- 算法1-3 全排列问题
咚咚轩
dfs
题目描述按照字典序输出自然数1到n所有不重复的排列,即n的全排列,要求所产生的任一数字序列中不允许出现重复的数字。输入格式一个整数n。输出格式由1∼n组成的所有不重复的数字序列,每行一个序列。每个数字保留5个场宽。输入输出样例输入#13输出#1123132213231312321说明/提示1≤n≤9。#include#includeusingnamespacestd;intn;inta[12];i
- 算法1-3 选数
咚咚轩
搜索递归
题目描述已知n个整数x1,x2,⋯,xn,以及1个整数k(k#includeusingnamespacestd;intn,k;inta[22],ans;//判断质数boolprime(intnum){if(num>n>>k;for(inti=1;i>a[i];}f(1,k,0);cout<
- 高精度 A+B Problem
咚咚轩
高精度加法
题目描述高精度加法,相当于a+bproblem,不用考虑负数。输入格式分两行输入。a,b≤。输出格式输出只有一行,代表a+b的值。输入输出样例输入#111输出#12输入#210019099输出#210100方法1:结果用数组返回(推荐)#includeusingnamespacestd;strings1,s2;inta[100001],b[100001],c[100001];//三个整数数组,用于
- C39RF C39RF Applied Financial
后端
Subject:C39RFAppliedFinancialModellinginPythonCaseStudy1Date:Submissiondeadline:28thofFebruary,12pmUKtime,4pmDubaitime,and8pmMalaysiatime.Pleasenotethefollowingbeforeyoucommencetheassignment:•Youhavet
- DAT 560G: Database Design and SQL
后端
DAT560G:DatabaseDesignandSQLSpring2025,MiniAAssignment#4:SQLPart3Instructions1.Thisisanindividualassignment.Youmaynotdiscussyourapproachtosolvingthesequestionswithanyone,otherthantheinstructororTA.2.P
- COMP3425 Data Mining S1 2025
后端
COMP3425DataMiningS12025UndergraduateAssignment1Maximummarks100Weight20%ofthetotalmarksforthecourseMintopasshurdle30%LengthMaximumof8pagesexcludingcoverpage,bibliographyandappendices.LayoutA4.Atleast1
- 4 算法1-3 三连击(升级版)
咚咚轩
枚举
题目描述将1,2,…,9共9个数分成三组,分别组成三个三位数,且使这三个三位数的比例是A:B:C,试求出所有满足条件的三个三位数,若无解,输出No!!!。输入格式三个数,A,B,C。输出格式若干行,每行3个数字。按照每行第一个数字升序排列。输入输出样例输入#1123输出#1192384576219438657273546819327654981说明/提示保证Ausingnamespacestd;i
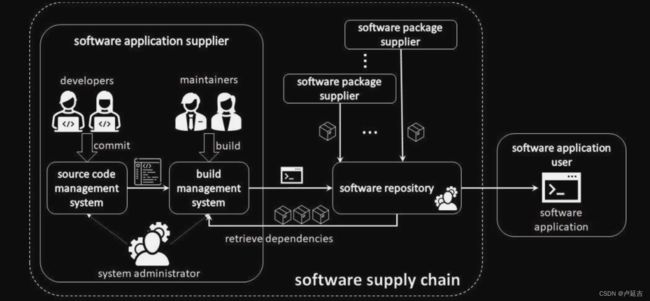
- 软件供应链安全工具链研究系列—RASP自适应威胁免疫平台(下篇)
DevSecOps选型指南
安全网络软件供应链安全工具HW
在“软件供应链安全工具链研究系列—RASP自适应威胁免疫平台-上篇”中我们提到了RASP工具的基本能力、原理以及工具的应用场景,了解到了RASP工具在各场景下发挥的价值。那么在当今高强度攻防对抗的大场景下,RASP作为最后一道防线,不论是从高危漏洞修复还是应对高级攻击技术,都有着更高的要求。1.工具应具备的能力建议1.1技术能力方面建议1.1.1虚拟补丁技术RASP在为应用系统赋予威胁免疫能力的同
