path: /
backend:
serviceName: tomcat
servicePort: 80
应用yaml文件,访问443端口
kubectl apply -f ingress.yaml
kubectl get svc -n ingress-nginx
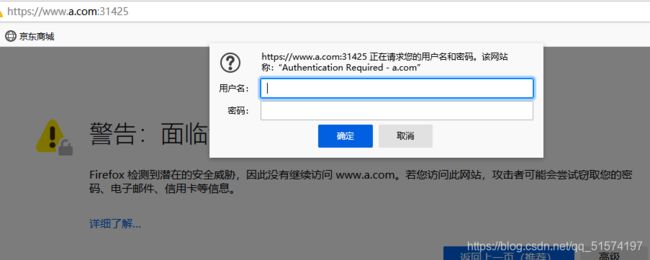
Nginx进行BasicAuth认证
##安装httpd软件包,创建认证文件,Secret
yum -y install httpd
htpasswd -c auth a.com
kubectl create secret generic basic-auth --from-file=auth
配置yaml文件
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-ingress
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - a.com'
spec:
tls:
- hosts:
- www.a.com
secretName: tls-secret
- hosts:
- www.b.com
secretName: tls-secret
rules:
- host: www.a.com
http:
paths:
- path: /
backend:
serviceName: web
servicePort: 80
- host: www.b.com
http:
paths:
- path: /
backend:
serviceName: tomcat
servicePort: 80
应用ingress.yaml文件,测试访问
kubectl apply -f ingress.yaml
Nginx重写
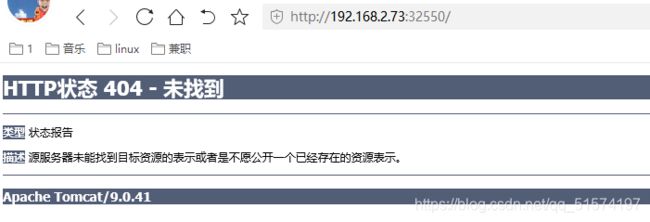
直接上yaml,我这里通过域名访问nginx的443端口,重写到后端tomcat的SVC的外部80端口,中间还实现了会话层卸载。
cat ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: nginx-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: http://192.168.2.73:32550
spec:
tls:
- hosts:
- www.a.com
secretName: tls-secret
rules:
- host: www.a.com
http:
paths:
- path: /
backend:
serviceName: web
servicePort: 80
kubectl apply -f ingress.yaml
下面还有一些功能,感兴趣的同学可以试一下
| 名称 | 描述 | 值 |
|---|---|---|
| nginx.ingress.kubernetes.io/rewrite-target | 必须重定向流量的目标URI | 串 |
| nginx.ingress.kubernetes.io/ssl-redirect | 指示位置部分是否仅可访问SSL(当Ingress包含证书时默认为True) | 布尔 |
| nginx.ingress.kubernetes.io/force-ssl-redirect | 即使Ingress未启用TLS,也强制重定向到HTTPS | 布尔 |
| nginx.ingress.kubernetes.io/app-root | 定义Controller必须重定向的应用程序根,如果它在’/'上下文中 | 串 |
| nginx.ingress.kubernetes.io/use-regex | 指示Ingress上定义的路径是否使用正则表达式 | 布尔 |