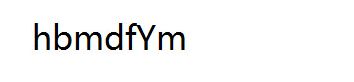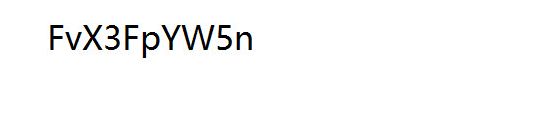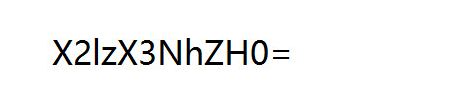buuctf misc page 2
目录
-
- 被劫持的神秘礼物
- 刷新过的图片
- snake
- [BJDCTF2020]认真你就输了
- [BJDCTF2020]藏藏藏
- 被偷走的文件
- [GXYCTF2019]佛系青年
- 菜刀666
- [BJDCTF2020]你猜我是个啥
- 秘密文件
- 梅花香之苦寒来
- [BJDCTF2020]just_a_rar
- [SWPU2019]神奇的二维码
- [BJDCTF2020]鸡你太美
- [BJDCTF2020]一叶障目
- 穿越时空的思念
- [BJDCTF2020]纳尼
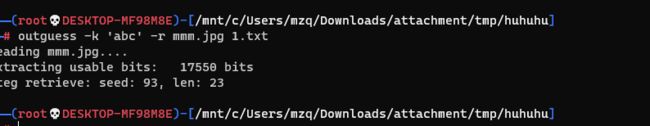
- [ACTF新生赛2020]outguess
- [SWPU2019]我有一只马里奥
- HBNIS2018]excel破解![在这里插入图片描述
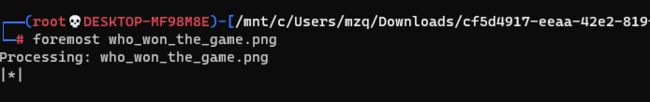
- 谁赢了比赛?
- [HBNIS2018]来题中等的吧