- 深入拆解Nightingale(一)
weixin_47028810
夜莺运维github开源软件golang
前言了解了一段时间的开源项目夜莺,虽说看了一些官方提供了文档和还有视频,并且有幸参加快猫的黄埔营培训,算是新手入门水平。还是存在很多问题不懂,我想关键应该其中细节并没有很了解,另一方面也听大佬说‘阅读优秀的源代码是软件工程师提高自己编程能力和学习开源框架的最佳手段之一’,所有我打算写一系列关于夜莺监控在源码级别的分析,希望能做到深入拆解的地步并且深入浅出的表达出来,哈哈哈。ps夜莺是源于滴滴,目前
- JS :移除数组中的指定数据
25号底片~
jsjavascript前端开发语言
1.Array.prototype.filter()方法filter()方法会创建一个新数组,包含所有通过测试的元素。可以通过过滤掉不需要的元素来实现移除。constarray=[1,2,3,4,5];constitemToRemove=3;constnewArray=array.filter(item=>item!==itemToRemove);console.log(newArray);//输
- [k8s源码]9.workqueue
weixin_45396500
k8s源码java开发语言
client-go是一个库,提供了与KubernetesAPI服务器交互的基础设施。它提供了诸如Informer、Lister、ClientSet等工具,用于监听、缓存和操作Kubernetes资源。而自定义控制器则利用这些工具来实现特定的业务逻辑和自动化任务。业务逻辑实现:client-go不包含特定的业务逻辑。自定义控制器允许实现特定于您的应用程序或需求的逻辑。扩展Kubernetes:通过自
- JAVA面试常见题_基础部分_Mysql调优
茂茂在长安
mysqlJAVAjava面试mysql
性能监控使用showprofile查询剖析工具,可以指定具体的type此工具默认是禁用的,可以通过服务器变量在绘画级别动态的修改setprofiling=1;当设置完成之后,在服务器上执行的所有语句,都会测量其耗费的时间和其他一些查询执行状态变更相关的数据。select*fromemp;在mysql的命令行模式下只能显示两位小数的时间,可以使用如下命令查看具体的执行时间showprofiles;执
- 常用Python代码
newlz2000
python
常见的for循环去博客设置页面,选择一款你喜欢的代码片高亮样式,下面展示同样高亮的代码片.1Value=[(10,150),(100,200),(180,230)]fori,(minVal,maxVal)inenumerate(Value):plt.subplot(1,3,i+1)edges=cv2.Canny(image,minVal,maxVal)edges=cv2.GaussianBlur(
- Qt 中,**信号与槽(Signals & Slots)机制
enyp80
qt数据库开发语言
在Qt中,信号与槽(Signals&Slots)机制是实现对象间通信的核心模式,通常也被视为一种高效的“通知者模式”。它允许对象在特定事件发生时通知其他对象,且完全解耦。核心概念信号(Signal)由signals关键字声明,表示事件发生(如用户点击、数据更新)。无需实现代码,由Qt的元对象系统(Meta-ObjectSystem)自动生成。示例:voidvalueChanged(intnewVa
- 小程序侧边导航栏左右联动
ShinyRuo_
小程序javascript前端
1.点击左边导航栏,右边内容滚动到指定区域用scroll-view组件中的scroll-into-view来解决{{item.name}}{{item.name}}{{items.name}}data(){activeIndex:0,//导航栏高亮索引contentActive:null,//内容块scroll-into-view的idheightArr:[],//内容块高度数组container
- Ollama本地私有化部署通义千问大模型Qwen2.5
ErbaoLiu
数据分析&大模型机器学习&大模型自然语言处理&大模型大模型LLMQwen2.5Qwen2Ollama
