【kali】34 WEB渗透——扫描工具w3af_console
这里写自定义目录标题
- 一、简介
-
- 1.plugin
- 2. kali 安装w3af[问题解决]
- 二、 操作
-
- 1. 启动帮助
- 2.plugins模块
-
- 开启三个插件模块
- 扫描所有插件模块
- 3. profiles 模块
- 4.http-settings 模块
- 5.misc-settings (杂项设置)模块
- 6.target 模块
- 7.启动
- 8.脚本
w3af_console
一、简介
- web扫描框架(开源、不断添加
- 集成exploit模块
1.plugin
audit(审计):该类插件会向Crawl插件爬取出的注入点发送特制的POC数据以确认漏洞是否存在。
infrastructure(基础):这类插件用来标识有关目标系统的信息,如安装的WAF,操作系统和HTTP守护进程等。
grep(检索):这类插件会分析其他插件发送的HTTP请求和相应并识别漏洞。
evasion(绕过):通过修改由其他插件生成的HTTP请求来绕过简单的入侵检测规则。
mangle:允许修改基于正则表达式的请求和响应
auth:
Mangle:允许修改基于正则表达式的请求和响应。
bruteforce:在爬取阶段进行暴力登陆
output(输出):这类插件会将插件的数据保存到文本,xml或者是html文件中。调试的信息也会发送到输出Output插件并可保存和分析。如果启用了text_file和xml_file这两个Output插件,则这两个都会记录有Audit插件发现的任何漏洞。
crawl(爬取):通过爬取网站站点来获得新的URL地址。如果用户启用了Crawl类型的多个插件,此时将产生一个循环: A插件在第一次运行时发现了一个新的url,w3af会将其发送到插件B。如果插件B发现一个新的url则会发送到插件A。这个过程持续进行直到所有插件都已运行且无法找到更多的新信息。
Attack(攻击):如果Audit插件发现了漏洞,Attack将会进行攻击和利用,通常会在远程服务器上返回一个shell或者比如SQL注入则会获取数据库的数据。
2. kali 安装w3af[问题解决]
安装w3af时遇到./w3af_console We recommend you install pip before continuing.http://www.pip-installer.org/en/latest/installing.html
# 切换到主目录,官方指定在主目录下安装
cd ~
# 换成了aliyun的源
vim /etc/apt/sources.list
deb http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
deb-src http://mirrors.aliyun.com/kali kali-rolling main non-free
contrib
deb http://ftp.de.debian.org/debian buster main
apt-get update
# 安装NPM包管理工具
apt install npm libyaml-dev libsqlite3-dev
# 安装lxml,需要先安装此软件,官方文档未提示安装,但不安装便会报错
apt-get build-dep python-lxml
# 补全python库环境
apt install python-dev build-essential libssl-dev libffi-dev libxml2-dev libxslt1-dev zlib1g-dev