- [GXYCTF2019]gakki
- [WUSTCTF2020]find_me
- [ACTF新生赛2020]base64隐写
- [SWPU2019]伟大的侦探
- [GUET-CTF2019]KO
- 黑客帝国
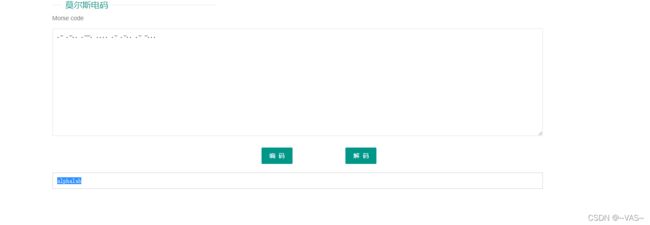
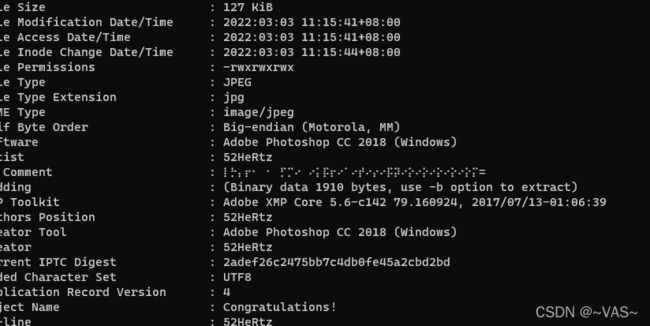
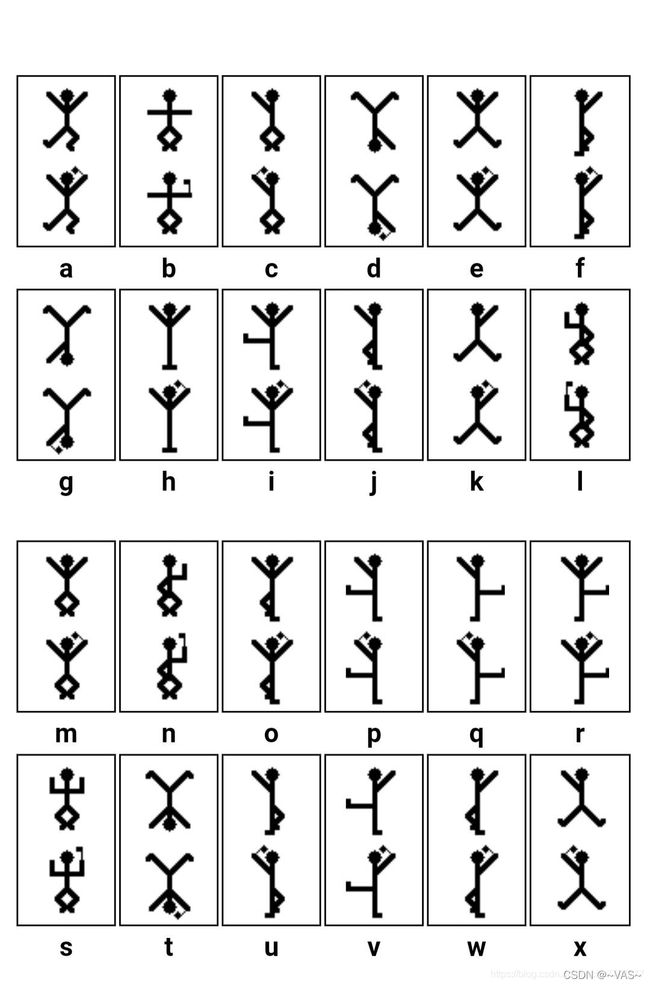
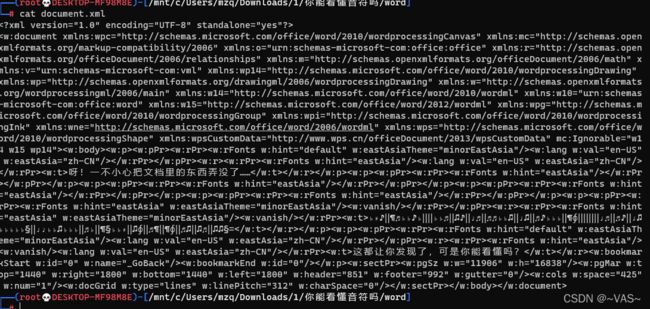
- [MRCTF2020]你能看懂音符吗
- [MRCTF2020]ezmisc
- sqltest
- [SWPU2019]你有没有好好看网课?
被劫持的神秘礼物
刷新过的图片
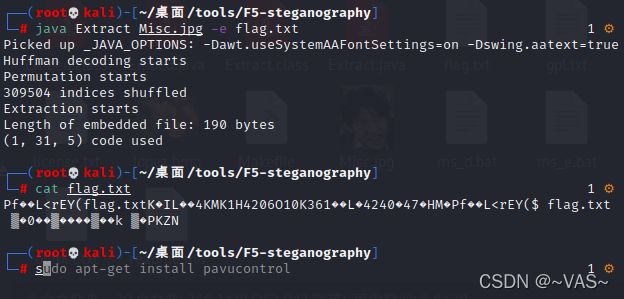
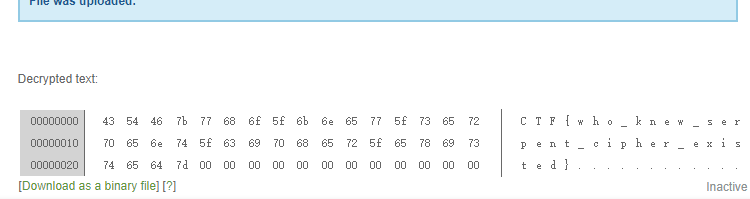
snake
serpent加密 http://serpent.online-domain-tools.com/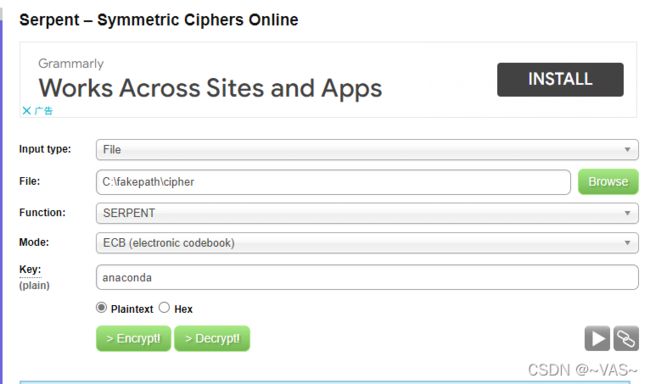
[BJDCTF2020]认真你就输了
[BJDCTF2020]藏藏藏
被偷走的文件