目录Qwen2.5介绍Qwen2.5新闻Ollama介绍Linux安装Ollama一键安装Ollama手工安装Ollama卸载OllamaOllama运行Qwen2基于Transformers进行推理本文复现环境:Python3.12.6+Windows8.1+LinuxCentOS7+PyCharmCommunityEdition2022.3.3。Qwen2.5github地址如下:GitHub
- Python 列表与元组全攻略:从新手到高手的必备指南
吴师兄大模型
python开发语言列表(List)元组(Tuple)算法编程PYTHON
Langchain系列文章目录01-玩转LangChain:从模型调用到Prompt模板与输出解析的完整指南02-玩转LangChainMemory模块:四种记忆类型详解及应用场景全覆盖03-全面掌握LangChain:从核心链条构建到动态任务分配的实战指南04-玩转LangChain:从文档加载到高效问答系统构建的全程实战05-玩转LangChain:深度评估问答系统的三种高效方法(示例生成、手
- 注意力机制(Attention Mechanism)详细分类与介绍
Jason_Orton
分类数据挖掘人工智能
注意力机制(AttentionMechanism)是近年来在深度学习中非常流行的一种技术,特别是在自然语言处理(NLP)、计算机视觉等任务中,具有显著的效果。它的核心思想是模仿人类在处理信息时的注意力分配方式,根据不同部分的重要性给予不同的关注程度。1.注意力机制的背景与动机在传统的深度学习模型(如RNN、CNN等)中,信息处理通常是按照固定的规则和结构进行的,模型对输入的各个部分给予相同的关注。
- 第十章:服务器消费者管理模块
转调
仿Rabbit消息队列c++消息队列
目录第一节:代码实现1-1.Consumer类1-2.QueueConsumer类1-3.QueueConsumerManger类第二节:单元测试下期预告:服务器的消费者管理模块在mqserver目录下实现。第一节:代码实现创建一个名为mq_consumer.hpp的文件,打开并做好前置工作:#ifndef__M_CONSUMER_H__#define__M_CONSUMER_H__#includ
- 回合制游戏文字版(升级)
漫漫不慢.
游戏
//在上一篇博客的基础上,加了细节的改动//改动:添加了外貌,性别,招式的细节描绘;添加了个人信息展示界面//一创建java文件1,命名为playGamepackagetest2;importjava.util.Random;publicclassplayGame{//格斗游戏,每个游戏角色的姓名,血量,都不相同,在选定人物的时候(new对象的时候),这些信息就应该被确定下来//eg:姓名:乔峰血
- 策略模式环境类的实现方式对比
-代号9527
JavaDev策略模式
文章目录1、策略模式2、聚合策略类实现方式一3、聚合策略类实现方式二4、对比5、补充:ApplicationContextAware接口1、策略模式近期工作中,需要处理4.x和5.x两个版本的数据,所以自然想到的是策略模式,写一个抽象类,然后两个版本分别实现抽象类,以后也好扩展。publicinterfaceClusterMetaDataProcessor{voidprocessData();}p
- TensorFlow 架构
weixin_zdpau
AItensorflow人工智能神经网络
https://www.tensorflow.org/guide/extend/architecture一WedesignedTensorFlowforlarge-scaledistributedtrainingandinference,butitisalsoflexibleenoughtosupportexperimentationwithnewmachinelearningmodelsands
- 使用mybatisPlus的queryWrapper做左联接,内联接
R-sz
mybatisjavamysql
在service层生成使用mybatisplus的querywapper的Java代码SELECTbs_user.id,bs_user.mobile,bs_user.username,bs_user.password,bs_user.enable_state,ss_user_social_security.user_id,ss_user_social_security.enterprises_pa