# 下载安装包
git clone https://github.com/andresriancho/w3af.git
cd w3af
apt-get install -y python-pip
# 报错,卸载pip重新安装
# 发现No module named ‘ConfigParser‘
# 使用python2安装pip
curl https://bootstrap.pypa.io/pip/2.7/get-pip.py -o get-pip2.py
python get-pip2.py
# 一直缺这个
apt install python-pip-whl=18.1-5
./w3af_console
# 如果报错,缺什么补什么!!
# 终于ok了
./w3af_dependency_install.sh
二、 操作
1. 启动帮助
help
2.plugins模块
开启三个插件模块
状态模块变为enabled
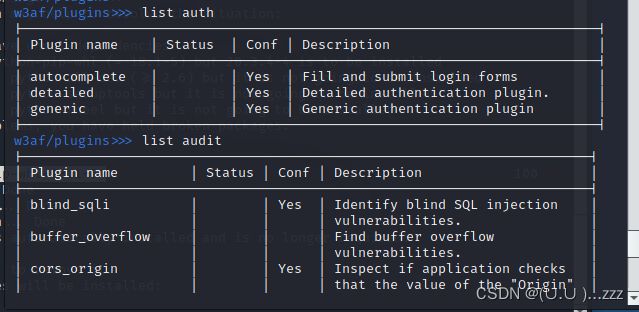
w3af/plugins>>> audit xss sqli lfi
w3af/plugins>>> list audit
|------------------------------------------------------------------------|
| Plugin name | Status | Conf | Description |
|------------------------------------------------------------------------|
| blind_sqli | | Yes | Identify blind SQL injection |
| | | | vulnerabilities. |
| buffer_overflow | | | Find buffer overflow |
| | | | vulnerabilities. |
| cors_origin | | Yes | Inspect if application checks |
| | | | that the value of the "Origin" |
| | | | HTTP header isconsistent with |
| | | | the value of the remote IP |
| | | | address/Host of the sender |
| | | | ofthe incoming HTTP request. |
| csrf | | | Identify Cross-Site Request |
| | | | Forgery vulnerabilities. |
| dav | | | Verify if the WebDAV module is |
| | | | properly configured. |
| deserialization | | | Identify deserialization |
| | | | vulnerabilities. |
| eval | | Yes | Find insecure eval() usage. |
| file_upload | | Yes | Uploads a file and then |
| | | | searches for the file inside |
| | | | all known directories. |
| format_string | | | Find format string |
| | | | vulnerabilities. |
| frontpage | | | Tries to upload a file using |
| | | | frontpage extensions |
| | | | (author.dll). |
| generic | | Yes | Find all kind of bugs without |
| | | | using a fixed error database. |
| global_redirect | | | Find scripts that redirect the |
| | | | browser to any site. |
| htaccess_methods | | | Find misconfigurations in |
| | | | Apache's "" |
| | | | configuration. |
| ldapi | | | Find LDAP injection bugs. |
| lfi | Enabled | | Find local file inclusion |
| | | | vulnerabilities. |
| memcachei | | | No description available for |
| | | | this plugin. |
| mx_injection | | | Find MX injection |
| | | | vulnerabilities. |
| os_commanding | | | Find OS Commanding |
| | | | vulnerabilities. |
| phishing_vector | | | Find phishing vectors. |
| preg_replace | | | Find unsafe usage of PHPs |
| | | | preg_replace. |
| redos | | | Find ReDoS vulnerabilities. |
| response_splitting | | | Find response splitting |
| | | | vulnerabilities. |
| rfd | | | Identify reflected file |
| | | | download vulnerabilities. |
| rfi | | Yes | Find remote file inclusion |
| | | | vulnerabilities. |
| rosetta_flash | | | Find Rosetta Flash |
| | | | vulnerabilities in JSONP |
| | | | endpoints |
| shell_shock | | | Find shell shock |
| | | | vulnerabilities. |
| sqli | Enabled | | Find SQL injection bugs. |
| ssi | | | Find server side inclusion |
| | | | vulnerabilities. |
| ssl_certificate | | Yes | Check the SSL certificate |
| | | | validity (if https is being |
| | | | used). |
| un_ssl | | | Find out if secure content can |
| | | | also be fetched using http. |
| websocket_hijacking | | | Detect Cross-Site WebSocket |
| | | | hijacking vulnerabilities. |
| xpath | | | Find XPATH injection |
| | | | vulnerabilities. |
| xss | Enabled | Yes | Identify cross site scripting |
| | | | vulnerabilities. |
| xst | | | Find Cross Site Tracing |
| | | | vulnerabilities. |
| xxe | | | Find XXE vulnerabilities. |
|------------------------------------------------------------------------|
w3af/plugins>>>
扫描所有插件模块
w3af/plugins>>> audit all
w3af/plugins>>> list audit
|------------------------------------------------------------------------|
| Plugin name | Status | Conf | Description |
|------------------------------------------------------------------------|
| blind_sqli | Enabled | Yes | Identify blind SQL injection |
| | | | vulnerabilities. |
| buffer_overflow | Enabled | | Find buffer overflow |
| | | | vulnerabilities. |
| cors_origin | Enabled | Yes | Inspect if application checks |
| | | | that the value of the "Origin" |
| | | | HTTP header isconsistent with |
| | | | the value of the remote IP |
| | | | address/Host of the sender |
| | | | ofthe incoming HTTP request. |
| csrf | Enabled | | Identify Cross-Site Request |
| | | | Forgery vulnerabilities. |
| dav | Enabled | | Verify if the WebDAV module is |
| | | | properly configured. |
| deserialization | Enabled | | Identify deserialization |
| | | | vulnerabilities. |
| eval | Enabled | Yes | Find insecure eval() usage. |
| file_upload | Enabled | Yes | Uploads a file and then |
