【网络实验】eNSP模拟华为防火墙配置双机热备VRRP
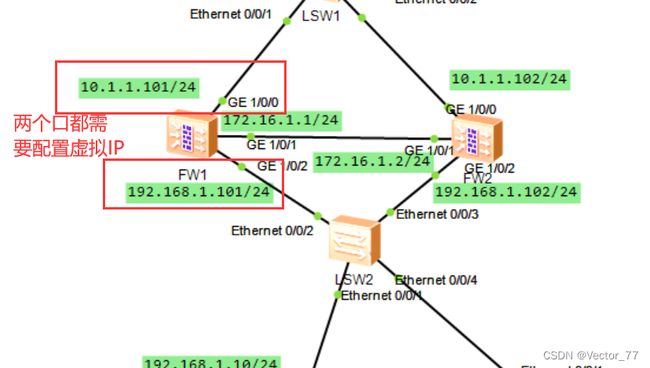
一、实验拓扑图
二、实验步骤
1、配置各个设备的ip
AR1:
[Huawei]int g0/0/0
[Huawei-GigabitEthernet0/0/0]ip add 10.1.1.1 24
[Huawei-GigabitEthernet0/0/0]q
[Huawei]int LoopBack 0
[Huawei-LoopBack0]ip add 1.1.1.1 24
FW1:
[USG6000V1]sysname FW1//改名字
[FW1]
[FW1]undo info-center enable //关闭更新提示
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]ip add 10.1.1.101 24
[FW1-GigabitEthernet1/0/0]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 172.16.1.1 24
[FW1-GigabitEthernet1/0/1]int g1/0/2
[FW1-GigabitEthernet1/0/2]ip add 192.168.1.101 24
FW2:
[USG6000V1]sysname FW2
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]ip add 10.1.1.102 24
[FW2-GigabitEthernet1/0/0]int g1/0/1
[FW2-GigabitEthernet1/0/1]ip add 172.16.1.2 24
[FW2-GigabitEthernet1/0/1]int g1/0/2
[FW2-GigabitEthernet1/0/2]ip add 192.168.1.102 24
PC1和PC2略
2、配置防火墙区域
FW1:
[FW1]firewall zone trust
[FW1-zone-trust]add int g1/0/2
[FW1-zone-trust]firewall zone untrust
[FW1-zone-untrust]add int g1/0/0
[FW1-zone-untrust]firewall zone dmz
[FW1-zone-dmz]add int g1/0/1
[FW1-zone-dmz]q
FW2:
[FW2]firewall zone trust
[FW2-zone-trust]add int g1/0/2
[FW2-zone-trust]fi
[FW2-zone-trust]firewall zone untrust
[FW2-zone-untrust]add int g1/0/0
[FW2-zone-untrust]firewall zone dmz
[FW2-zone-dmz]add int g1/0/1
3、配置安全策略
FW1:
[FW1]security-policy
[FW1-policy-security]rule name heart
[FW1-policy-security-rule-heart]source-zone local
[FW1-policy-security-rule-heart]destination-zone dmz
[FW1-policy-security-rule-heart]action permit
[FW1-policy-security-rule-heart]q
[FW1-policy-security]rule name tru_to_untru
[FW1-policy-security-rule-tru_to_untru]source-zone trust
[FW1-policy-security-rule-tru_to_untru]destination-zone untrust
[FW1-policy-security-rule-tru_to_untru]action permit
FW2:
[FW2]security-policy
[FW2-policy-security]rule name heart
[FW2-policy-security-rule-heart]source-zone local
[FW2-policy-security-rule-heart]destination-zone dmz
[FW2-policy-security-rule-heart]action permit
[FW2-policy-security-rule-heart]q
[FW2-policy-security]rule name tru_to_untru
[FW2-policy-security-rule-tru_to_untru]source-zone trust
[FW2-policy-security-rule-tru_to_untru]destination-zone untrust
[FW2-policy-security-rule-tru_to_untru]action permit
4、配置VRRP双机热备
试让PC1 ping AR1,ping不通->因为PC1的网关写的是待配置的虚拟网关ip
还有一个原因是没配置静态ip
FW1:
[FW1-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 10.1.1.100 active//配置上行链路接口的虚拟ip
[FW1-GigabitEthernet1/0/0]q
[FW1]int g1/0/2
[FW1-GigabitEthernet1/0/2]vrrp vrid 2 virtual-ip 192.168.1.100 active//配置下行链路的接口虚拟ip
[FW1-GigabitEthernet1/0/2]q
[FW1]hrp int g1/0/1 remote 172.16.1.2//配置心跳线,ip为对端ip
[FW1]hrp enable//开启双机热备功能
HRP_S[FW1]hrp auto-sync//设置双机热备为自动备份
FW2:
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 10.1.1.100 standby
[FW2-GigabitEthernet1/0/0]int g1/0/2
[FW2-GigabitEthernet1/0/2]vrrp vrid 2 virtual-ip 192.168.1.100 standby
[FW2-GigabitEthernet1/0/2]q
[FW2]hrp int g1/0/1 remote 172.16.1.1
[FW2]hrp enable
Info: NAT IP detect function is disabled.