- nestjs+mysql+prisma + swagger项目搭建
哆啦咪唏
mysqljavascriptprismanestjs
nestjs学习(一)项目地址1.基础操作安装nestyarnadd-g@nestjs/cli创建项目nestnewproject-name启动服务器yarnrunstartyarnstart:dev监听文件变化,自动重启服务使用nest-cli快速创建service/controller,会自动引入Module中nestg[文件类型][文件名][文件目录(src目录下)]详细过程可以参考nest
- 谷歌浏览器chrome插件、扩展程序无法下载的解决方法
weixin_33878457
以下是下载离线插件包的方法:每个GoogleChrome扩展都有一个固定的ID,例如https://chrome.google.com/webstore/detail/bfbmjmiodbnnpllbbbfblcplfjjepjdn把这个扩展的ID复制下来,替换下面URL中的“~~~~”https://clients2.google.com/service/update2/crx?response
- Qt for Android下QMessageBox背景黑色、文字点击闪烁
子建莫敌
Qtqtandroidc++QMessageBox文字闪烁背景黑色
最近在基于Qt开发安卓应用的时候,在红米平板上默认QMessageBox出现之后,背景黑色,并且点击提示文字会出现闪烁,影响用户体验。问题分析1、设置QMessageBox样式,设置背景色、文字颜色,如下所示:QMessageBox{background:white;color:white;}尝试之后,问题仍存在2、继承QMessageBox,自定义MessageboxMessagebox:pub
- 播放音频uni-app
qq_37902065
varp=plus.audio.createPlayer("/static/test.mp3");p.play();setTimeout(function(){p.stop()},5000)
- uniapp实现复制粘贴功能(uni.setClipboardData、uni.getClipboardData)
Komorebi ঞ꧔ꦿ
uniappuni-app小程序前端
思路:使用uniapp的uni.setClipboardData(设置系统剪贴板的内容)和uni.getClipboardData(获取系统剪贴板内容)要复制的内容:{{qq}}exportdefault{data(){return{qq:'1111',};},methods:{copyContent(data){uni.setClipboardData({data,success:functio
- 救命!论文被知网判定AI生成?别慌!手把手教你3分钟自救
chatpaper001
人工智能自然语言处理深度学习AIGCAI写作
最近知网搞了个大动作!2025年2月13日刚更新的学术检测系统,直接把论文圈炸了锅。新上线的AIGC检测2.13版本,连文献综述都可能被打上"AI生成"标签!这次更新有多狠?看这3点就知道1️⃣AI检测准到离谱现在连固定模板的内容都可能中标。比如摘要、引言这些套路化部分,一不小心就被系统盯上。2️⃣专业术语成雷区理论名词、机构名称用多了,系统直接亮红灯。上周有个同学写"Transformer模型"
- A100 解析:为何它成为 AI 大模型时代的首选?
PPIO派欧云
算力gpu算力算法ai
前言NVIDIAA100TensorCoreGPU可针对AI、数据分析和HPC应用场景,在不同规模下实现出色的加速,有效助力更高性能的弹性数据中心。A100采用NVIDIAAmpere架构,是NVIDIA数据中心平台的引擎。A100的性能比上一代产品提升高达20倍,并可划分为七个GPU实例,以根据变化的需求进行动态调整。A100提供40GB和80GB显存两种版本,A10080GB将GPU显存增加了
- 遍历dom 并且存储(将每一层的DOM元素存在数组中)
换个号韩国红果果
JavaScripthtml
数组从0开始!!