| | | | searches for the file inside |
| | | | all known directories. |
| format_string | Enabled | | Find format string |
| | | | vulnerabilities. |
| frontpage | Enabled | | Tries to upload a file using |
| | | | frontpage extensions |
| | | | (author.dll). |
| generic | Enabled | Yes | Find all kind of bugs without |
| | | | using a fixed error database. |
| global_redirect | Enabled | | Find scripts that redirect the |
| | | | browser to any site. |
| htaccess_methods | Enabled | | Find misconfigurations in |
| | | | Apache's "" |
| | | | configuration. |
| ldapi | Enabled | | Find LDAP injection bugs. |
| lfi | Enabled | | Find local file inclusion |
| | | | vulnerabilities. |
| memcachei | Enabled | | No description available for |
| | | | this plugin. |
| mx_injection | Enabled | | Find MX injection |
| | | | vulnerabilities. |
| os_commanding | Enabled | | Find OS Commanding |
| | | | vulnerabilities. |
| phishing_vector | Enabled | | Find phishing vectors. |
| preg_replace | Enabled | | Find unsafe usage of PHPs |
| | | | preg_replace. |
| redos | Enabled | | Find ReDoS vulnerabilities. |
| response_splitting | Enabled | | Find response splitting |
| | | | vulnerabilities. |
| rfd | Enabled | | Identify reflected file |
| | | | download vulnerabilities. |
| rfi | Enabled | Yes | Find remote file inclusion |
| | | | vulnerabilities. |
| rosetta_flash | Enabled | | Find Rosetta Flash |
| | | | vulnerabilities in JSONP |
| | | | endpoints |
| shell_shock | Enabled | | Find shell shock |
| | | | vulnerabilities. |
| sqli | Enabled | | Find SQL injection bugs. |
| ssi | Enabled | | Find server side inclusion |
| | | | vulnerabilities. |
| ssl_certificate | Enabled | Yes | Check the SSL certificate |
| | | | validity (if https is being |
| | | | used). |
| un_ssl | Enabled | | Find out if secure content can |
| | | | also be fetched using http. |
| websocket_hijacking | Enabled | | Detect Cross-Site WebSocket |
| | | | hijacking vulnerabilities. |
| xpath | Enabled | | Find XPATH injection |
| | | | vulnerabilities. |
| xss | Enabled | Yes | Identify cross site scripting |
| | | | vulnerabilities. |
| xst | Enabled | | Find Cross Site Tracing |
| | | | vulnerabilities. |
| xxe | Enabled | | Find XXE vulnerabilities. |
|------------------------------------------------------------------------|
w3af/plugins>>>
3. profiles 模块
w3af>>> profiles (预定义扫描文件)
w3af/profiles>>> list (显示当前可用扫描配置文件)
|----------------------------------------------------------------------------------------------------------------------------------|
| Profile | Description |
|----------------------------------------------------------------------------------------------------------------------------------|
| bruteforce | Bruteforce form or basic authentication access controls using default credentials. To run this profile, |
| | set the target URL to the resource where the access control is, and then click on Start. |
| audit_high_risk | Perform a scan to only identify the vulnerabilities with higher risk, like SQL Injection, OS Commanding, |
| | Insecure File Uploads, etc. |
| full_audit | This profile performs a full audit of the target website, using only the web_spider plugin for crawling. |
| OWASP_TOP10 | The Open Web Application Security Project (OWASP) is a worldwide free and open community focused on |
| | improving the security of application software. OWASP searched for and published the ten most common |
| | security flaws. This profile search for this top 10 security flaws. For more information about the |
| | security flaws: http://www.owasp.org/index.php/OWASP_Top_Ten_Project . |
| fast_scan | Perform a fast scan of the target site, using only a few discovery plugins and the fastest audit |
| | plugins. |
| empty_profile | This is an empty profile that you can use to start a new configuration from. |
| web_infrastructure | Use all the available techniques in w3af to fingerprint the remote Web infrastructure. |
| full_audit_spider_man | Perform a manual discovery using the spider_man plugin, and afterwards scan the site for any known |
| | vulnerabilities. |
| sitemap | Use different online techniques to create a fast sitemap of the target web application. This plugin will |
| | only work if you've got Internet access and the target web application is being spidered by Yahoo! |
|----------------------------------------------------------------------------------------------------------------------------------|
w3af/profiles>>> help
|-------------------------------------------------------------------------|
w3af/profiles>>> save_as test01
Profile saved.
