0592-5.16.1-如何配置Kerberos高可用
1 文档编写目的
对于一个启用了Kerberos的正式生产系统,还需要考虑KDC的高可用。而Kerberos服务是支持配置为主备模式的,数据同步是通过kprop服务将主节点的数据同步到备节点。本文主要讲述如何在CDH5.16.1中配置Kerberos服务的高可用。在前面的文章中Fayson介绍过《如何配置Kerberos服务的高可用》,但无论是CDH还是OS版本到较低,本文也主要是为了更新文档。
- 内容概述
1.备节点安装Kerberos服务
2.主备节点Kerberos配置修改
3.主节点数据同步至备节点并配置同步任务
- 测试环境
1.CM和CDH版本为CDH 5.16.1
2.操作系统为RedHat7.2
3.采用root用户
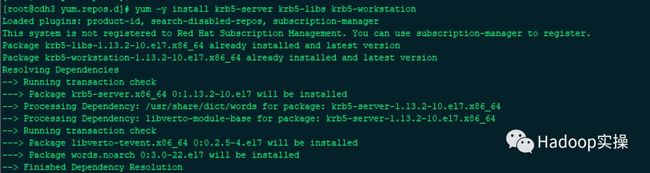
2 备节点安装Kerberos服务
yum install -y krb5-server openldap-clients krb5-workstation krb5-libs
注意:此处只安装服务,暂不做相应配置及启动服务。
3 主Kerberos节点操作
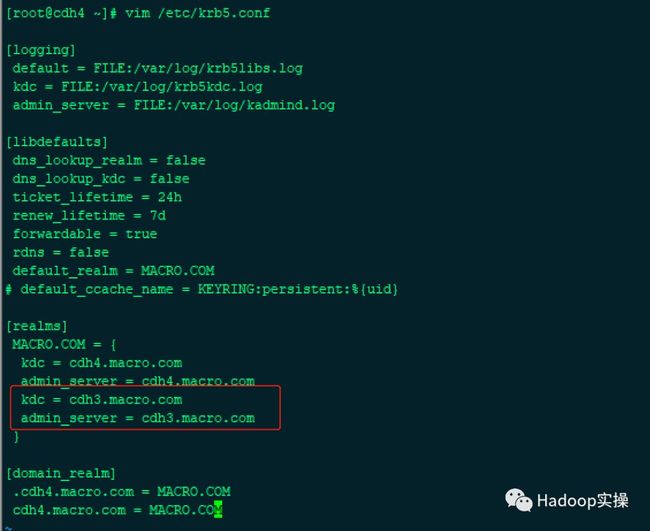
1.修改/etc/krb5.conf的配置文件,在realms配置下增加备Kerberos的配置
[realms]
CLOUDERA.COM = {
kdc = cdh4.macro.com
admin_server = cdh4.macro.com
kdc = cdh3.macro.com
admin_server = cdh3.macro.com
}
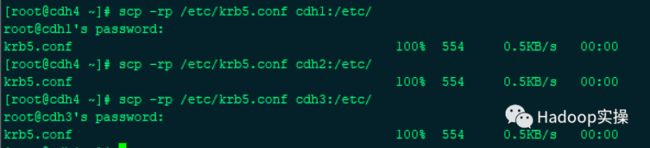
2.将修改后的/etc/krb5.conf文件同步到集群的所有Kerberos客户端节点相应目录
scp -rp /etc/krb5.conf cdh1:/etc/
scp -rp /etc/krb5.conf cdh2:/etc/
scp -rp /etc/krb5.conf cdh3:/etc/
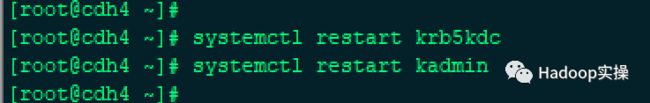
3.保存配置,然后重启krb5kdc和kadmin服务
systemctl restart krb5kdc
systemctl restart kadmin
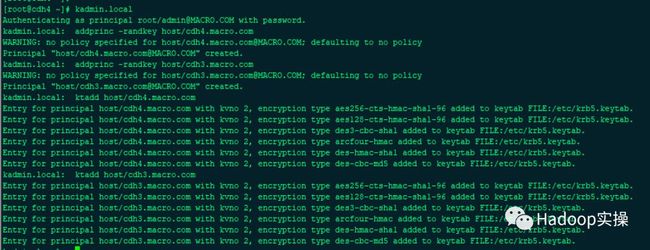
4.创建主从同步账号,并为账号生成keytab文件
kadmin.local
kadmin.local: addprinc -randkey host/cdh4.macro.com
kadmin.local: addprinc -randkey host/cdh3.macro.com
kadmin.local:
kadmin.local: ktadd host/cdh4.macro.com
kadmin.local: ktadd host/cdh3.macro.com