var a=[],i=0;
for(var j=0;j<30;j++){
a[j]=[];//数组里套数组,且第i层存储在第a[i]中
}
function walkDOM(n){
do{
if(n.nodeType!==3)//筛选去除#text类型
a[i].push(n);
//con
- Android+Jquery Mobile学习系列(9)-总结和代码分享
白糖_
JQuery Mobile
目录导航
经过一个多月的边学习边练手,学会了Android基于Web开发的毛皮,其实开发过程中用Android原生API不是很多,更多的是HTML/Javascript/Css。
个人觉得基于WebView的Jquery Mobile开发有以下优点:
1、对于刚从Java Web转型过来的同学非常适合,只要懂得HTML开发就可以上手做事。
2、jquerym
- impala参考资料
dayutianfei
impala
记录一些有用的Impala资料
1. 入门资料
>>官网翻译:
http://my.oschina.net/weiqingbin/blog?catalog=423691
2. 实用进阶
>>代码&架构分析:
Impala/Hive现状分析与前景展望:http
- JAVA 静态变量与非静态变量初始化顺序之新解
周凡杨
java静态非静态顺序
今天和同事争论一问题,关于静态变量与非静态变量的初始化顺序,谁先谁后,最终想整理出来!测试代码:
import java.util.Map;
public class T {
public static T t = new T();
private Map map = new HashMap();
public T(){
System.out.println(&quo
- 跳出iframe返回外层页面
g21121
iframe
在web开发过程中难免要用到iframe,但当连接超时或跳转到公共页面时就会出现超时页面显示在iframe中,这时我们就需要跳出这个iframe到达一个公共页面去。
首先跳转到一个中间页,这个页面用于判断是否在iframe中,在页面加载的过程中调用如下代码:
<script type="text/javascript">
//<!--
function
- JAVA多线程监听JMS、MQ队列
510888780
java多线程
背景:消息队列中有非常多的消息需要处理,并且监听器onMessage()方法中的业务逻辑也相对比较复杂,为了加快队列消息的读取、处理速度。可以通过加快读取速度和加快处理速度来考虑。因此从这两个方面都使用多线程来处理。对于消息处理的业务处理逻辑用线程池来做。对于加快消息监听读取速度可以使用1.使用多个监听器监听一个队列;2.使用一个监听器开启多线程监听。
对于上面提到的方法2使用一个监听器开启多线
- 第一个SpringMvc例子
布衣凌宇
spring mvc
第一步:导入需要的包;
第二步:配置web.xml文件
<?xml version="1.0" encoding="UTF-8"?>
<web-app version="2.5"
xmlns="http://java.sun.com/xml/ns/javaee"
xmlns:xsi=
- 我的spring学习笔记15-容器扩展点之PropertyOverrideConfigurer
aijuans
Spring3
PropertyOverrideConfigurer类似于PropertyPlaceholderConfigurer,但是与后者相比,前者对于bean属性可以有缺省值或者根本没有值。也就是说如果properties文件中没有某个bean属性的内容,那么将使用上下文(配置的xml文件)中相应定义的值。如果properties文件中有bean属性的内容,那么就用properties文件中的值来代替上下
- 通过XSD验证XML
antlove
xmlschemaxsdvalidationSchemaFactory
1. XmlValidation.java
package xml.validation;
import java.io.InputStream;
import javax.xml.XMLConstants;
import javax.xml.transform.stream.StreamSource;
import javax.xml.validation.Schem
- 文本流与字符集
百合不是茶
PrintWrite()的使用字符集名字 别名获取
文本数据的输入输出;
输入;数据流,缓冲流
输出;介绍向文本打印格式化的输出PrintWrite();
package 文本流;
import java.io.FileNotFound
- ibatis模糊查询sqlmap-mapping-**.xml配置
bijian1013
ibatis
正常我们写ibatis的sqlmap-mapping-*.xml文件时,传入的参数都用##标识,如下所示:
<resultMap id="personInfo" class="com.bijian.study.dto.PersonDTO">
<res
- java jvm常用命令工具——jdb命令(The Java Debugger)
bijian1013
javajvmjdb
用来对core文件和正在运行的Java进程进行实时地调试,里面包含了丰富的命令帮助您进行调试,它的功能和Sun studio里面所带的dbx非常相似,但 jdb是专门用来针对Java应用程序的。
现在应该说日常的开发中很少用到JDB了,因为现在的IDE已经帮我们封装好了,如使用ECLI
- 【Spring框架二】Spring常用注解之Component、Repository、Service和Controller注解
bit1129
controller
在Spring常用注解第一步部分【Spring框架一】Spring常用注解之Autowired和Resource注解(http://bit1129.iteye.com/blog/2114084)中介绍了Autowired和Resource两个注解的功能,它们用于将依赖根据名称或者类型进行自动的注入,这简化了在XML中,依赖注入部分的XML的编写,但是UserDao和UserService两个bea
- cxf wsdl2java生成代码super出错,构造函数不匹配
bitray
super
由于过去对于soap协议的cxf接触的不是很多,所以遇到了也是迷糊了一会.后来经过查找资料才得以解决. 初始原因一般是由于jaxws2.2规范和jdk6及以上不兼容导致的.所以要强制降为jaxws2.1进行编译生成.我们需要少量的修改:
我们原来的代码
wsdl2java com.test.xxx -client http://.....