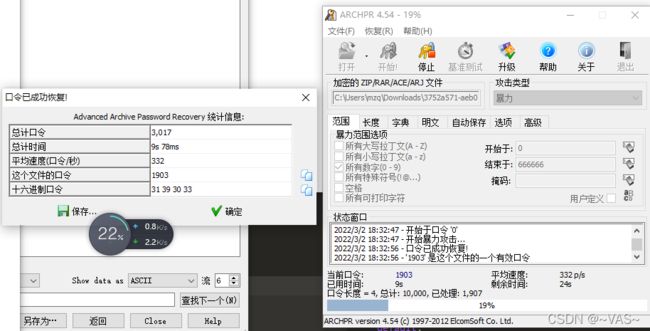
有个rar直接formost,压缩包有密码进行常规密码爆破1-8位
解压得flag

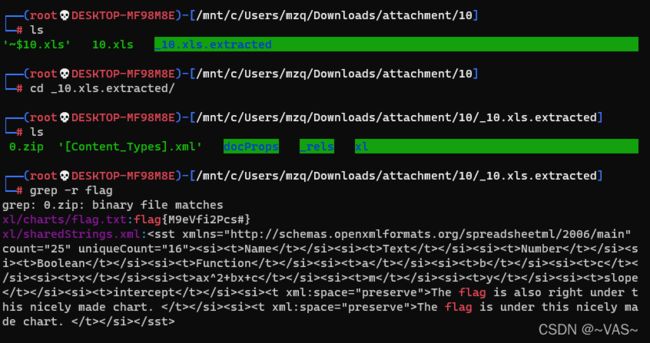
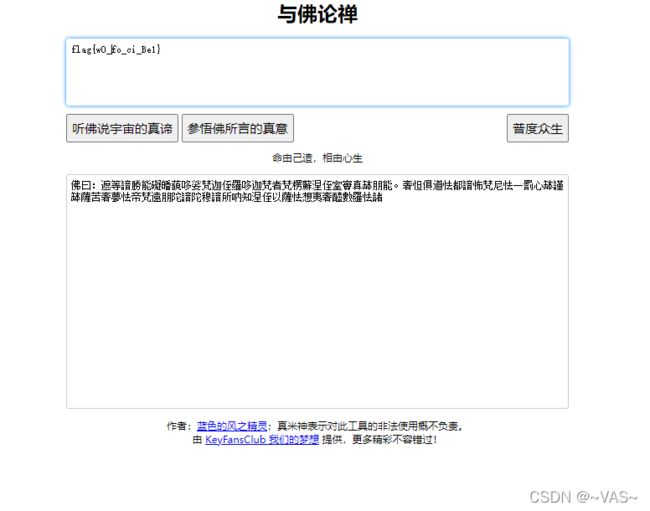
[GXYCTF2019]佛系青年
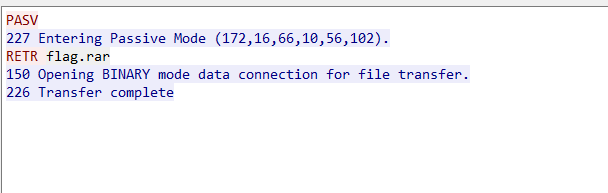
菜刀666
在tcp流7里找到一个图片,保存位jpg,打开发现是一个密码,猜测有压缩包
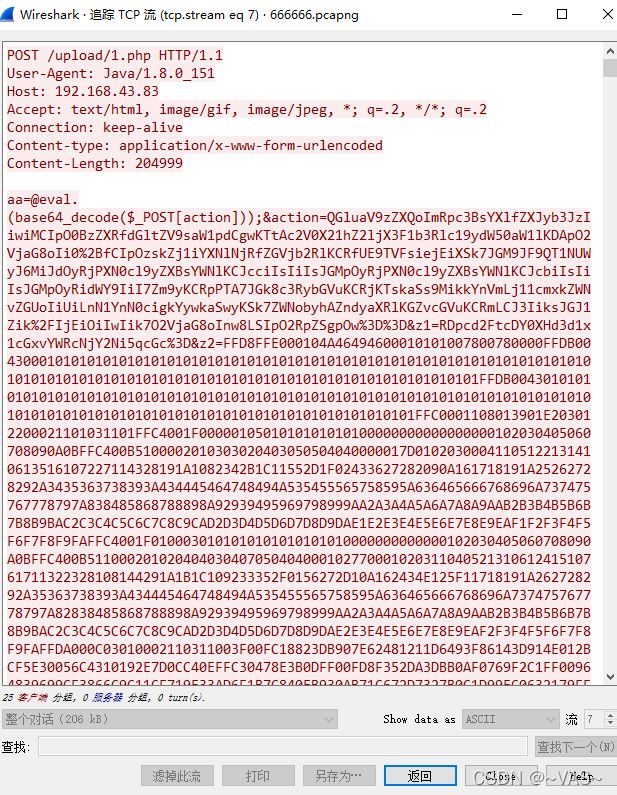

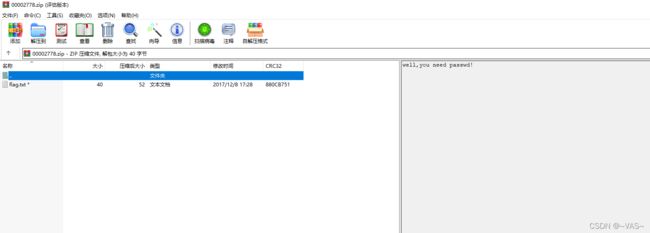
foremost分解pcap得到一个压缩包,输入密码拿到flag
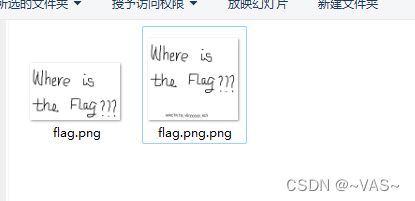
[BJDCTF2020]你猜我是个啥
010editor打开发现是png,修改文件后缀
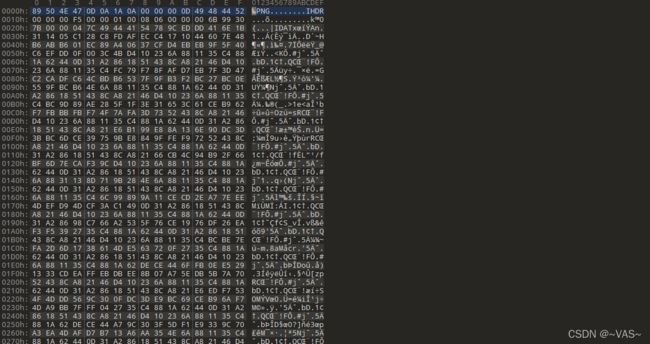
得到一个二维码,扫码发现并没有flag

搜索flag发现在文件末尾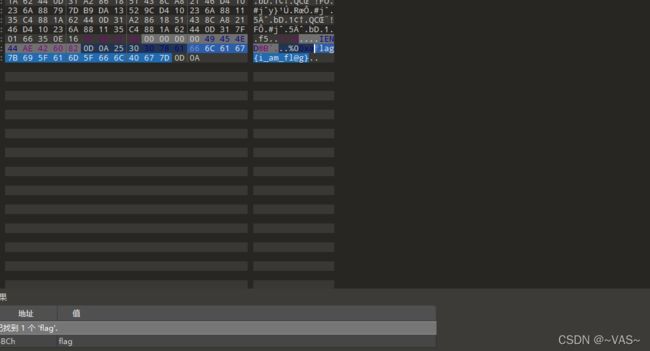
秘密文件
梅花香之苦寒来