4.http-settings 模块
扫描http的配置选项
w3af>>> http-settings
w3af/config:http-settings>>> help
|-------------------------------------------------------------------------|
| view | List the available options and their values. |
| set | Set a parameter value. |
| save | Save the configured settings. |
|-------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
|-------------------------------------------------------------------------|
w3af/config:http-settings>>> view
|------------------------------------------------------------------------|
| Setting | Value | Modified | Description |
|------------------------------------------------------------------------|
| url_parameter | | | URL parameter |
| | | | (http://host.tld/path;<parameter>) |
| timeout | 0 | | HTTP connection timeout |
| headers_file | | | HTTP headers filename which |
| | | | contains additional headers to be |
| | | | added in each request |
|------------------------------------------------------------------------|
| cookie_jar_file | | | Cookie Jar file holding HTTP |
| | | | cookies |
| ignore_session_cookies | False | | Ignore session cookies |
|------------------------------------------------------------------------|
| ntlm_auth_url | | | NTLM authentication domain (target |
| | | | domain name) |
| ntlm_auth_user | | | NTLM authentication username |
| ntlm_auth_passwd | | | NTLM authentication password |
| ntlm_auth_domain | | | NTLM authentication domain |
| | | | (windows domain name) |
|------------------------------------------------------------------------|
| rand_user_agent | False | | Use random User-Agent header |
| max_file_size | 400000 | | Maximum file size |
| max_http_retries | 2 | | Maximum number of HTTP request |
| | | | retries |
| user_agent | w3af.org | | User Agent header |
| max_requests_per_second | 0 | | Maximum HTTP requests per second |
|------------------------------------------------------------------------|
| string_match_404 | | | Tag HTTP response as 404 if the |
| | | | string is found in it's body |
| always_404 | | | Comma separated list of URLs which |
| | | | will always be detected as 404 |
| | | | pages |
| never_404 | | | Comma separated list of URLs which |
| | | | will never be detected as 404 |
| | | | pages |
|------------------------------------------------------------------------|
| proxy_port | 8080 | | Proxy TCP port |
| proxy_address | | | Proxy IP address |
|------------------------------------------------------------------------|
| basic_auth_user | | | Basic authentication username |
| basic_auth_passwd | | | Basic authentication password |
| basic_auth_domain | | | Basic authentication domain |
|------------------------------------------------------------------------|
w3af/config:http-settings>>>
5.misc-settings (杂项设置)模块
w3af>>> misc-settings (杂项设置)
w3af/config:misc-settings>>> view
|---------------------------------------------------------------------------------------------------------------------------------|
| Setting | Value | Modified | Description |
|---------------------------------------------------------------------------------------------------------------------------------|
| msf_location | /opt/metasploit3/bin/ | | Full path of Metasploit framework binary directory |
| | | | (/opt/metasploit3/bin/ in most linux installs) |
|---------------------------------------------------------------------------------------------------------------------------------|
| interface | ppp0 | | Local interface name to use when sniffing, doing reverse |
| | | | connections, etc. |
| local_ip_address | 10.10.10.128 | | Local IP address to use when doing reverse connections |
|---------------------------------------------------------------------------------------------------------------------------------|
| max_discovery_time | 120 | | Maximum crawl time (minutes) |
| stop_on_first_exception | False | | Stop scan after first unhandled exception |
|---------------------------------------------------------------------------------------------------------------------------------|
| form_id_action | exclude | | Define the form_id_list filter behaviour |
| non_targets | | | A comma separated list of URLs that w3af should ignore |
| form_id_list | [] | | Filter forms to scan using form IDs |
|---------------------------------------------------------------------------------------------------------------------------------|
| fuzz_url_filenames | False | | Indicates if w3af plugins will send fuzzed file names in order to |
| | | | find vulnerabilities |
| fuzz_url_parts | False | | Indicates if w3af plugins will send fuzzed URL parts in order to |
| | | | find vulnerabilities |
| fuzzable_headers | | | A list with all fuzzable header names |
| fuzzed_files_extension | gif | | Indicates the extension to use when fuzzing file content |
| form_fuzzing_mode | tmb | | Indicates what HTML form combo values w3af plugins will use: all, |
| | | | tb, tmb, t, b |
| fuzz_form_files | True | | Indicates if w3af plugins will send payloads in the content of |
| | | | multipart/post form files. |
| fuzz_cookies | False | | Indicates if w3af plugins will use cookies as a fuzzable parameter |
|---------------------------------------------------------------------------------------------------------------------------------|
w3af/config:misc-settings>>> help
|----------------------------------------------------------------------------------------------------------------------------------|
| view | List the available options and their values. |
| set | Set a parameter value. |
| save | Save the configured settings. |
|----------------------------------------------------------------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
|----------------------------------------------------------------------------------------------------------------------------------|
w3af/config:misc-settings>>> back
The configuration has been saved.
