华为防火墙 DMZ 设置
DMZ 是英文"Demilitarized Zone"的缩写,中文名称为"隔离区"
它是为了解决安装防火墙后外部网络不能访问内部网络服务器的问题,而设立的一个位于内部网络与外部网络之间的缓冲区,在这个网络区域内可以放置一些公开的服务器资源。
例如FTP服务器、E-Mail服务器及网站服务器等允许外部用户访问这些服务器,但不可能接触到存放在内网中的信息,就算黑客入侵DMZ服务器,也不会影响到公司内部网络安全,不允许任何外部网络的直接访问,实现内外网分离,在企业的信息安全防护加了一道屏障。
环境:
虚拟机2台:Windows10,Windows Server 2012 R2
外网IP3个: 192.168.137.11,192.168.137.12,192.168.137.13
实现的功能:
1、内网客户端和DMZ服务器可以上网
2、内网可以访问DMZ服务器,但是DMZ服务器不能访问内网
3、外网可以远程桌面DMZ服务器
拓扑图如下:
一、外网
1、配置外网IP
sys
[Huawei]sys R1
[FW1]un in en
# 开启 DHCP
[FW1]dhcp enable
# 配置三个外网
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]ip addr 192.168.137.10 24
[FW1-GigabitEthernet1/0/0]ip addr 192.168.137.11 24 sub
[FW1-GigabitEthernet1/0/0]ip addr 192.168.137.12 24 sub
[FW1-GigabitEthernet1/0/0]service-manage all permit
[FW1-GigabitEthernet1/0/0]quit
# 配置外网区域
[FW1]firewall zone untrust
[FW1-zone-untrust]add int g1/0/0
[FW1-zone-untrust]quit 2、安全策略
# 安全策略
[FW1]security-policy
[FW1-policy-security]rule name "untrust to local"
[FW1-policy-security-rule-untrust to local]source-zone untrust
[FW1-policy-security-rule-untrust to local]destination-zone local
[FW1-policy-security-rule-untrust to local]action permit
[FW1-policy-security-rule-untrust to local]rule name "local to untrust"
[FW1-policy-security-rule-local to untrust]source-zone local
[FW1-policy-security-rule-local to untrust]destination-zone untrust
[FW1-policy-security-rule-local to untrust]action permit
[FW1-policy-security-rule-local to untrust]rule name "trust to untrust"
[FW1-policy-security-rule-trust to untrust]source-zone trust
[FW1-policy-security-rule-trust to untrust]destination-zone untrust
[FW1-policy-security-rule-trust to untrust]source-address address-set 192.168.100.*
[FW1-policy-security-rule-trust to untrust]action permit
[FW1-policy-security-rule-trust to untrust]quit二、内网
1、配置内网IP
# 配置内网
[FW1-policy-security]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip addr 192.168.100.254 24
[FW1-GigabitEthernet1/0/1]dhcp select int
[FW1-GigabitEthernet1/0/1]dhcp server dns-list 114.114.114.114
[FW1-GigabitEthernet1/0/1]service-manage ping permit
[FW1-GigabitEthernet1/0/1]quit
# 配置内网区域
[FW1]firewall zone trust
[FW1-zone-trust]add int g1/0/1
[FW1-zone-trust]quit
# 配置地址列表
[FW1]ip address-set 192.168.100.* type object
[FW1-object-address-set-192.168.100.*]address 0 192.168.100.0 mask 24
[FW1-object-address-set-192.168.100.*]quit
# 配置Nat策略实现上网
[FW1]nat-policy
[FW1-policy-nat]rule name "snat 1"
[FW1-policy-nat-rule-snat 1]source-zone trust
[FW1-policy-nat-rule-snat 1]egress-interface GigabitEthernet1/0/0
[FW1-policy-nat-rule-snat 1]action source-nat easy-ip
[FW1-policy-nat-rule-snat 1]quit2、配置路由和DNS