a = """hexdata"""
import binascii
def hexStr_to_str(hex_str):
hex = hex_str.encode('utf-8')
str_bin = binascii.unhexlify(hex)
return str_bin.decode('utf-8')
if __name__ == "__main__":
hex_str = hexStr_to_str(a)
for i in hex_str.split():
x,y = eval((i))
with open('1.txt','a') as f:
f.write((str(x)+" "+str(y)+'\n'))
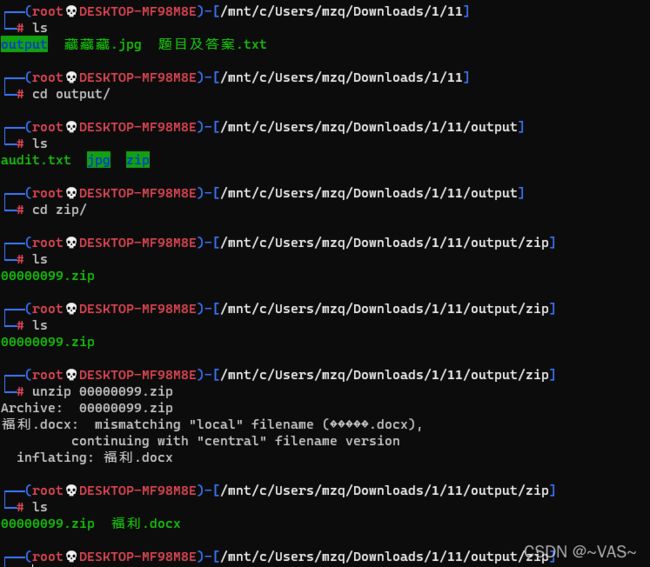
[BJDCTF2020]just_a_rar
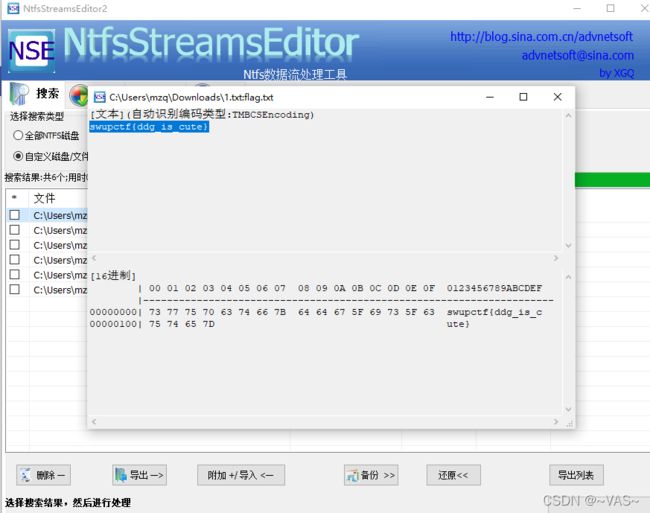
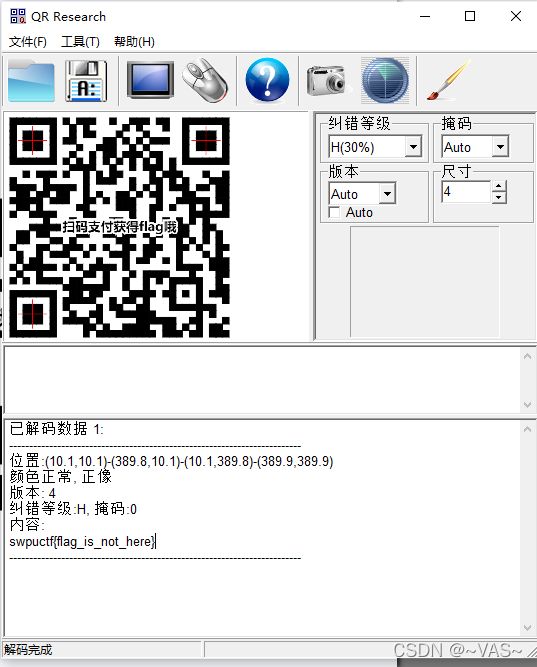
[SWPU2019]神奇的二维码
扫码给了个假的flag
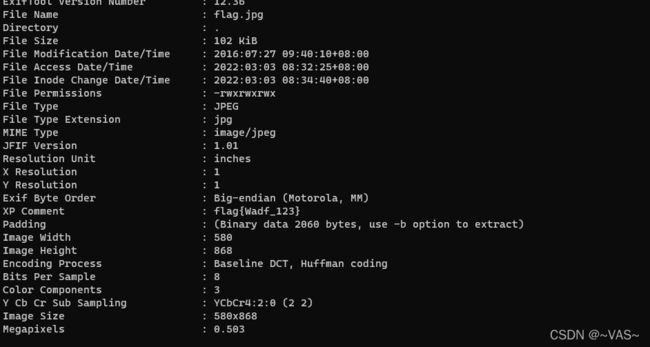
zsteg扫描到存在一个rar文件,进行提取文件
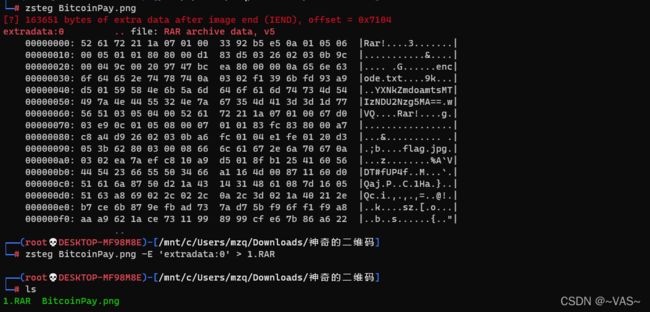
