2022年春秋杯网络安全联赛-冬季赛RE部分题解
easy_python
python字节码
逻辑整理后就给flag
flag = [204, 141, 44, 236, 111, 140, 140, 76, 44, 172, 7, 7, 39, 165, 70, 7, 39, 166, 165, 134, 134, 140, 204, 165, 7, 39, 230, 140, 165, 70, 44, 172, 102, 6, 140, 204, 230, 230, 76, 198, 38, 175]
for i in range(42):
flag[i] = ((flag[i] >> 5) | (flag[i] << 3) )& 0xff
print(bytes(flag))
#flag{ddbae889-2895-44df-897d-2ae30df77b61}godeep
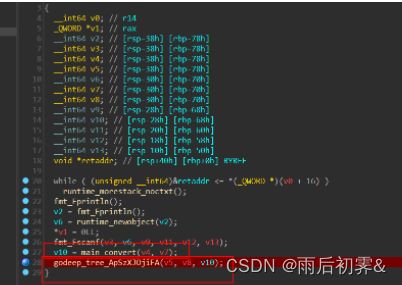
题目提示是找字符串,我们交叉引用的Rigth只有一个地方。
接着梳理程序流程。
在 在main_convert(v4, v7);中,把我们输入的字符串的每个值转二进制
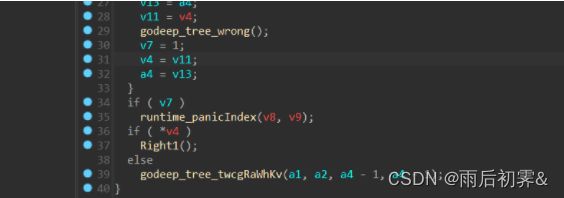
而下面的godeep_tree函数中相当于一个完全二叉树,左0右1。拿着转换二进制来进行走,一直要走到Right这个叶子。
此时*v4的值为1,所以最后8个字是xxxx xxx1 8个一组恢复一个字节
所以思路就是从Right叶子逆推到main函数,一直对函数调用进行交叉引用
s=[0b01100110,0b01100011,0b00110000,0b00110011,0b01100010,0b01100100,0b00111001,0b00110111,0b00101101,0b01100110,0b01100110,0b00110111,0b01100010,0b00101101,0b00110100,0b00110001,0b00111001,0b01100110,0b00101101,0b00111000,0b00111001,0b00111000,0b00110111,0b00101101,0b00110111,0b00111000,0b01100010,0b01100011,0b00110111,0b00110100,0b00110101,0b01100100,0b00110011,0b01100010,0b00110000,0b01100001]
print(bytes(s))
print(len(s))
#b'fc03bd97-ff7b-419f-8987-78bc745d3b0a'
#36reindeer game
玩游戏通关就行,懒得py打包逆向了
flag{82a2acb6-9803-4936-92db-f1431d90c6d1}
baby_transform(未完成)
这个程序逻辑也不复杂
void __fastcall FFT(char *a1, double *a2, int len)
{
double v3; // [rsp+0h] [rbp-40h]
int i; // [rsp+20h] [rbp-20h]
int v6; // [rsp+24h] [rbp-1Ch]
double v8; // [rsp+30h] [rbp-10h]
double v9; // [rsp+38h] [rbp-8h]
for ( i = 0; i < len; ++i )
{
v6 = 0;
v8 = 0.0;
v9 = 0.0;
while ( v6 < len )
{
v8 = (double)a1[v6] * cos((double)v6 * (-6.283185307179586 * (double)i) / (double)len) + v8;
v3 = (double)a1[v6];
v9 = sin((double)v6++ * (-6.283185307179586 * (double)i) / (double)len) * v3 + v9;
}
*a2 = v9;
a2[1] = v8;
a2 += 2;
}
}好像是FFT算法,但我找了几个恢复的脚本。都恢复不出来。
不知道咋回事