Linux之iptables及firewall超详解
目录
一.搭建web服务,设置任何人能够通过80端口访问
1.设置任何人都可以通过80端口访问web服务器
2.查看配置表确保已经成功配置
3.访问服务器可以看到成功访问
4.删除策略
5.发现不能访问
二.禁止所有人ssh远程登录该服务器
1.默认开放ssh服务,先在客户测试端远程登录
2.添加策略,禁止所有人ssh远程登录
3.在客户端上测试发现远程登陆失效
4.由于使用的Xshell也是使用ssh远程登陆的,所以会断开,只能在VMware上删除策略
三.禁止某个主机地址ssh远程登录该服务器,允许该主机访问服务器的web服务
1.禁止客户端远程登录服务器
2.在客户端测试
3.添加策略允许客户端访问web服务
4.客户端上测试成功访问到web服务
四.禁止某个ip地址进行ssh访问
在指定ip的机器上不能远程登录
五.配置端口转发(在192.168.40.0网段的主机访问该服务器的5423端口将被转发到80端口)
1. 添加富规则进行端口转发
2.重新加载配置
3.访问5423端口
六.此规则将本机80端口转发到192.168.40.131的8080端口上
一.搭建web服务,设置任何人能够通过80端口访问
1.设置任何人都可以通过80端口访问web服务器
[root@rhcsa ~]# iptables -I INPUT -p tcp --dport 80 -j ACCEPT2.查看配置表确保已经成功配置
[root@rhcsa ~]# iptables -L --line-numbers
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT tcp -- anywhere anywhere tcp dpt:http
2 ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
3 ACCEPT icmp -- anywhere anywhere
4 ACCEPT all -- anywhere anywhere
5 ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
6 REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
1 REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination 3.访问服务器可以看到成功访问
4.删除策略
[root@rhcsa ~]# iptables -D INPUT 1
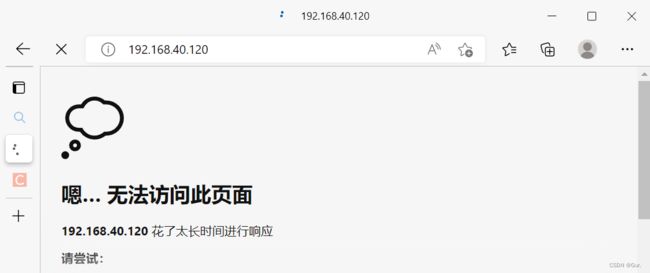
5.发现不能访问
二.禁止所有人ssh远程登录该服务器
1.默认开放ssh服务,先在客户测试端远程登录
[root@rhce ~]# ssh [email protected]
The authenticity of host '192.168.40.129 (192.168.40.129)' can't be established.
ECDSA key fingerprint is SHA256:70V58bQzrfUci7EE23sAS/cd7Zjc3zbRhTx15uN1PVY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.40.129' (ECDSA) to the list of known hosts.
[email protected]'s password:
Activate the web console with: systemctl enable --now cockpit.socket
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
Last login: Sun Jul 31 08:16:08 2022 from 192.168.40.1
2.添加策略,禁止所有人ssh远程登录
iptables -I INPUT -p tcp --dport 22 -j REJECT3.在客户端上测试发现远程登陆失效
[root@rhce ~]# ssh [email protected]
ssh: connect to host 192.168.40.129 port 22: Connection refused
4.由于使用的Xshell也是使用ssh远程登陆的,所以会断开,只能在VMware上删除策略
三.禁止某个主机地址ssh远程登录该服务器,允许该主机访问服务器的web服务
1.禁止客户端远程登录服务器
[root@rhcsa ~]# iptables -I INPUT -p tcp -s 192.168.40.131 --dport 22 -j REJECT2.在客户端测试
[root@rhce ~]# ssh [email protected]
ssh: connect to host 192.168.40.129 port 22: Connection refused
3.添加策略允许客户端访问web服务
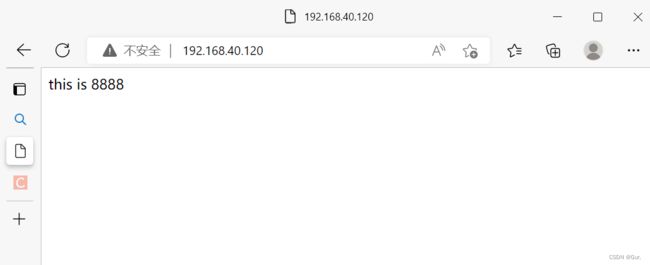
[root@rhcsa ~]# iptables -I INPUT -p tcp -s 192.168.40.131 --dport 80 -j ACCEPT4.客户端上测试成功访问到web服务
[root@rhce ~]# curl 192.168.40.120
this is 8888
四.禁止某个ip地址进行ssh访问
#移除允许所有人通过ssh远程连接的配置
[root@rhcsa ~]# firewall-cmd --permanent --remove-service=ssh
success
#添加富规则禁止特定的ip通过ssh远程连接
[root@rhcsa ~]# firewall-cmd --permanent --add-rich-rule 'rule family="ipv4" source address="192.168.40.131" service name="ssh" reject'
success
#重新加载当前配置
[root@rhcsa ~]# firewall-cmd --reload
success[root@rhcsa ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens160 ens224
sources:
services: cockpit dhcpv6-client http
ports: 2222/tcp 8888/tcp
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="192.168.40.131" service name="ssh" reject在指定ip的机器上不能远程登录
[root@rhce ~]# ssh [email protected]
ssh: connect to host 192.168.40.129 port 22: Connection refused
五.配置端口转发(在192.168.40.0网段的主机访问该服务器的5423端口将被转发到80端口)
1. 添加富规则进行端口转发
[root@rhcsa ~]# firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.40.0/24" forward-port port="5423" protocol="tcp" to-port="80"'
success
2.重新加载配置
[root@rhcsa ~]# firewall-cmd --reload
success
3.访问5423端口

六.此规则将本机80端口转发到192.168.40.131的8080端口上
[root@rhcsa ~]# firewall-cmd --add-forward-port=port=80:proto=tcp:toport=8080:toaddr=192.168.40.131 --permanent
success
[root@rhcsa ~]# firewall-cmd --reload
success