打开后发现没啥用,binwalk分解图片,有4个压缩包出来了,经过很多次尝试,前两两个应该是混淆用的。
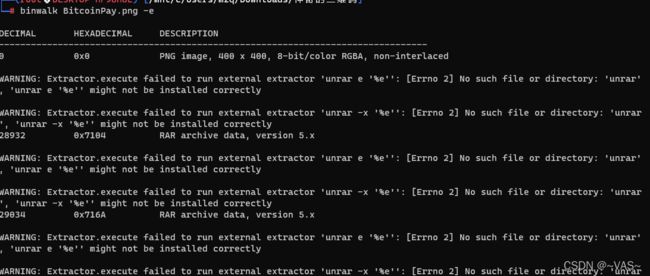
音频压缩包的密码是docx的base64解密后的
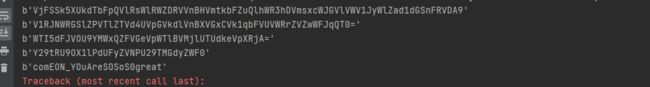
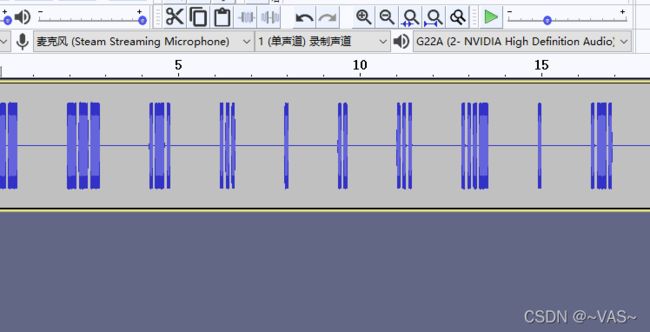
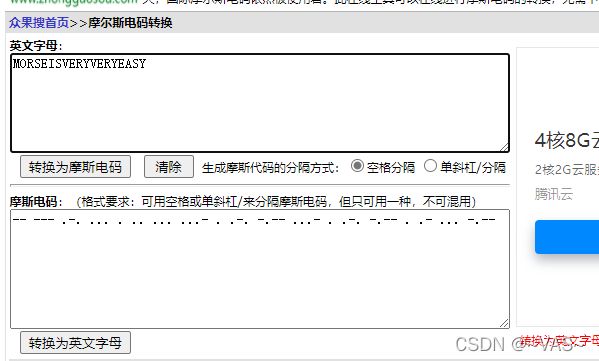
mp3文件用audi打开发现是摩斯密码
flag{小写}
[BJDCTF2020]鸡你太美
[BJDCTF2020]一叶障目
修复图片高度
import binascii
import struct
import sys
file = input("图片地址:")
fr = open(file,'rb').read()
data = bytearray(fr[0x0c:0x1d])
crc32key = eval('0x'+str(binascii.b2a_hex(fr[0x1d:0x21]))[2:-1])
#原来的代码: crc32key = eval(str(fr[29:33]).replace('\\x','').replace("b'",'0x').replace("'",''))