修改后的代
- 动态页面正文部分中文乱码排障一例
ronin47
公司网站一部分动态页面,早先使用apache+resin的架构运行,考虑到高并发访问下的响应性能问题,在前不久逐步开始用nginx替换掉了apache。 不过随后发现了一个问题,随意进入某一有分页的网页,第一页是正常的(因为静态化过了);点“下一页”,出来的页面两边正常,中间部分的标题、关键字等也正常,唯独每个标题下的正文无法正常显示。 因为有做过系统调整,所以第一反应就是新上
- java-54- 调整数组顺序使奇数位于偶数前面
bylijinnan
java
import java.util.Arrays;
import java.util.Random;
import ljn.help.Helper;
public class OddBeforeEven {
/**
* Q 54 调整数组顺序使奇数位于偶数前面
* 输入一个整数数组,调整数组中数字的顺序,使得所有奇数位于数组的前半部分,所有偶数位于数组的后半
- 从100PV到1亿级PV网站架构演变
cfyme
网站架构
一个网站就像一个人,存在一个从小到大的过程。养一个网站和养一个人一样,不同时期需要不同的方法,不同的方法下有共同的原则。本文结合我自已14年网站人的经历记录一些架构演变中的体会。 1:积累是必不可少的
架构师不是一天练成的。
1999年,我作了一个个人主页,在学校内的虚拟空间,参加了一次主页大赛,几个DREAMWEAVER的页面,几个TABLE作布局,一个DB连接,几行PHP的代码嵌入在HTM
- [宇宙时代]宇宙时代的GIS是什么?
comsci
Gis
我们都知道一个事实,在行星内部的时候,因为地理信息的坐标都是相对固定的,所以我们获取一组GIS数据之后,就可以存储到硬盘中,长久使用。。。但是,请注意,这种经验在宇宙时代是不能够被继续使用的
宇宙是一个高维时空
- 详解create database命令
czmmiao
database
完整命令
CREATE DATABASE mynewdb USER SYS IDENTIFIED BY sys_password USER SYSTEM IDENTIFIED BY system_password LOGFILE GROUP 1 ('/u01/logs/my/redo01a.log','/u02/logs/m
- 几句不中听却不得不认可的话
datageek
1、人丑就该多读书。
2、你不快乐是因为:你可以像猪一样懒,却无法像只猪一样懒得心安理得。
3、如果你太在意别人的看法,那么你的生活将变成一件裤衩,别人放什么屁,你都得接着。
4、你的问题主要在于:读书不多而买书太多,读书太少又特爱思考,还他妈话痨。
5、与禽兽搏斗的三种结局:(1)、赢了,比禽兽还禽兽。(2)、输了,禽兽不如。(3)、平了,跟禽兽没两样。结论:选择正确的对手很重要。
6
- 1 14:00 PHP中的“syntax error, unexpected T_PAAMAYIM_NEKUDOTAYIM”错误
dcj3sjt126com
PHP
原文地址:http://www.kafka0102.com/2010/08/281.html
因为需要,今天晚些在本机使用PHP做些测试,PHP脚本依赖了一堆我也不清楚做什么用的库。结果一跑起来,就报出类似下面的错误:“Parse error: syntax error, unexpected T_PAAMAYIM_NEKUDOTAYIM in /home/kafka/test/
- xcode6 Auto layout and size classes
dcj3sjt126com
ios
官方GUI
https://developer.apple.com/library/ios/documentation/UserExperience/Conceptual/AutolayoutPG/Introduction/Introduction.html
iOS中使用自动布局(一)
http://www.cocoachina.com/ind
- 通过PreparedStatement批量执行sql语句【sql语句相同,值不同】
梦见x光
sql事务批量执行
比如说:我有一个List需要添加到数据库中,那么我该如何通过PreparedStatement来操作呢?