6.target 模块
w3af>>> target
w3af/config:target>>> set target http://10.10.10.129
w3af/config:target>>> view
|-------------------------------------------------------------------------------------------------------------------|
| Setting | Value | Modified | Description |
|-------------------------------------------------------------------------------------------------------------------|
| target_framework | unknown | | Target programming framework |
| | | | (unknown/php/asp/asp.net/java/jsp/cfm/ruby/perl) |
| target | http://10.10.10.129 | Yes | A comma separated list of URLs |
| target_os | unknown | | Target operating system (unknown/unix/windows) |
|-------------------------------------------------------------------------------------------------------------------|
w3af/config:target>>>
7.启动
start
8.脚本
┌──(rootkali)-[/usr/local/src]
└─# cd
┌──(rootkali)-[~]
└─# cd w3af
┌──(rootkali)-[~/w3af]
└─# ls
circle.yml doc get-pip2.py profiles README.md scripts w3af w3af_console
configparser.py extras get-pip.py __pycache__ result tools w3af_api w3af_gui
┌──(rootkali)-[~/w3af]
└─# cd scripts
┌──(rootkali)-[~/w3af/scripts]
└─# ls
allowed_methods.w3af login_brute_form_GET.w3af
all.w3af login_brute_password_only.w3af
auth_detailed.w3af mangle_request.w3af
bing_spider.w3af mangle_response.w3af
blind_sqli_detection.w3af os_commanding-lnx-vdaemon.w3af
cookie_fuzzing.w3af os_commanding-lnx-w3afAgent.w3af
cross_domain.w3af os_commanding_shell.w3af
csrf.w3af os_commanding.w3af
dav_shell.w3af php_sca-payload.w3af
detect_transparent_proxy.w3af profile-fast_scan.w3af
digit_sum.w3af remote_file_include_local_ws.w3af
dvwa.w3af remote_file_include_proxy.w3af
eval_shell.w3af remote_file_include_shell.w3af
eval.w3af remote_file_include_shell-xss.w3af
exploit_all.w3af remote_file_include_w3af_site.w3af
exploit_fast.w3af spider_man.w3af
filename_xss.w3af sqli.w3af
file_upload_shell.w3af sqlmap_exploit_int.w3af
frontpage_version.w3af targets_from_file.w3af
header_fuzzing.w3af web_spider-ignore_regex.w3af
html_output.w3af web_spider-only_forward.w3af
list_all_plugins.w3af web_spider.w3af
local_file_include-payload.w3af xss_simple.w3af
local_file_include.w3af xss_stored.w3af
┌──(rootkali)-[~/w3af/scripts]
└─# cat sqli.w3af
# This is a demo of the attack plugin sql_shell
plugins
output console,text_file
output config text_file
set output_file output-w3af.txt
set verbose True
back
output config console
set verbose False
back
audit sqli
crawl web_spider
crawl config web_spider
set only_forward True
back
grep path_disclosure
back
target
set target http://moth/w3af/audit/sql_injection/select/sql_injection_string.php?name=andres
back
start
bug-report
details 0
back
exit
┌──(rootkali)-[~/w3af/scripts]
└─#