n = 4095
for w in range(n):
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
crc32result = binascii.crc32(data) & 0xffffffff
if crc32result == crc32key:
print(width,height)
newpic = bytearray(fr)
for x in range(4):
newpic[x+16] = width[x]
newpic[x+20] = height[x]
fw = open(file+'.png','wb')
fw.write(newpic)
fw.close
sys.exit()
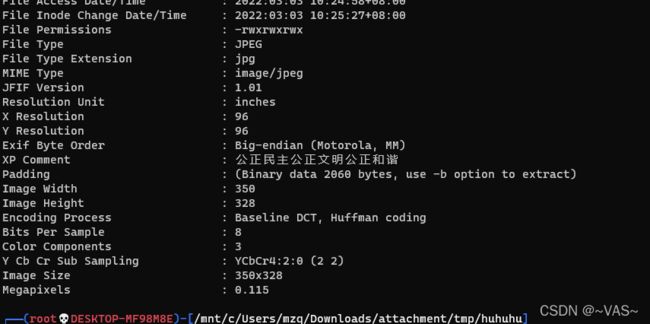
穿越时空的思念
[BJDCTF2020]纳尼
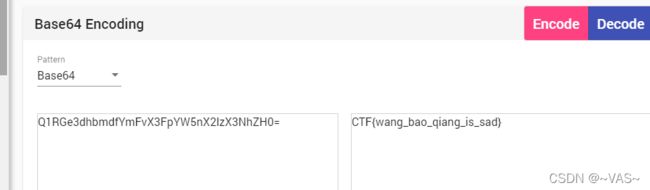
Q1RGe3dhbmdfYmFvX3FpYW5nX2lzX3NhZH0=
[ACTF新生赛2020]outguess
[SWPU2019]我有一只马里奥
[HBNIS2018]excel破解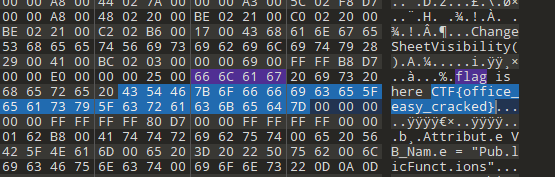
谁赢了比赛?