public void addCustomerByCommit(Connection conn , List<Customer> customerList)
{
String sql = "inseret into customer(id
- 程序员必知必会----linux常用命令之十【系统相关】
hanqunfeng
Linux常用命令
一.linux快捷键
Ctrl+C : 终止当前命令
Ctrl+S : 暂停屏幕输出
Ctrl+Q : 恢复屏幕输出
Ctrl+U : 删除当前行光标前的所有字符
Ctrl+Z : 挂起当前正在执行的进程
Ctrl+L : 清除终端屏幕,相当于clear
二.终端命令
clear : 清除终端屏幕
reset : 重置视窗,当屏幕编码混乱时使用
time com
- NGINX
IXHONG
nginx
pcre 编译安装 nginx
conf/vhost/test.conf
upstream admin {
server 127.0.0.1:8080;
}
server {
listen 80;
&
- 设计模式--工厂模式
kerryg
设计模式
工厂方式模式分为三种:
1、普通工厂模式:建立一个工厂类,对实现了同一个接口的一些类进行实例的创建。
2、多个工厂方法的模式:就是对普通工厂方法模式的改进,在普通工厂方法模式中,如果传递的字符串出错,则不能正确创建对象,而多个工厂方法模式就是提供多个工厂方法,分别创建对象。
3、静态工厂方法模式:就是将上面的多个工厂方法模式里的方法置为静态,
- Spring InitializingBean/init-method和DisposableBean/destroy-method
mx_xiehd
javaspringbeanxml
1.initializingBean/init-method
实现org.springframework.beans.factory.InitializingBean接口允许一个bean在它的所有必须属性被BeanFactory设置后,来执行初始化的工作,InitialzingBean仅仅指定了一个方法。
通常InitializingBean接口的使用是能够被避免的,(不鼓励使用,因为没有必要
- 解决Centos下vim粘贴内容格式混乱问题
qindongliang1922
centosvim
有时候,我们在向vim打开的一个xml,或者任意文件中,拷贝粘贴的代码时,格式莫名其毛的就混乱了,然后自己一个个再重新,把格式排列好,非常耗时,而且很不爽,那么有没有办法避免呢? 答案是肯定的,设置下缩进格式就可以了,非常简单: 在用户的根目录下 直接vi ~/.vimrc文件 然后将set pastetoggle=<F9> 写入这个文件中,保存退出,重新登录,
- netty大并发请求问题
tianzhihehe
netty
多线程并发使用同一个channel
java.nio.BufferOverflowException: null
at java.nio.HeapByteBuffer.put(HeapByteBuffer.java:183) ~[na:1.7.0_60-ea]
at java.nio.ByteBuffer.put(ByteBuffer.java:832) ~[na:1.7.0_60-ea]
- Hadoop NameNode单点问题解决方案之一 AvatarNode
wyz2009107220
NameNode
我们遇到的情况
Hadoop NameNode存在单点问题。这个问题会影响分布式平台24*7运行。先说说我们的情况吧。
我们的团队负责管理一个1200节点的集群(总大小12PB),目前是运行版本为Hadoop 0.20,transaction logs写入一个共享的NFS filer(注:NetApp NFS Filer)。
经常遇到需要中断服务的问题是给hadoop打补丁。 DataNod