使用随机生成秘钥的方式创建同步账号,并使用ktadd命令生成同步账号的keytab文件,默认文件生成在/etc/krb5.keytab下,生成多个账号则在krb5.keytab基础上追加。
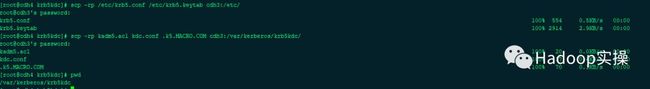
5.复制以下文件到备Kerberos服务器相应目录
将/etc目录下的krb5.conf和krb5.keytab文件拷贝至备Kerberos服务器的/etc目录下
将/var/kerberos/krb5kdc目录下的.k5.CLOUDERA.COM、kadm5.acl和krb5.conf文件拷贝至备Kerberos服务器的/var/kerberos/krb5kdc目录
cd /var/kerberos/krb5kdc
scp -rp /etc/krb5.conf /etc/krb5.keytab cdh3:/etc/
scp kadm5.acl kdc.conf .k5.MACRO.COM cdh3:/var/kerberos/krb5kdc/
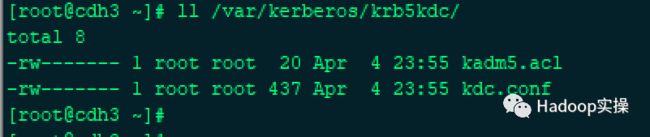
备节点查看
4 备Kerberos节点操作
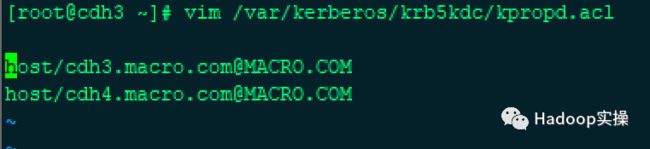
1.需要申明用来同步的用户,在/var/kerberos/krb5kdc/kpropd.acl配置文件中添加对应账户,如果配置文件不存在则新增
[root@cdh3 ~]# vim /var/kerberos/krb5kdc/kpropd.acl
host/cdh3.macro.com@MACRO.COM
host/cdh4.macro.com@MACRO.COM
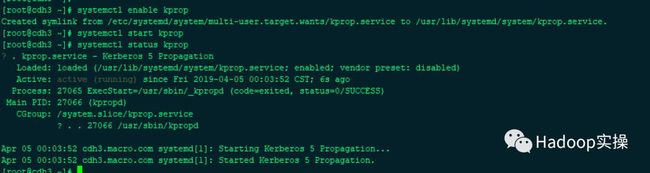
2.启动kprop服务并加入系统自启动
systemctl enable kprop
systemctl start kprop
systemctl status kprop
备节点上已经准备好数据传输。接下来在主节点上使用kdb5_util将Kerberos库导出,然后通过kprop命令向备节点同步数据。
5 节点数据同步至备节点
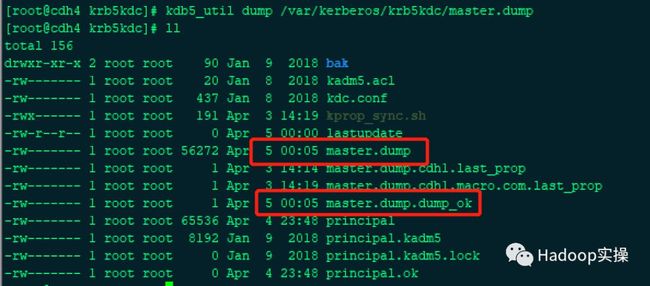
1.在主节点上使用kdb5_util命令导出Kerberos数据库文件
kdb5_util dump /var/kerberos/krb5kdc/master.dump
导出成功后生成master.dump和master.dump.dump_ok两个文件。
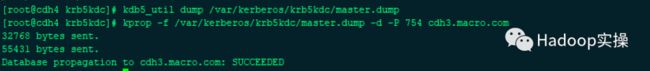
2.在主节点上使用kprop命令将master.dump文件同步至备节点
[root@cdh4 krb5kdc]# kdb5_util dump /var/kerberos/krb5kdc/master.dump
[root@cdh4 krb5kdc]# kprop -f /var/kerberos/krb5kdc/master.dump -d -P 754 cdh3.macro.com
32768 bytes sent.