stegsolve打开frame
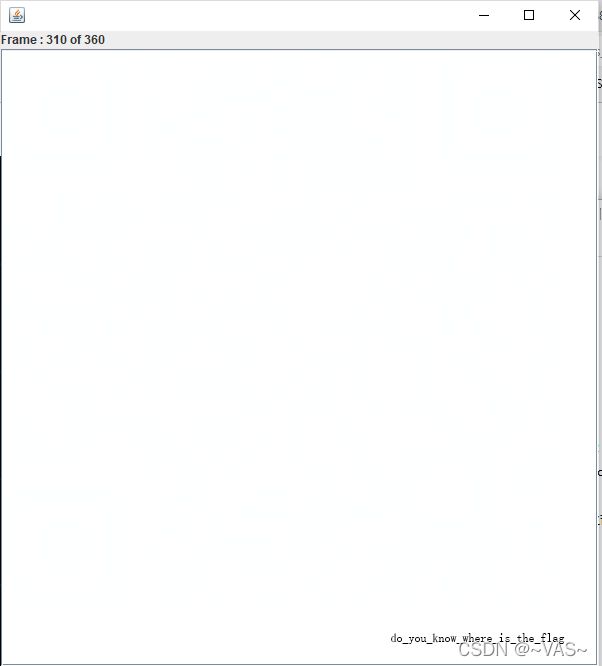
在310帧中发现字符,保存,重新观察通道


[HBNIS2018]来题中等的吧
[GXYCTF2019]gakki
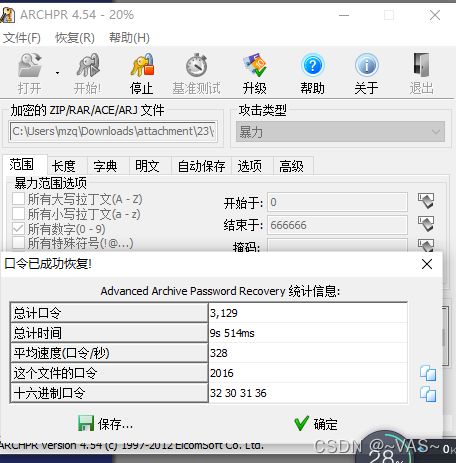
foremost分离rar压缩包发现有密码进行常规爆破

一堆无规律字符串,进行词频统计

# -*- coding:utf-8 -*-
#Author: mochu7
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()_+- =\\{\\}[]"
file_path = input('please input path:')
strings = open(file_path).read()
result = {}
for i in alphabet:
counts = strings.count(i)
i = '{0}'.format(i)
result[i] = counts
res = sorted(result.items(),key=lambda item:item[1],reverse=True)
for data in res:
print(data)
for i in res:
flag = str(i[0])
print(flag[0],end="")
[WUSTCTF2020]find_me
[ACTF新生赛2020]base64隐写
直接跑脚本就行了
import base64
b64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
path = input("Path : ")
address = (path[0:(len(path) - len(path.split('\\')[-1]))])
with open(path, 'rb') as f:
flag = ''
bin_str = ''
for line in f.readlines():
stegb64 = str(line, "utf-8").strip("\n")
rowb64 = str(base64.b64encode(base64.b64decode(stegb64)), "utf-8").strip("\n")