HRP_S[FW2]hrp auto-sync
5、配置AR1的静态路由
[Huawei]ip route-static 192.168.1.0 24 10.1.1.100
三、验证
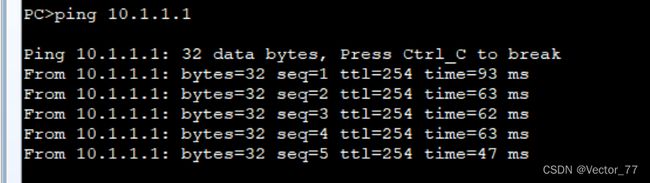
- PC1 ping AR1
抓包验证从FW1通过
2、shutdown FW1的某个接口
3、ping->自动切换到FW2
抓包验证
四、实验总结
-
心跳线双方的接口编号一定要一样;
- 华为防火墙不止三个区域,还可以自定义区域,只是这里刚好三个区域,可以就用dmz区域;但是设定其他自定义区域也没事,反正默认都不能互通;
- 防火墙的vrrp和路由器的vrrp有区别:
路由器的vrrp是在路由器内部设,如果只是双机热备,就只用设置一组vrid
防火墙的vrrp即使是双机热备也要设置两组,且是一个防火墙的上行链路接口和下行链路接口各为一组,且两个口都要配置虚拟ip
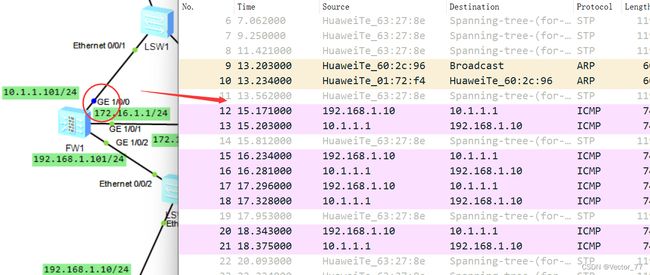
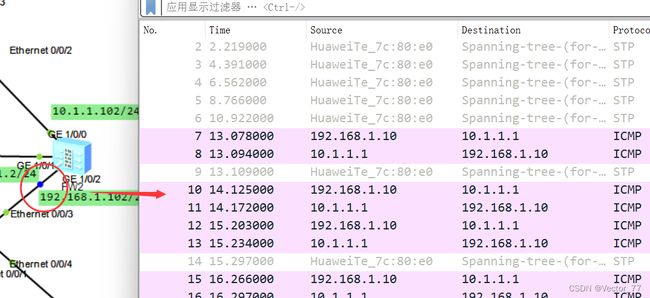
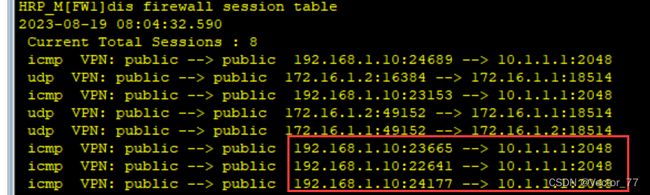
4、所有都配置完毕,发现一直ping不通,通过查询会话表才发现未配置AR1的静态路由,AR1只知道自己的网段!!没有路由条目
结合两张图可看出是流量回不来,进而判断是没有回程路由
由于是虚拟的,所以静态路由的下一跳地址是虚拟接口ip:(这一点比路由器的vrrp相对方便,路由器的VRRP需要写两条静态路由还要设置链路检测技术和静态路由优先级)
[Huawei]ip route-static 192.168.1.0 24 10.1.1.100
5、但是未实现主设备故障修好后自动切回主设备,需次设备也坏了才能切回主设备;
6、这个实验加深了网络故障排查的思路,例如ping不通是什么原因,同网段不同网段的思路去分析,不可达多半是网关找不到路由的问题。