55431 bytes sent.
Database propagation to cdh3.macro.com: SUCCEEDED
有如上图标识则表示数据同步成功。
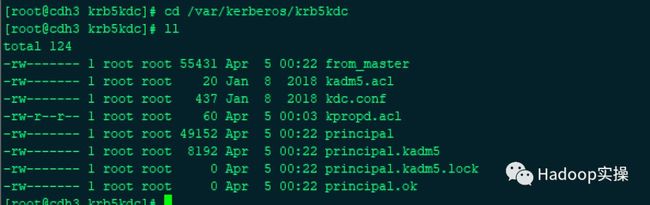
3.在备节点的/var/kerberos/krb5kdc目录下查看
[root@cdh3 krb5kdc]# cd /var/kerberos/krb5kdc
[root@cdh3 krb5kdc]# ll
在备节点的/var/kerberos/krb5kdc目录下增加了如上图标识的文件。
6 节点数据同步至备节点
1.在备节点上测试同步过来的数据是否能启动Kerberos服务
启动krb5kdc服务
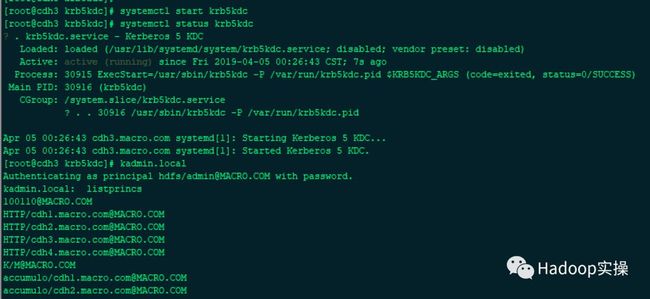
[root@cdh3 krb5kdc]# systemctl start krb5kdc
[root@cdh3 krb5kdc]# systemctl status krb5kdc
2.在备节点上验证kadmin服务是否正常
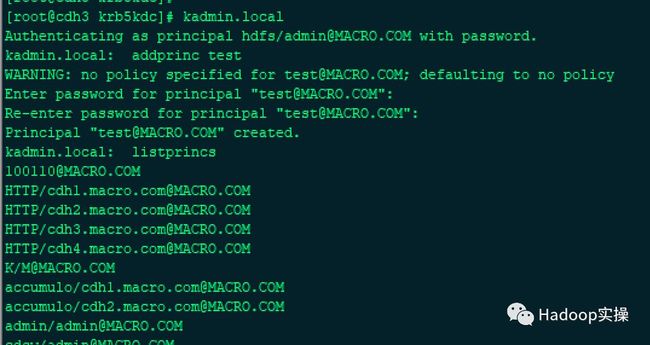
[root@cdh3 krb5kdc]# kadmin.local
Authenticating as principal hdfs/admin@MACRO.COM with password.
kadmin.local: addprinc test
WARNING: no policy specified for test@MACRO.COM; defaulting to no policy
Enter password for principal "[email protected]":
Re-enter password for principal "[email protected]":
Principal "[email protected]" created.
kadmin.local: listprincs
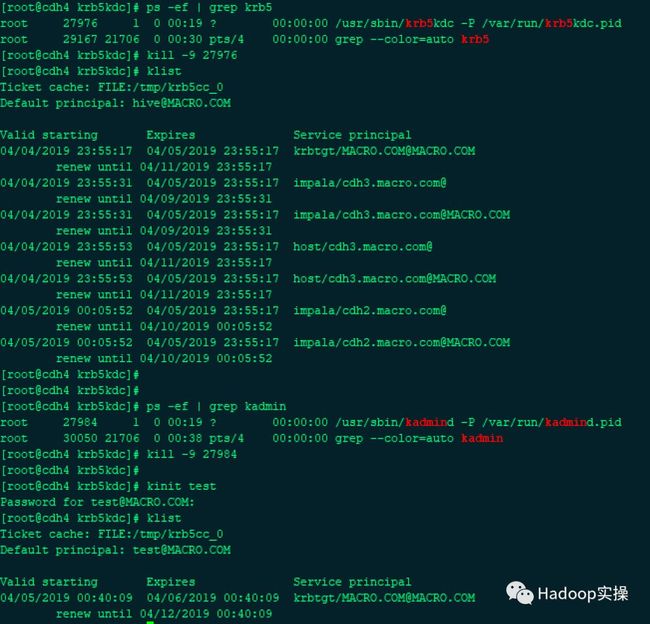
- kill主服务的krb5kdc服务和kadmin 服务进行验证
[root@cdh4 krb5kdc]# ps -ef | grep krb5
[root@cdh4 krb5kdc]# kill -9 27976
[root@cdh4 krb5kdc]# ps -ef | grep kadmin
[root@cdh4 krb5kdc]# kill -9 27984
[root@cdh4 krb5kdc]# ps -ef | grep kadmin
[root@cdh4 krb5kdc]# kill -9 27984
[root@cdh4 krb5kdc]# kinit test
[root@cdh4 krb5kdc]# klist
4.在备用服务器上服务依旧正常,可以正常添加凭证
[root@cdh3 krb5kdc]# kadmin.local
Authenticating as principal hdfs/admin@MACRO.COM with password.