# 设置静态路由
[FW1-policy-nat]ip route-static 0.0.0.0 0.0.0.0 192.168.137.1
# 防火墙配置 DNS
[FW1]dns resolve
[FW1]dns server 114.114.114.114
三、DMZ
1、配置DMZ区域IP
# 配置DMZ
[FW1]int g1/0/2
[FW1-GigabitEthernet1/0/2]ip addr 192.168.200.254 24
[FW1-GigabitEthernet1/0/2]dhcp select int
[FW1-GigabitEthernet1/0/2]dhcp server dns-list 114.114.114.114
[FW1-GigabitEthernet1/0/2]service-manage ping permit
[FW1-GigabitEthernet1/0/2]quit
# 配置DMZ区域
[FW1]firewall zone dmz
[FW1-zone-dmz]add int g1/0/2
[FW1-zone-dmz]quit
# 配置地址列表
[FW1]ip address-set 192.168.200.* type object
[FW1-object-address-set-192.168.200.*]address 0 192.168.200.0 mask 24
[FW1-object-address-set-192.168.200.*]quit
2、配置安全策略
# 安全策略
[FW1]security-policy
[FW1-policy-security]rule name "dmz to untrust"
[FW1-policy-security-rule-dmz to untrust]source-zone dmz
[FW1-policy-security-rule-dmz to untrust]destination-zone untrust
[FW1-policy-security-rule-dmz to untrust]source-address address-set 192.168.200.*
[FW1-policy-security-rule-dmz to untrust]action permit
[FW1-policy-security-rule-dmz to untrust]rule name "untrust to dmz"
[FW1-policy-security-rule-untrust to dmz]source-zone untrust
[FW1-policy-security-rule-untrust to dmz]destination-zone dmz
[FW1-policy-security-rule-untrust to dmz]destination-address address-set 192.168.200.*
[FW1-policy-security-rule-untrust to dmz]action permit
[FW1-policy-security-rule-untrust to dmz]rule name "trust to dmz"
[FW1-policy-security-rule-trust to dmz]source-zone trust
[FW1-policy-security-rule-trust to dmz]destination-zone dmz
[FW1-policy-security-rule-trust to dmz]source-address address-set 192.168.100.*
[FW1-policy-security-rule-trust to dmz]destination-address address-set 192.168.200.*
[FW1-policy-security-rule-trust to dmz]action permit
[FW1-policy-security-rule-trust to dmz]quit
3、配置NAT策略
# nat策略 实现上网
[FW1-policy-security]nat-policy
[FW1-policy-nat]rule name "snat 2"
[FW1-policy-nat-rule-snat 2]source-zone dmz
[FW1-policy-nat-rule-snat 2]egress-interface GigabitEthernet1/0/0
[FW1-policy-nat-rule-snat 2]action source-nat easy-ip
# nat策略 实现目标端口转换
[FW1-policy-nat-rule-snat 2]rule name "dnat 1"
[FW1-policy-nat-rule-dnat 1]source-zone untrust
[FW1-policy-nat-rule-dnat 1]destination-address 192.168.137.11 mask 255.255.255.255
[FW1-policy-nat-rule-dnat 1]service protocol tcp source-port 0 to 65535 destination-port 33389
[FW1-policy-nat-rule-dnat 1]action destination-nat static port-to-port address 192.168.200.2 3389
[FW1-policy-nat-rule-dnat 1]quit四、验证
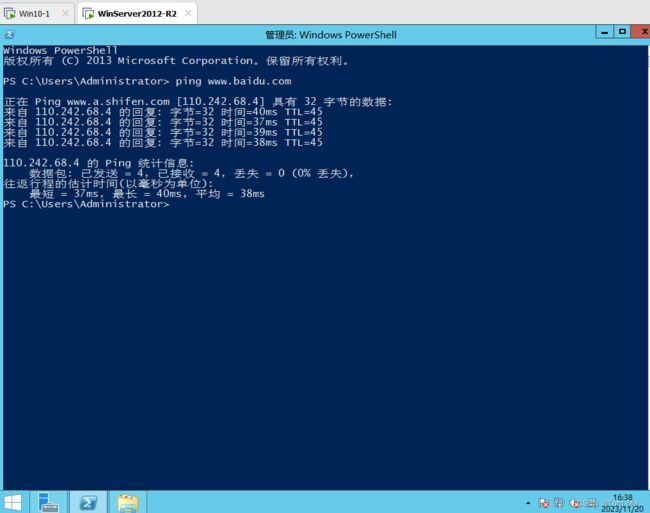
1、客户端上网
2、服务器上网
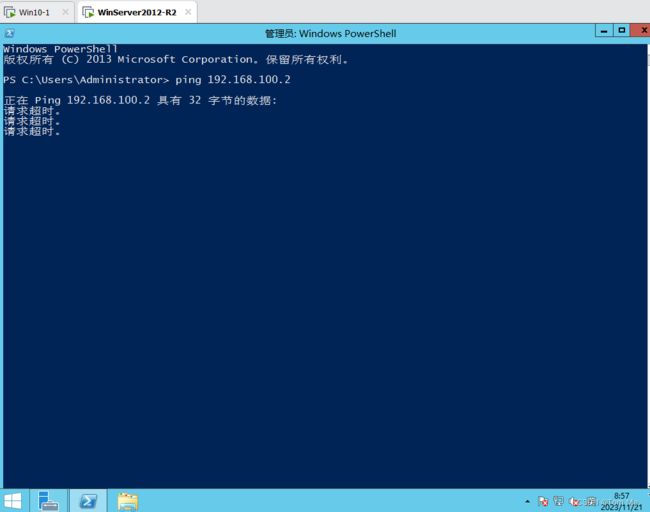
3、内网可以访问DMZ
4、DMZ 不能访问 内网
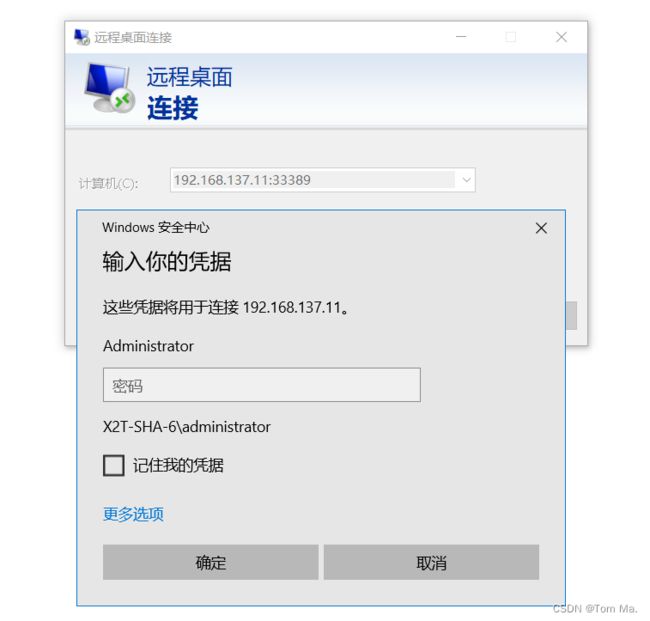
4、验证目的端口转换
当我们访问 192.168.137.11 33389 端口时,已成功转到换 Win2012 这台服务器的 3389 端口上面