offset = abs(b64chars.index(stegb64.replace('=', '')[-1]) - b64chars.index(rowb64.replace('=', '')[-1]))
equalnum = stegb64.count('=') # no equalnum no offset
if equalnum:
bin_str += bin(offset)[2:].zfill(equalnum * 2)
# flag += chr(int(bin(offset)[2:].zfill(equalnum * 2), 2))
# print(flag) 这样写得不出正确结果
#print(([chr(int(bin_str[i:i + 8], 2)) for i in range(0, len(bin_str), 8)]))
flag = ([chr(int(bin_str[i:i + 8], 2)) for i in range(0, len(bin_str), 8)])
with open(address+'steg_'+path.split('\\')[-1],'w') as file:
for i in flag:
file.write(i)
[SWPU2019]伟大的侦探
iloveholmesandwllm
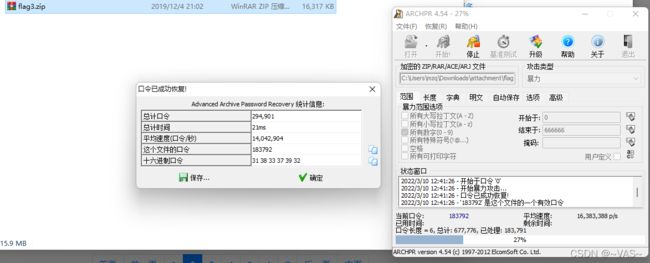
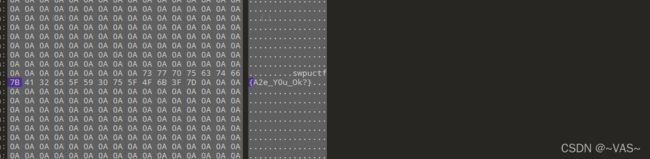
[GUET-CTF2019]KO
黑客帝国
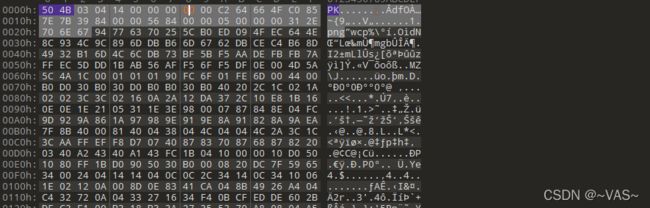
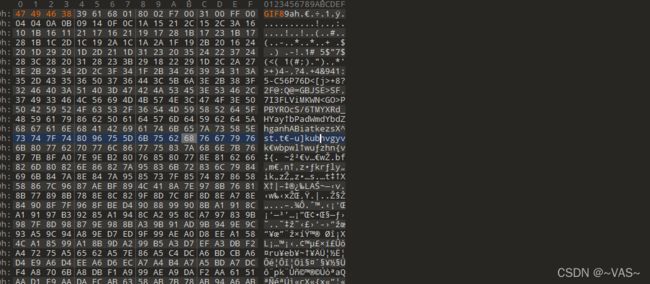
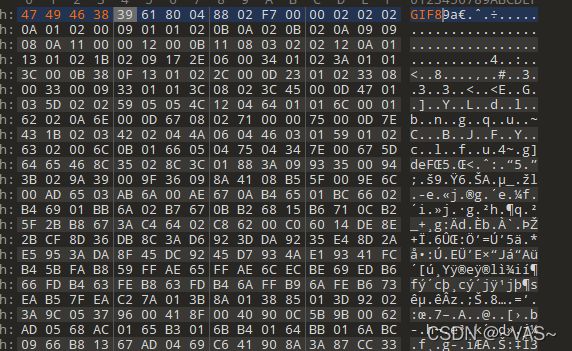
txt的数据头部数据明显是rar的16进制头部,保存为rar
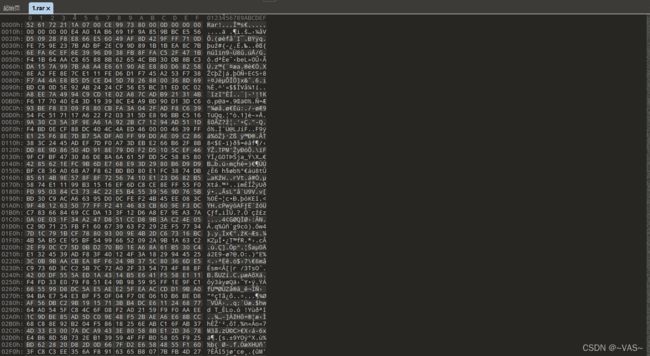
打开发现有密码进行常规的1-8位爆破
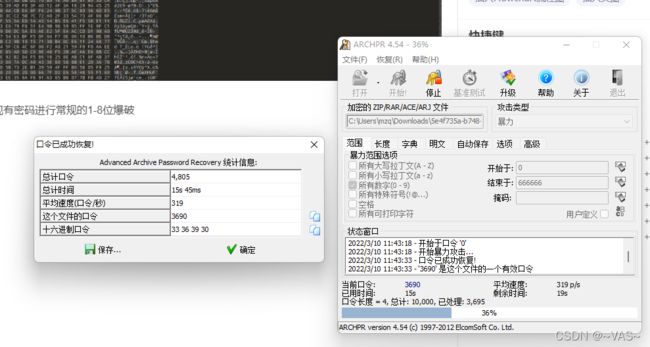
解压后用010editor打开图片,修改正确的头部
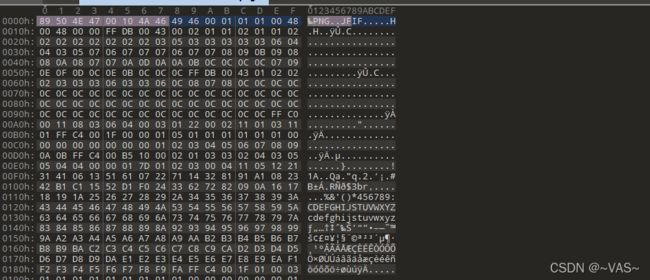
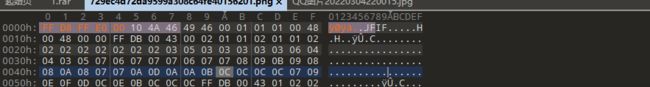

[MRCTF2020]你能看懂音符吗
[MRCTF2020]ezmisc
修复图片高宽
sqltest
flag{47edb8300ed5f9b28fc54b0d09ecdef7}