kadmin.local: addprinc test111
WARNING: no policy specified for test111@MACRO.COM; defaulting to no policy
Enter password for principal "[email protected]":
Re-enter password for principal "[email protected]":
Principal "[email protected]" created.
kadmin.local: listprinc
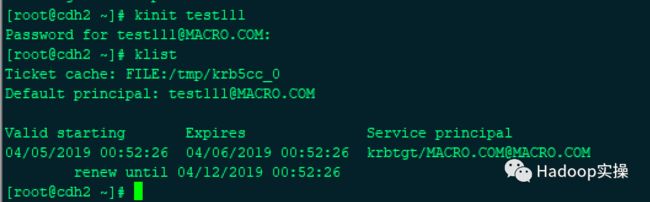
5.并且在其他客户端节点初始化刚新增的凭证正常
[root@cdh2 ~]# kinit test111
Password for test111@MACRO.COM:
[root@cdh2 ~]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: test111@MACRO.COM
7 配置主节点crontab任务定时同步数据
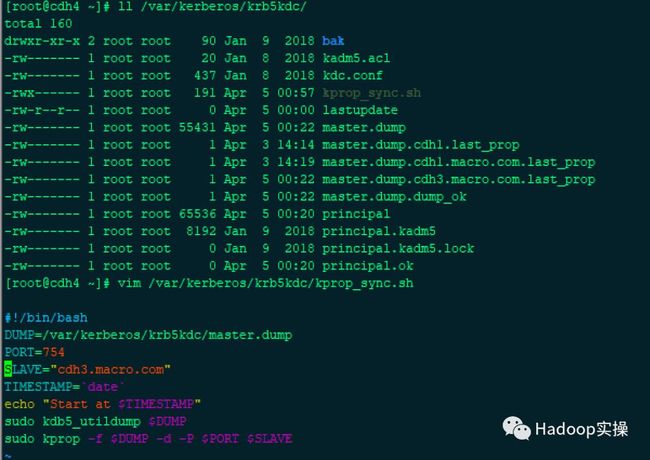
1.编写同步脚本
[root@cdh4 ~]# vim /var/kerberos/krb5kdc/kprop_sync.sh
#!/bin/bash
DUMP=/var/kerberos/krb5kdc/master.dump
PORT=754
SLAVE="cdh4.macro.com"
TIMESTAMP=`date`
echo "Start at $TIMESTAMP"
sudo kdb5_utildump $DUMP
sudo kprop -f $DUMP -d -P $PORT $SLAVE
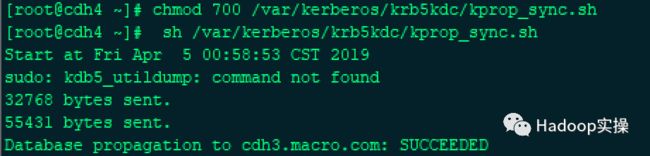
2.赋予kprop_sync.sh脚本可执行权限,并测试
[root@cdh4 ~]# chmod 700 /var/kerberos/krb5kdc/kprop_sync.sh
[root@cdh4 ~]# sh /var/kerberos/krb5kdc/kprop_sync.sh
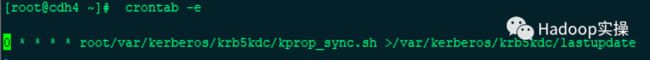
3.配置crontab任务
[root@cdh4 ~]# crontab -e
0 * * * * root/var/kerberos/krb5kdc/kprop_sync.sh >/var/kerberos/krb5kdc/lastupdate
退出并保存,启动服务并设置开机启动
[root@cdh4 ~]# systemctl enable crond
[root@cdh4 ~]# systemctl start crond